CVE-2025-24085: The iOS Zero-Day Exploit Selling on the Dark Web
Introduction
A newly discovered zero-day vulnerability, CVE-2025-24085 is a use-after-free vulnerability affecting Apple products, including iOS and macOS. It has been addressed in updates such as iOS 18.3 and macOS Sequoia 15.3 has emerged on the dark web and poses a severe security risk to Apple users. The exploit reportedly sells for 0.00254009 BTC ($233.09 USD) and enables attackers to escalate privileges within iOS devices. Researchers confirm that the vulnerability has been actively exploited in the wild. As Apple scrambles to patch the flaw, cybercriminals continue to exploit it for illicit gains.
In this blog, we discuss the inner workings of CVE-2025-24085, how it works, the impact it bears, Apple's response, and some suggested mitigation strategies.
The Dark Web Sale: CVE-2025-24085 Leaked
Recent intelligence from dark web marketplaces reveals that CVE-2025-24085 is being sold openly with the following details:
- Price: 0.00254009 BTC (~$233.09 USD)
- Sale Count: Unlimited
- Files Included:
- other.zip (3720.25KB) – Contains exploit-related data
- proof.mp4 (30250.52KB) – Demonstrates exploit in action
- README.txt (0.37KB) – Instructions by the seller
Affected Products:
- iOS 18.3
- iPadOS 18.3
- macOS Sequoia 15.3
- watchOS 11.3
- tvOS 18.3
- visionOS 2.3
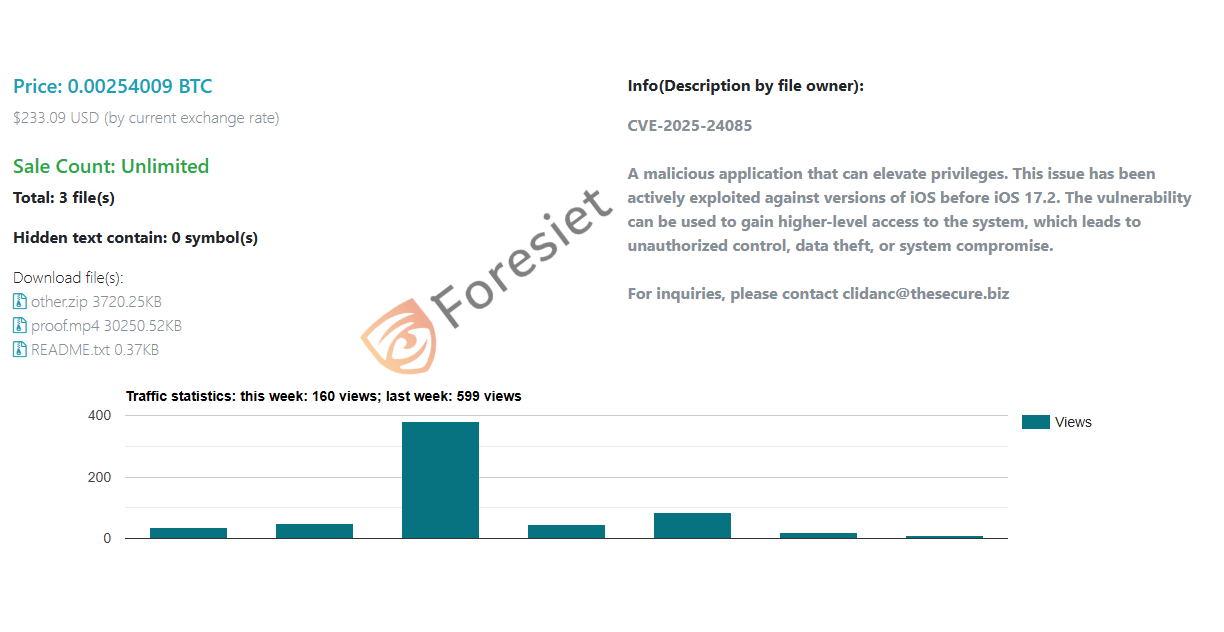
The seller’s description states:
“A malicious application that can elevate privileges. This issue has been actively exploited against versions of iOS before iOS 17.2. The vulnerability can be used to gain higher-level access to the system, which leads to unauthorized control, data theft, or system compromise.”
