Global IT Outage: CrowdStrike Falcon Sensor Update Mishap and Resulting Cyber Threats

Overview
On July 19, 2024, a botched CrowdStrike Falcon sensor update for Windows operating systems led to the largest IT outage in recent history. Although the issue stemmed from a technical malfunction, it inadvertently opened the door for real threat actors to exploit the situation. This incident has triggered a wave of malicious activities, particularly targeting CrowdStrike’s Latin American (LATAM) customers.
The Incident
CrowdStrike's flawed update caused the infamous Blue Screen of Death (BSOD) on millions of Windows computers worldwide, resulting in total system crashes. The impact was severe, disrupting businesses, airports, train stations, banks, broadcasters, and the healthcare sector on a global scale. This chaos created an ideal environment for cybercriminals to launch phishing attacks and create malicious domains disguised as fixes for the BSOD issue.
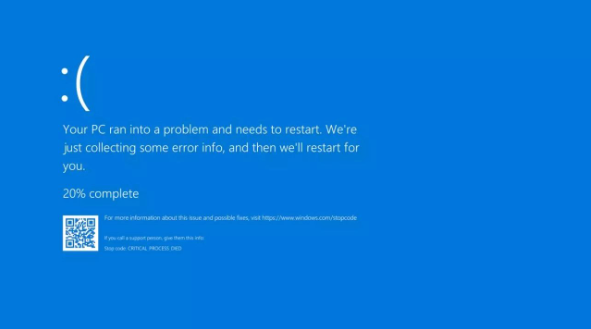
Blue Screen of Death (BSOD)
Exploitation by Cybercriminals
In the wake of the disruption, cybersecurity firm CrowdStrike reported that threat actors were leveraging the situation to distribute Remcos RAT (Remote Access Trojan) to their customers in Latin America. The attackers posed as CrowdStrike, providing a fake hotfix to address the issue.
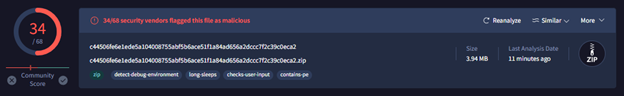
The Zip file flaged by online malware scanner
The attack method involved distributing a ZIP archive named "crowdstrike-hotfix.zip" which contained a malware loader known as Hijack Loader (also referred to as DOILoader or IDAT Loader). This loader, when executed, would deploy the Remcos RAT payload.
The ZIP file (SHA256 hash: c44506fe6e1ede5a104008755abf5b6ace51f1a84ad656a2dccc7f2c39c0eca2) was uploaded to an online malware-scanning service by a submitter based in Mexico.
The instructions within the archive posed as a utility to automate the recovery process from the content update issue, misleading users into running the malicious "Setup.exe" (SHA256 hash: 5ae3838d77c2102766538f783d0a4b4205e7d2cdba4e0ad2ab332dc8ab32fea9).
Targeted Campaign in LATAM
The ZIP archive included a text file ("instrucciones.txt") with Spanish-language instructions, urging targets to run an executable file ("setup.exe") to resolve the issue. The use of Spanish filenames and instructions indicated that this campaign was likely aimed at Latin American CrowdStrike customers.

