The Anatomy of Akira Ransomware: Is Your Organization Safe? Learn Threats, Exploits, and Safeguards

Introduction
Akira ransomware is a destructive malware that has ravaged industries since its discovery in March 2023. The operations have mostly targeted businesses in North America, the UK, and Australia.
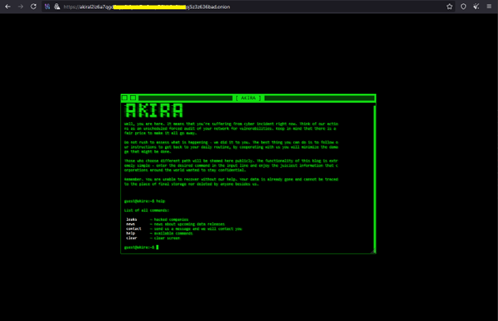
Akira ransomware’s darkweb site
Akira employs a double-extortion tactic; it does not only encrypt the victim's data but also exfiltrates the data, and subsequently threatens to leak it on the internet unless the ransom demand is met. This blog describes the history, tactics, and mitigations behind Akira ransomware.
History and Evolution
These reports claim that the Akira ransomware originates from the notorious Conti ransomware group that went down after a significant data leak in March 2022. The data leak revealed the source code of Conti, its chat logs, playbooks, and storage servers. Following the disbandment of the group, many of the affiliates resurfaced under new names, with Akira being one of the most notable successors.
This connection to Conti has availed Akira's operators of sophisticated tools and methodologies, making it a significant threat in the cybersecurity landscape.
Tactics, Techniques, and Procedures (TTPs)
The perpetrators behind Akira ransomware engage various tactics and techniques to compromise and gain a foothold in the target environment. Their tactics to gain the first point of entry include:
- Exploiting compromised credentials
- Leveraging vulnerabilities in software and systems
- Utilizing VPN services lacking multi-factor authentication (MFA)
- Exploiting external-facing services like Remote Desktop Protocol (RDP)
- Conducting spear-phishing campaigns
- Abusing legitimate credentials
Once the attackers get into a network, they use tools and techniques to maintain persistence and extend their foothold. These include:
- Credential Dumping Tools: Mimikatz and LaZagne
- Network Discovery Tools: SoftPerfect and Advanced IP Scanner
- PowerShell Commands: Used to delete Volume Shadow Copies (VSS) on Windows systems, hindering recovery efforts
Encryption and Ransom Demands
The ransomware, Akira, utilizes a hybrid encryption model. This hybrid model incorporates the ChaCha20 stream cipher and an RSA public-key cryptosystem to ensure good encryption speed and security for files. Encrypted files carry extensions such as.akira or.powerranges.
The ransom note is delivered to the victim, containing a unique code and contact information for the threat actors, through a.onion URL hosted on the dark web. These notes usually focus on the need for urgency in payment and the exposure of data to force compliance.
Technical Analysis
The Akira ransomware demonstrates a very high-level utilization of Windows libraries for cryptographic processes in its malicious activities. This malware imports several cryptographic functions from ADVAPI32.dll and CRYPT32.dll to perform processes such as encryption, key management, and decoding of data.
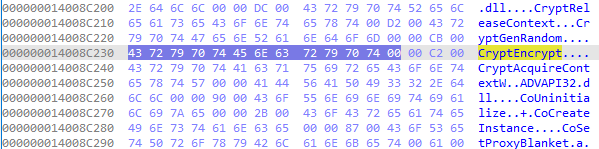
hexadecimal dump of a memory region
Cryptographic Functions
From ADVAPI32.dll:
- CryptEncrypt: Encrypts data using a cryptographic key.
- CryptAcquireContextW: Acquires a cryptographic context for a specific provider.
- CryptReleaseContext: Releases a previously acquired cryptographic context.