How CVE-2025-24085 Works
CVE-2025-24085 exploits a memory management flaw in Apple’s Core Media framework, a crucial component that processes audio, video, and other media content.
Exploitation Mechanism
This attack exploits memory corruption in the Core Media area. The malware will be given a chance to alter memory space and thus hamper normal runtime behavior. Subsequently, for privilege escalation purposes, the injection of malicious code into a flawed process will achieve unauthorized access by the attacker onto the system, culminating at the kernel exploit phase, that enables arbitrary execution within the ios kernel. In doing so, the exploit circumvents critical security mechanisms such as Sandboxing and Code Signing to allow full control over the compromised device.
Attack Chain
The attack begins with the deployment phase, which delivers a malicious app or an infected media file to the victim. Once the victim opens the file or launches the app, the execution phase is triggered, exploiting a memory corruption vulnerability in Core Media. This leads to privilege elevation, allowing the attacker to gain root-level access and take full control of the device. To maintain and grant continued access, the attacker installs a backdoor that provides long-term monitoring, data exfiltration, and manipulation of system functions without detection.
Potential Risks
The exploit allows for remote take-over so that hackers can assume control of the compromised device from anywhere. After establishing a foothold, the attacker can carry out data theft, hence putting a client's personal files, banking credentials, and passwords at serious risk. Spyware deployment might be carried out to continue with surveillance.
The exploit also bypasses security measures, and standard protections like Face ID, Touch ID, and Secure Enclave are compromised, leaving the device and its data open to further exploitation.
Apple’s Response
Apple has acknowledged the existence of CVE-2025-24085 and is working on a patch. In a statement, Apple said:
“We are aware of reports regarding CVE-2025-24085 and are actively investigating the issue. The security and privacy of our users are our top priorities, and we will release a software update to address this vulnerability as soon as possible.”
Apple has also advised users to:
- Avoid installing untrusted kernel extensions.
- Enable Lockdown Mode on iOS devices to reduce the attack surface.
- Regularly update their devices to the latest software versions.
The company has acknowledged CVE-2025-24085 and issued security updates throughout its ecosystem to patch the vulnerability. The recent patches resolve the issue with Core Media memory corruption, which cyber hackers could exploit to carry out attacks. Specifically, for iPhones and iPads, iOS 18.3 and iPadOS 18.3 patch this flaw; whereas macOS devices are covered by macOS Sequoia 15.3. Finally, Apple bolstered protection extended its range of platforms to watchOS 11.3, visionOS 2.3, and tvOS 18.3, protecting the devices involved.
Apple recommends users immediately update their devices to the latest versions to prevent exploitation.
Mitigation Strategies
Users should take several key security measures to protect against CVE-2025-24085. First, it is essential to update immediately to the latest iOS, macOS, or watchOS version to ensure that your device has the most recent security patches. Secondly, users should disable untrusted media handling by avoiding the opening of unknown or unverified media files that may contain exploits.
Apps also have to be downloaded from credible sources, specifically the App Store. The activities on the devices must be watched out for since it will react to such malware if infection begins, usually characterized by unusual heating or random draining of batteries. Last, there are some security tools: endpoint protection, which guards all data; anti-exploit, preventing malicious threats and infections.
Conclusion
The critical zero-day vulnerability CVE-2025-24085 has already been weaponized by cybercriminals. The sale of the exploit on the dark web only proves that there are still constant threats targeting Apple users. Even though Apple responded with security patches, the devices remain unpatched and still at risk. Updating devices, being cautious about downloads, and monitoring for suspicious activity can help users mitigate risks associated with this vulnerability.
Source:
About us!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


July 10, 2025, 9 a.m.
