The Dark Playbook: Cyber Threats, IntelBroker Exploits, Supply Chain Attacks, and Infostealers

Advanced cyberattacks by adversaries who maximize the impact using the combination of sophisticated tools and methods are the norm. Some of the most dangerous strategies are integrating supply chain attacks, infostealer malware, and infamous threat actors, including IntelBroker and CyberNiggers. The above-mentioned groups typify the growing landscape of the cyber threat that makes use of collaboration, sophisticated tools, and strategic exploitation of vulnerabilities.
What Are Supply Chain Attacks and Infostealer Malware?
A supply chain attack targets third-party vendors or service providers to distribute malware, taking advantage of trusted relationships to infiltrate multiple organizations.With infostealer malware, attackers can gather sensitive information such as credentials and financial information.
How Supply Chain Attacks and Infostealers Fit In
There's been a relationship between supply chain attacks and infostealers since threat actors have infiltrated supply chain compromises with infostealer malware to magnify the effect of their attacks. Most of the time, the first point of infiltration is through vulnerability exploitation in trusted vendors, software developers, or distribution systems, and attackers can roll out malicious updates or software globally.
The infostealer malware implemented is designed to steal sensitive data, including account credentials, monetary information, and session tokens for exfiltration to further breach and exploit it. Data sold through dark web forums is done on a profit motivation or directly put into ransomware attacks, espionage, or sabotage attacks to amplify damages within the exploited environment.
Examples of Supply Chain Attacks:
These hacks include:
- SolarWinds (2020): Hackers inserted malware named Sunburst within the update of the software called SolarWinds Orion. This infected thousands of organizations globally.
- CCleaner (2017): Hackers breached a legitimate variant of the most popular CCleaner utility by spreading malware among millions of its users.
- Target Breach (2013): Hackers gained access to Target's network through a compromised HVAC vendor, resulting in the theft of millions of customer credit card details.
IntelBroker’s Exploitation Tactics Revealed: Insights from Emo’s Leak
A leak by the hacker called Emo made known details of the hacking methods used by IntelBroker, showing how cybercriminals steal important account information, collect sensitive data, and access sensitive systems from infostealer malware logs.
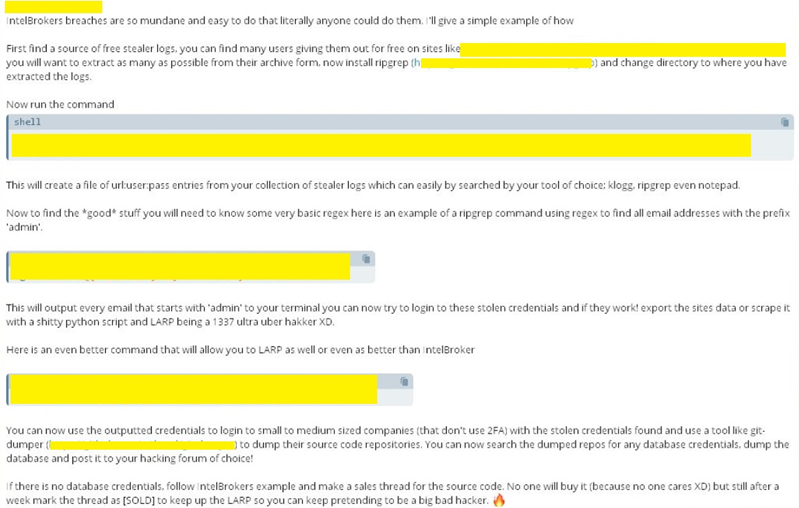
Shows about IntelBroker hacking method
Attackers have various methods of exploiting stealer logs, such as gathering, prioritizing, and misusing credentials in order to maximize their attack. Stolen logs are searched by attackers using a high-speed text search tool named ripgrep by using commands which filter the URL, Username, and Password field and gather information into a file. These found credentials are later tested on numerous platforms with great emphasis on valuable systems. Systems include high-privilege accounts with admin or organization email account details because these might have access to critical systems or databases. Regular expressions help isolate these accounts for targeted exploitation.In addition, attackers target URLs of Git repository found in the logs by utilizing commands to scan for repositories and using tools such as git-dumper to download them.
In the repositories searched, sensitive information may include database credentials, API keys, or proprietary code vulnerabilities. Such credential theft happens with wide-scale exploitation, which means that while the stolen misused credentials might be used through automation of a login for the unapproved access. It scrubs personal data, organizational details, and uses those credentials in identity impersonations for legitimate individuals. These kinds of activities permit hackers for immediate exploitation along with increasing attackers' credibility when trading or advertising this compromised information at malicious online forums.
The Role of Infostealer Malware in Cyberattacks
Malware with Infostealer types constitute a crucial part of IntelBroker hacking arsenal. Infostealer malware is designed with the intent to steal and transfer sensitive information, for instance user names, passwords, credit card information, and even session cookies. All this information is saved in stealer logs and can be accessed by threat actors for further exploitation.
Emo's leak also shows specific techniques that cybercriminals, including IntelBroker, use to exploit these stealer logs. Here is a look at how attackers filter and extract valuable data from the logs
Extracting Credentials from Logs
Attackers also use tools such as ripgrep-a high-speed text search tool to filter out the extraction of credentials from big data sets. They are searching for patterns like URL, username, password by which they can quickly compile lists of valid login credentials. For example, the following command extracts this data from a log file:
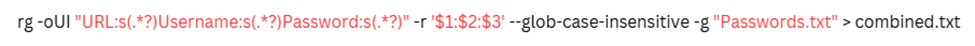
In other words, this directive will automatically collect certain information from a text file and reassemble it in a more structured way.
Targeting High-Value Accounts and Exploiting Git Repositories

