Busting the SugarLocker Syndicate: Syndicate's Secrets and Takedown Tactics

Sugarlocker Summary
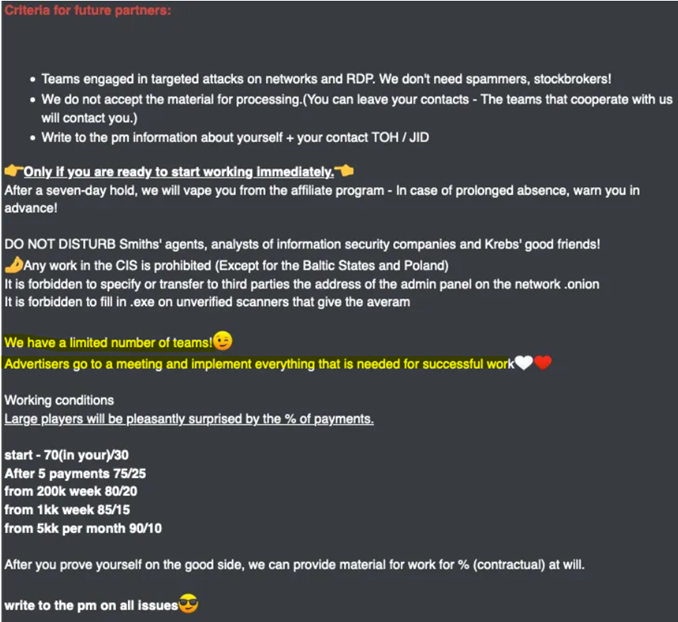
On February 23, 2022, the operator linked to the SugarLocker ransomware, utilizing the pseudonym "gustavedore," was conspicuously seeking new partnerships on the Dark Web. SugarLocker operates through a highly flexible Ransomware-as-a-Service (RaaS) framework, facilitating extensive customization for its users in the clandestine corners of the Dark Web. Anticipated heightened activity is foreseen due to ongoing updates to this model and the strategic recruitment of additional partners within the Dark Web ecosystem.
SugarLocker, also recognized as Encoded01 ransomware, is developed in Delphi and stands out by offering a more extensive array of options compared to other RaaS offerings within the obscured realms of the Dark Web. Presently, there is no confirmed connection with other established ransomware groups on the Dark Web. Notably, the ransom note employed by SugarLocker closely mirrors that of REvil, while its negotiation page aligns with the practices of CLOP, providing a unique footprint in the dark alleys of the Dark Web.
The individual identified as "gustavedore," responsible for orchestrating the SugarLocker ransomware, commenced RaaS operations in November 2021, strategically navigating the intricate landscape of the Dark Web. Actively pursuing collaborations, "gustavedore" engages potential partners through interactions on RAMP, a Dark Web forum exclusively dedicated to discussions and transactions related to ransomware, emphasizing the covert nature of these activities within the Dark Web domain.
Sugar Locker Detail Analysis
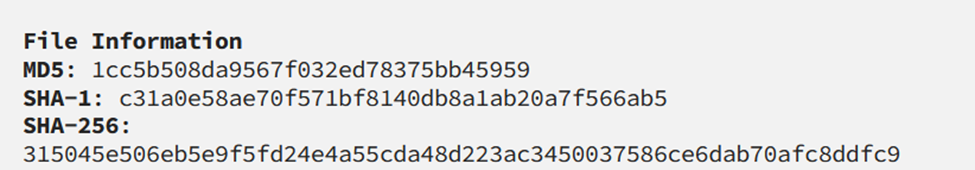
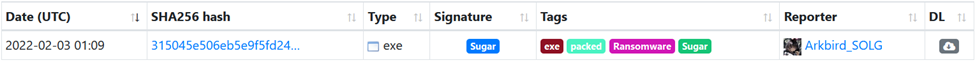
Upon activation, the Sugar Ransomware initiates connections to whatismyipaddress.com and ip2location.com to retrieve the device's IP address and geographical coordinates. Subsequently, it proceeds to download a 76MB file from http://cdn2546713.cdnmegafiles[.]com/data23072021_1.dat, although the exact purpose of this downloaded file remains unclear.
The ransomware will encrypt all files, excluding those contained within specified folders or bearing designated file names as listed below:
Excluded folders:
- \windows\
- \DRIVERS\
- \PerfLogs\
- \temp\
- \boot\
Excluded files:
- BOOTNXT
- bootmgr
- pagefile
- .exe
- .dll
- .sys
- .lnk
- .bat
These processes persist even when attempts are made to halt or reboot the system, resulting in degradation of overall system performance by inducing slowdowns.
