Analysing Operation FlightNight: A Cyber Espionage Campaign Targeting Indian Government and Energy Sectors

Introduction
In recent months, the cybersecurity landscape has witnessed the emergence of sophisticated threats targeting critical infrastructure and governmental entities. One such threat, dubbed "Operation FlightNight," has garnered attention due to its strategic targeting of Indian government entities and the energy sector. Foresiet analysts have been diligently investigating this campaign to understand its modus operandi and implications for cybersecurity.
Background
Beginning on March 7th, 2024, Foresiet analysts detected an uncategorized threat actor named FlightNight employing a modified version of the open-source information stealer HackBrowserData to infiltrate Indian government entities and energy companies. The attacker's methodology involved the delivery of malware via phishing emails, disguised as invitation letters from the Indian Air Force. Once executed, the malware facilitated the exfiltration of sensitive data to attacker-controlled Slack channels, which EclecticIQ analysts termed "FlightNight."
Targets and Data Exfiltration
The targets of Operation FlightNight included various government agencies responsible for electronic communications, IT governance, and national defense, alongside private Indian energy companies. The exfiltrated data encompassed a wide array of sensitive information, including confidential internal documents, private email messages, financial records, and details pertaining to oil and gas drilling activities.
Assessment and Implications
With a total of 8.81 GB of exfiltrated data, analysts have raised concerns regarding the potential for further intrusions into the Indian government's infrastructure. Behavioral similarities between Operation FlightNight and a previously reported attack on January 17, 2024, strongly indicate a connection, leading EclecticIQ analysts to assess with high confidence that the motive behind these actions is cyber espionage.
Collaborative Efforts and Assistance
In response to these threats, Foresiet has collaborated with Indian authorities to share findings and assist in identifying victims, facilitating the incident response process. By working together with relevant stakeholders, we aim to mitigate the impact of Operation FlightNight and enhance cybersecurity measures to safeguard critical infrastructure and sensitive data.
Invitation Letter
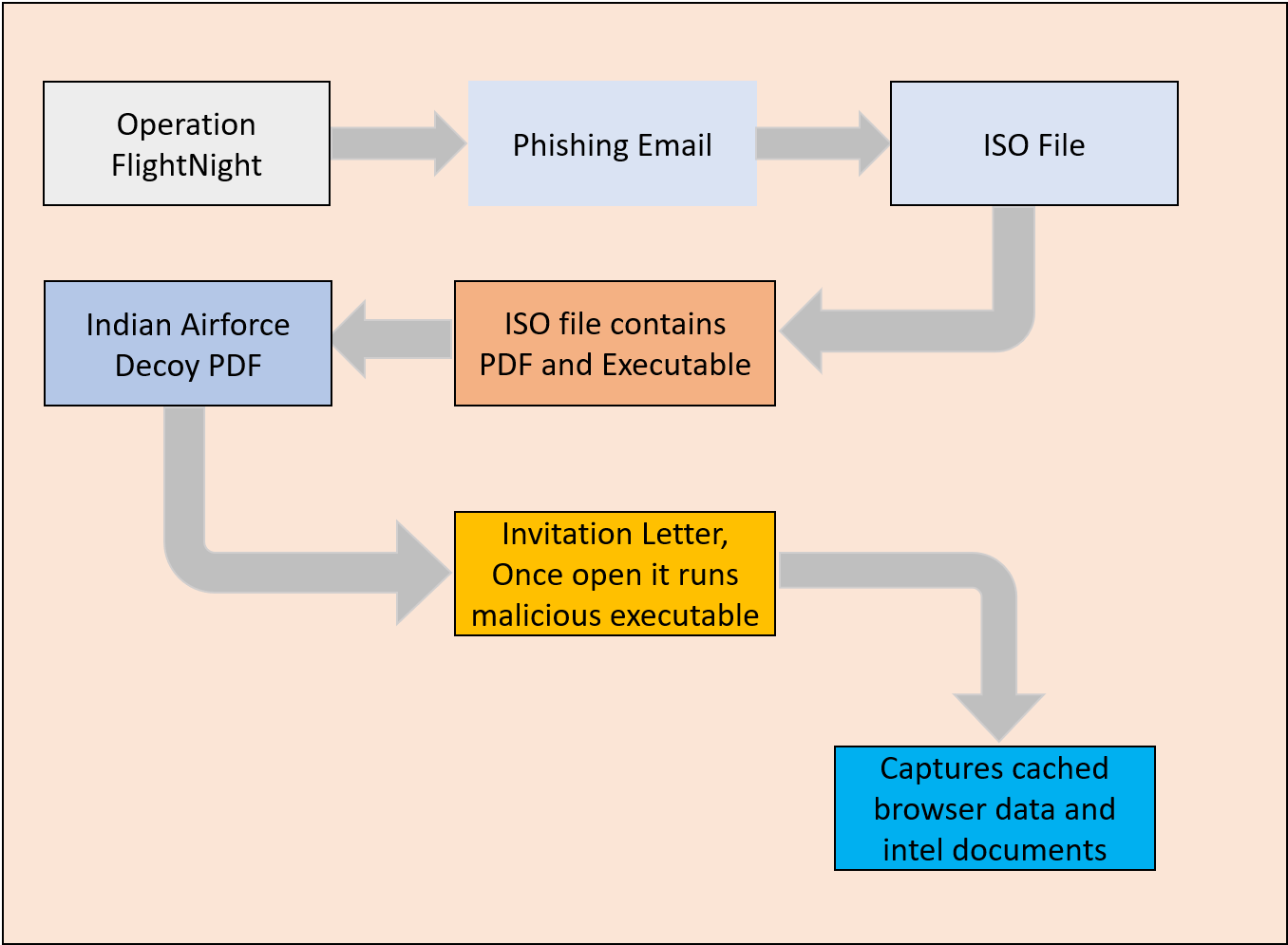
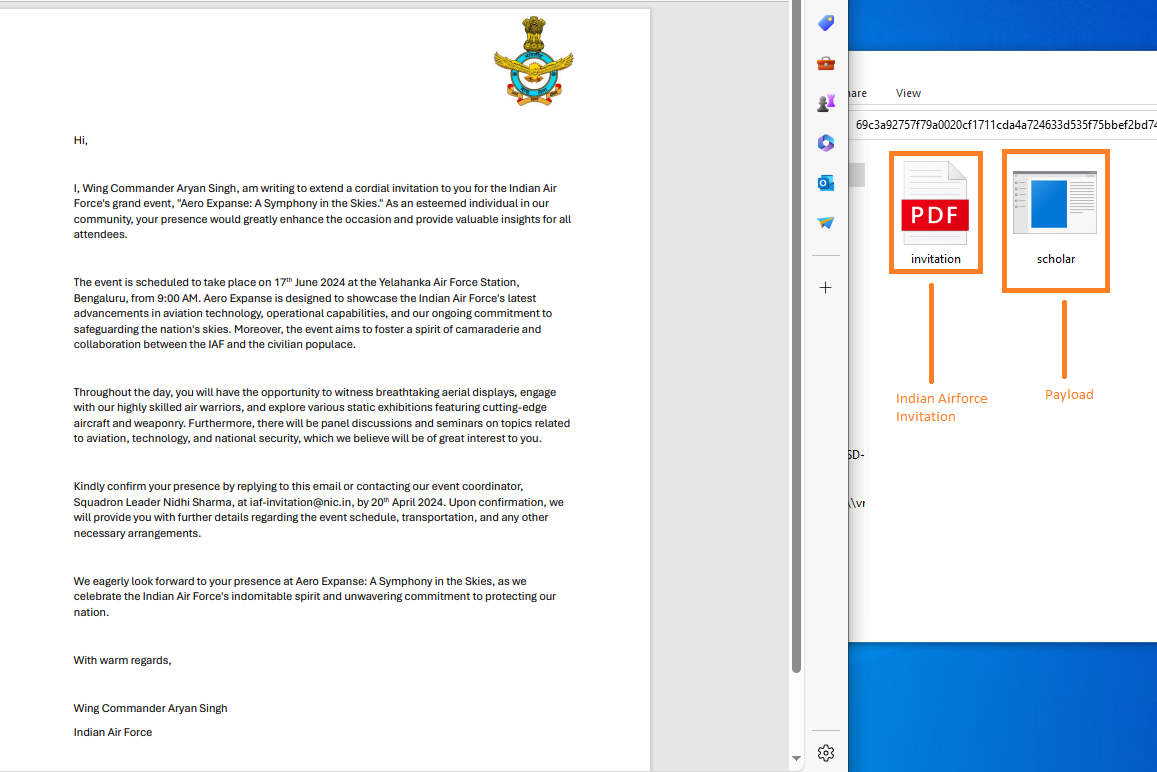
The threat actor employed a deceptive tactic by disguising malware within a decoy PDF document, masquerading as an invitation letter purportedly from the Indian Air Force. This malicious document was concealed within an ISO file, alongside an executable form of the malware. Furthermore, a shortcut file (LNK) was appended to the package, designed to dupe recipients into unwittingly triggering the malware.
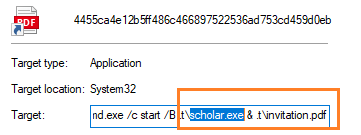
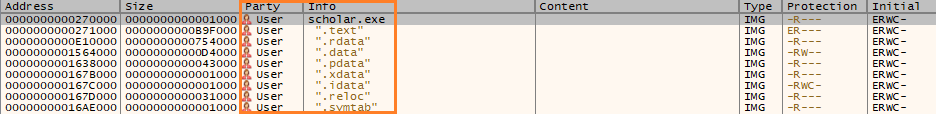
This pdf injected with scholar.exe
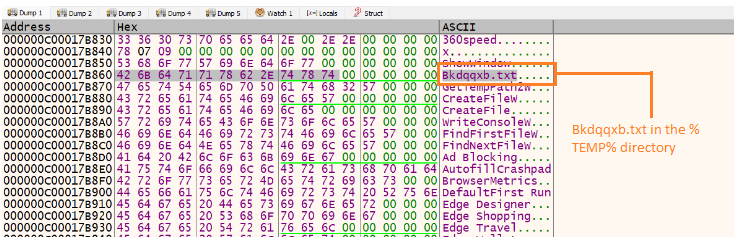
The malware creates a TXT file named "Bkdqqxb.txt" in the `%TEMP%` directory and utilizes it as a mutex to inhibit multiple instances from executing concurrently on the same host. This filename, along with web browser names, is stored in an encoded format and dynamically decoded during the malware's execution.
