HTML Smuggling - An Old Technique with New Tricks

Since the inception of the internet and the World Wide Web (WWW), HTML has been a fundamental part of digital communication, enabling document exchange services between various devices on the network. Developed by Tim Berners-Lee, the father of the WWW, in 1993, the markup language is still used to display documents on web browsers today. Despite undergoing significant version upgrades over the last three decades, with HTML5 being the latest version recommended by the World Wide Web Consortium (W3C), the language has specific characteristics that allow attackers to exploit loopholes and compromise systems. This article delves into one such exploit: HTML Smuggling, and malware that utilizes it.
Before delving into HTML Smuggling, it is important to grasp the concept of JavaScript "blobs". Blobs are an object that contains unchangeable, raw data arranged in a format comparable to a file. These byte collections are stored in the user's memory and function in the same way as files. Consequently, they can be saved in memory as files and utilized to construct file-like objects on the client-side that can be passed to JavaScript APIs requiring URLs.
The utilization of the blob object is a key component in HTML Smuggling attacks. These attacks involve the insertion of attacker payloads, containing malicious code, into the blob object, which is subsequently decoded into an object once accessed by the victim through their web browser. The attacker exploits the flexible nature of HTML5 and JavaScript to store and execute the payload on the victim's system. HTML5 anchor tags with a "download" attribute and JS blobs are used to modify and embed the payload on the victim's system.
Uploading malware onto the victim’s system is the ultimate goal of the attacker. There are many different methods the attacker can use to upload the malware, of which HTML Smuggling is one of them. This method isn’t new, as it has been known for a long while now. The reason this method isn’t very popular until now is because there are easier, more successful methods of malware transmission attacks such as through default macros on Windows. Microsoft however has been disabling default macros on web-based documents to prevent such attacks, resulting in a renewed focus on HTML Smuggling as an attack vector to carry out malware upload.
When malware is decoded and primed on the victim's system, it becomes capable of evading detection by firewalls and antivirus software that typically search for unusual formats like docx, exe or zip files and compare their signatures to identify malware. JavaScript blobs enable the creation of objects directly on the client, causing the payload to be automatically generated as soon as the HTML page loads on the web browser.
It is worth noting that when utilizing JavaScript blobs, the downloaded file will not be associated with any URL since the payload is dismantled on the victim's system.
Here is an example code snippet demonstrating how a JavaScript blob object can embed a malicious program within the code:
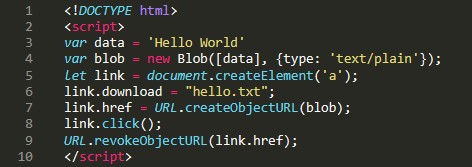
In this code snippet, the payload data is stored in a variable called data and is embedded into a blob object as plain text in the second line. The third line creates an anchor element that links the JavaScript code to the HTML page. The link variable is then used to trigger the automatic download of the file to the web browser.
To create a URL to the blob function, createObjectURL() is called with the blob object as an argument. Once the URL is created, the click() function is used to simulate a click on the anchor object, which executes the anchor tag and immediately constructs the payload.txt file as soon as the webpage loads. Finally, revokeObjectURL() is used to destroy any references to the URL so that any evidence of what is happening is hidden.
The image below illustrates how the text file is downloaded automatically upon loading the webpage.
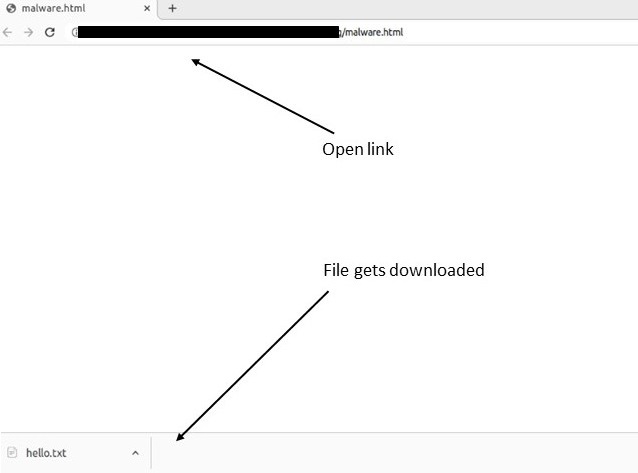
The code example above is a simple demonstration of how HTML Smuggling can be exploited by malware. Typically, malware payloads are more complex and often encrypted using algorithms such as Base64 to avoid detection by firewalls and antivirus software.
Here is a flowchart depicting the process of HTML Smuggling:
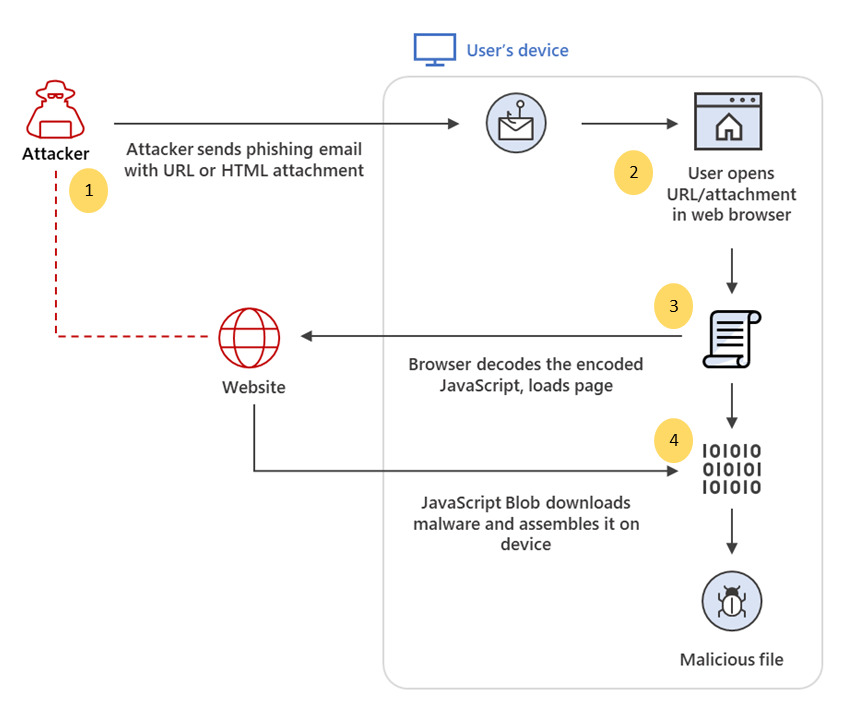
QakBot
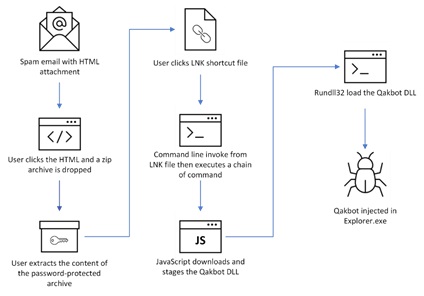
QakBot is a malware that employs HTML Smuggling as a means of dissemination and is one of the most prevalent and powerful malware types in existence today. This malware has been utilized in email phishing and social engineering attacks on unsuspecting victims to spread and steal data since last year. Due to Microsoft's crackdown on default macros, QakBots have shifted from exploiting macros to using HTML Smuggling to spread.
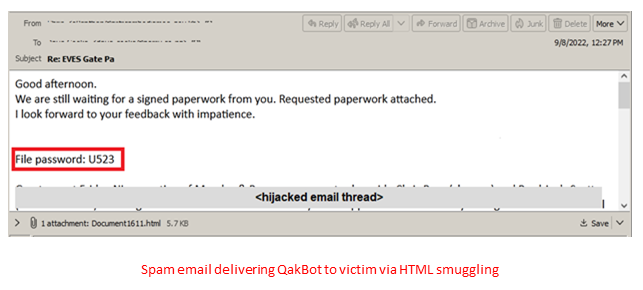
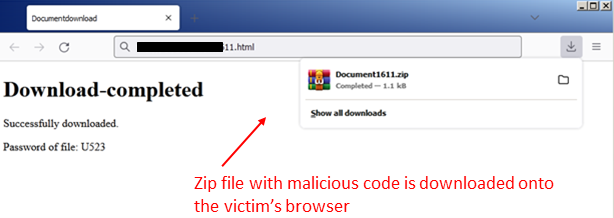
Since the fourth quarter of 2022, there have been repeated campaigns by foreign state and non-state actors to clone and impersonate well-known software companies and products such as Dropbox and Google Drive. The goal is to conceal their downloads and compromise victims' computer systems by stealing their data and monitoring their activities. Email has been the preferred method of propagation, as mass spam emails with dubious links and attractive styling have led victims to click on links promising material gains, discounts from the clone's websites, or fake bank emails regarding fee dues. Clicking on these links results in the download of zip files onto their systems and triggers the blob() function to automatically unload its contents.
The diagram below illustrates the propagation and compromise of QakBot on its victims:

