The Naver Deception: Analyzing Quasar RAT's Distribution through a Popular South Korean Platform

Introduction to Quasar RAT
Quasar RAT, also known as xRAT, is a malicious remote access trojan (RAT) that primarily targets Windows systems. Developed as an open-source project around 2015, it quickly garnered attention in the cybersecurity community due to its flexibility and ease of modification. Quasar RAT allows cybercriminals to gain unauthorized remote access to infected computers, making it a potent tool for espionage and theft.
How Quasar RAT Operates
The Quasar RAT is designed to provide cybercriminals with complete control over an infected system. Once installed, it can execute a range of malicious activities, including keystroke logging, stealing personal information, accessing the webcam and microphone, and managing files and processes. The RAT can also download and run additional malware, further compromising the system.
Recent Analysis by Foresiet
Our team recently analyzed a Quasar RAT infection that was distributed through a malicious website posing as a legitimate Naver site (152.32.139[.]73 - gnasdoin[.]site). This site, which mimicked the appearance of the popular South Korean platform, tricked users into downloading the malware bundled in a zip file.
What is naver site ?
Naver is a popular South Korean online platform, similar to Google. It offers a wide range of services, including a search engine, email, news, and more. In the context of QuasarRAT malware, the malicious website (152.32.139[.]73 - gnasdoin[.]site) is designed to look like a legitimate Naver site to trick users into downloading the malware.
Upon visiting these domains, users might encounter a directory listing with the following details:
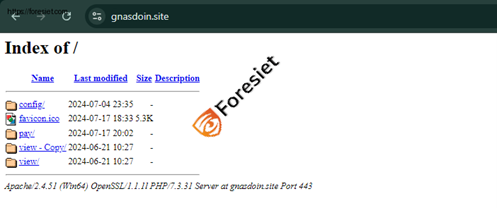
Malicious domain
Once the file named setup is downloaded and executed, it contains a batch script with the following code:
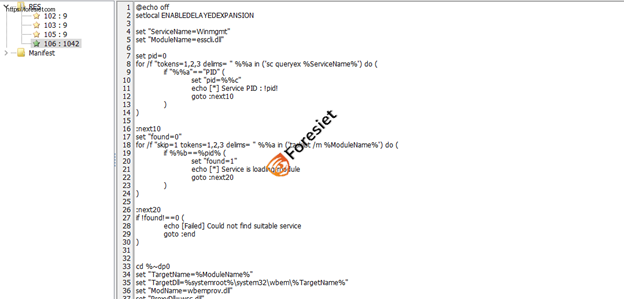
.dll malicious file
This script effectively hides the malicious activity by modifying system files and services.
Infection Vectors
Quasar RAT typically infects devices through several common methods:
- Phishing campaigns, where users download and open malicious email attachments.
- Drive-by downloads from compromised or malicious websites.
- Malicious software bundles where users install unverified software.
- Infected removable drives, such as USBs or external hard drives.
Signature Analysis
The following signatures and tactics, techniques, and procedures (TTPs) are associated with Quasar RAT:
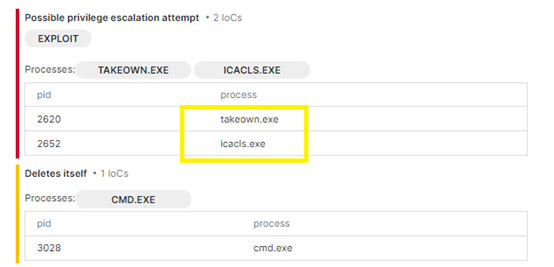
Signatures about the .dll file, Image -1
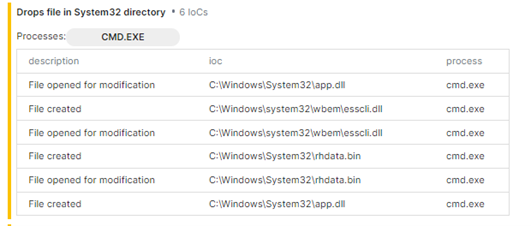
Signatures about the .dll file, Image -2
- Privilege Escalation Attempts: Detection of potential privilege escalation attempts (2 IoCs).
- Exploit Behavior: Detection of self-deletion behavior (1 IoC).
- File Modification: Modifies file permissions (1 TTP, 2 IoCs).
- Discovery: Detects VMProtect packed files (1 IoC); VMProtect commercial packer detection.
- Indicator Removal: Files deleted as part of indicator removal (1 TTP).
- Defense Evasion: Drops files in the System32 directory (6 IoCs); Drops files in the Windows directory (3 IoCs); Launches sc.exe to control services (2 IoCs); Kills processes with taskkill (1 IoC); Suspicious behaviors such as LoadsDriver (2 IoCs), AdjustPrivilegeToken (7 IoCs), and WriteProcessMemory (30 IoCs).
