Meduza Stealer: Detailed Analysis of its Features, Capabilities, and Recent Updates on Active C2

The Meduza Stealer, a malware designed for comprehensive data theft, first appeared on dark web forums on June 12, 2023. It was introduced by a mysterious actor known only as 'Meduza,' with prices ranging from $199 to $1199. Since its emergence, it has gained attention across cybercriminal communities for its potent capabilities.
Announcement on darkweb forum
New version of Meduza stealer announced on telegram
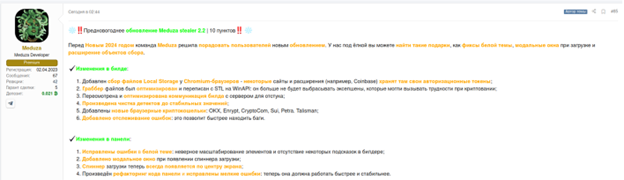
Recent Update: Meduza Stealer 2.2
On December 24, 2023, Meduza Stealer received a notable update, version 2.2, featuring:
- Fixes for White Theme Issues
- Improvements for Modal Windows on Loading
- Expanded Data Collection Objects
These updates aim to enhance the malware’s effectiveness and user experience.
Purpose and Target
Meduza Stealer is a specialized tool designed for stealing data. It targets users' browsing activities, capturing a wide array of information such as login credentials, browsing history, bookmarks, and even details from browser-based cryptocurrency wallets and password managers. Essentially, no digital asset is secure from its reach. Currently, Meduza Stealer supports Windows Server 2012, 2016, 2019, 2022, and Windows 10/11.
The author has proven it works effectively across all these versions, with other Dark Web actors calling it "stable and ideal."
Key Features and Improvements
The Meduza Stealer malware is designed to outshine competitors like Azorult, Redline, Racoon, and Vidar Stealer. Its recent enhancements include:
- Support for More Software Clients: Meduza now supports browser-based cryptocurrency wallets, increasing its range of targets.
- Upgraded Credit Card Grabber: This improvement enhances its ability to capture sensitive financial data.
- Advanced Password Storage Dump: New mechanisms for extracting credentials and tokens across various platforms.
- Enhanced Data Collection: Comprehensive extraction of login credentials, browsing history, bookmarks, crypto wallet extensions, password managers, and 2FA extensions.
Meduza Stealer: What It Can Do and How It Works
Meduza Stealer is a powerful malware that targets a wide range of applications and data. It’s capable of stealing information from:
- 106 Browsers: Including Google Chrome, Microsoft Edge, Brave, Opera, Firefox, and many others.
- 107 Cryptocurrency Wallets: Such as MetaMask, TrustWallet, Coinbase, and several desktop wallets.
- File Extensions: Through its FileGrabber module.
- Instant Messengers: Like Telegram and Discord.
- Gaming Platforms: Steam.
- Password Managers: Including 1Password, LastPass, and Bitwarden.
- VPN Services: OpenVPN.
- Email Clients: Outlook.
- Google Tokens.
- Browsers: Meduza can extract data from browsers based on Chromium (e.g., Google Chrome, Microsoft Edge) and Gecko (e.g., Firefox, SeaMonkey). It supports many other less common browsers as well.
- Cryptocurrency Extensions: It targets crypto-related extensions and applications such as MetaMask, BinanceChain, and Coinomi, among others.
- Desktop Cryptocurrency Wallets: It can steal data from wallets like Coinomi, Exodus, and Jaxx Liberty.
- Password Managers: The malware supports a range of password managers, including Bitwarden, Dashlane, and KeePassXC.
- Discord Clients: It affects different versions of Discord, including Discord Canary and Discord PTB.
- Telegram Clients: It targets Telegram Desktop and Kotatogram.
- Preservation of Original Format: Logs are saved in the same form as they arrive on the server.
- Convenient Folder Structure: Browser-related data is neatly organized into designated folders.
- Google Token Collection: Google tokens are stored in a separate folder.
- Autofill Fields Aggregation: Autofill fields are compiled into a single text file.
- Separate Outlook Folder: Data related to Outlook is stored in a dedicated folder.
- Specific Signatures: Detailed identification of the compromised system.
- Comprehensive Details: Extensive information on extracted data and system status.
