Dark Storm Team: The Hacker Group Behind the DDoS Attack on X (Twitter)

Executive Summary
On March 10, 2025, X (formerly Twitter) experienced a series of outages due to a large-scale Distributed Denial of Service (DDoS) attack. The platform went down multiple times throughout the day, affecting millions of users globally. Elon Musk later confirmed that X was targeted by a "massive cyberattack", with initial investigations pointing to Ukraine-based IP addresses as the source.
Amidst the chaos, a group called Dark Storm Team claimed responsibility for the attack via Telegram. This group has been active since early 2023, engaging in hacktivism, cyberattacks, and now, cryptocurrency promotion. Interestingly, at the same time as the attack, Dark Storm Team was promoting its own cryptocurrency, DARKSTORM/SOL, leading many to question their true motives.
This blog explores:
- The DDoS attack on X and its impact.
- Who is Dark Storm Team?
- The link between cyberattacks and crypto scams.
- Elon Musk’s response and the ongoing investigation.
The DDoS Attack That Brought X (Twitter) Down
Timeline of the Attack
On March 10, 2025, X suffered four major outages at:
- 5:30 AM ET
- 9:30 AM ET
- 11:15 AM ET
- 1:15 PM ET
Who Is Dark Storm Team?
Dark Storm Team first appeared in 2023 as a hacktivist collective, mainly targeting government and corporate websites. They have been linked to pro-Palestinian cyber campaigns, defacing sites with political messages. However, their recent activities suggest a shift from hacktivism to cybercrime.
Known Activities
- Website defacement campaigns (2023)
- DDoS attacks on media platforms (late 2023 - early 2024)
- Telegram recruitment of hackers & botnet operators
- Promotion of a cryptocurrency token (DARKSTORM/SOL)
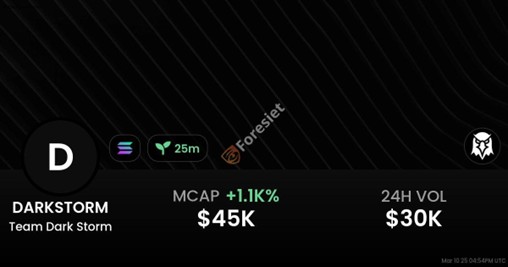
This last point is crucial—Dark Storm Team has begun promoting their own cryptocurrency on the Solana blockchain. The timing of the X attack coinciding with their token launch suggests a coordinated attempt to generate hype and financial gain.
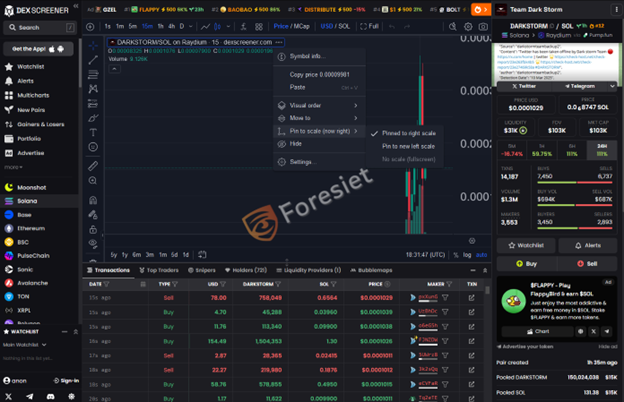
DarkStorm/SOL: A Crypto Pump-and-Dump?
While analyzing a DexScreener listing, it was evident that DarkStorm/SOL was being actively traded. The token showed suspicious trading activity, with sudden price spikes and dumps—common characteristics of a pump-and-dump scam.
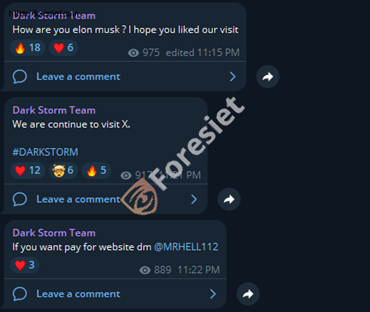
The Dark Storm Team Telegram included a link to this token, claiming it was their "official" cryptocurrency. Given their history, this raise concerns that:
- They are using cyberattacks to create artificial hype.
- They may be planning to dump the token after inflating its value.
- They could be laundering money through crypto.
Cyberattacks and Cryptocurrency: The Growing Link
This isn’t the first time hackers have used cyberattacks to boost a cryptocurrency’s value. Several cybercriminal groups have used this tactic:
- Lazarus Group (North Korea) launched malware campaigns to steal cryptocurrency.
- Anonymous Sudan has conducted DDoS attacks while promoting fundraising in crypto.
- Killnet (Russian hacktivist group) has accepted payments in crypto for “cyber services.”
- Dark Storm Team may be following a similar business model —attacking high-profile platforms like X while simultaneously pushing their cryptocurrency.
How Crypto Scams Are Evolving
- Fake "hacktivist" branding – Groups claim to be ideological but are profit-driven.
- Manipulation of token prices – Cyberattacks create media attention, leading to artificial spikes.
- Scamming their own followers – Many who buy into the hype may be left with worthless tokens.
Our Security experts have warned against investing in any tokens linked to Dark Storm Team, as there is a high probability of fraud.
Elon Musk’s Response and the Investigation
What Elon Musk Said
Elon Musk took to X after the attack and stated:
“We traced the attack to IP addresses originating from Ukraine. However, we are investigating further to confirm the true source.”
This statement has sparked geopolitical speculation, with some wondering if:
- The attack is linked to a state-sponsored group.
- Dark Storm Team is operating from Ukraine, or if they are using VPNs and proxies to mask their real location.
X’s Security Measures Moving Forward
X has since implemented:
- Stronger bot detection systems
- IP filtering and geolocation restrictions
- Enhanced DDoS mitigation strategies
However, our experts believe this won’t be the last attack from Dark Storm Team. The group has already stated that they will continue targeting major platforms.
Dark Storm Team’s Real Intentions
The DDoS attack on X was not just a random act of hacktivism. Instead, it appears to be a coordinated campaign for financial gain—leveraging high-profile attacks to promote a questionable cryptocurrency.
The Dark Storm Team has claimed responsibility for the attack on X, with their IP addresses tracing back to Ukraine, though the true origin remains unverified. They are also promoting a cryptocurrency called DARKSTORM/SOL, which raises concerns of a potential scam. Elon Musk confirmed that the attack was “massive” and well-coordinated. In response, X is implementing new security measures, but there are warnings that more attacks could follow.
About us!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


July 10, 2025, 9 a.m.
