Top 5 Stealer Logs Currently Affecting Users in 2024

In today's digital landscape, stealer logs have become a significant threat, targeting sensitive information and compromising security. At Foresiet Threat Intelligence Team, we continuously monitor and analyze these threats to help protect individuals and organizations. Here are the top 5 stealer logs currently affecting users:
What Are Infostealers?
Infostealers are a type of malware specifically designed to steal sensitive information from infected systems. This can include login credentials, credit card details, cryptocurrency wallets, browser data, and system information. Infostealers typically operate covertly, collecting data without the user's knowledge and transmitting it back to the attackers. The stolen data is then often used for financial fraud, identity theft, or sold on the dark web.
Differences between Infostealing and Ransomware Attacks
While both infostealing and ransomware attacks are forms of cybercrime, they operate differently and have distinct objectives:
- Infostealers: These focus on covertly collecting and exfiltrating sensitive information from victims. The goal is to gather data that can be used for financial gain, either through direct use or by selling the information.
- Ransomware: This type of malware encrypts the victim's data and demands a ransom for the decryption key. The primary objective is to extort money from the victim in exchange for restoring access to their data.
How Do Infostealers Work?
Infostealers typically follow a series of steps to accomplish their goals:
- Infection: The malware is delivered to the target system via phishing emails, malicious websites, or through the download of pirated software.
- Execution: Once executed, the infostealer operates silently, avoiding detection by security software through obfuscation techniques.
- Data Collection: The malware captures sensitive information such as keystrokes, stored passwords, cookies, and system details.
- Exfiltration: Collected data is transmitted back to the attacker’s command and control (C2) servers, often through encrypted channels to evade network monitoring.
- Monetization: Attackers use the stolen data for financial fraud, identity theft, or sell it on the dark web.
Private Sales on the Dark Web
The dark web serves as a marketplace for cybercriminals to buy and sell stolen data, malware, and other illicit goods. Infostealers are often sold in private sales or subscription models, allowing other cybercriminals to deploy them in their own attacks.
Prices for infostealers vary based on their capabilities and effectiveness, with more sophisticated malware fetching higher prices. These transactions are typically conducted in cryptocurrency to maintain anonymity.
Top 5 Stealer Logs Currently Affecting Users
1. RedLine Stealer
Capabilities: Written in C++ and C#, RedLine Stealer is designed to steal a wide array of sensitive information, including passwords, credit card details, cryptocurrency wallets, browser data (such as cookies and history), and system information. Its capabilities are extensive: it captures every keystroke made by the user (keylogging), extracts data from forms filled out by users (form grabbing), and steals credentials for FTP servers and email accounts.
Additionally, it can exfiltrate files from the infected system and supports customizable plugins that allow attackers to add new functionalities.
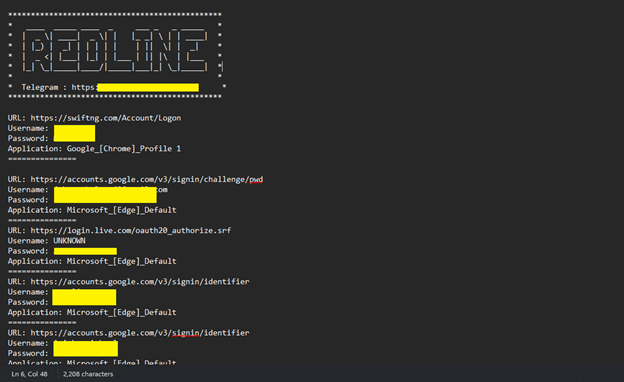
RedLine Stealer log file
Distribution: RedLine is often employed in targeted attacks aimed at specific victims. It is primarily distributed through phishing emails and malicious websites. Attackers craft convincing emails that entice users to click on malicious links or download infected attachments.
Impact: The stolen data can be used for identity theft, financial fraud, and unauthorized access to personal and corporate accounts. Victims may face severe financial losses and reputational damage, especially if corporate accounts are compromised. To evade detection by antivirus software, RedLine employs various obfuscation techniques, making its code harder to read and analyze.
2. Raccoon Stealer
Capabilities: Raccoon Stealer, written in C++ and recently in C, is adept at stealing a wide range of sensitive information, including passwords, credit card details, cryptocurrency wallets, browser data (such as cookies and history), and system information. Emerging in 2019, it has been widely recognized and extensively used within the cybercriminal community, available for purchase through a subscription model.
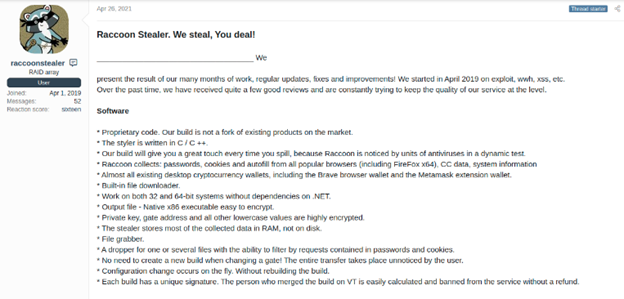
A post introducing Raccoon Stealer on a Russian-language forum
Distribution: This malware is often spread through cracked software and email attachments. Users who download pirated software are at high risk of infection.
Impact: The compromised data can lead to severe privacy breaches and potential financial losses. Stolen cookies can be used to hijack active sessions, allowing attackers to bypass authentication mechanisms and access sensitive accounts. Raccoon Stealer’s capabilities include the theft of web browser data, such as cookies, history, and saved passwords, as well as targeting popular cryptocurrency wallet software to steal digital currencies. It also possesses self-spreading capabilities, enabling it to propagate to other systems within a network.
3. Vidar Stealer
Capabilities: Vidar Stealer is a potent malware written in C++, capable of stealing a wide range of data from the compromised system. It targets personal data, web-browser data, cryptocurrency wallets, financial data, and sensitive files within user directories, communication applications, process explorer data, network communications, and more.
Malware is being sold on the dark web and underground forums as a malware-as-a-service, leveraging social media platforms as part of its C2 infrastructure to get details such as IP address, instructions, updates, and downloads.

