New Ransomware Groups Emerging in Late May 2025: A Threat Intelligence Overview

As of the end of May 2025, seven new ransomware groups have surfaced with active leak sites and confirmed victim postings. These groups—Silent Ransomware, Gunra Ransomware, JGroup Ransomware, IMN Crew, DireWolf Ransomware, DataCarry Ransomware, and SatanLock Ransomware have demonstrated early signs of active targeting and data exfiltration campaigns.
This blog provides a detailed breakdown of their activity, initial victimology, and attribution by geography where applicable. Screenshots of each group’s leak site are available and should be included accordingly.
1. Silent Ransomware Group
First Identified: Late May 2025
Leak Site Status: Active
Initial Victims:
- United States
- Canada
Silent Ransomware launched with a clear focus on North American targets. Their leak site follows a conventional ransomware blog structure with proof-of-leak data and countdowns.
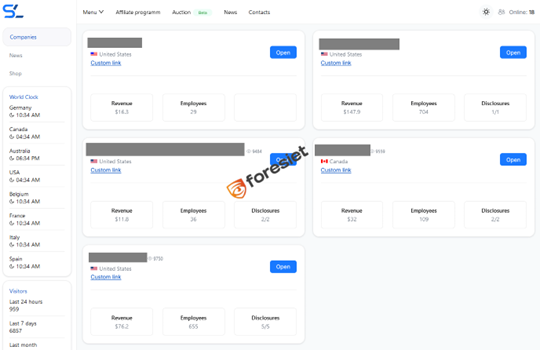
Silent Ransomware leak site homepage or victim index.
2. Gunra Ransomware
First Identified: Late May 2025
Leak Site Status: Active
Targeted Countries:
- Japan
- Egypt
- Panama
- Italy
- Argentina
- Brazil
- Mexico
- Croatia
Gandra Ransomware appears to be globally oriented, targeting organizations across Asia, Europe, South America, and the Middle East. Their leak site emphasizes multilingual support and victim-specific folders.
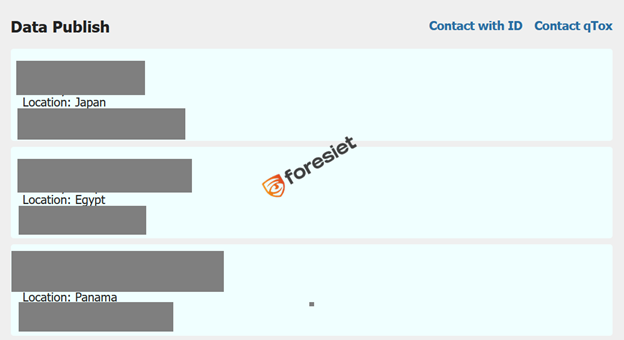
Gandra blog showing international targeting.
3. JGroup Ransomware
Victim Count: 17
Leak Site Status: Active
Observed Victim Countries (via domain analysis):
- Hungary
- India
- Brazil
- Argentina
- China
- Vietnam
- France
- Australia
- United States
- Luxembourg
- Indonesia
- Switzerland
The JGroup leak site lists victims by domain only, but regional attribution has been inferred through analysis of top-level domains (TLDs).
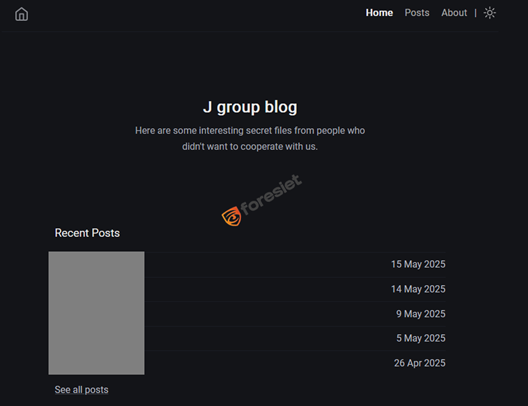
JGroup ransomware blog with anonymized victim list.