Content of instrucciones.txt
Symptoms and Impact
- Symptoms: Hosts experiencing a bugcheck/blue screen error related to the Falcon Sensor.
- Unaffected Systems:
- Windows hosts not impacted by the update do not require any action.
- Windows hosts brought online after 0527 UTC are not affected.
- Hosts running Windows 7/2008 R2 are not impacted.
- Mac- or Linux-based hosts are not impacted.
- Channel File Details:
- The reverted (good) version: "C-00000291*.sys" with a timestamp of 0527 UTC or later.
- The problematic version:"C-00000291.sys" with a timestamp of 0409 UTC.
Workaround Steps to Fix CrowdStrike Bug
For Individual Hosts:
- Reboot the host to allow it to download the reverted channel file.
- If the host crashes again:
- Boot Windows into Safe Mode or the Windows Recovery Environment.
- (Optional) Use a wired network and Safe Mode with Networking for better remediation.
- Navigate to the %WINDIR%\System32\drivers\CrowdStrike directory.
- Locate and delete the file matching “C-00000291*.sys”.
- Boot the host normally.
- Note: Bitlocker-encrypted hosts may require a recovery key.
For Public Cloud or Similar Environments Including Virtual:
- Option 1:
- Detach the operating system disk volume from the impacted virtual server.
- Create a snapshot or backup of the disk volume as a precaution.
- Attach/mount the volume to a new virtual server.
- Navigate to the %WINDIR%\System32\drivers\CrowdStrike directory.
- Locate and delete the file matching “C-00000291*.sys”.
- Detach the volume from the new virtual server.
- Reattach the fixed volume to the impacted virtual server.
- Option 2:
- Roll back to a snapshot before 0409 UTC.
Analysis of Malicious Domains
In the aftermath of the CrowdStrike incident, threat actors took advantage of the confusion by creating fake domains to trick users into visiting malicious sites. These fake domains were designed to mimic legitimate fix pages and were used to distribute malware.
The attackers also posted fake contact numbers to scam users further. Screenshots of these malicious domains are included for reference.
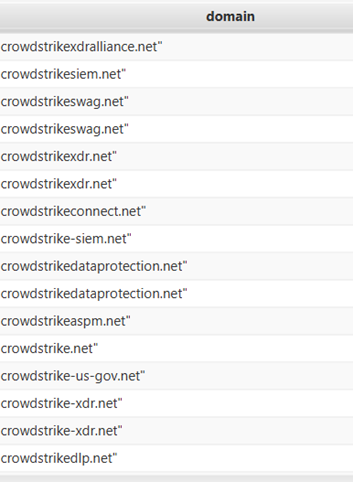
Image 1 showing fake domains
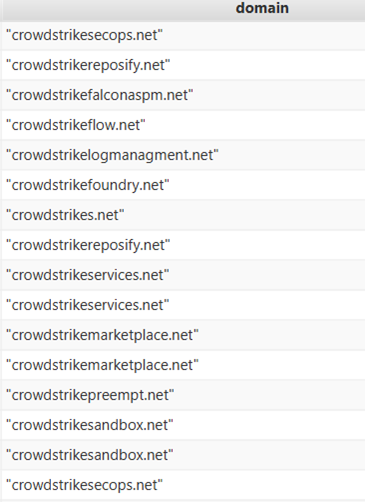
Image 2 showing fake domains
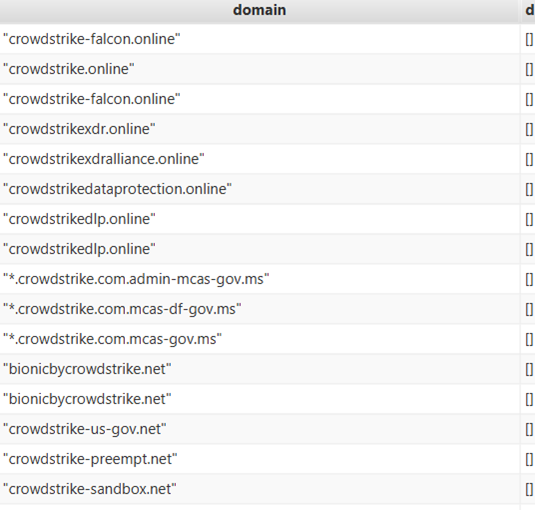
Image 3 showing fake domains
What We Can Learn From This Incident
This unfortunate event serves as a learning moment for everyone, especially businesses and tech companies. Here are a few takeaways:
- The Importance of Robust Testing: Before rolling out updates, thorough testing can prevent widespread issues—something we all hope for.
- Cybersecurity Awareness: Regular training for employees on recognizing phishing attempts and secure practices can make a significant difference.
- Clear Communication: During incidents, timely communication from companies about what is happening can help mitigate panic and misinformation.
It’s almost like a reminder of that age-old saying, “better safe than sorry.” We should prioritize being informed and prepared, especially in this digital age where technology plays such a critical role in our lives.
The impact of CrowdStrike’s botched update was felt far and wide, illustrating not only the fragility of our reliance on technology but also how swiftly cybercriminals can take advantage of chaos.
Let’s keep the conversation going—what steps do you think we should take to improve our response to such incidents? Experiences on how to avoid falling prey to malicious schemes could help us all stay safer in our digital lives! Remember, staying informed is your best defense.
About us!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


July 10, 2025, 9 a.m.
