Protecting Your Business from Data Breaches and Cybercrime

Introduction
In today’s digital age, companies across various sectors are increasingly vulnerable to cyber attacks. Among the most alarming tactics cybercriminals use is leveraging stolen data to launch targeted attacks on businesses. With this data in hand, attackers can craft sophisticated schemes to exploit vulnerabilities and cause serious harm to companies. Let's dive into the methods cybercriminals employ using stolen data and how it affects businesses like yours.
Here's a quick overview of their key tactics:
- Reconnaissance & Target Identification With stolen data like employee credentials or internal communications, cybercriminals identify high-value targets and vulnerabilities within the organization to plan their attacks.
- Phishing & Social Engineering Using personal details, attackers create convincing phishing emails to trick employees into providing more information or downloading malware.
- Business Email Compromise (BEC) Cybercriminals impersonate executives using stolen email data to trick employees or partners into transferring money or sensitive information.
- Supply Chain Attacks By compromising weak links in the supply chain, hackers gain access to a company’s network, targeting suppliers or logistics partners.
- Ransomware Attacks Stolen data enables hackers to launch ransomware attacks, encrypting critical files and demanding a ransom, often with the threat of leaking the data.
- Selling Data on the Dark Web When cybercriminals don’t exploit data directly, they sell it on dark web markets, where it can be purchased by others looking to conduct attacks.
Incidents in 2024: Data Breaches
2024 has seen several significant breaches where stolen data was used to target both individuals and companies:
- Date:June 02, 2024
- Victim: Ticketmaster
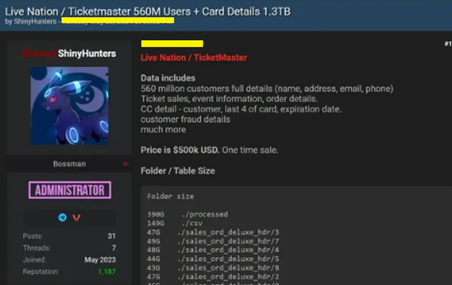
ticketmaster breach posted on darkweb
ShinyHunters claimed to have stolen a 1.3 terabyte database containing personal and credit card details of 560 million Ticketmaster users. The stolen data was offered for $500,000.
Threat Actor: ShinyHunters
- Date:June 02, 2024
- Victim: Twilio
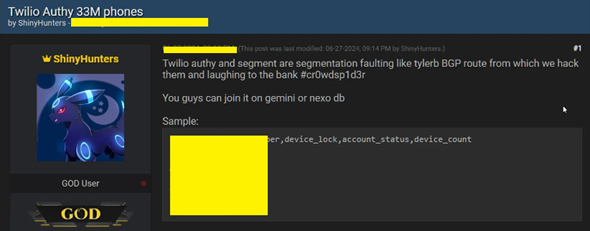
Twilio leaked data posted on darkweb
Hackers exploited an unsecured API endpoint to verify the phone numbers of millions of Authy MFA users, exposing them to potential phishing and SIM swapping attacks. ShinyHunters leaked a CSV file with over 33 million phone numbers.
Threat Actor: ShinyHunters
- Date:August 04, 2024
- Victim: Keytronic
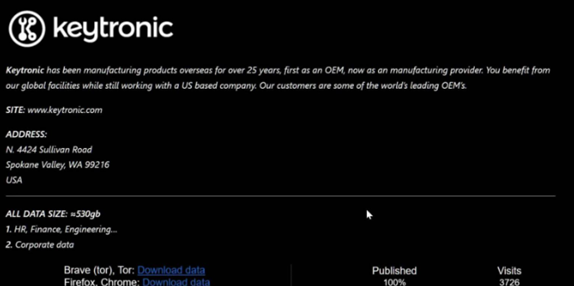
Screenshot from the Black Basta ransomware dark web blog.
Keytronic reported over $17 million in losses after a ransomware attack by Black Basta, disrupting business operations in Mexico and the U.S.
