Cl0p Ransomware’s Reign of Cyber Extortion: Analyzing the Recent Cleo Software Exploits

Introduction
In the context of ongoing cyber risk assessment , ransomware is one of the most commercial and destructive forms of cybercrime. Amidst the ocean of crime groups within cyberspace, the Cl0p ransomware syndicate is one of the more refined and persistent threats. This group of cyber-thieves has made notorious headlines with aggressive forms of extortion and campaigns. Once again, in the recent attacks on Cleo software, this in itself reflects the catastrophic impact of unpatched vulnerabilities and the importance of proactive vendor risk management in combination with cyber-exposure assessment is critical.
In this article, you will find the anatomy details of the vulnerabilities exploited in the Cleo software by the Cl0p ransomware, as well as impacts from their current campaign. Armed with an understanding of how Cl0p works, which industries it targets, and vulnerabilities such as CVE-2024-50623, we hope to better arm organizations with practical steps in the direction of strengthening their defenses against this very strong opponent.
Executive Summary
The most recent campaign of the group exploits vulnerabilities in Cleo's software suite, especially Cleo Harmony, VLTrader, and LexiCom. The critical flaw identified is CVE-2024-50623, which includes unrestricted file upload and download with the capability of remote code execution. This vulnerability has allowed Cl0p to compromise the data of 62 companies, an unconfirmed total that may run into hundreds more.
From its dark website, Cl0p published an excerpted, redacted list of the compromised organizations with an ultimatum addressed to its victims, so it seems to rely greatly on both psychological and technical forces. It's a challenge in the case of zero-day exploits in coordinated mass attacks for which the organization would have to rely heavily on the practices of vulnerability management and incident response.
Key takeaways from the recent activity of Cl0p:
- Exploitation of Cleo Software: They used the vulnerability that Cl0p CVE-2024-50623 had made available to target hundreds of worldwide businesses that deployed Cleo's file transfer solution, resulting in massive exfiltrations of data and service outages.
- Victim Profile: Given the number of known victims that the gang has chosen to target, there is an assumption that it will be targeting some high-value information. For example, Cl0p has some of the big Fortune 500 companies and in some ways, educational institutions affected.
- Escalating Tactics: Cl0p could still use CVE-2024-55956 combined with the exploiting of vulnerabilities from Cleo and amplify the attack vector and even sophistication.
- Global Impact: More than 4,000 organizations use Cleo software. That alone speaks volumes about the amplitude of the attack and the complexity involved in the supply chain today.
The rest of this blog is a comprehensive examination of Cl0p's ransomware operations, technical details of the vulnerabilities exploited, and strategic measures that organizations can take to further mitigate risks associated with such attacks.
What is Cl0p Ransomware?
Cl0p ransomware, also known as "Clop," appeared in February 2019 and gained notoriety very fast. Considered the heir to the CryptoMix ransomware family, now one of the most-feared groups of ransomware due to high-value network accesses and massive breaches of data that can be pulled out. Also, unlike every other type of ransomware that only encrypts files, this particular ransomware, Cl0p, exfiltrates them- using the latter for leverage before extorting victims.
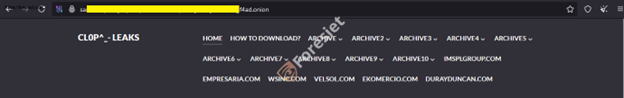
cl0p ransomware darkweb leak site
This is a ransomware-as-a-service (RaaS) group operating in an affiliate structure. The affiliate groups carry out the attacks, while the core groups only provide the malware and infrastructure. It focuses on industries such as retail, health care, finance, transport, and other domains, which choose sensitive or critical data from respective organizations.
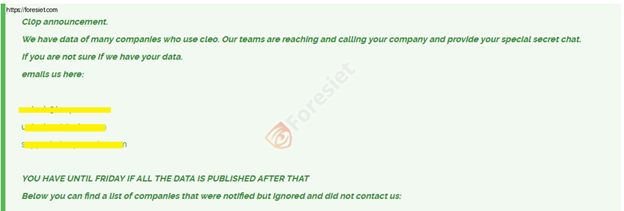
cl0p ransomware darkweb leak site
They directly contact the victims, warn them, and they have an active leak website where they publish data of non-compliant victims.
Core Cl0p ransomware characteristics are:
- Double Extortion: Encrypting data while also threatening to release stolen data publicly.
- Targeted Campaigns: Prioritizing organizations with high-value data and weak security measures.
- Sophisticated Exploits: Leveraging zero-day vulnerabilities and advanced evasion techniques.
CVE-2024-50623 and CVE-2024-55956 exploited vulnerabilities in the Cleo Product
The two vulnerabilities are CVE-2024-50623 and CVE-2024-55956 which hackers had exploited to infiltrate the software of Cleo and therefore conducted the recent attacks by Cl0p ransomware.