Attackers focus on the high-privilege accounts. These include the admin or the organizational email account. They can target these accounts with commands such as the following regular expressions:
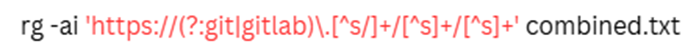
Admin accounts are prime targets because they often provide access to sensitive databases or enterprise tools. Additionally, attackers exploit Git repositories found in logs by identifying URLs with:
Once identified, tools like git-dumper are used to clone repositories and search for sensitive data such as credentials, configuration files, or vulnerabilities in code
IntelBroker and CyberNiggers: Leveraging Exploitation Tactics
IntelBroker's Advanced Tactics
Shows IntelBroker Profile
IntelBroker's operations indicate that this group operates within a strategic method of data acquisition and exploitation;
- Stealth and Autonomy: Working in solitude is used as a tactic for breach detection.
- Precise Exploitation: Critical infrastructure, as well as prominent firms like General Electric and Los Angeles International Airport are targeted.
CyberNiggers’ Collaboration

Show profile of cyberniggers on cybercrime forum
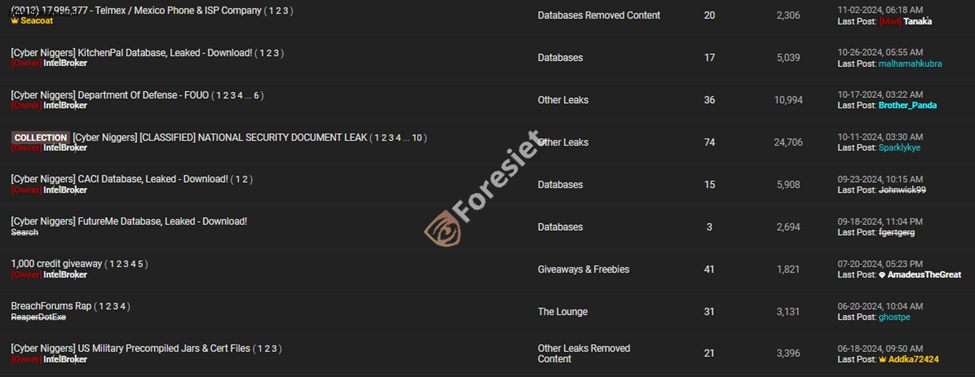
Shows CyberNiggers past activities on cybercrime forum
CyberNiggers provides IntelBroker's activities with a group-based attack that enables it to conduct mass attacks:
- Financial Institution Breaches: Steals access credentials to enter highly classified financial systems.
- Advanced Tools: It makes use of zero-day exploits and social engineering to heighten their attack.
Mitigation Strategies against These Threats
To mitigate the risks posed by supply chain attacks and infostealers, organizations can adopt several strategies aimed at strengthening their defenses and minimizing vulnerabilities.
First, it is crucial to strengthen vendor security by conducting rigorous assessments of third-party vendors and their cybersecurity practices to ensure they meet high security standards.
Deploying advanced endpoint protection, like EDR, Endpoint Detection and Response solutions can help detect and block infostealer malware before it can do significant damage. Zero trust architecture is also another essential approach, whereby the access controls are very strict so that it can verify every incoming request irrespective of its origin so that no one, including people inside the network, gets any automatic trust. Threat intelligence forms a major function in staying up-to-date with new emerging threat actor activities, for instance, by the groups of IntelBroker and CyberNiggers and the vulnerability used by these. Organizations need to regularly update vulnerability management: ensuring that their software is being constantly patched and updated to minimize possible weaknesses. Network monitoring, coupled with anomaly detection, allows organizations to find suspicious activities, like unauthorized data exfiltration or login attempts with an unusual number of failed login attempts, to alert them of the possible presence of an ongoing attack. Lastly, a well-thought-out preparedness plan in terms of incident response enables the quick detection and mitigation of breach impacts, making an attack as little impactful on operations as possible.
Common TTPs Employed in Cybercrime Operations:
Infostealers like FormBook and Emotet are commonly coupled with Credential Dumping (T1003) and Phishing (T1566) to acquire the first access and advance Credential Access.
Through Supply Chain Attacks, one can exploit Exploitation of Public-Facing Applications (T1190), and Command and Scripting Interpreter (T1059) to obtain sensitive information through exploitation of access to software or services an organization has to offer.
Exfiltration of Data is conducted by the major technique based on the mode that is adopted mostly, Exfiltration Over Web Service (T1071.001), since most groups- especially APT28 or the Lazarus Group-use APTs.
This is manifested in the latest attacks: supply chain attacks, malware infostealers, and certain cybercriminal groups, such as IntelBroker and CyberNiggers. They carry out high-valued data assets acquisition with much expertise while using malware tools in the exploitation of vulnerabilities.
In any case, to counter these constantly changing threats, organizations must proactively engage in cybersecurity measures like vendor management, advanced monitoring, and rapid response capabilities.
Conclusion
Supply chain attacks and infostealer malware with those cybercrime groups - for example, like IntelBroker and CyberNiggers - reflect the level of sophistication with which modern threats come. The bad guys are making the most out of exploiting those vulnerabilities and exploiting high-precision, sophisticated tools targeting high-value data. It's the duty of organizations to be proactive regarding cybersecurity, hence, areas on vendor management, advanced monitoring, and rapid response need to mitigate these shifting risks.
About us!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


