Analyzing ShinyHunters' Cybercrime Activity in the Truist Bank, Twilio Authy, and Neiman Marcus Breaches

Introduction
In the rapidly evolving landscape of cyber threats, few groups have made as significant an impact as ShinyHunters. Emerging in 2020, this international cyber threat group has been responsible for several high-profile data breaches, causing substantial disruptions across various sectors.
The Foresiet Threat Intelligence Team has been closely monitoring ShinyHunters' activities to understand their methods, targets, and the broader implications of their actions.
How Does ShinyHunters Hack?
Targeting various organizations and leaking stolen data on dark web forums. Their methods typically involve a combination of social engineering tactics, exploiting vulnerabilities in software or web applications, and using phishing techniques to gain unauthorized access to systems. They often look for weak points in security, such as outdated software versions or poorly configured systems, to exploit.
Their attacks have included data breaches affecting large corporations, government agencies, and other high-profile targets. To protect against groups like ShinyHunters, organizations should prioritize cybersecurity measures such as regular software updates, strong authentication practices, employee training on phishing awareness, and implementing robust intrusion detection systems.
Notable Breaches
The impact of ShinyHunters' activities reverberates globally, with numerous significant breaches attributed to their operations. From leaking millions of user records from popular online platforms to compromising sensitive government databases, their actions underscore the critical need for robust cybersecurity measures across industries.
Who is ShinyHunters?
ShinyHunters, also known as ShinyCorp, is a notorious cyber threat group that gained prominence in 2020. Despite their playful, Pokémon-inspired name, ShinyHunters is a serious player in the world of cybercrime. They specialize in the theft and sale of vast databases, having targeted multiple companies and stolen millions of records. Their notoriety skyrocketed with their theft of over 90 million customer records from Tokopedia, an Indonesian e-commerce giant, and over 10 million user accounts from the Indian education platform Unacademy.
ShinyHunter Profie
Key Incidents Involving ShinyHunters
FBI Takedown and BreachForums Incident
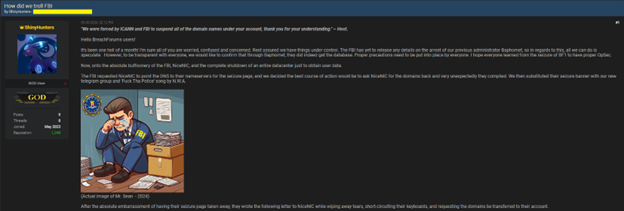
On May 30, ShinyHunters announced the FBI's takedown of BreachForums twice, sharing their side of the story on a dark web forum. They mockingly detailed how they trolled the FBI by reclaiming their domains and replacing the seizure banner with their new Telegram group and N.W.A's "F#ck Tha Police" song.
Incident About FBI
They also confirmed that the FBI had obtained the database through their previous administrator, Baphomet, emphasizing the importance of proper operational security (OpSec) for their community.
ShinyHunters' full statement is as follows:
Hello BreachForums users!
It's been one hell of a month! I'm sure all of you are worried, confused and concerned. Rest assured we have things under control. The FBI has yet to release any details on the arrest of our previous administrator Baphomet, so in regards to this, all we can do is speculate. However, to be transparent with everyone, we would like to confirm that through Baphomet, they did indeed get the database. Proper precautions need to be put into place by everyone. I hope everyone learned from the seizure of BF1 to have proper OpSec.
Now, onto the absolute buffoonery of the FBI, NiceNIC, and the complete shutdown of an entire datacenter just to obtain user data.
The FBI requested NiceNIC to point the DNS to their nameservers for the seizure page, and we decided the best course of action would be to ask NiceNIC for the domains back and very unexpectedly they complied. We then substituted their seizure banner with our new telegram group and 'Fuck Tha Police' song by N.W.A.
After the absolute embarrassment of having their seizure page taken away, they wrote the following letter to NiceNIC while wiping away tears, short-circuiting their keyboards, and requesting the domains be transferred to their account.