Threat Actor: Black Basta Ransomware
- Date:September 09, 2024
- Victim: Fortinet
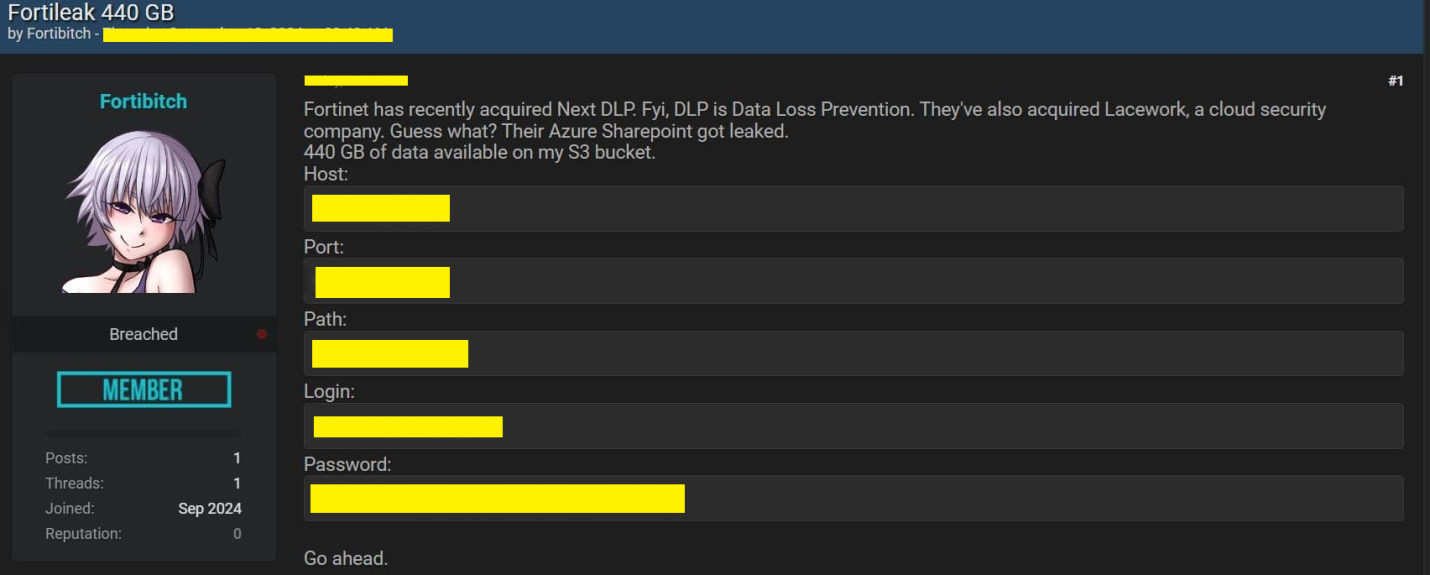
Fortinet data leaked on darkweb.
Fortinet revealed that hackers gained access to a limited number of customer files on a third-party cloud-based file drive.
Threat Actor: Unknown
Types of Stolen Data Sold on the Dark Web
Cybercriminals trade various types of stolen data on the dark web, each posing unique threats to individuals and companies. Here’s a breakdown of the key categories:
- Personal Data Includes names, addresses, phone numbers, birth dates, Social Security numbers, and hacked email addresses. This data is often used for identity theft or fraud.
- Financial Data Comprises stolen credit card details, online banking credentials, and cryptocurrency account information, used to steal funds or commit fraud.
- Online Account Logins Covers username-password combinations for platforms like social media, ride-sharing, and streaming services. This data enables unauthorized access and impersonation.
- Medical Data Encompasses medical histories, prescriptions, biometric data, and billing information. It can be used for medical fraud or identity theft.
- Corporate Data Includes intellectual property, patents, and operational details. Hackers sell this data to competitors or use it for extortion.
How Foresiet Can Help
At Foresiet, we are dedicated to safeguarding your business from cyber threats through comprehensive security solutions tailored to your unique needs. Our services include robust security measures, regular security audits, and ongoing employee training to enhance awareness and preparedness against cyber attacks. With our proactive monitoring and incident response planning, we ensure that your organization is ready to tackle any potential threats efficiently.
By partnering with Foresiet, you can confidently focus on your core business operations, knowing that your cybersecurity is in expert hands.
Conclusion
In an increasingly interconnected world, the risk of cyberattacks is a constant challenge for businesses. Cybercriminals are becoming more sophisticated, using stolen data to launch highly targeted attacks that can disrupt operations, steal valuable assets, and damage reputations. For companies like Foresiet, understanding how attackers use stolen information is the first step in building a resilient defense.
By prioritizing robust cybersecurity measures, training employees, and maintaining vigilance over potential threats, businesses can stay ahead of cybercriminals. Protecting sensitive data and maintaining secure operations isn’t just a necessity—it's a critical part of safeguarding the future of any organization in today’s digital age. At Foresiet, staying proactive and informed will help ensure your company’s continued success in an ever-evolving threat landscape.
About Foresiet!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


July 10, 2025, 9 a.m.
