Nitrogen Campaign: A Threat Targeting Tech and Non-Profit Sectors in North America

Foresiet Security Intelligence has recently uncovered the Nitrogen campaign, which has set its sights on numerous organizations within the technology and non-profit sectors across North America. While Foresiet managed to intercept the infections before significant hands-on-keyboard activity took place, there are strong indications that threat actors are leveraging this infection chain to establish compromised environments for deploying ransomware. This assessment echoes the recent findings from Trend Micro, who have reported encountering a similar infection chain resulting in a BlackCat (also known as ALPHV) ransomware infection.
Attackers are employing counterfeit advertisements for commonly used system utilities as a vehicle to disseminate the dangerous Nitrogen malware.
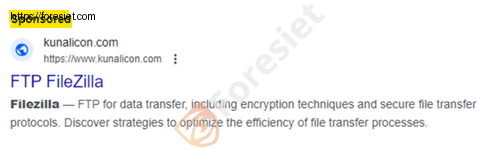
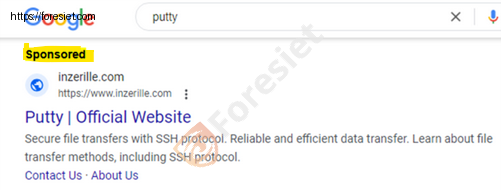
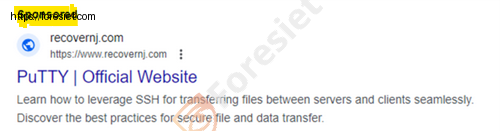
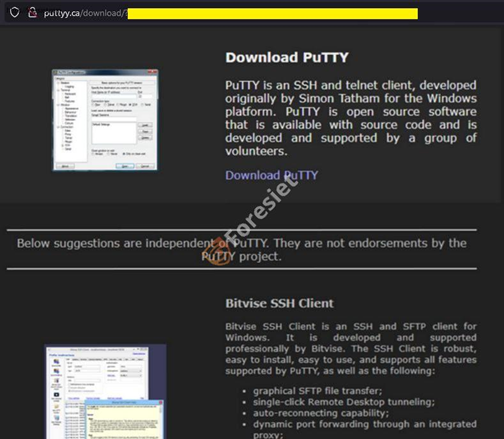
Auto-download’s: PUTTY
The attackers have developed a sophisticated malvertising infrastructure, utilizing cloaking techniques to effectively evade detection. Upon clicking on the ads, users may find themselves redirected to either a seemingly harmless decoy site or a video featuring Rick Astley, a deliberate tactic aimed at deriding security researchers.
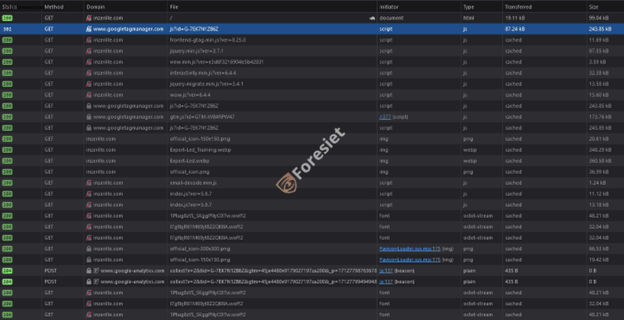
However, for unsuspecting victims, the redirection leads to counterfeit websites meticulously designed to imitate the authentic software pages they are replicating. These deceptive sites are engineered to be remarkably convincing, increasing the likelihood of individuals unknowingly downloading malware-infected installers.
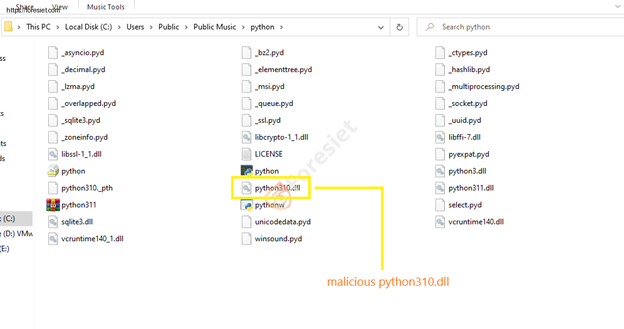
DLL File
After downloading the trojanized installers, they appear as ISO images on the compromised computer. These files are then mounted in Windows Explorer and can be mapped to a drive, providing access to the enclosed content.
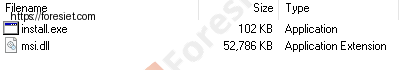
Within the ISO image lies a file disguised as the msiexec.exe Windows tool, often renamed to install.exe or setup.exe. When executed, this renamed msiexec.exe triggers the covert loading of the malicious msi.dll file (referred to as NitrogenInstaller), also housed within the same image.