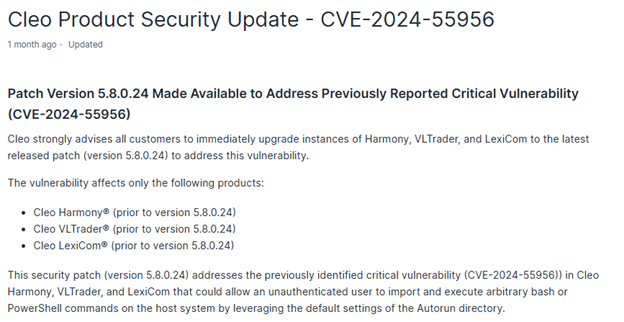
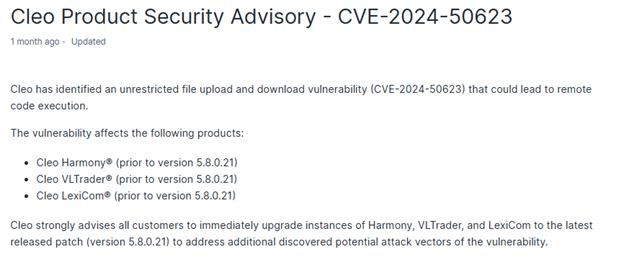
The two critical vulnerabilities discovered had posed and awarded the attackers with the capability of running distant code and unauthorized command executions with Cleo Harmony, VLTrader, and LexiCom. Such vulnerabilities should be known by an organization and their impacts to make it safe in its systems.
Cl0p Ransomware Operations in 2025
Cl0p ransomware was aggressive throughout 2025 by exploiting several software vulnerabilities, including products from Cleo. This group has caused significant data breaches that extort over $500 million from organizations while being quite high profile in the ransomware world.
The newly launched campaign plays on the weak points of the software suite, focusing on Cleo Harmony, VLTrader, and LexiCom. Most undeniably, they will take this type of zero-day, namely CVE-2024-50623, and therefore will be able to remotely execute code that would extract every piece of sensitive information stored within any compromised organization and disturb operations already in progress. Because of these attributes, and much more importantly, having a very great potential to generate revenue, this ransomware gang solidified itself at the very top in elite-class ransomware environments of excellent quality.
Attack Mitigation Strategies
In all such attacks by Cl0p distributed, businesses must take the prime responsibility to maintain a depth defense system that includes the following leading defense techniques-
- Patch Management: One of Cleo's solution products, the application software to be updated into its recent version in the class, including closing identified vulnerability at CVE-2024-50623.
- Backup and Recovery: The routine backup of important data should always be kept in an offline source to recover fast, without being deceived by the ransom demands.
- Network Segmentation: The spread of ransomware can be controlled using network segmentation alongside restricting access towards sensitive systems.
- Endpoint Detection and Response (EDR): ED Advanced tools that monitor and respond in real-time to all suspicious activities
- Security Awareness Training: Train the employees on how to stay away from phishing attempts and all the other commonly used entry points by ransomware
- Zero Trust Architecture: The security model uses the verify-all-users-and-devices model to access any resources.
Conclusion
The recent attacks of Cleo software by ransomware group Cl0p remind all about the dangers of volatility within the cyber threat landscape as well as ransomware groups being persistent threats, proving technical brilliance and flexibility. It has exposed vulnerabilities such as CVE-2024-50623, exploiting both psychological and technological pressures against victims in every corner of the globe.
For organizations, the lessons from these attacks are clear:
- Proactive Vulnerability Management: Organizations should have policies for the implementation of punctual patches about vulnerabilities; in line, prioritized scan tools for the adoption of updated vulnerabilities must be developed such that minimum exposure happens.
- Incident Response Planning: The better developed and practiced an incident response plan is; the lesser the ransomware attacks the lesser damage caused thereby.
- Cybersecurity Awareness: It reduces the initial compromise chances in terms of employee training for phishing detection and other ransomware entry points.
- Zero Trust Architecture: It prevents attackers from having lateral movement, hence protecting the most critical assets with a Zero Trust security model.
The Cl0p ransomware group is becoming more aggressive and expansive in their attacks. Organizations must remain vigilant of this increasing threat and improve technological defense as well as organizational resilience against these looming threats. There is a pervasive form of ransomware that endangers the ransomware threat and needs to be diminished by best practices shared amongst themselves.
Through collective action, an organization can deflect not only the ransomware campaign but also contribute towards making the digital world a better place for all of us. Let this be a call to action towards improving the cybersecurity of an increasingly connected world.
About us!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


July 10, 2025, 9 a.m.