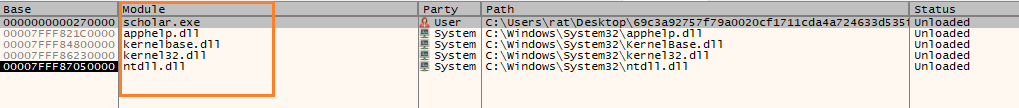
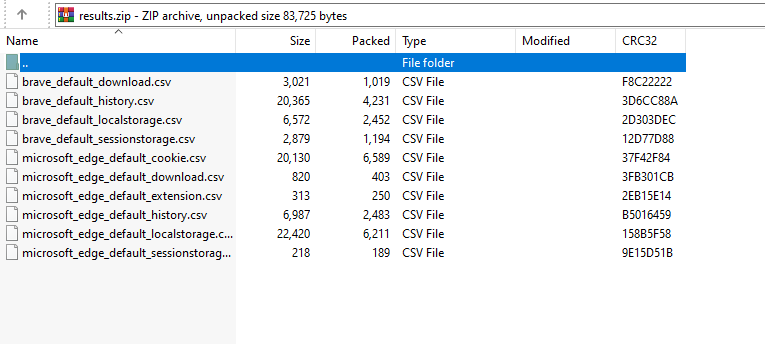
The cached web browser data was stored within the file path "C:\Users\Public\results.zip". This file was transmitted to attacker-controlled Slack channels using the `files.upload` API method.
Detection & Mitigation Opportunities
Email Filtering : Implement robust email filtering solutions to detect and block phishing emails, such as those impersonating legitimate organizations like the Indian Air Force.
Behavioral Analysis : Employ behavioral analysis techniques to identify suspicious activities indicative of malware execution, such as unusual file access patterns or unauthorized data exfiltration attempts.
Endpoint Protection : Utilize advanced endpoint protection solutions equipped with real-time threat detection capabilities to detect and prevent the execution of malicious payloads, including modified versions of known malware like HackBrowserData.
Network Traffic Monitoring : Implement network traffic monitoring tools to detect anomalous communication patterns, such as unexpected data transfers to unauthorized or unusual destinations, such as Slack channels.
List of the targeted web browser
- Google Chrome
- Google Chrome Beta
- Chromium
- Microsoft Edge
- 360 Speed
- Brave
- Opera
- OperaGX
- Vivaldi
Conclusion
Operation FlightNight underscores the evolving nature of cyber threats and the importance of proactive cybersecurity measures. As threat actors continue to exploit vulnerabilities for nefarious purposes, collaboration, information sharing, and robust cybersecurity frameworks are essential in defending against such attacks. Foresiet remains committed to staying at the forefront of cybersecurity research and contributing to global efforts to combat cyber threats effectively.
Indicator of compromise
| Indicator Type | Indicators |
| SHA256 | a811a2dea86dbf6ee9a288624de029be24158fa88f5a6c10acf5bf01ae159e36 |
| SHA256 | 4fa0e396cda9578143ad90ff03702a3b9c796c657f3bdaaf851ea79cb46b86d7 |
| SHA256 | 4a287fa02f75b953e941003cf7c2603e606de3e3a51a3923731ba38eef5532ae |
| SHA256 | dab645ecb8b2e7722b140ffe1fd59373a899f01bc5d69570d60b8b26781c64fb |
| SHA256 | 4455ca4e12b5ff486c466897522536ad753cd459d0eb3bfb1747ffc79a2ce5dd |
| SHA256 | 69c3a92757f79a0020cf1711cda4a724633d535f75bbef2bd74e07a902831d59 |
| SHA256 | 0ac787366bb435c11bf55620b4ba671b710c6f8924712575a0e443abd9922e9f |
MITRE ATT&CK® Techniques
| Tactic | Technique |
| T1567 | Exfiltration Over Web Service |
| T1539 | Steal Web Session Cookie |
| T1217 | Browser Information Discovery |
| T1071.001 | Application Layer Protocol: Web Protocols |
| T1083 | File and Directory Discovery |
| T1566.002 | Phishing: Spearphishing Link |
| T1036.008 | Masquerading: Masquerade File Type |
| T1140 | Deobfuscate/Decode Files or Information |
| T1204.002 | User Execution: Malicious File |
About Foresiet!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


July 1, 2025, 7:17 p.m.

July 1, 2025, 7:07 p.m.