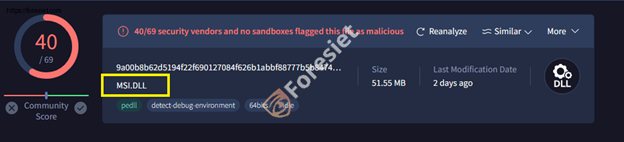
The malicious code, found within MsiLoadStringW, is inserted into the genuine msi.dll situated in the system directory. Although DLL proxying is not a novel technique, it is typically linked with DLL hijacking attacks rather than DLL sideloading or preloading methods.
After the injection, the NitrogenInstaller DLL manages the setup of a registry run key to maintain persistence. This key, named "Python" is created at HKEY_USERS{User_SID}\Software\Microsoft\Windows\CurrentVersion\Run\Python. Moreover, a related scheduled task named "OneDrive Security" is detected, pointing to the binary C:\Users\Public\Music\python\pythonw.exe. This task is scheduled to run every five minutes.
To enable the later stages of the attack, specifically the installation of Cobalt Strike Beacons, threat actors need a fully operational Python environment. This clarifies the rationale behind deploying the genuine BeaconPack Python Package: to run Python code necessary for subsequent steps in the infection process.
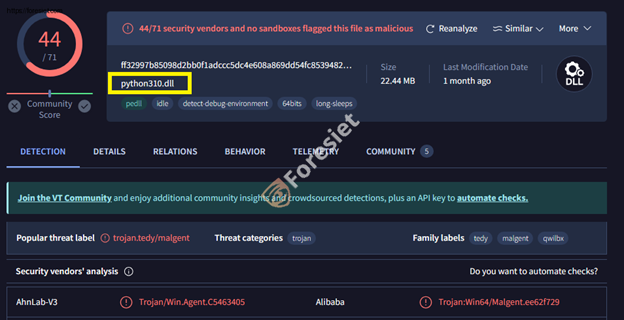
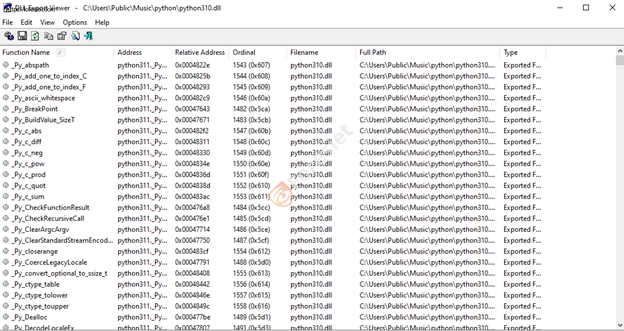
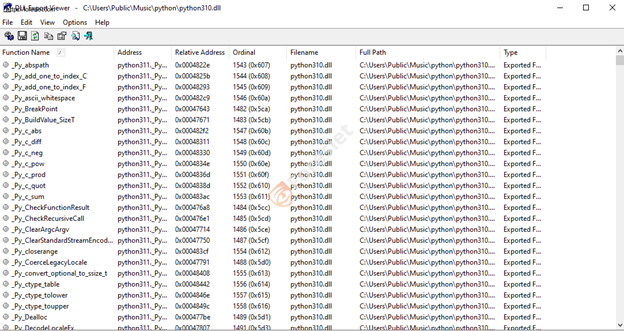
We've noticed that threat actors have made alterations to the malicious Python package, elevating it to version 3.11. In this updated iteration, they've incorporated the NitrogenStager, concealed as python311.dll. Additionally, the original clean Python DLL has been renamed to python311x.dll.
It's crucial to highlight that the NitrogenStager Python package is incapable of running Python scripts. Instead, its primary function has been substituted with malicious connect-back code. Moreover, all other exports within the package are directed to the genuine Python DLL (python311.dll).
Conclusion
Through diligent observation and analysis, Foresiet Security Intelligence has closely examined the Nitrogen malware campaign, which targets organizations within the technology and non-profit sectors across North America. This sophisticated attack utilizes deceptive malvertising techniques, cloaking mechanisms, and advanced DLL manipulation tactics to infiltrate systems and establish persistence. The threat actors involved in this campaign exhibit a clear intention to leverage compromised environments for malicious ends, potentially including ransomware deployment. Foresiet maintains a vigilant stance in monitoring and mitigating such threats, safeguarding the ongoing security of its clients and their digital assets.
About Foresiet!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


July 10, 2025, 9 a.m.