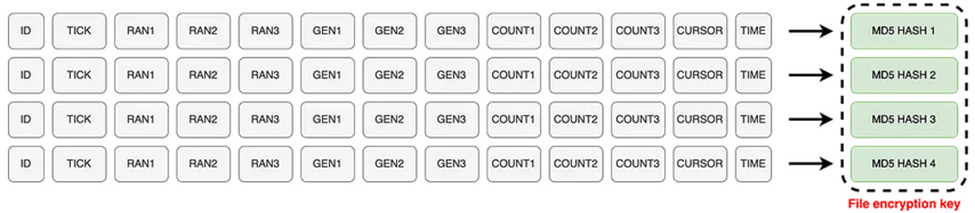
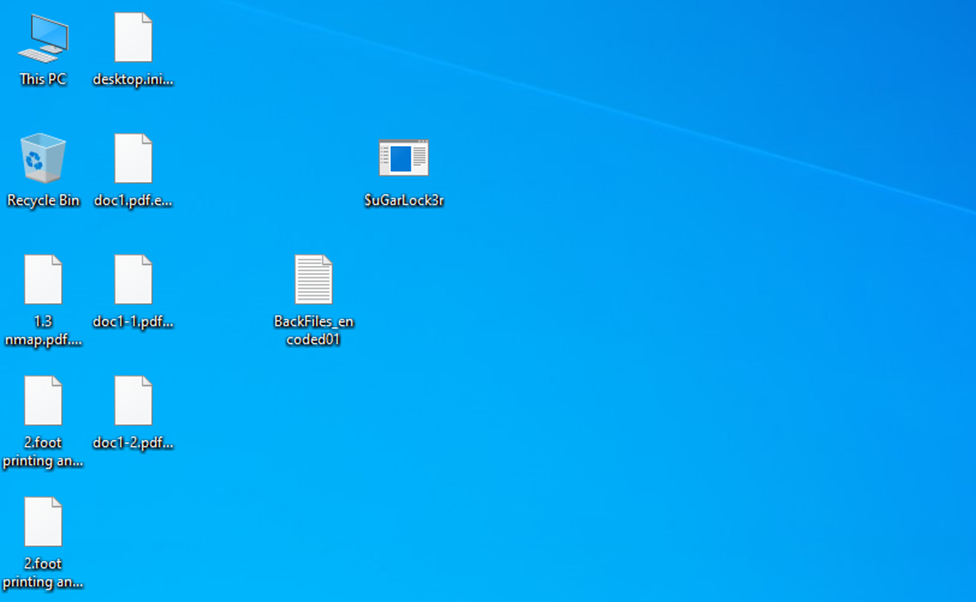
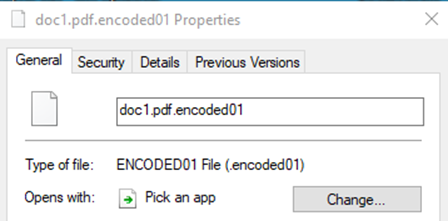
The encrypted files will have the .encoded01 extension appended to file names, as shown below.
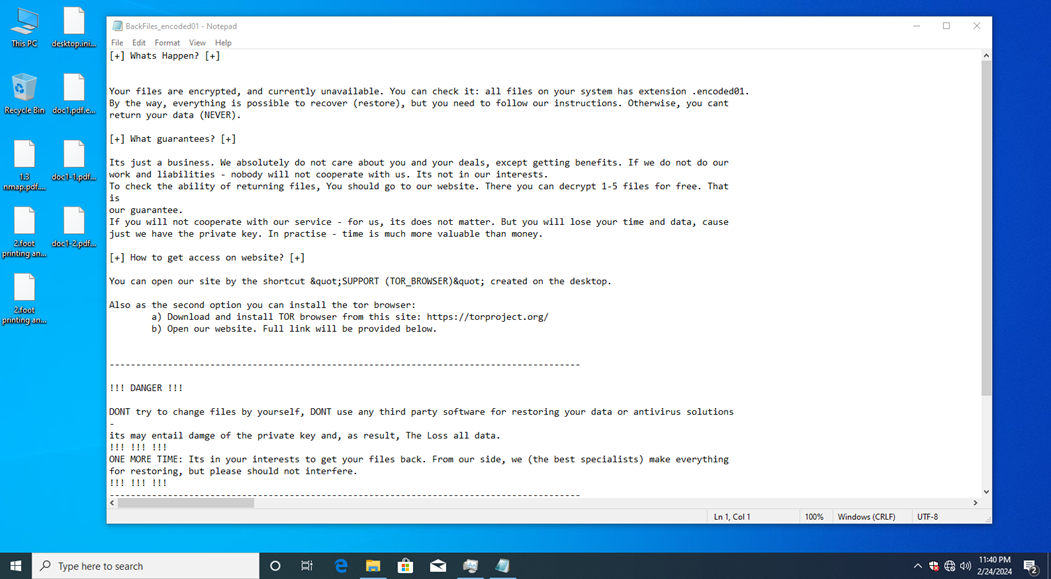
Additionally, the ransomware generates ransom notes titled "BackFiles_encoded01.txt" in every folder scanned for files on the compromised computer.