- 103[.]161[.]224[.]131
- 193[.]33[.]153[.]62
- 109[.]237[.]99[.]23
- 5[.]42[.]101[.]189
- 5[.]42[.]106[.]42
- 77[.]105[.]146[.]121
- 5[.]42[.]103[.]11
- 109[.]107[.]181[.]83
- 77[.]105[.]147[.]243
- 79[.]137[.]205[.]182
- 5[.]42[.]73[.]251
- 46[.]226[.]166[.]245
- 79[.]137[.]197[.]154
- Chromium-Based Browsers Support:b> Meduza will be able to dump local storage data from Chromium-based browsers. This includes extracting authorization tokens from websites and extensions like Coinbase. Recent updates have already added support for dumping Windows Credential Manager and Windows Vault.
- Optimized Password Grabber: The password grabber has been rewritten from STL to WinAPI, enhancing its efficiency. Improvements have also been made to C2C (Command and Control) communications.
- New Browser-Based Cryptocurrency Wallets: Support will be added for new crypto wallets such as OKX, Enrypt, CryptoCom, Sui, Petra, and Talisman. Meduza will also support Google Account tokens, which can be used for cookie manipulation to access compromised accounts. New versions of Google Chrome (Canary, Dev, Beta) will also be supported. A new feature called “Google Token Recovery” will help process these tokens.
- Enhanced Obfuscation and AV Evasion: The crypting stub has been improved for better antivirus evasion. For an additional fee of $119, users can receive enhanced obfuscation for even better anti-detection coverage.
- 1 Month: $199
- 3 Months: $399
- Lifetime: $1199
- Launch MedusaServer.exe.
- Install Python 3.10.2.
- Install Microsoft Visual Studio Redistributable.
- Run the following commands in the console:
- Copy code
- pip install poetry
- poetry config virtualenvs.in-project true
- cd panel
- poetry install
- .venv\Scripts\activate
- playwright install
- python server.py
Supported Software List:
Log Structure and Data Handling
Meduza Stealer maintains a clear and organized log structure:
Report and Log Details
Meduza Stealer generates detailed reports similar to those produced by other stealer malware like Azorult and Redline. These reports provide:
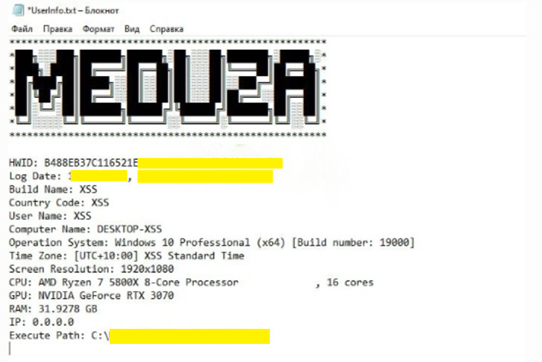
Meduza Stealer Log file
Active C2 Panels
As of August 23, 2024, the following active C2 panels for Meduza Stealer have been identified:
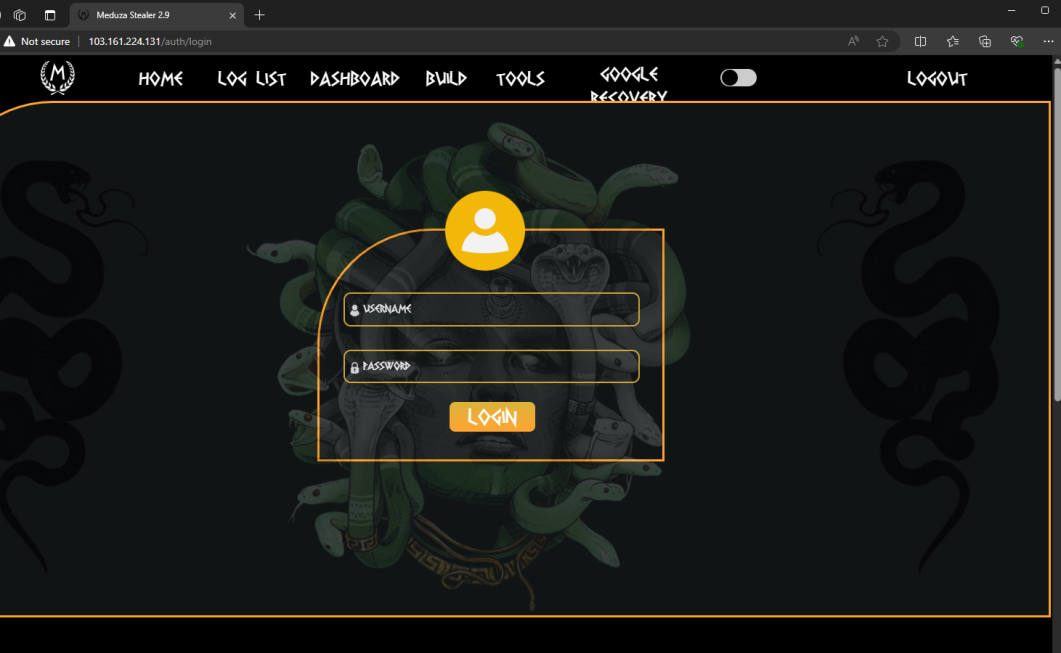
Active C2 Panels
Meduza Stealer features a graphical user interface (GUI) that allows attackers to interact with the malware easily

Graphical user interface (GUI)
Upcoming Upgrades for Meduza Stealer in 2024
In 2024, Meduza Stealer will introduce several significant upgrades:
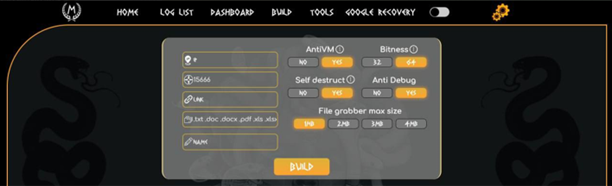
Configuration Panel
Partnership with TrueCrypt Service
