Chinese healthcare comapany, Hinacom breached

In yet another alarming breach incident, the notorious hacking group SiegedSec has targeted the healthcare sector once again. This time, their target was the prominent Chinese healthcare company Hinacom. The cybercriminals successfully infiltrated the company's defenses, exposing a staggering 11GB of sensitive data. This blog explores the details of the hack, the potential consequences, and the urgent need for improved healthcare security.
The Hinacom Breach:
On a dark day for Hinacom, SiegedSec unleashed their hacking prowess, compromising the company's security infrastructure and gaining unauthorized access to their systems. The result? An extensive data leak that compromises patient information, exposes source code and databases, and reveals various documents.
Data Breach Fallout:
The sheer volume of data compromised in the Hinacom breach raises significant concerns about the privacy and security of patients. Medical records, personal information, and other sensitive data have been exposed, leaving patients vulnerable to identity theft, fraud, and other malicious activities. Moreover, the leak of source code and databases can have severe implications for Hinacom's operations and intellectual property.
SiegedSec's Previous Attacks on Companies:
The Hinacom breach is not the first display of SiegedSec's malevolent intentions towards the healthcare industry. Previously, the group targeted Poorvika, the popular mobile phone chain store, and numerous other organizations in various sector. SiegedSec's pattern of attacks underscores the urgency for companies to strengthen their security measures.
