Stay Ahead of Ransomware: Comprehensive Solutions against DragonForce Attacks

Introduction
In the ever-evolving landscape of cybersecurity threats, the DragonForce ransomware group has quickly become a serious menace to organizations worldwide. First discovered in August 2023, DragonForce has made headlines by leveraging two powerful ransomware variants—a fork of the infamous LockBit3.0 and a modified version of ContiV3.

DragonForce profile
This group’s ability to exploit vulnerabilities in critical sectors, including manufacturing, real estate, and transportation, has brought them to the forefront of global cyber threats.
With the introduction of SystemBC malware, they have created a sophisticated toolkit that targets and cripples companies with alarming precision.

DragonForce promoting its ransomware-as-a-service on darkweb
What is DragonForce Ransomware?
DragonForce operates as a Ransomware-as-a-Service (RaaS) affiliate program, offering customizable ransomware tools to affiliates. This program is designed for malicious actors who want to launch sophisticated ransomware attacks

Dragonforce data leak site
Darweb forum profile of dragon force
Their affiliate program offers tools for attack customization and automation, even utilizing "Bring Your Own Vulnerable Driver" (BYOVD) techniques to disable security processes and clear Windows Event Logs—making it much harder for investigators to trace their activities.
A spike in activity occurred in late June 2024 when an underground dark web forum post by a user named "dragonforce" began advertising the affiliate program. Affiliates who join the program are promised up to 80% of the ransom payout.
DragonForce provides its affiliates with two ransomware variants: one that is custom-built and another that is a modified version of LockBit, both capable of bypassing advanced Endpoint Detection and Response (EDR) and Extended Detection and Response (XDR) systems.
Affiliates are also given access to a panel to create and configure ransomware samples, allowing them to target specific companies and customize encryption settings based on the victim’s infrastructure.
Since its introduction, DragonForce's affiliate program has grown significantly, making it a formidable threat to businesses across industries.
Attack Methodology
The DragonForce attack chain follows a structured, multi-stage process:
- 1. Initial Access: The group typically gains unauthorized access through compromised Remote Desktop Protocol (RDP) servers, leveraging stolen or weak credentials.
- 2. Malware Deployment: Using PowerShell commands, they deploy tools like Cobalt Strike, SystemBC malware, and Mimikatz to establish persistence and maintain control over the network. These tools also aid in credential harvesting and lateral movement, allowing the ransomware to spread across the victim’s environment.
- 3. Persistence and Discovery: By manipulating registry keys and utilizing compromised accounts, DragonForce maintains access over an extended period. Network scanning tools are used to map out the victim’s environment, ensuring that they can encrypt as much critical data as possible.
- 4. Final Stage – Data Encryption and Exfiltration: The ransomware is deployed to encrypt critical data, with a final payload designed to disable recovery options and maximize the ransom demands. Both ransomware variants used by DragonForce are designed to clear logs and evade forensic investigations, making recovery and attribution even more difficult.
High-Profile Victims and Growing Reach
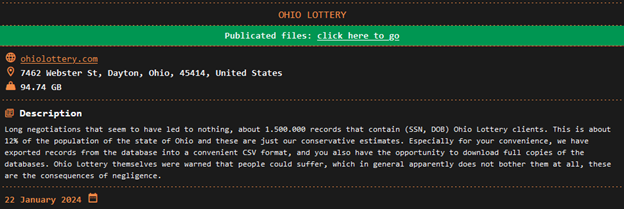
The group has already targeted high-profile organizations like the Ohio Lottery, claiming to have stolen over 94.74 GB of data containing millions of records. There are currently 63 victims listed on the group's Data Leak Site. The home page displays the published victims along with those facing ransom payment deadlines.
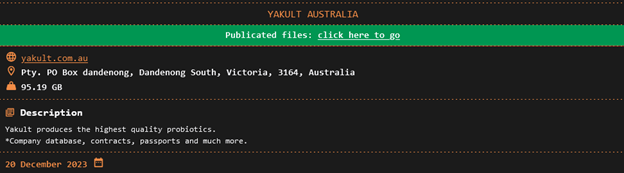
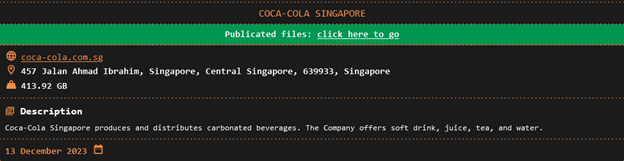
Other claimed victims include Yakult Australia, which lost 95.19 GB of company data, and Coca-Cola in Singapore, where 413.92 GB of sensitive information was breached.
What Should We Do to Protect Our Business from Ransomware?
Your organization can follow essential cybersecurity practices to protect itself from DragonForce and other ransomware threats. These practices include:
- Making Secure Offsite Backups: Regularly back up important data to an offsite location to prevent data loss in case of an attack.
- Running Up-to-Date Security Solutions: Ensure all computers and servers have the latest security patches and antivirus software to guard against vulnerabilities.
- Restricting Lateral Movement: Use network segmentation to prevent attackers from moving freely across your organization if they gain initial access.
- Using Strong, Unique Passwords: Protect sensitive data and accounts with hard-to-crack passwords, and enable multi-factor authentication for an extra layer of security.
- Encrypting Sensitive Data: Where possible, ensure sensitive information is encrypted to reduce the risk of exposure in case of a breach.
- Reducing the Attack Surface: Disable unnecessary functions and services in your systems to limit the number of entry points for attackers.
- Employee Awareness and Training: Educate your staff about the risks of cyberattacks, phishing schemes, and ransomware tactics to minimize the risk of human error.
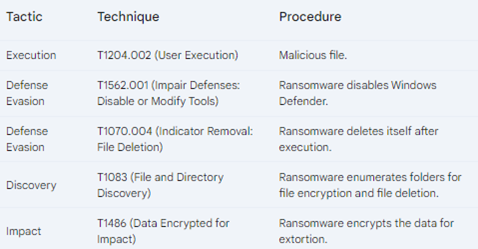
Attack Chain Breakdown: Ransomware Attack
Conclusion
DragonForce ransomware represents a growing threat to organizations around the globe, leveraging advanced techniques, sophisticated malware, and a highly effective affiliate program. As their operations expand, companies in vulnerable industries must act now to strengthen their defenses. By adopting robust anti-malware solutions, conducting regular security audits, enforcing strong authentication protocols, and developing comprehensive backup and recovery plans, businesses can reduce their risk and minimize the impact of potential attacks.
About Foresiet!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


July 1, 2025, 7:17 p.m.

July 1, 2025, 7:07 p.m.