The malware identified targets the `System32` directory by creating and modifying suspicious files. It primarily uses `cmd.exe` to execute these actions, including creating `app.dll`, `esscli.dll`, and `rhdata.bin`, and altering their contents.
This activity indicates a potential attempt to blend malicious files with legitimate system files and evade detection. Monitoring for these specific files and unusual `cmd.exe` operations can help in detecting and mitigating this threat.
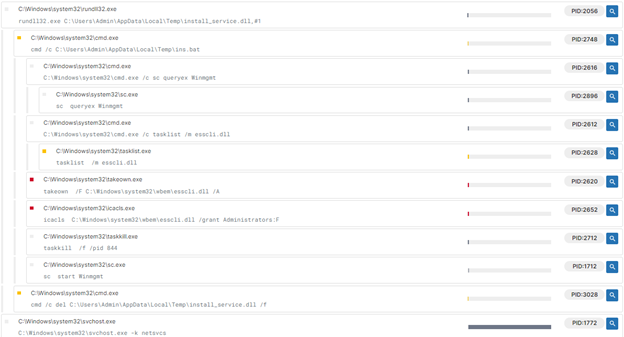
Signatures about the .dll file, Image -3
The observed malware signature reveals a series of suspicious activities indicative of a sophisticated infection. The process begins with rundll32.exe executing a DLL file from the Temp directory, a common tactic for malware to hide and operate covertly. It then runs a batch file through cmd.exe, which may carry out further malicious actions.
The malware queries and manipulates system services and tasks using commands like sc queryex Winmgmt and tasklist /m esscli.dll, potentially to identify or control processes. File permissions are adjusted with takeown.exe and icacls.exe, ensuring the malware can access or modify critical files. The final cleanup steps involve taskkill.exe to terminate processes and cmd.exe to delete its own DLL file, all aimed at erasing traces and maintaining persistence while evading detection.
YARA rule
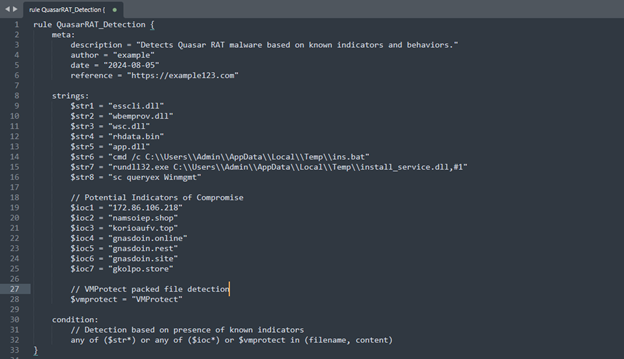
Screenshots shows about YARA rule
Precautions
To protect against Quasar RAT and similar threats, users should follow these precautions:
- Be Cautious with Emails: Avoid opening email attachments or clicking on links from unknown or suspicious senders.
- Verify Websites: Ensure you are downloading software from reputable and verified sources. Avoid visiting questionable websites.
- Regular Updates: Keep your operating system and software up-to-date with the latest security patches to close vulnerabilities.
- Antivirus Software: Install and maintain reputable antivirus software to detect and prevent malware infections.
- Backup Data: Regularly back up important data to recover it in case of an infection or data loss.
- Educate Users: Train employees and users on recognizing phishing attempts and avoiding malicious downloads.
Indicators of Compromise (IOC)
To identify potential Quasar RAT infections, monitor for the following indicators of compromise:
- Malicious IP Addresses: Unusual network traffic to IP addresses such as 172.86.106[.]218.
- Suspicious Domains: Communication with domains like namsoiep[.]shop, korioaufv[.]top, and gnasdoin[.]online.
- Unusual Files: Presence of files with names such as setup, esscli.dll, wbemprov.dll, and wsc.dll in system directories.
- Service Modifications: Changes in system services, especially if they involve renaming or replacing critical system DLL files.
- Directory Listings: Unusual directory listings on domains with Apache server banners, as seen with the malicious site gnasdoin.rest.
Mitigation and Prevention
By staying informed and practicing good cybersecurity hygiene, users can significantly reduce their risk of falling victim to Quasar RAT and other malicious threats.
For further assistance or if you suspect an infection, contact the Foresiet Threat Intelligence Team. Our experts are here to help with comprehensive analysis and response strategies.
Domains
- namsoiep[.]shop
- korioaufv[.]top
- gnasdoin[.]online
- gnasdoin[.]rest
- gkolpo[.]store
About us!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


July 1, 2025, 7:17 p.m.

July 1, 2025, 7:07 p.m.