Attack on Poorvika:
In the middle of March this year, the Indian tech retailer Poorvika Mobiles became the latest cyberattack victim. The hacker group SiegedSec leaked over 15GB of sensitive data on the company's employees, including personal and financial information. While the hacker group did not disclose their method of obtaining the information here too, it was evident that they hacked into a backend server, as the leaked data was in SQL format. The group also referred to the apprehension of Pompompurin, the owner of BreachedForums, by the US FBI in their data dump.
Technical Details of the Hinacom Hack:
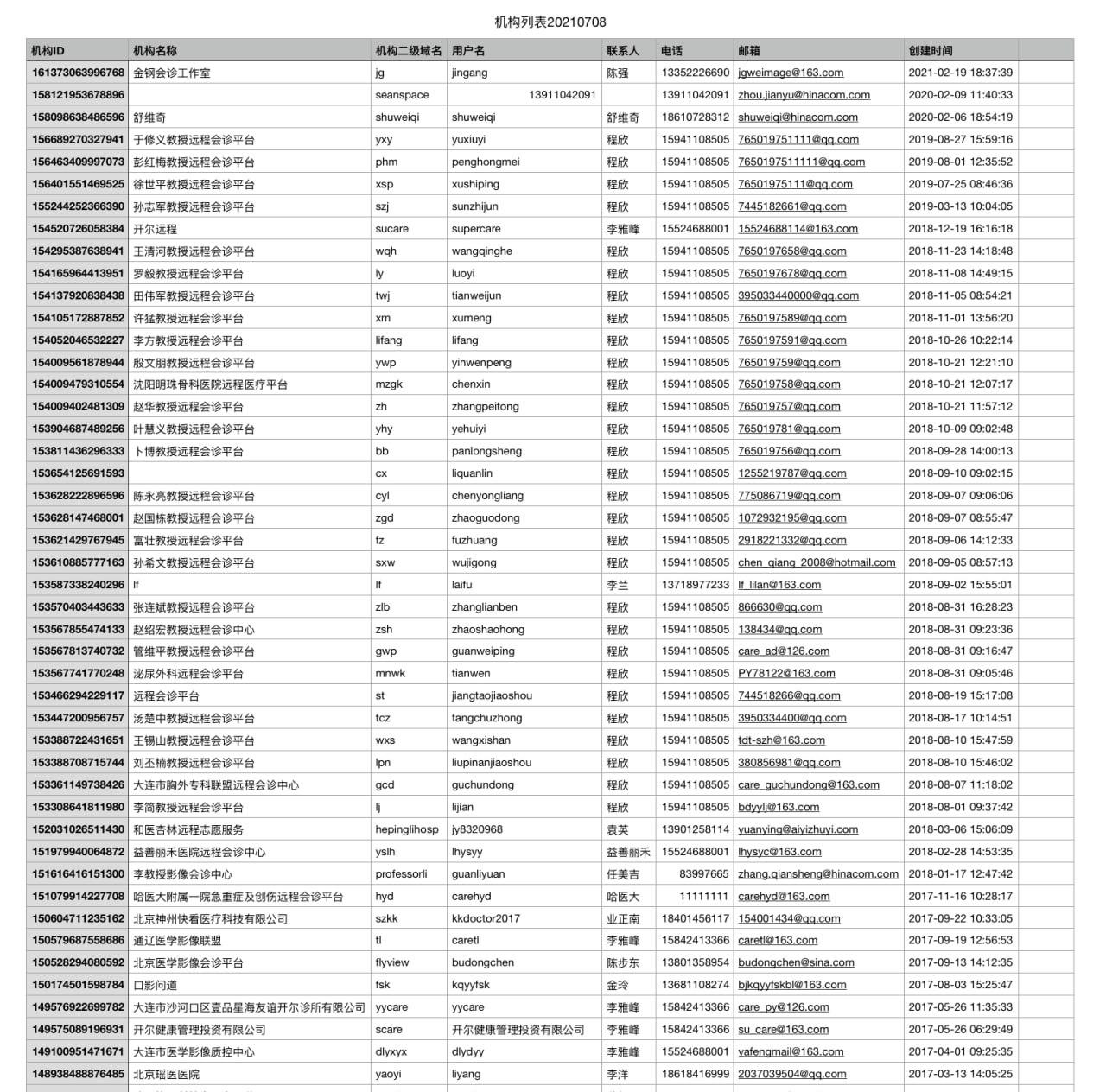
The data leaked by the attackers includes data from the databases and the company’s miPlatform. Furthermore, user data was also leaked as a separate folder along with the above information.
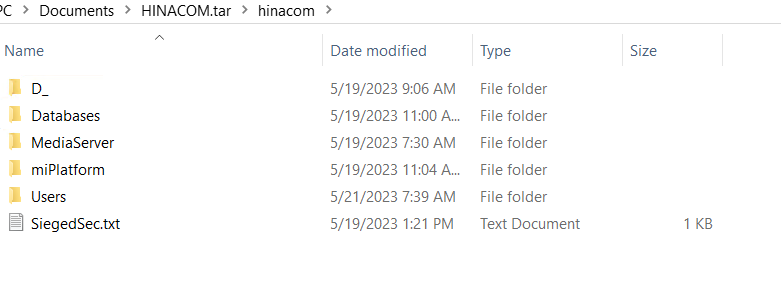
Inside the Database folder, information regarding the company’s User Tracking, miPlatform model and Server reports were leaked in the form of BAK files. There was an msdb file among the above documents
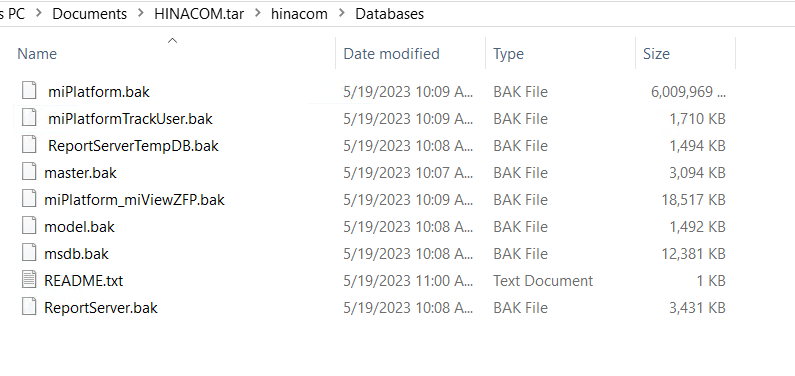
On further inspection of the Administrator view of the Users folder, highly sensitive data regarding cookies, contact information and user data was also part of the package the attackers gained by compromising the company’s servers.