Meduza Stealer has partnered with TrueCrypt Service, a well-known underground crypting service. TrueCrypt Service is extensively used by malware and ransomware operators to obfuscate their payloads and evade antivirus detection. This partnership enhances Meduza’s ability to remain undetected by improving its cryptographic techniques and overall stealth capabilities.
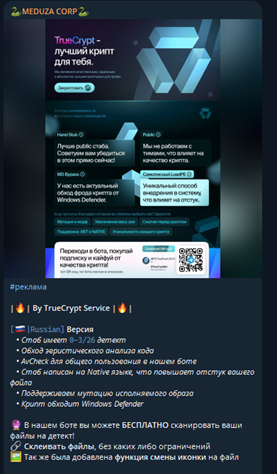
TrueCrypt Service
Meduza Stealer Subscription Pricing
These prices offer various options for accessing Meduza Stealer, depending on the length of subscription required.
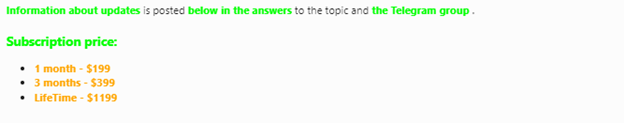
Screenshots shows price details
Accessing Meduza Stealer
After payment, new clients are invited to a private, invite-only Telegram channel where they can access the latest tools. As of now, the newest version available through this channel is Meduza 2.2.7, which can be downloaded upon subscription activation.
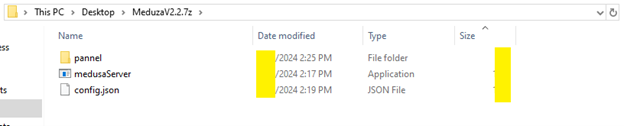
Meduza source files 1
The Command and Control (C2C) panel for Meduza Stealer has been upgraded and continues to be written in Python. These improvements enhance its functionality and efficiency in managing and monitoring compromised systems.
Meduza source files 2
To install Meduza Stealer, follow these steps:
Configuration for Communication:
Meduza 2.2 supports communication via Telegram IM for delivering logs from the infected victim. The operator can configure this by setting up the API key and channel ID.
Meduza Stealer: Leading the Pack
Meduza Stealer stands out as one of the best tools in its class, thanks to its comprehensive feature set and regular updates. It provides excellent operative support and benefits from consistent improvements that enhance its functionality.
With its flexible configuration system and extensive application coverage, Meduza is effectively competing with established malware tools like Azorult and Redline Stealer. These attributes make Meduza a powerful and adaptable option for those in the malware landscape.
Conclusion
Meduza Stealer has established itself as a formidable player in the malware arena with its comprehensive capabilities and continuous enhancements. Its robust feature set, including support for a wide range of applications and flexible configuration options, positions it as a top competitor alongside tools like Azorult and Redline Stealer.
The ongoing updates and operative support ensure that Meduza remains at the cutting edge of malware technology. For those in the cybersecurity field or dealing with malware, understanding and staying updated on Meduza's developments is crucial for effective defense and response strategies.
About Foresiet!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


