Major Cybersecurity Breach of a Leading Asian Telecom Company: An Unprecedented Data Heist

Overview
In a startling revelation, a hacker known as "kiberphant0m" has claimed responsibility for breaching a major Asian telecom company with annual revenues exceeding $5 billion. This breach, described as one of the largest and most damaging in recent history, has exposed a wealth of sensitive data and granted unprecedented access to the company's internal network. The extent of the breach highlights significant vulnerabilities within the telecom sector and raises critical concerns about data security, privacy, and corporate governance.
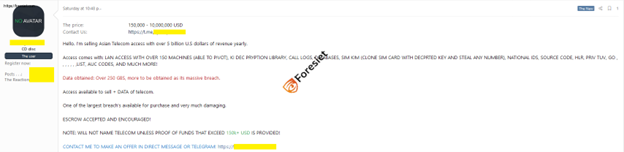
Incident happed forum
Scope of the Breach
The breach encompasses an alarming range of data and network access:
- LAN Access: kiberphant0m has gained access to over 150 machines within the company's LAN, providing a foothold for further penetration into the network.
- Decryption Library for KI (Key Integrity): This allows the hacker to manipulate encryption keys and potentially decrypt sensitive communications.
- Call Logs: Detailed records of calls made through the telecom network, which could reveal private information about users.
- Databases: Access to various databases containing critical operational and customer data.
- SIM Card Cloning Capability (SIM KIM): The hacker possesses the tools and decrypted keys necessary to clone SIM cards, facilitating the theft of mobile identities.
- National ID Information: Compromised personal identification data of millions of users.
- Source Code: Access to the telecom company’s proprietary software, potentially revealing system vulnerabilities.
- HLR (Home Location Register): Access to the database containing IMSI numbers, allowing the hacker to hijack mobile identities.
- AUC (Authentication Center) Codes: These codes are essential for authenticating users on the network, critical for ensuring secure communications.
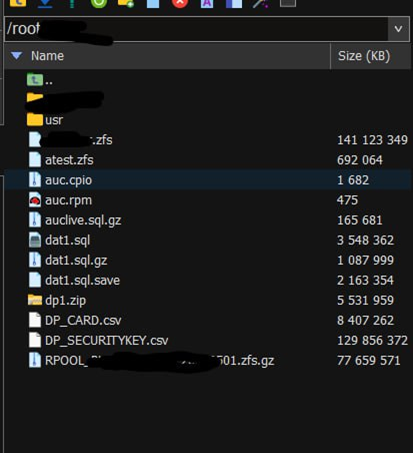
The total data compromised so far amounts to over 250 GB, with the hacker suggesting there could be up to 1 TB more stored on the company's servers.
Details of the Offer
kiberphant0m has put this extensive trove of data and network access up for sale with the following terms:
- Price Range: Between $150,000 and $10,000,000 USD, depending on the buyer's requirements.
- Escrow Service: Accepted and encouraged to facilitate the transaction.
- Identity Disclosure: The identity of the telecom company will only be disclosed upon proof of funds exceeding $150,000 USD.
This offer includes all data obtained so far, login credentials, root access to machines, and detailed instructions for maintaining network control.
Method of Breach
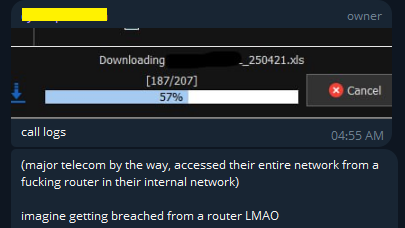
In a private Telegram group, kiberphant0m has shared screenshots and detailed accounts of the breach, explicitly mentioning the telecom company. Remarkably, the hacker managed to infiltrate the entire network through a single compromised router within the internal infrastructure. This access, coupled with root superuser rights, enabled the extensive data exfiltration.
The breach data extends from 2013 to the present day, with new information being retrieved daily. This ongoing access provides the hacker with the ability to continually siphon off fresh data, escalating the severity of the breach.
Implications and Conclusion
This incident serves as a stark reminder of the vulnerabilities within even the most robust corporate networks. The breach not only threatens the privacy of millions of users but also exposes critical corporate and operational data, potentially crippling the affected telecom company's operations and reputation.
For companies across all sectors, this breach underscores the urgent need for comprehensive cybersecurity measures, including:
- Regular Security Audits: To identify and mitigate vulnerabilities before they can be exploited.
- Advanced Encryption Techniques: To protect sensitive data both at rest and in transit.
- Employee Training: Ensuring that all staff are aware of cybersecurity best practices and the importance of vigilance against potential threats.
- Incident Response Planning: Having a robust plan in place to quickly and effectively respond to breaches when they occur.
At Foresiet, we specialize in providing top-tier cybersecurity solutions tailored to the needs of our clients. Our services include comprehensive security audits, advanced threat detection and response, and continuous monitoring to safeguard your data and network infrastructure.
In light of incidents like this, it is clear that proactive and robust cybersecurity measures are essential to protecting your business and your customers.
About Foresiet!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


July 10, 2025, 9 a.m.