The ransom note, "BackFiles_encoded01.txt," includes details regarding the status of the victim's files, a unique identification code, and a hyperlink to a Tor website providing instructions for ransom payment.
Register in the registry to automatically run after booting
If the FLAG_Autorun option is enabled, the SugarLocker is executed every boot by registering the current file path in the registry below.
- PATH: HKCU\Software\Microsoft\Windows\CurrentVersion\Run
- Key: [ID2]
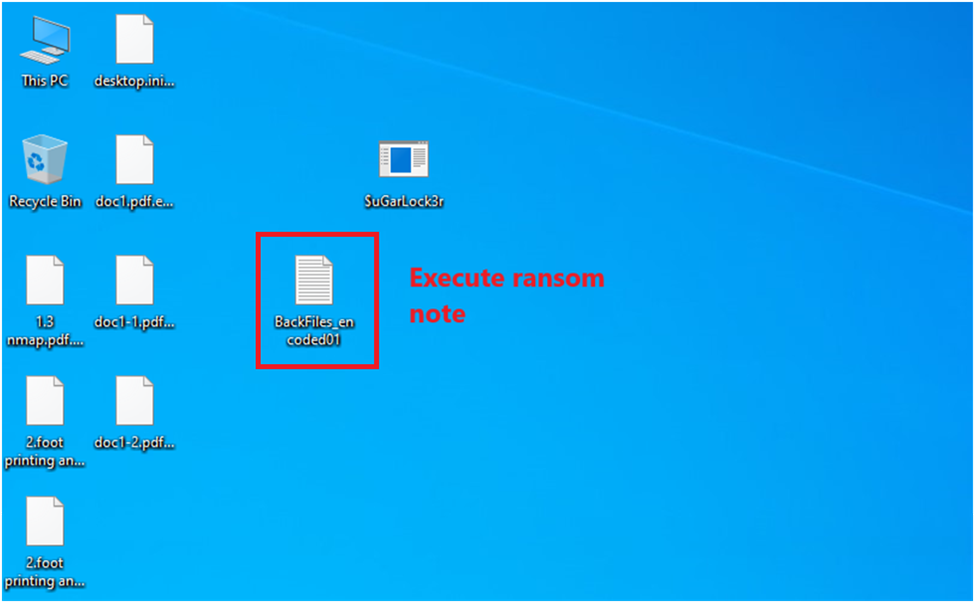
Execute ransom note :
Users are instructed to install the Tor browser for accessing the negotiation site. Subsequently, a ransom note is generated, adhering to the specified path and content guidelines. Additionally, the execution of a notepad.exe process ensures the prominent display of the ransom note.
Download the Tor browser to access the negotiation site
- First, to create a Tor browser directory on the desktop, the desktop path is collected according to the Integrity Level of the current token.
- System Privileges: Finds user logon sessions and collects the user profile path.
- After that, access the download URL to download additional files.
- Download URL: http://cdn2546713[.]cdnmegafiles.com/data23072021_1.dat
Upon visiting the Tor site, the victim will be directed to a personalized page featuring their unique details, including the Bitcoin address for ransom payment, a chat section for communication with the perpetrators, and an option to decrypt up to five files free of charge.
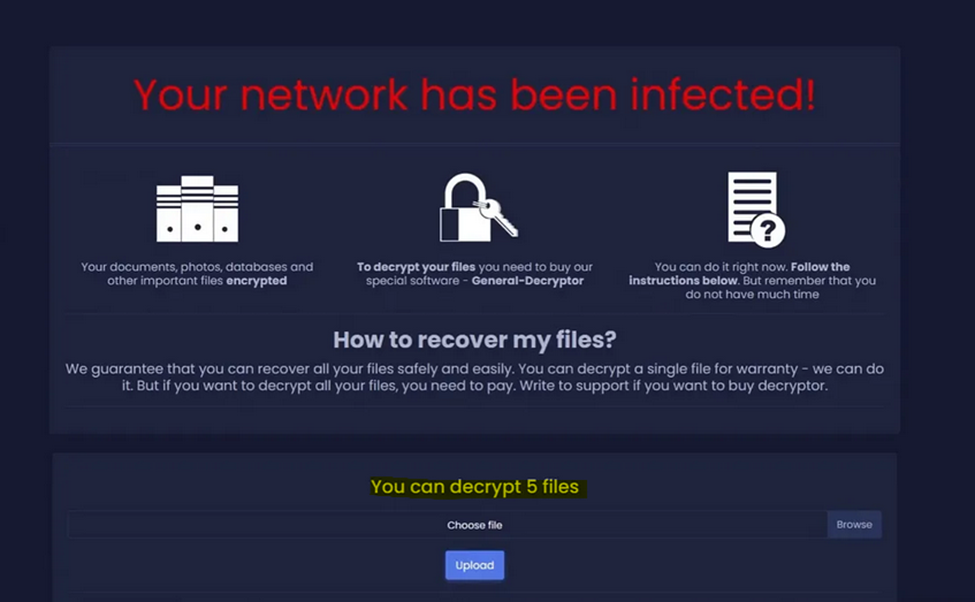
The ransomware campaign displays remarkably modest ransom demands, as witnessed by BleepingComputer, often requesting merely a few hundred dollars in exchange for a decryption key.
