AsyncRAT Exposed: Investigating Email-Driven Cyber Attacks
Introduction
AsyncRAT, also known as "Asynchronous Remote Access Trojan," represents a secretive form of malware meticulously crafted to infiltrate computer systems and exfiltrate critical data. Recently, McAfee Labs unveiled a novel avenue through which this insidious threat proliferates, elucidating its inherent peril and adeptness at circumventing security measures.
This sophisticated malware employs an array of file types, including PowerShell, Windows Script File (WSF), and VBScript (VBS), concealed within a malicious HTML file. This intricate stratagem effectively bypasses conventional antivirus protocols, enabling the seamless dissemination of the infection.
Infection Chain
An HTML page is included as an attachment, which upon opening, initiates an automatic download of a Windows Script File (WSF). Crafted with a deceptive title resembling an Order ID, it creates an illusion of legitimacy, enticing users to execute it. Upon running the WSF file, the infection progresses automatically, requiring no additional user intervention.
Subsequently, the infection chain unfolds by deploying Visual Basic Script (VBS), JavaScript (JS), Batch (BAT), Text (TXT), and PowerShell (PS1) files.
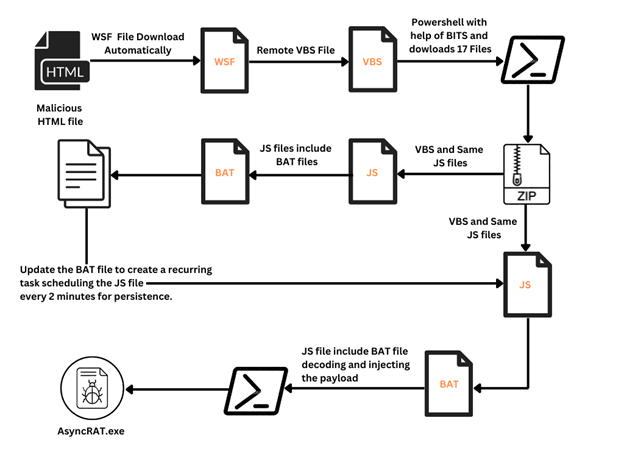
Infection Chain
Technical Analysis
Clicking on a link embedded within a spam email can trigger the opening of a webpage. This webpage may initiate the download of a Windows Script File (WSF), potentially resulting in significant complications.
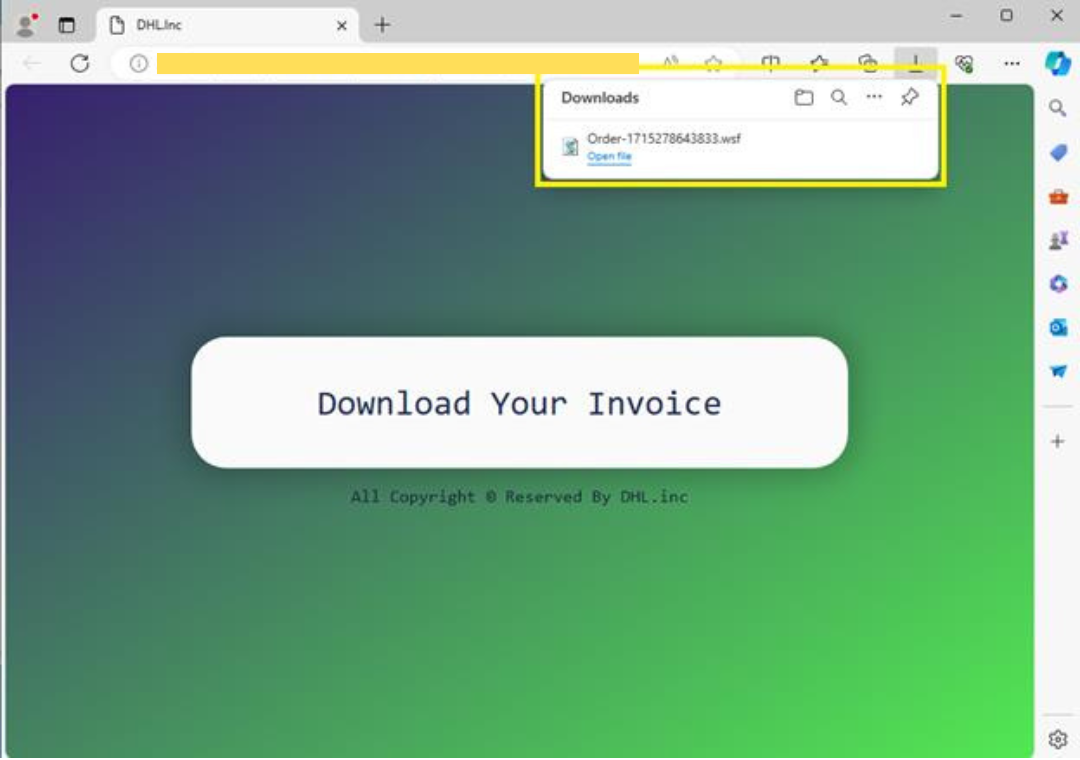
HTML page
We've pinpointed code segments embedded within a .wsf file facilitating the retrieval of an additional text file.
