Inside the Belsen Group Attack: 15000 FortiGate VPN Credentials and Configurations Exposed

Introduction
It was in January 2025 when a disaster leakage of data was leaked having more than 15,000 configuration files carrying VPN credentials leaked from FortiGate devices spread on several devices. It depicts acute problems inside organizations using the products by Fortinet about a higher need for an excellent security approach. The Belsen Group, the hacking collective carried out this attack by taking advantage of the zero-day vulnerability known as CVE-2022-40684. The product that was attacked had evil access and made use of its resources. Read on to find more information on this one breach which suggests that the data from where organizations must take lessons will not reach such a stage in the future soon.
The Breach: Key Details
Vulnerability Exploited
This critical flaw was CVE-2022-40684 in Fortinet's systems. The flaw was published in October 2022 and relates to bypassing administrative authentication by using specially crafted HTTP or HTTPS requests. With a CVSS score of 9.8, the vulnerability has therefore remained highly critical to attackers.
Timeline of the Attack
The leak started sometime at the end of 2022 when Belsen Group exploited the vulnerability to steal configuration files as well as VPN credentials. The exfiltrated data has so far only come into the public domain during January 2025, which translates into a pretty long lag between data theft and coming into public purview. This would prolong the vulnerability windows not only to the organizations but also to much more extensive ones where the attackers will sell their stolen data.
Data Leaked
The exposed data consists of:
- Over 15,000 unique FortiGate firewall configurations.
- Credentials that contain some readable passwords.
- Certificates issued for device management.
- Firewall rule configurations are highly large. These were highly categorized by country and had sensitive files like config.conf and VPN-passwords.txt. They carry network configuration, security policy, and VPN-related credentials; therefore, gold for these thieves.
Attackers: The Belsen Group
The Belsen Group took responsibility for the attack, labelling it as the largest operation the group ever handled. This very sophisticated group leveraged this zero-day vulnerability for unauthorized access to thousands of FortiGate devices.
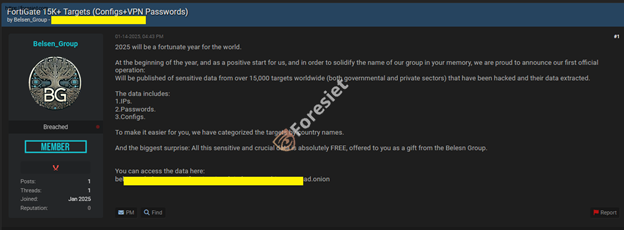
The Belsen Group claimed responsibility for the breach on a dark web forum.
While exploiting the critical flaw, the hacking group showed how unpatched vulnerabilities could cause catastrophic damage to systems usually utilized by everybody.
Anatomy of the Breach
Exploiting CVE-2022-40684
Exploit vulnerability The Belsen group used CVE 2022 40684 in which they bypassed authentication credentials in an administrative position. Each of the above requests targeted Fortinet appliances both HTTP and also HTTPS was fashioned by attackers just to bypass Fortinet appliance's authentication. Indeed, such exploitation poses that remedial mitigation to such fundamental infrastructure must happen quickly.
Data Organization
It arranged the siphoned data systematically based on countries and IP addresses. For instance, each folder had files named config.conf, VPN-passwords.txt, and so on, all holding network configuration information containing sensitive details about the VPN. Such organized structuring indicates a very obvious effort towards extracting maximum usability of the data either for further sales or exploitation.
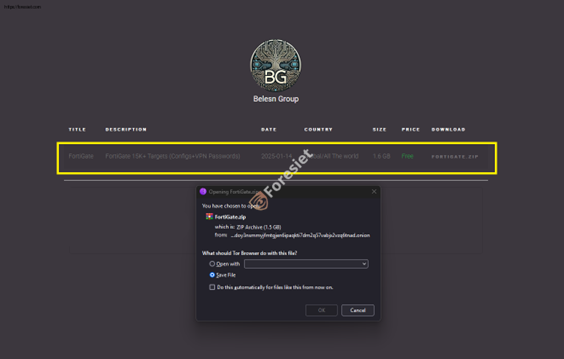
The group hosted the stolen data on an onion site for dark web download.
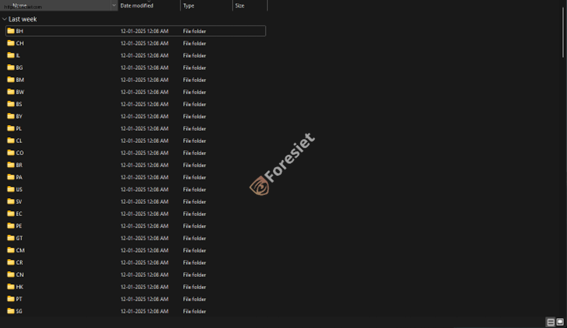
The leaked data was organized by country, with folders for specific regions.
The exfiltrated data was distributed into the countries, but there were regional folders. Each country folder was divided into various IP addresses holding sensitive files. For instance, files that carried VPN information and configuration settings.
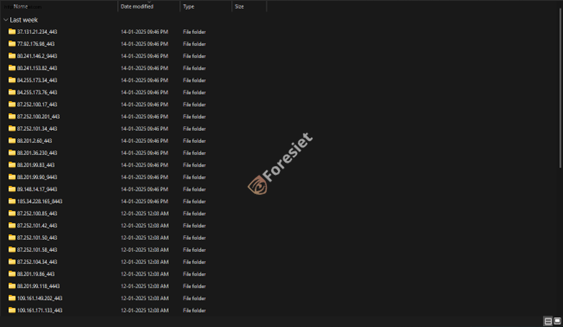
Country folders contained subfolders by IP with sensitive files like VPN credentials.
Tools and Scripts
