Oracle Cloud Breach? Hacker Claims 6M Records & 140K Tenants at Risk – Foresiet Research vs. Oracle’s Denial

Overview of the Alleged Breach
On March 20, 2025, a threat actor known as Rose87168 posted on the dark web, claiming to be selling breached Oracle Cloud Traditional servers along with approximately 6 million exfiltrated user records. The hacker did not mention the price for the stolen data. He alleged that critical information, including SSO (Single Sign-On) and LDAP credentials, Java Keystore (JKS) files, passwords, and authentication keys, was stolen from Oracle’s login infrastructure.
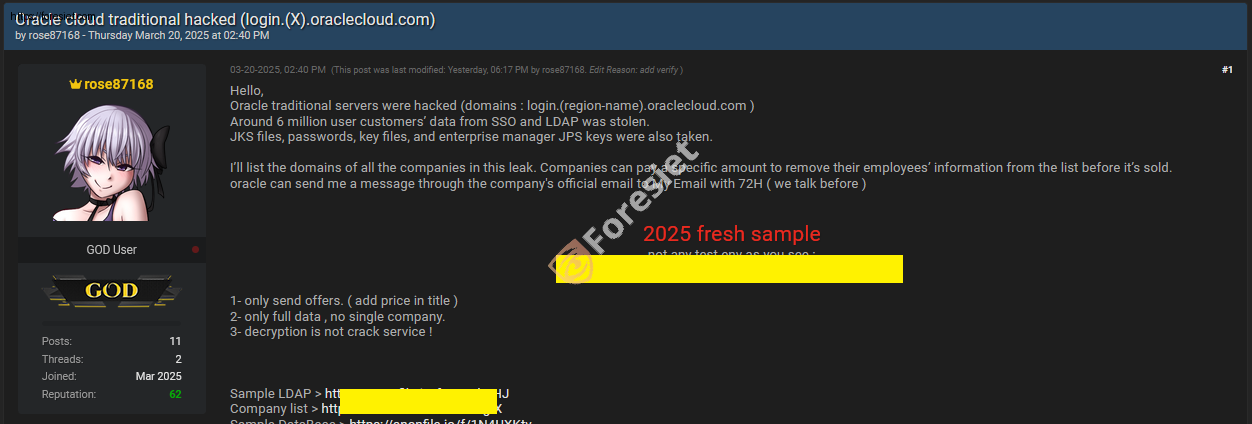
Screenshot shows stolen Oracle Cloud data
The database contains approximately 6 million lines of data leaked from Oracle Cloud’s SSO and LDAP, including:
- JKS (Java KeyStore) files
- Encrypted SSO passwords
- Key files
- Enterprise Manager JPS (Java Platform Security) keys
How Was Oracle Allegedly Hacked?
Vulnerability Exploited: CVE-2021-35587
Public security scans and dark web chatter suggest that the hacker may have exploited CVE-2021-35587, a critical vulnerability in Oracle Access Manager (OAM) that allows unauthenticated remote attackers to gain admin access.
Signs That Oracle Cloud Traditional Was Running an Outdated System
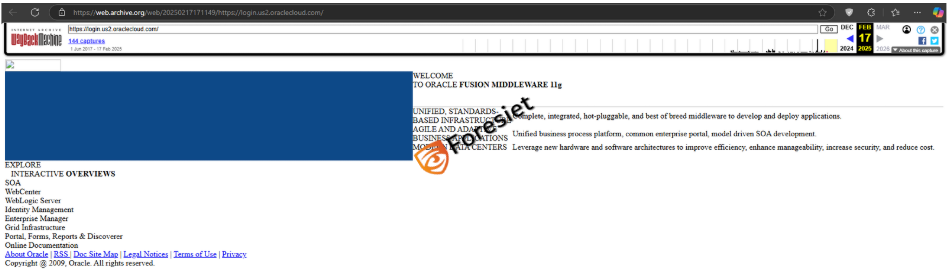
Screenshot shows The archived snapshot from the Wayback Machine (dated February 17, 2025) shows the Oracle Cloud login page running on Oracle Fusion Middleware 11g, possibly indicating outdated infrastructure.
- The affected subdomain (login.us2.oraclecloud.com) was reportedly using Oracle Fusion Middleware 11G, which last received updates in 2014.
- Public security scans (e.g., FOFA, Shodan) indicated that the system had not been patched for years.
- CVE-2021-35587 was listed in CISA’s Known Exploited Vulnerabilities (KEV) Catalog in December 2022, meaning it was a known target for attackers.
- The subdomain login.us2.oraclecloud.com was captured on the Wayback Machine on 17 Feb 2025, showing it was hosting Oracle Fusion Middleware 11G.
The threat actor claimed to have compromised the subdomain login.us2.oraclecloud.com, which has allegedly been taken down since the hack. He also mentioned his ProtonMail address."
