Lazarus Group Strikes Again: North Korean Hackers Steal $1.46 Billion in Bybit Crypto Heist

In recent weeks, the cryptocurrency community has been rocked by a series of high-profile thefts, including a $1.46 billion suspicious outflow from Bybit, a $11.5 million Coinbase social engineering scam, and an XRP laundering attempt linked to North Korea. Blockchain investigator ZachXBT has been actively tracking these incidents, mapping the stolen funds' movement across multiple chains.
At the same time, researchers at Foresiet have been closely monitoring ZachXBT’s findings and public discussions Telegram channels, analyzing how these threat actors operate. The evolving situation raises serious questions about exchange security, money laundering tactics, and potential involvement of state-sponsored cybercriminals.
This blog will break down the latest on-chain evidence, laundering techniques, and key players behind these attacks.
Breakdown of Recent Crypto Thefts
Coinbase Social Engineering Attack ($11.5M Stolen) – January 2025
On January 31, 2025, ZachXBT reported that a Coinbase user was social-engineered and scammed for 110 cbBTC (~$11.5M) on Base. The stolen assets were swiftly swapped, bridged, and laundered using multiple instant exchanges, eventually consolidating with funds from other compromised Coinbase accounts.
Transaction Hashes for Theft
- https://basescan.org/tx/0x8639f4b4420d47d68f27dc27967ff62ec913106e5b9ce99011de99b8d91813cd
- https://basescan.org/tx/0xb5895314777776da645529df83cd0d0883ed456e2c81e27c97eb5cf45a59c36b
- https://basescan.org/tx/0xfa26f3917519444c7d3d9ca05fc70b289d44958cb55801b9221d7b492f41c76d
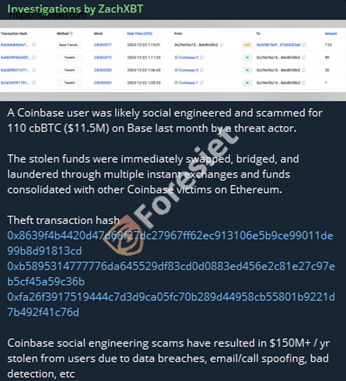
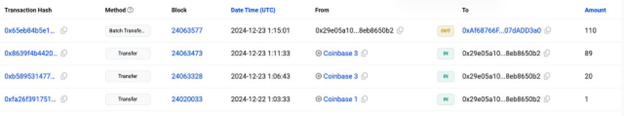
The attacker utilized bridging protocols to obscure the trail of stolen funds, making it difficult to trace their movement. Additionally, the stolen funds were mixed with other Coinbase victim deposits on Ethereum, suggesting a broader campaign specifically targeting users. Notably, blockchain investigator ZachXBT estimates that social engineering scams affecting Coinbase users result in losses exceeding $150 million annually.
North Korean DPRK Hackers’ XRP Transfer Mistake – February 4, 2025
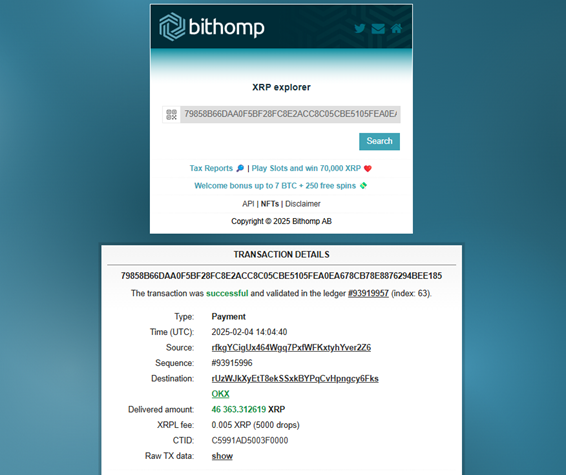
On February 4, 2025, a suspected North Korean state-sponsored hacking group attempted to move 46.3K XRP ($121K) from stolen funds. However, in a major blunder, they forgot to include a destination tag when depositing the XRP to an exchange.
Transaction Hash
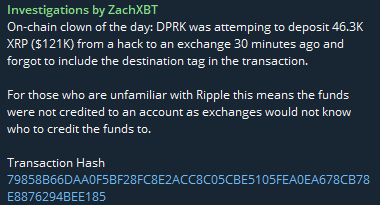
- https://xrplexplorer.com/explorer/79858B66DAA0F5BF28FC8E2ACC8C05CBE5105FEA0EA678CB78E8876294BEE185
Why This Matters
North Korean cybercriminals, specifically the Lazarus Group, have stolen billions from the crypto sector. However, a mistake in their operation prevented the stolen funds from being credited to their intended exchange account. This incident highlights how even elite hacking groups can make critical operational security errors.
Bybit Hack – $1.46 Billion Suspicious Outflows (February 21, 2025)