Cue the second round of embarrassment for the FBI. Unbeknownst to them, we had transferred the domains to another registrar using the EPP code (saved before seizure). Mr. Sean and 'Special Agent' McKelvey have now been placed on suicide watch after being proven to be complete morons, fucking up a seizure this badly. That's not the end of it either, the FBI went as far as to shut down a legitimate business entirely by seizing EVERY SERVER in an ENTIRE datacenter just to obtain the escrow data. We'd like to apologize to NiceVPS for causing the FBI to shut down your business.
Moving forward: Save the .onion URL. Obviously, clearnet domains aren't going to last forever, though if it goes anything like how it has gone so far we might keep .st forever. We're working on getting everything back up and running. We'll keep everyone posted as we restore our infrastructure.
Recent Breaches
ShinyHunters recent activity’s
Truist Bank
On June 13, 2024, Truist Bank confirmed a breach that occurred in October 2023, affecting over 79,000 employees. The exposed data included work emails, account balances, dates of birth, job titles, names, partial credit card data, and phone numbers.
ShinyHunters released this data on BreachForums, mocking Truist Bank and emphasizing the severe consequences of their attacks.
Neiman Marcus
In May 2024, ShinyHunters breached Neiman Marcus, an American luxury retailer. After the company refused to pay for the deletion of the data, ShinyHunters published it on BreachForums.
The leak involved over 40 million unique email addresses and extensive personal and financial information, including account balances, browser user agent details, credit cards, dates of birth, gift cards, IP addresses, names, payment histories, payment methods, phone numbers, and physical addresses.
Twilio Authy
ShinyHunters also targeted Twilio Authy, compromising data on 33 million phones. They boasted about their success in breaching Twilio Authy and Segment, indicating their persistent targeting of high-profile companies.
Why Do Threat Actors Share Leaked Data for Free?
Threat actors often share leaked data for free for several strategic reasons:
- Building Reputation and Credibility: By releasing valuable data for free, threat actors can establish or enhance their reputation within the hacking community. This can help them gain trust and credibility, which is crucial for future endeavors, collaborations, and recruiting members.
- Attracting Attention: Free leaks can attract significant media and public attention. This publicity can amplify the perceived power and influence of the threat actor or group, which may be used to instill fear or pressure their targets.
- Testing the Value of Data: Releasing a portion of the data for free can serve as a teaser to demonstrate the value and authenticity of the leak. This can entice potential buyers to pay for the rest of the data or future leaks.
- Disruption and Chaos: By sharing sensitive data publicly, threat actors can cause widespread disruption and chaos. This can be part of a broader strategy to damage the reputation of the targeted organization, harm individuals, or destabilize systems.
- Political or Ideological Motives: Some threat actors, such as hacktivists, may have political or ideological motives. Sharing data for free can be a way to promote their cause, expose wrongdoing, or mobilize public opinion against a particular entity or government.
- Economic Pressure: In some cases, sharing data for free can be a tactic to exert economic pressure on a target. For example, after a significant breach, the threat of more data being released can push organizations to pay ransoms or comply with demands.
- Demonstration of Capabilities: For less known or new threat actors, releasing data for free can be a way to demonstrate their capabilities and prove they are capable of executing significant breaches. This can attract future business in the cybercriminal underworld.
- Disinformation and Psychological Warfare: Free leaks can be part of a broader strategy of disinformation and psychological warfare. By releasing data selectively or out of context, threat actors can manipulate public perception and sow distrust within organizations and among the public.
Conclusion
ShinyHunters has firmly established itself as a significant threat in the cyber world. Their audacious attacks, global reach, and sophisticated methods pose serious risks to businesses and individuals alike. The Foresiet Threat Intelligence Team remains committed to monitoring such threats and providing timely insights to help organizations bolster their cybersecurity defenses. As cyber threats continue to evolve, staying informed and vigilant is more crucial than ever.
By staying updated on the latest activities of threat groups like ShinyHunters, businesses can take proactive steps to protect their data and maintain robust security measures.At Foresiet Threat Intelligence Team, we are dedicated to helping our clients navigate the complexities of the cybersecurity landscape, ensuring they are prepared to face any challenges that arise.
About Foresiet!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