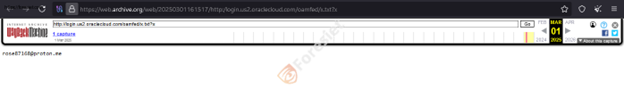
Screenshot of the text file uploaded by the threat actor on the endpoint login.us2.oraclecloud.com.
What the Hacker Likely Did
- Exploited CVE-2021-35587 to bypass authentication and gain control of Oracle Access Manager.
- Extracted sensitive data, including:
- SSO session data and authentication tokens
- LDAP directory details (usernames, emails, encrypted passwords)
- JKS files and Enterprise Manager JPS keys (used for securing Oracle services)
- Tenant information from affected companies
- Exfiltrated the stolen data and posted a ransom demand on BreachForums, offering companies the option to pay for data removal before selling the full dataset.
Why CVE-2021-35587 Was Likely Used
This exploit allows remote unauthenticated access to Oracle Access Manager (OAM), which is directly tied to SSO and LDAP authentication. Since the leaked data contains SSO session details, LDAP user credentials, and JKS files, this strongly suggests that OAM was compromised, leading to the data exfiltration.
However, additional vulnerabilities (such as SSRF in Oracle WebLogic or credential stuffing attacks) could have been used alongside CVE-2021-35587.
Analysis of the Leaked Data
Screenshot shows samples_LDAP.txt hacker shared
Based on the Sample_Database.txt and Sample_LDAP.txt files, the hacker appears to have accessed Oracle Cloud SSO and LDAP directories. Here’s what we found:
1. Stolen Data Categories
- Employee Accounts: Names, emails, usernames, and organizational roles.
- Tenant Information: Tenant IDs, access groups, and administrative privileges.
- Authentication Data:
- SASL/MD5 hashed passwords
- LDAP directory details
- Encrypted authentication credentials
- Enterprise Manager JPS Keys: Used for Oracle authentication.
2. Authentication Data:
- LDAP credentials (SASL/MD5 hashed passwords)
- SSO authentication tokens
- Java Keystore (JKS) files (used for securing credentials)
- Enterprise Manager JPS keys (used for internal service authentication)
3. Cloud Tenants & Infrastructure Information:
- Tenant GUIDs & Unique Identifiers (e.g., orclMTTenantGuid=11987096172814988)
- Access privileges (Read/Write permissions for Oracle user directories)
4.Password & Security Settings:
- Password change flags (indicating if users were forced to change passwords)
- Password expiration dates (some were from 2018, suggesting old accounts)
- Login attempt counters (showing failed authentication attempts)
Oracle’s Official Response
Oracle has denied the breach, stating:
"There has been no breach of Oracle Cloud. The published credentials are not for the Oracle Cloud. No Oracle Cloud customers experienced a breach or lost any data."
Why Did Oracle Deny the Breach?
While Oracle insists that no breach occurred, the situation may be more complex. Here are a few possible reasons for their denial:
1. Legal & Reputation Considerations
Admitting to a breach could lead to regulatory scrutiny, lawsuits, and loss of customer trust. Companies often choose carefully worded statements to minimize damage.
2. Technical Loophole in Definition of "Cloud Breach"
If the attack targeted Oracle Access Manager (OAM) running on an older system rather than Oracle’s core cloud infrastructure, Oracle might argue that their "Cloud" itself was not breached—even though an Oracle-managed system was compromised.
3. Mitigation Measures Taken
After reports of the breach, the affected subdomain (login.us2.oraclecloud.com) was allegedly taken down. If Oracle disabled or contained the affected system, they may argue that no ongoing risk exists.
Lessons from This Incident
- Always keep enterprise authentication systems updated — especially Oracle Fusion Middleware and Access Manager.
- Monitor public CVE reports — exploits for critical vulnerabilities (like CVE-2021-35587) should be addressed immediately.
- Use multi-layered security controls — even if a system like OAM is compromised, additional security layers (such as MFA and restricted access policies) can help mitigate the impact.
- Track dark web forums for threat intelligence — organizations should actively monitor BreachForums and similar platforms for early warnings of leaked data.
Immediate Actions for Affected Organizations
- Reset all Oracle Cloud passwords (including service accounts).
- Rotate authentication keys and JKS certificates to prevent reuse.
- Enable multi-factor authentication (MFA) if not already enforced.
- Check logs for unusual login activity related to Oracle Cloud services.
- Monitor dark web forums for potential data resale or credential leaks.
- Engage Oracle support to verify if your organization was impacted.
Conclusion
While Oracle denies any breach of their cloud, available evidence suggests that an outdated Oracle Access Manager server was compromised, leading to SSO and LDAP credential leaks. The situation underscores the importance of patching vulnerabilities, proactive monitoring, and incident response in securing enterprise cloud environments.
Organizations using Oracle Cloud Traditional should immediately review their security posture, rotate credentials, and ensure they are not impacted by the alleged breach.
About us!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.