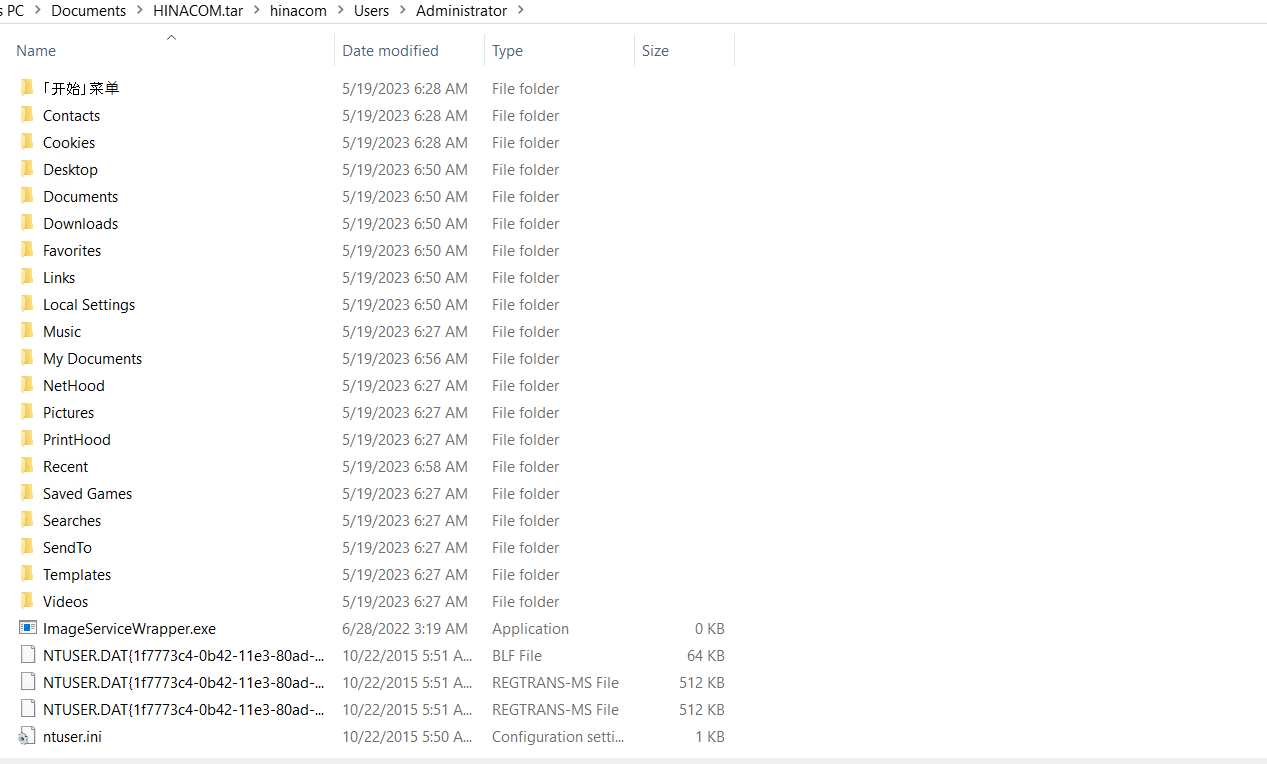
The media server was also not spared, as the folders of data regarding the servers that were compromised were also leaked
While the exact methodology employed by SiegedSec to breach Hinacom's defenses has not been publicly disclosed, it is essential to understand the common attack vectors and vulnerabilities that cybercriminals exploit in healthcare organizations:
1. Phishing Attacks:
Cybercriminals often use phishing emails to deceive employees into clicking on malicious links or attachments, leading to unauthorized access.
2. Weak Passwords:
Weak or reused passwords provide a straightforward entry point for attackers. Organizations must enforce strict password policies and implement multi-factor authentication.
3. Unpatched Software:
Failure to apply necessary software updates and security patches can leave systems exposed to known vulnerabilities.