The most alarming development is the massive $1.46 billion outflow from Bybit, first flagged on February 21, 2025. The stolen assets included mETH & stETH, which were quickly swapped on decentralized exchanges (DEXs) for ETH.
Suspicious Address Linked to the Heist
- 0x47666Fab8bd0Ac7003bce3f5C3585383F09486E2
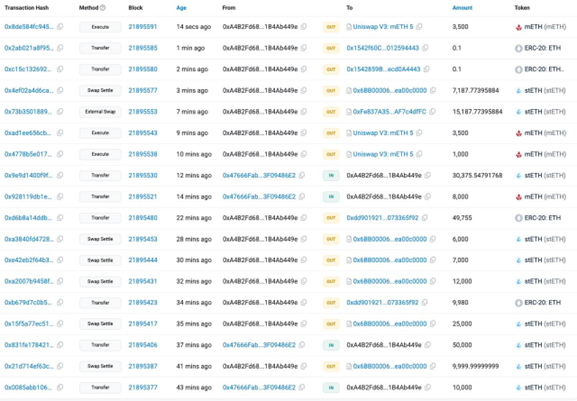
Attacker’s Money Laundering Strategy
The attacker first converted the stolen mETH and stETH into ETH using decentralized exchanges (DEXs). To evade detection, they then split 10,000 ETH across 39 separate wallets. Further obfuscation efforts included additional transactions indicating bridging other chains and laundering through instant exchanges.
ZachXBT has urged exchanges and services to blacklist these addresses across all EVM-compatible chains to prevent further movement of funds.
Who Is Behind the Bybit Hack?
While it's too early to confirm, several indicators suggest that a highly organized cybercriminal group or state-sponsored actors are responsible:
Lazarus Group (DPRK)
- North Korean hackers have been behind some of the largest crypto heists (e.g., Ronin Bridge, Harmony Horizon).
- The attempted XRP transfer mistake earlier in the month suggests active operations from DPRK-affiliated hackers.
Cybercriminal Syndicate
- The Coinbase theft and Bybit exploit both involved well-planned laundering techniques.
- Such advanced tactics are typically used by Russian, North Korean, or professional cybercrime rings. Insider or Exchange Exploit?
- The sheer scale of the $1.46 billion outflows suggests a possible inside job or security breach at Bybit.
- If it was an external exploit, it may involve vulnerabilities in smart contracts or withdrawal mechanisms.
How Can You Spot Money Laundering in Transactions?
When looking at transactions, some red flags indicate money laundering:
- Funds sent to multiple new wallets in small amounts → Example: Bybit hacker split 10K ETH into 39 addresses
- Funds moved through cross-chain bridges → Example: Swapping ETH to BTC, then back to ETH
- Usage of known mixer services (Tornado Cash, Sinbad, ChipMixer, etc.) → Common Lazarus tactic.
- Fast swaps on DEXs immediately after a theft → Prevents exchanges from freezing stolen assets.
- Deposits into suspicious exchanges with low KYC (e.g., Russian, DPRK-friendly platforms) → Lazarus frequently uses Garantex, Bitzlato, and small P2P exchanges.
Conclusion & What Happens Next?
The Bybit hack, along with the Coinbase social engineering scam and North Korea’s cyber activities, highlights the increasing sophistication of cryptocurrency attacks. The disappearance of $1.46 billion from Bybit points to a significant security failure, and if it was an external hack, the exploiters may attempt further laundering in the coming days. Blockchain analytics are actively tracking the stolen funds, and exchanges and services must blacklist the associated wallets to prevent further transactions. Meanwhile, Bybit's response whether confirming a breach or investigating an internal security lapse remains critical.
We will continue monitoring new blockchain movements tied to these incidents. Stay tuned for updates.
About us!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


July 1, 2025, 7:17 p.m.

July 1, 2025, 7:07 p.m.