Protecting against HTML Smuggling:
As HTML Smuggling utilizes HTML5 and JavaScript attributes, the most sure-fire way to prevent is by disabling JavaScript on the web browser, as JS blobs are used to embed and transport malicious code to the victim’s browser. This, however, is easier said than done as most of the websites today require JS to process their business logic and perform computation during the interactions between the server and web browser.
Traditional defence methods are insufficient to protect potential victims from these attacks. A well-structured, multi-layered, and resilient defence strategy with high heuristic and processing capabilities is necessary to detect and prevent these attacks on time. One way to thwart such attacks is to utilize malware detectors that contain well-trained machine learning models capable of detecting multiple types of malwares, including QakBots. Additionally, strengthening API endpoints, improving protection against phishing attacks, and employing cloud protection software are necessary to prevent the spread of malware and viruses.
Conclusion
This article has demonstrated that HTML Smuggling is an exploit that can occur even in systems equipped with the most advanced antivirus software. The recent increase in the exploitation of this vulnerability is alarming, and we can anticipate the creation and spread of more sophisticated and resilient malware that will challenge the efficacy of existing security frameworks. Foresiet would like to remind its readers and clients to remain vigilant and report any suspicious activity to the relevant authorities.
The following list provides information on the indicators of compromise associated with QakBot malware:
| Indicator Type | Indicators |
| domain | purepowerinc.net |
| domain | huhuwarcanoefestival.com |
| IPv4 | 165.22.48.183 |
| SHA256 | 3acac1bb2a028372aad7f36510028823a36c5d63eeb3a72e0c5804adec204fce |
| SHA1 | fbc916f065157cc5a13f22453c19f7dfecc3c228 |
| SHA1 | efd195d8ef795e123bb1c1faee77459a781c003e |
| SHA1 | ed67cb8a6c44871ec6ffb6517d77b5e84f00b399 |
| SHA1 | e318c01fcd1f711fd063e845ca2431012086658f |
| SHA1 | df3f2f97383d4ae897b3197e8d07f474f651a053 |
| SHA1 | d92b31ddf25e30e7cc34239bf45c7ec913b713c4 |
About Foresiet!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


July 10, 2025, 9 a.m.