4. Insider Threats:
In some cases, disgruntled employees or individuals with privileged access can misuse their privileges to gain unauthorized access or leak sensitive data. 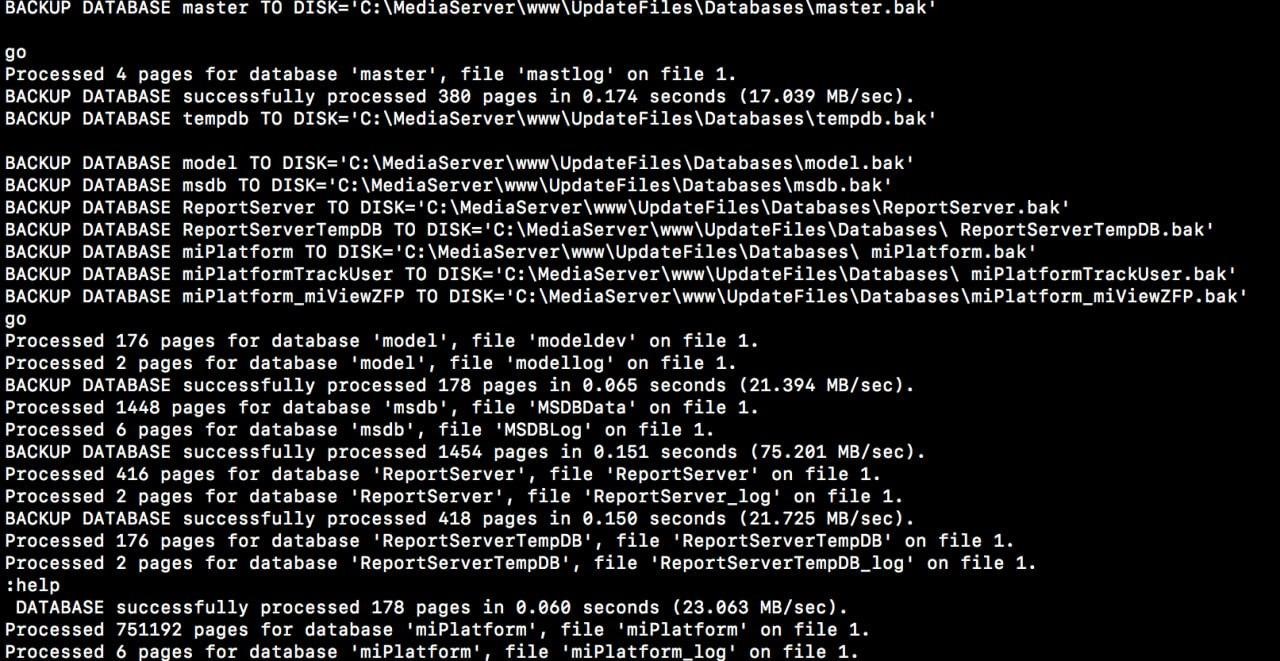
Addressing the Urgent Need for Improved Healthcare Security:
The Hinacom breach serves as a stark reminder that healthcare organizations must prioritize cybersecurity and take proactive steps to safeguard patient data. The following measures can help bolster healthcare security:
1. Robust Security Measures:
Implementing comprehensive security measures, including firewalls, intrusion detection systems, and encryption protocols, can significantly enhance defense against cyber threats.
2. Employee Education and Awareness:
Regular training sessions on cybersecurity best practices, such as identifying phishing attempts and maintaining strong passwords, are crucial in preventing successful attacks.
3. Regular Security Audits:
Conducting periodic security audits and penetration testing can identify vulnerabilities and ensure timely remediation.
4. Patch Management:
Promptly applying software updates and security patches is essential to address known vulnerabilities and prevent exploitation.
5. Incident Response Planning:
Developing a well-defined incident response plan can minimize the impact of a breach and facilitate swift action in the event of an incident.Conclusion:
The Hinacom breach orchestrated by SiegedSec is a grim reminder of the persistent threats faced by the healthcare industry. The compromised patient data and system vulnerabilities highlight the urgent need for healthcare organizations to invest in robust security measures. By prioritizing cybersecurity, implementing best practices, and fostering a culture of vigilance, the healthcare sector can better protect patient privacy and secure its critical infrastructure from future cyber-attacks.
About Foresiet!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


July 10, 2025, 9 a.m.