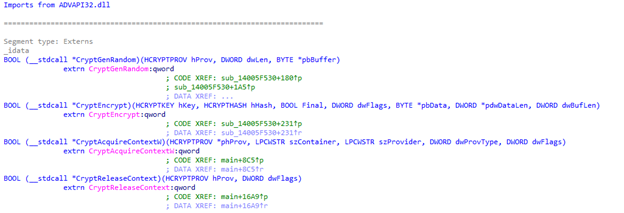
offers a visual representation of the core cryptographic operations employed by the code.

From CRYPT32.dll:
- CryptDecodeObjectEx: Decodes encoded cryptographic data structures.
- CryptStringToBinaryA: Converts encoded strings to binary data.
- CryptImportPublicKeyInfo:b> Imports public key information into a cryptographic context.
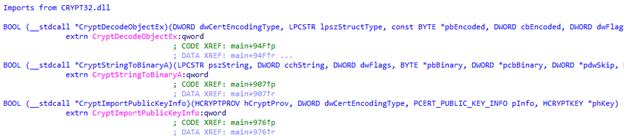
offers a visual representation of the core cryptographic operations employed by the code.
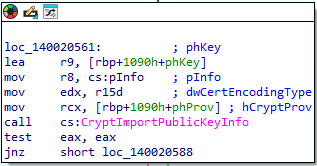
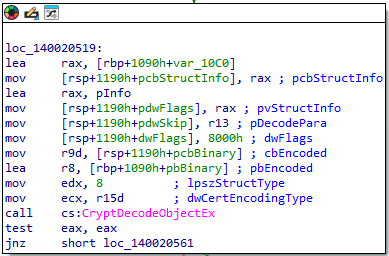
These functions enable the ransomware to perform secure communications and secure its malicious payload
Assembly Code Behavior
The ransomware's assembly code demonstrates its proper usage of the Windows Cryptography API. For example, after preparing all the necessary data and parameters, it calls the CryptEncrypt function. The main steps are as follows:
- Using movups instructions to process 128-bit memory blocks, copying data from [rbx+118h] and [rbx+128h] into xmm1 and xmm0 registers, and writing it back to memory at [rbx+138h] and [rbx+148h].
- Setting up encryption parameters such as dwBufLen (buffer length), pdwDataLen (data length pointer), and pbData (pointer to the data buffer) on the stack.
- Setting the address [rbx+470h] to 28h and flags like dwFlags and hHash to zero.
- Fetching the encryption key (hKey) from [rax+8].
After all these preparations, the CryptEncrypt function is called. Its return value determines whether the call is successful or not. If it fails, the error handling routines are called. This sequence points out Akira's careful implementation of cryptographic functions for secure data handling and protection.
Example of Ransom Note
Ransomware usually carries a ransom note in a text file readme.txt that guides the victim on how to pay the ransom and retrieve their files.
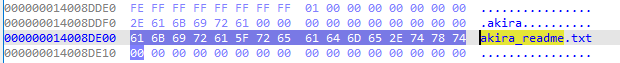
shows the readme.txt file in HEX view
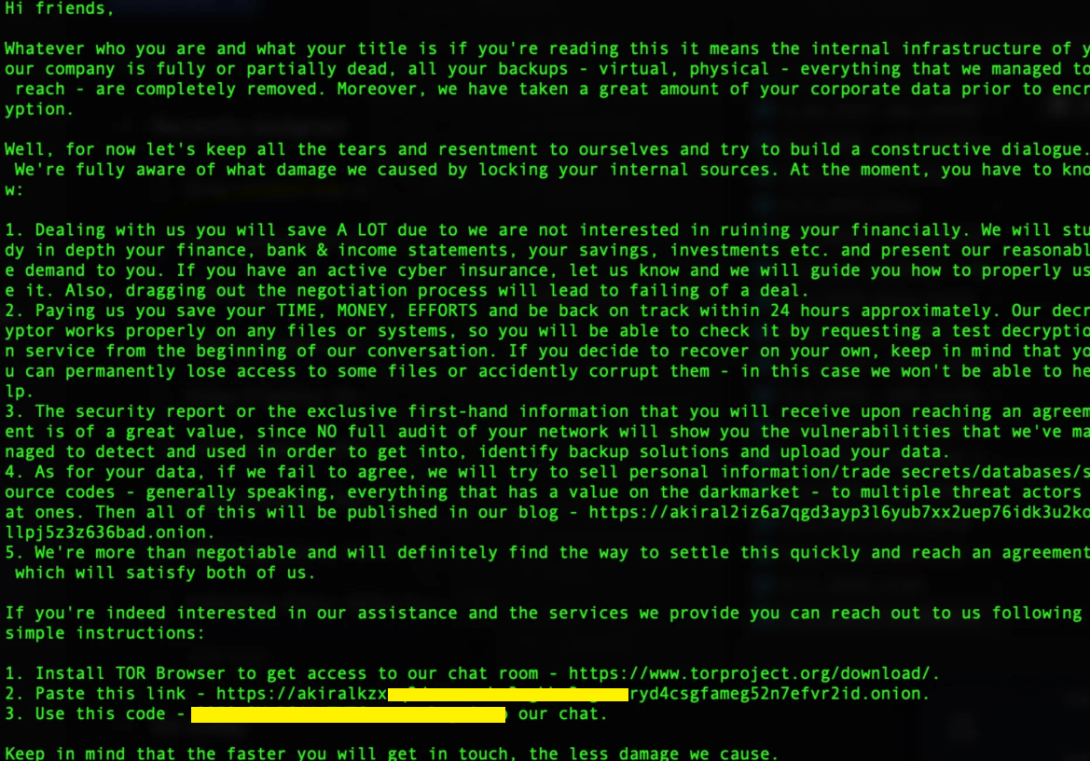
The ransom note demands a significant payment for data recovery.
Vulnerabilities Exploited
The operators of Akira ransomware have been known to exploit several high-profile vulnerabilities to gain access to systems. Some of them include:
Recent CVEs:
