Protect Your Business from Interlock Ransomware: Prevention and Detection Tips

At Foresiet, our mission is to help businesses stay informed about emerging cybersecurity risks. One of the latest and most dangerous threats is Interlock ransomware, a variant that has made waves on the dark web. This ransomware group claims to be more than just extortionists, positioning themselves as enforcers of accountability for companies that fail to adequately protect customer data and intellectual property.
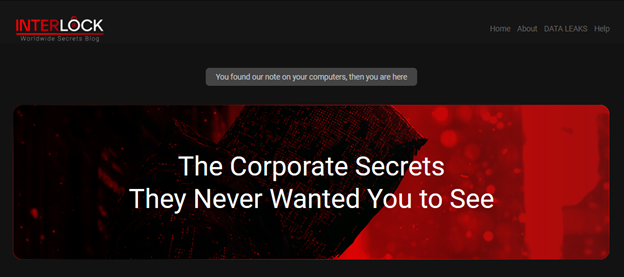
Screenshot shows the prodile of Interlock
Interlock’s attacks are not just about demanding ransom payments. According to their dark web statement, they exploit vulnerabilities left exposed by organizations, delivering "a harsh but necessary wake-up call" to those who neglect cybersecurity. This group has particularly set its sights on the healthcare industry, where downtime and data breaches can have severe, life-altering consequences.
Targeting the Healthcare Sector: Interlock’s Modus Operandi
Interlock ransomware has emerged with a sophisticated focus on virtual environments—specifically targeting VMware’s ESXi hypervisors. By compromising virtual machines (VMs) while leaving physical servers and workstations untouched, Interlock effectively shuts down critical systems. Their tactics involve encrypting virtual disk files (VMDKs) and modifying root passwords on ESXi hosts, making recovery nearly impossible without significant delays.
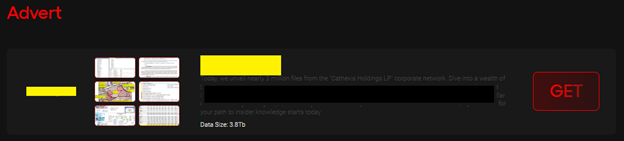
Their first victim was posted.
Key Attack Vectors:
- Target Industry: Healthcare.
- Entry Point: Exploited vulnerabilities within virtual environment
- Impact: Encryption of VMDK files, shutdown of VMs, deletion of local backups to prevent data recovery.
- Command & Control (C2): Established through a scheduled task over an anonymized network, with reverse shell communication for remote control.
Malware File Analysis
Our analysis of Interlock's ransomware processes reveals several key components that aid in its malicious activities:
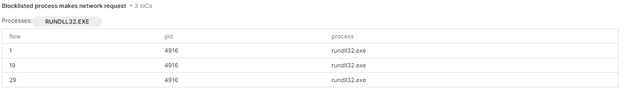
- Processes: The ransomware leverages common system processes such as rundll32.exe to load DLLs and execute commands. For example, it loads malicious DLLs from the following locations:
-
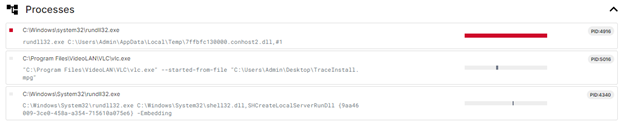
- rundll32.exe C:\Users\Admin\AppData\Local\Temp\7ffbfc130000.conhost2.dll
- o rundll32.exe C:\Windows\System32\shell32.dll,SHCreateLocalServerRunDll
-
- Signatures: Certain processes, such as rundll32.exe, were flagged for making unauthorized network requests. This behavior, alongside the network traffic to C2, is a strong indicator of compromise (IoC).
-
- Network Activity: The malware communicates with a C2 server at IP address 150.171.27.10:443, over HTTPS (TLS-encrypted), making it harder for standard network monitoring tools to detect the ransomware’s operations.
Protecting Against Interlock Ransomware
Given the sophisticated techniques and tactics employed by Interlock, organizations must adopt a multi-layered defense approach. At Foresiet, we recommend the following key actions:
- Patch Management: Regularly update systems, especially those running virtual environments, to close off known vulnerabilities that ransomware groups exploit.
- Access Controls & MFA: Enforce multifactor authentication (MFA) and strong access controls to prevent unauthorized access to critical systems.
- Backup Strategy: Ensure backups are performed regularly and stored offline to avoid them being encrypted or deleted by ransomware.
- Endpoint Detection & Response (EDR): Deploy EDR solutions to monitor for suspicious activity, such as unusual process execution or network traffic patterns.
YARA Rule Overview: Detecting Interlock’s ELF Binary
Detecting Interlock ransomware requires advanced signature-based detection mechanisms. One effective approach is through YARA rules, which can identify specific ELF binaries based on their internal structure. The rule designed for detecting Interlock’s ELF binary uses a combination of unique string patterns and file size criteria.
Key Characteristics of the YARA Rule:
- Focus on String Patterns: This YARA rule searches for specific terms found within the binary, such as cipher_descriptor, __vdso_clock_gettime, and sysctlbyname. These terms indicate cryptographic functions, system memory management, and system calls often used by malware.
- File Size Constraints: The rule ensures the file size of the binary falls between 710KB and 868KB, a characteristic of Interlock's ELF binary, to avoid false positives.
- Trigger Conditions: The rule only triggers when all specified strings are found within the file, ensuring precise detection based on the malware’s internal workings. This approach offers an advantage over traditional detection methods that rely on IP addresses or file hashes, which can be easily modified by attackers.
MITRE Techniques Used by Interlock
Interlock ransomware leverages multiple techniques mapped to the MITRE ATT&CK framework, a globally-recognized tool for understanding adversary tactics and techniques. Some key MITRE techniques seen in Interlock’s operations include:
- T1496 – Resource Hijacking: Interlock compromises virtualized environments to control and disrupt vital system resources, effectively hijacking them for malicious purposes like encryption.
- T1562.001 – Impair Defenses: Disable or Modify Tools: Interlock deletes local backups and alters security settings to prevent recovery, hindering response efforts.
- T1218.011 – Signed Binary Proxy Execution: Rundll32: The ransomware uses the rundll32.exe process to execute malicious DLLs and maintain persistence, which is a hallmark of proxy execution techniques.
- T1027 – Obfuscated Files or Information: By using encryption and anonymized networks, Interlock obfuscates its communications and actions, making detection and response more difficult.
- T1071.004 – Application Layer Protocol: Web Protocols: The malware communicates with its C2 servers over HTTPS, encrypting its traffic and hiding it within legitimate web traffic.
Conclusion
The emergence of Interlock ransomware is a stark reminder of the importance of maintaining robust cybersecurity defenses. By targeting virtual environments in industries like healthcare, Interlock is proving to be a formidable threat. The technical sophistication displayed in its tactics, combined with its philosophy of "accountability through exploitation," raises the stakes for organizations everywhere.
At Foresiet, we are dedicated to helping businesses stay ahead of these evolving threats. Stay vigilant, stay protected, and never underestimate the importance of data security in today’s digital landscape.
About Foresiet!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.