The attackers used specific scripts for organizing and processing the stolen information. For example, one leaked archive contained a Python script that seemed to rename and manipulate password files. The script itself is harmless but indicates how the attackers sorted out the data that was stolen.
Implications of the Breach
Security Vulnerabilities
Severe security vulnerabilities are exposed by the hack because the FortiGate configurations and credentials are leaked. The plaintext VPN credentials can be used for unauthorized access to networks, and the firewall rules provided give far too detailed a map of one's target network architecture. Leaked management certificates for devices can be used for man-in-the-middle attacks or impersonation, further compromising network integrity and user trust. IP folders - included vpn-passwords.txt, config.conf amongst others that had VPN credentials and the device configs.
IP folders exposed VPN credentials and device configs
Reputational Damage
Organizations impacted by the breach are at risk of reputational damage, particularly if the leaked data is used in subsequent attacks. Such incidents can erode client and partner confidence in the organization’s ability to protect sensitive information, potentially damaging long-term relationships and brand credibility.
Financial Consequences
The breach will lead to significant financial losses. Organizations breached are going to face huge amounts paid in fines on account of their violation of pertinent data protection legislation, incur enormous expenses of the response and the restoration of incidents and ultimately become defendants in cases filed by the interested parties to obtain loss compensation in damages sustained.
Lessons Learned
Patch Management
This is a classic example of how patch management is a critical aspect of cybersecurity. Organizations should therefore scan for vulnerability disclosures regularly and patch accordingly to close emerging threats. Routine vulnerability assessment is also crucial to identify and remediate unpatched systems and minimize exposure to potential exploits.
Incident Response Planning
Quite incidentally, a good response to the incident will minimize its effects, such as prompt identification and confinement of threats and clear communication about the breach with the stakeholders, while an investigation or forensic analysis is in place to find the extent of the breach and the source. Preparations before incidents can make faster recovery and better resilience against future incidents.
Zero-Trust Security Model
This zero-trust security model will limit the opportunities where an attack is likely to succeed. It will authenticate and authorize users and devices at points of access, maintain least privilege access controls that remove unnecessary permissions and continuously monitor for anomalous network activities. In this environment, where no entity is trustworthy, it will help the organizations protect their sensitive data and systems well.
Call to Action for Affected Organizations
Organizations for whom Fortinet installation gets affected must do the following:
- Upgrade Software: Upgrade all systems as well as equipment with secure, latest editions of the Fortinet Software
- Change Credentials: VPN Login credentials and all Administrator Passwords of every system are to be changed.
- Revoke Certificates: Certificates related to management should be revoked when the device becomes compromised.
- Conduct Security Audits: A Security audit must be done in the entire Systems that are associated with the network.
- Engage Cybersecurity Experts: Engage with cybersecurity experts to drive security high enough that one will never succumb to such hacks.
Conclusion
The Belsen Group had orchestrated the breach of FortiGate, and it becomes a cruel reminder of what an unpatched system has weaknesses in. This is where the hackers, through the exploitation of critical zero-day flaws, demonstrated devastating breaches.
To prevent such incidents in the future, organizations have to take proactive measures toward cyber security, such as timely patch management, proper incident response planning, and the concept of a zero-trust security model. This far-reaching breach spells doom, but it allows organizations to learn better defenses against future threats.
About us!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


July 1, 2025, 7:17 p.m.

July 1, 2025, 7:07 p.m.