- CVE-2023-20269:b> Zero-day Cisco Adaptive Security Appliance (ASA) and Firepower Threat Defense (FTD) products are vulnerable to brute-force attacks.
- CVE-2023-27532: A flaw exists in the Veeam backup servers' extraction of encrypted credentials from the configuration database.
- CVE-2024-40766:b> Remote code execution is possible using the SonicWall SonicOS exploit.
Additional Exploited Vulnerabilities:
- CVE-2021-21972: Arbitrary code execution in VMware vCenter Server
- CVE-2019-6693: Code execution possibility with Citrix ADC and Gateway.
- CVE-2022-40684: Fortinet FortiOS and FortiGate arbitrary code execution vulnerability exploited
Mitigations and Recommendations
To prevent Akira ransomware, the organizations must adopt best practices to avoid such an incident as mentioned below:
- Implement Multi-Factor Authentication (MFA): Secure VPNs, RDP, and other remote access services.
- Deploy Endpoint Detection and Response (EDR): Implement the solution to detect and mitigate endpoint threats.
- Regularly Back Up Data: Ensure that the backups are stored offline or in isolated environments to prevent ransomware access.
- Security Awareness Training: Educate employees on identifying phishing and social engineering attacks.
- Apply Security Patches: Keep all systems and software up-to-date with the latest patches to mitigate vulnerabilities.
Tools used by Akira Ransomware
Akira ransomware remains one of the biggest threats to organizations globally, because of its advanced tactics, powerful encryption, and aggressive extortion practices. Knowing its evolution, technical capabilities, and exploitation strategies are critical to defend against this malware. Organizations need to be vigilant and proactive in building layered security that reduces their risk of being affected and recovers as quickly as possible in case of an attack.
Conclusion
The Akira ransomware is one of the most powerful threats to organizations worldwide because of its sophisticated tactics, robust encryption, and aggressive extortion methods. Understanding its evolution, technical capabilities, and exploitation strategies is necessary for defending against this malware.
Organizations should be vigilant and proactive in adopting layered security measures that minimize their risk and ensure rapid recovery in the event of an attack.
About us!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