4. IMN Crew Ransomware
Leak Site Status: Active
Known Victims Include:
- United States
- Eastern Europe
- Indonesia
- Croatia
- Mexico
- European Union
- Sweden
IMN Crew targets a mix of industries including insurance, manufacturing, and government sectors, spread across North America, Europe, and Asia.

IMN Crew ransomware blog front page with blurred victim listings.
5. DireWolf Ransomware
Leak Site Status: Active
Victim Overview:
- United Arab Emirates
- Middle East
- Australia
- Canada
- Thailand
- European Union
- New Zealand
DireWolf has a low-profile but active leak site. Their targets suggest interest in regulatory, logistics, and industrial sectors.
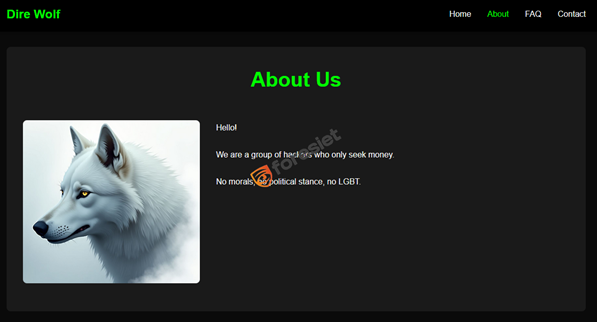
DireWolf leak site with anonymized entries.
6. DataCarry Ransomware
Victim Count: 9
Known Geolocations:
- Latvia
- Middle East
- France
- United States
- Switzerland
- Germany
- United Kingdom
- France
- United States
DataCarry targets mid- to high-profile businesses in sectors such as insurance, healthcare, aerospace, and legal services.
DataCarry ransomware victim index page.
7. SatanLock Ransomware
Known Victim:
- One government technology department in Ecuador
SatanLock has so far published only one victim, but the nature of the target government sector—could indicate the early stage of a politically motivated or highly targeted campaign.
SATANLOCK ransomware victim index page.
Threat Techniques and Tactics (TTPs)
While many of these groups are newly emerged, early patterns and similarities with known ransomware groups can be inferred based on infrastructure, behavior, and leak site mechanics. Exact techniques will vary depending on payload analysis and available IOCs. These are inferred based on behavior consistent with known ransomware operations. Here's a generalized MITRE ATT&CK alignment observed across multiple groups:
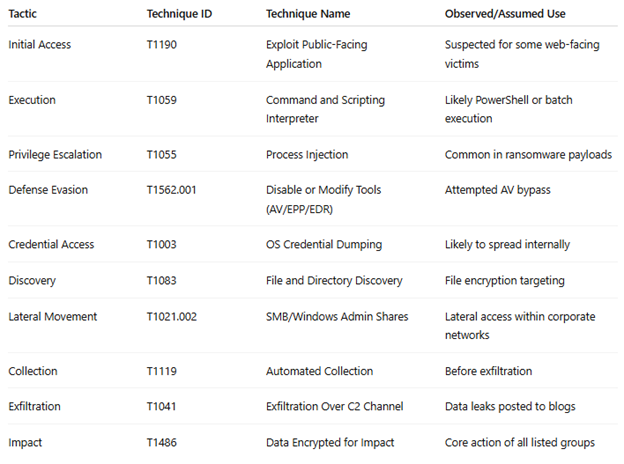
Potential Affiliations or Overlaps
While attribution is still speculative, early indicators suggest some of these groups may be:
- Splinter groups of retired or rebranded ransomware-as-a-service (RaaS) operators
- Testing campaigns by seasoned affiliates launching new brands
- Copycat actors using open-source ransomware kits with minor modifications
No known direct links to major ransomware families like LockBit, BlackCat, or Cl0p have been confirmed as of this writing.
Conclusion
The emergence of these seven ransomware groups in a short timeframe underscores the fragmentation and persistence of the ransomware ecosystem. With geographic targeting spanning five continents and multiple verticals, these actors demonstrate an aggressive expansion strategy from day one.
Organizations should monitor these groups for indicators of compromise, evolving leak tactics, and potential shifts in targeting behavior as their operations mature.
About us!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