At this time, it is unclear if the ransomware has any weaknesses that could allow decryption for free. https://www.nomoreransom.org/en/decryption-tools.html
History of SugarLocker Ransomware
As of January 10, 2022, the latest verified iteration of SugarLocker is version 1.0.6. Versions 1.0.5, 1.0.4, and 1.0.3 have been effectively addressed through supplementary investigative measures. Commencing from version 1.0.4, there has been a progressive augmentation in the count of execution parameters with each successive version update. Additionally, version 1.0.5 incorporated a logging function designed to validate the successful execution of malevolent activities.
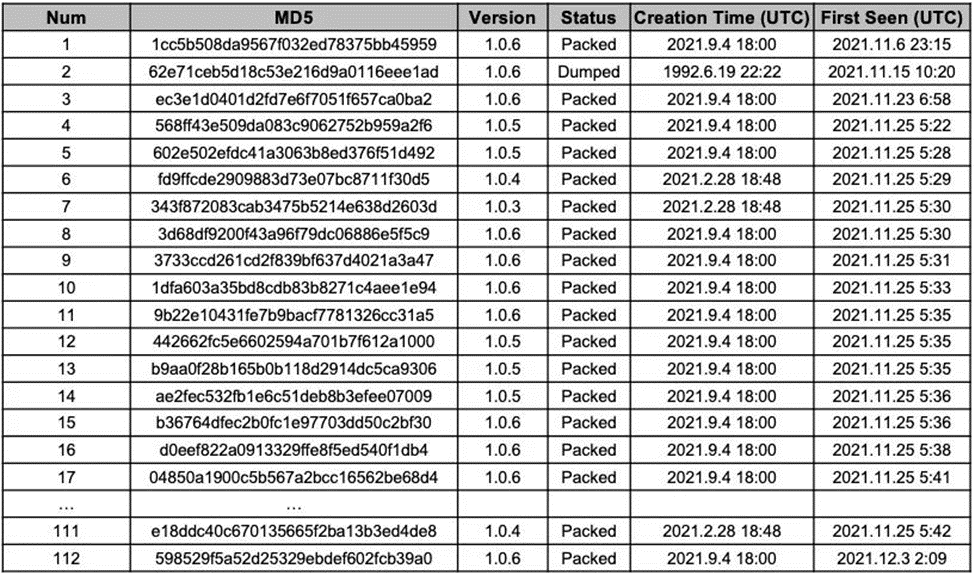
Among 112 samples, the statistics for each version are as follows.
Russian Authorities, FACCT Company Collaborate to Apprehend SugarLocker Cybercrime Syndicate Members,
Russian authorities, in collaboration with FACCT Company, have apprehended members of the SugarLocker cybercrime syndicate. Operating under the guise of the legitimate IT firm Shtazi-IT, the group claimed to offer various services, including the development of landing pages, mobile applications, scripts, parsers, and online stores. However, upon investigation, it was revealed that the SugarLocker ransomware (Encoded01) was developed in early 2021 and became active in November of the same year.
In January 2024, three members of the group, including 34-year-old Alexander Ermakov (aliases: blade_runner, GustaveDore, JimJones), were arrested. The raid resulted in the seizure of laptops, mobile phones, and substantial evidence of illicit activities. Ermakov had previously been implicated in cyberattacks targeting Medibank Private, exposing personal data of nearly 10 million Australians. This prompted the Australian government to launch its first offensive against cybercriminals.

The defendants face charges under Article 273 of the Criminal Code of the Russian Federation for the "Creation, use, and dissemination of malicious computer programs," carrying a maximum penalty of 7 years' imprisonment. The ongoing investigation is a collaborative effort between the Russian Ministry of Internal Affairs and FACCT.
As of February 21, 2024, the collaboration has resulted in the dismantling of the SugarLocker ransomware group, as announced in a FACCT press release. The cybercriminals had operated under the guise of a legitimate IT company, offering services for website development and online applications.
About Foresiet!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