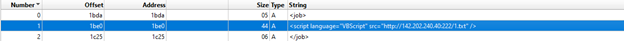
wsf file
The content of the "1.txt" file comprises specific code lines intended for retrieving another file named "r.jpg." However, this file is actually located in the public directory under the name "ty.zip." Subsequently, the zip file is extracted within the same public folder, resulting in the creation of numerous files.

Extracted in a public folder
Sequence of Infection
The "ty.zip" archive contains 17 supplementary files. Among them, the file named "basta.js" is assigned to execute initially. Below is the content of "basta.js":
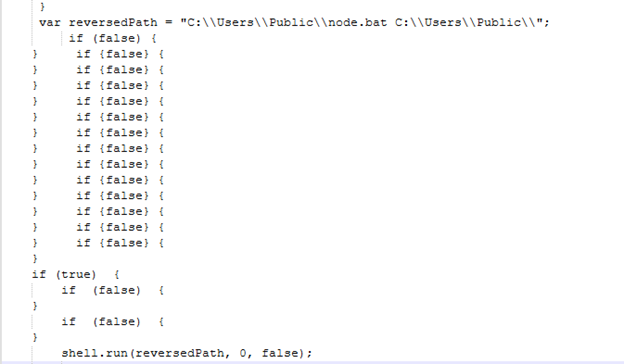
basta.js
"basta.js" calls upon the "node.bat" file located within the same directory.
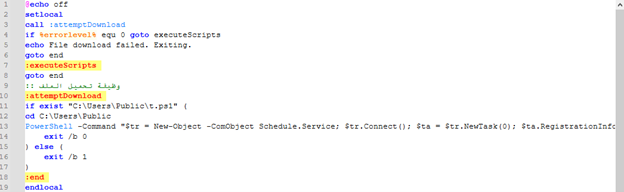
node.js
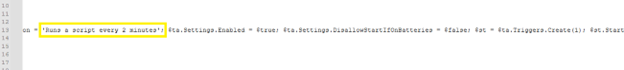
RegistrationInfo.Description = ‘Runs a script every 2 minutes
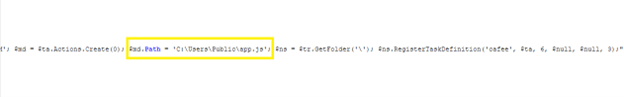
Path = ‘C:\Users\Public\
The "t.bat" file contains a brief obfuscated code segment, which, when deciphered, translates into the following PowerShell command:
Powershell.exe -ExecutionPolicy Bypass -File "C:\Users\Public\t.ps1"
This command executes a PowerShell script located at "C:\Users\Public\t.ps1" while bypassing the execution policy.
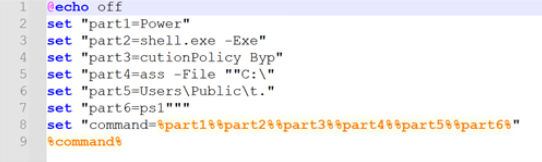
Content of t.bat
Mitigation
Avoiding falling victim to email phishing demands a cautious mindset. Verify sender details, scrutinize links, and watch for errors in spelling and grammar. Be wary of urgent requests for personal information and verify any unusual demands.
Enable email spam filters, delete suspicious emails promptly, and keep software updated. These measures, including using the latest version of Acrobat Reader, fortify defenses against phishing attempts.
Conclusion
This blog post has elucidated the methodology behind AsyncRAT attacks, tracing from an HTML-triggered WSF file download to the injection of malicious code. These techniques are frequently employed by attackers seeking unauthorized access to systems. With Microsoft's implementation of defenses against malicious Office macros, it's anticipated that attackers will increasingly leverage these file types.
At Foresiet, we strongly discourage opening files from unfamiliar sources, particularly those received via email. For businesses, we recommend providing security training to employees and implementing a secure web gateway with advanced threat protection. This solution aids in real-time scanning and detection of harmful files, thereby enhancing organizational security.
Indicator of compromise
| Indicator Type | Indicators |
| File | SHA256 |
| HTML | 969c50f319a591b79037ca50cda55a1bcf2c4284e6ea090a68210039034211db |
| WSF | ec6805562419e16de9609e2a210464d58801c8b8be964f876cf062e4ab52681a |
| ty.zip | daee41645adcf22576def12cb42576a07ed5f181a71d3f241c2c14271aad308b |
| basta.js | 909ec84dfa3f2a00431a20d4b8a241f2959cac2ea402692fd46f4b7dbf247e90 |
| node.bat | 569e33818e6af315b5f290442f9e27dc6c56a25259d9c9866b2ffb4176d07103 |
| app.js | 7d8a4aa184eb350f4be8706afb0d7527fca40c4667ab0491217b9e1e9d0f9c81 |
| t.bat | e2d30095e7825589c3ebd198f31e4c24e213d9f43fc3bb1ab2cf06b70c6eac1d |
| t.ps1 | a0c40aa214cb28caaf1a2f5db136bb079780f05cba50e84bbaeed101f0de7fb3 |
About Foresiet!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


July 10, 2025, 9 a.m.
