Chinese APT Exploits Ivanti CVE-2025-22457 with Malware

A newly disclosed vulnerability in Ivanti Connect Secure (ICS) VPN appliances has been weaponized in the wild by a Chinese nation-state threat actor, UNC5221. Tracked as CVE-2025-22457, this critical stack-based buffer overflow vulnerability allows unauthenticated remote attackers to execute arbitrary code, posing a significant risk to enterprise networks.
CVE-2025-22457: Critical Buffer Overflow Vulnerability
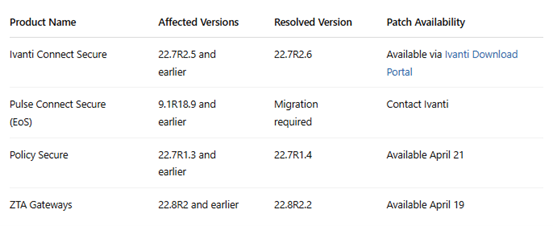
Ivanti’s Connect Secure VPN, along with Ivanti Policy Secure and ZTA Gateways, are affected by a stack-based buffer overflow vulnerability that received a CVSS score of 9.0 (Critical). The flaw affects versions prior to:
- Ivanti Connect Secure: 22.7R2.6
- Policy Secure: 22.7R1.4
- ZTA Gateways: 22.8R2.2
Ivanti released a patch for this vulnerability on February 11, 2025, with the recommendation that customers immediately update to the latest secure versions. Legacy ICS 9.x versions, which are now end-of-support, remain vulnerable and are being actively exploited.
Active Exploitation by UNC5221
Chinese-linked espionage group UNC5221 is actively exploiting CVE-2025-22457. The attacks began in mid-March 2025, with threat actors leveraging this vulnerability to deploy a suite of custom malware tailored for stealth and persistence.
Emerging Malware Ecosystem: TRAILBLAZE, BRUSHFIRE, and SPAWN
Following successful exploitation, the attackers deploy two newly identified malware families:
TRAILBLAZE:
A memory-resident dropper designed to evade traditional detection methods. It injects a stealth backdoor into legitimate ICS processes.
TRAILBLAZE:
- T1055 – Process Injection
- T1027 – Obfuscated Files or Information
- T1059 – Command and Scripting Interpreter
BRUSHFIRE:
A passive SSL_read hook backdoor that activates only when specific encrypted strings are received, allowing covert shellcode execution.
- T1176 – Browser Extensions (SSL Hooking)
- T1071.001 – Application Layer Protocol: Web Protocols
- T1024 – Custom Cryptographic Protocol
In addition, the attackers introduced a modular malware framework dubbed SPAWN, which consists of several specialized components:
SPAWNSLOTH:
Disables logging by targeting the dslogserver process, affecting both local logs and remote syslog forwarding.
MITRE Techniques:
- T1562.002 – Impair Defenses: Disable Windows Event Logging
- T1005 – Data from Local System
SPAWNSNARE:
A utility that extracts and encrypts Linux kernel images using AES.
MITRE Techniques:
- T1003 – OS Credential Dumping (if credentials in kernel memory)
- T1486 – Data Encrypted for Impact
SPAWNWAVE:
A powerful hybrid component combining features from SPAWNSLOTH, SPAWNSNARE, and BRUSHFIRE to maintain stealth and control over compromised systems. These tools work in concert to establish long-term persistence and evade detection, even across system reboots.
MITRE Techniques:
- T1036 – Masquerading
- T1105 – Ingress Tool Transfer
- T1218 – Signed Binary Proxy Execution
Indicators of Compromise (IOCs)
Below is a compilation of observed IOCs linked to the exploitation of CVE-2025-22457 by UNC5221 and the deployment of TRAILBLAZE, BRUSHFIRE, and SPAWN malware components.
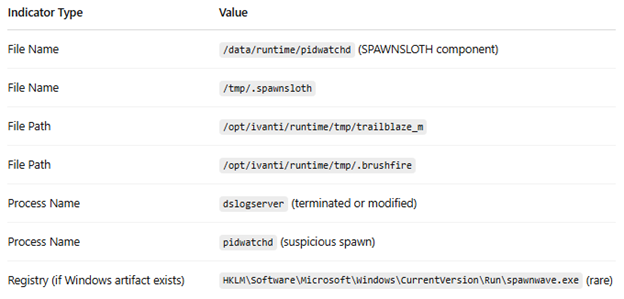
File and Process Artifacts
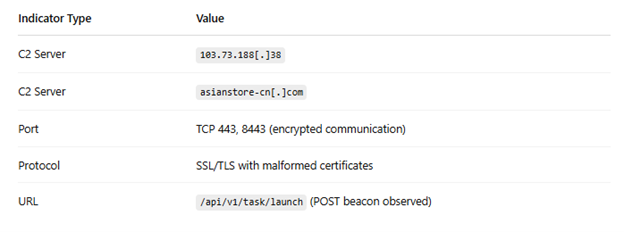
Network Indicators
SSL Hook Behavior (BRUSHFIRE)
- Modifies OpenSSL SSL_read function to parse inbound data.
- Looks for specific hex patterns or AES-encrypted strings before executing shellcode.
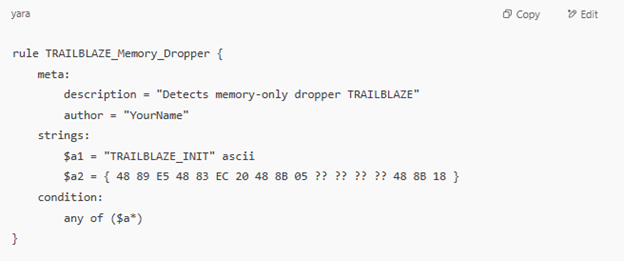
Detection Rules (Example YARA)
Affected Products and Patches
Recommended Actions
Organizations using Ivanti Connect Secure or related products should:
- Immediately upgrade to the patched versions.
- Monitor for indicators of compromise related to TRAILBLAZE, BRUSHFIRE, and SPAWN.
- Isolate legacy 9.x devices and initiate migration to supported platforms.
- Implement enhanced logging and endpoint monitoring to detect memory-resident threats.
Conclusion
The exploitation of CVE-2025-22457 highlights the growing sophistication of state-backed actors and the critical importance of timely patch management. Organizations relying on Ivanti products must treat this vulnerability as a top-priority threat and take swift action to mitigate risk.
MD5
- 10659b392e7f5b30b375b94cae4fdca0
- 4628a501088c31f53b5c9ddf6788e835
- 6e01ef1367ea81994578526b3bd331d6
- ce2b6a554ae46b5eb7d79ca5e7f440da
- e5192258c27e712c7acf80303e68980b
SHA256
- 0066a643db06125f6faa98f1efa73cbcae674a322a47d22eef479169f814dc95
- 04e79c022071f1e404b8ac5d2e7d3f228795385ad45f225b1bacc65f4e3d76b1
- 350b3c2c99a9b849b454e0ce35cb3dc3b1c386cc9c8be90e77389c500f3e400a
- 612988314d14ea3005286eac914722aac75691c6afc0a49108cfbfe98936e8ed
- b1221000f43734436ec8022caaa34b133f4581ca3ae8eccd8d57ea62573f301d
About us!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


July 10, 2025, 9 a.m.