Vidar promotion post in a Telegram chat
Distribution: Vidar Stealer is usually delivered via malvertising and exploit kits. Malicious ads and compromised websites are common vectors for this malware.
Impact: The theft of cryptocurrency wallets can result in significant financial losses, and stolen login credentials can be used for further malicious activities. Vidar’s ability to exfiltrate a wide range of data makes it a potent threat to both individuals and businesses. Its self-destruction capability after gathering all the information from the system adds to its stealth, reducing the chances of detection and analysis.
4. Agent Tesla
Capabilities: Agent Tesla is an advanced keylogger with features like clipboard logging, screen keylogging, screen capturing, and extracting stored passwords from different web browsers. It is written in .NET and supports all versions of the Windows operating system. Agent Tesla is a .Net-based Remote Access Trojan (RAT) and data stealer for gaining initial access that is often used for Malware-As-A-Service (MaaS). In this criminal business model, threat actors known as initial access brokers (IAB) outsource their specialized skills for exploiting corporate networks to affiliate criminal groups.
Web Interface of Agent Tesla
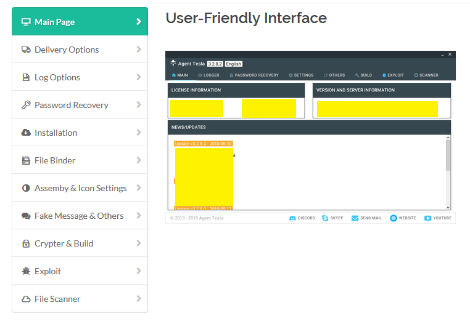
Interface of Agent Tesla
Distribution: It is commonly distributed via phishing campaigns. Attackers often use social engineering techniques to trick users into downloading the malware. Agent Tesla delivers emails attached with .zip, .gz, .cab, .msi and .img files and Microsoft Office documents with malicious Visual Basic Application (VBA) macros to compromise victim systems.
Impact: The captured data can be used for unauthorized access, espionage, and identity theft. Agent Tesla first appeared in 2014 and surged in the 2020s when it was leveraged for COVID-19 PPE-themed phishing campaigns.
Although its native second-stage capabilities are not as sophisticated as those of other malware families, it provides attackers with an easy-to-use interface to monitor the attack process and download stolen information, making it an attractive choice of malware for IABs.
5. FormBook
FormBook, also known as xLoader, is classified as a potent stealer (spyware). True to its name, it excels in form-grabbing techniques, extracting data directly from HTML forms on websites. It also adeptly steals information from keystrokes, browser autofill features, and clipboard contents, including sensitive data like credit card numbers and multi-factor authentication tokens.
Capabilities: FormBook targets Windows systems to steal credentials, take screenshots, and download additional malware. It can also log keystrokes and capture browser data, making it a comprehensive threat. FormBook is known for its versatility in staging additional malware, making it a preferred tool for complex cyber campaigns.
A post introducing for ForumBook
Distribution: It is widely distributed through email attachments and malicious websites. Users who open infected attachments or visit compromised sites are at risk. It was used in spam campaigns targeting the aerospace, defense contractor, and manufacturing sectors within the US and South Korea.
Impact: The stolen credentials and downloaded malware can lead to extensive data breaches and system compromise. FormBook’s ability to download and execute additional payloads makes it a persistent and evolving threat. The recent emergence of MalVirt loaders delivering FormBook further complicates detection and mitigation efforts.
Protecting Against Stealer Logs
To mitigate the risks posed by these stealer logs, we recommend the following measures:
- Regularly update software: Ensure all applications and operating systems are up to date with the latest security patches.
- Be cautious with email attachments and links: Avoid opening attachments or clicking on links from unknown or suspicious sources.
- Use strong, unique passwords: Employ strong passwords for all accounts and consider using a password manager.
- Enable multi-factor authentication (MFA): MFA adds an extra layer of security to your accounts, making it harder for attackers to gain access.
- Invest in comprehensive security solutions: Utilize advanced security tools and services to detect and prevent malware infections.
Conclusion
In an era where cyber threats are constantly evolving, awareness and proactive measures are crucial to safeguarding sensitive information. Stealer logs like RedLine, Raccoon, Vidar, Agent Tesla, and FormBook are formidable adversaries that require vigilance and robust cybersecurity practices.
At Foresiet Threat Intelligence Team, we are committed to providing the latest insights and solutions to help you stay ahead of these threats. Stay informed, stay secure.
About us!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


July 1, 2025, 7:17 p.m.

July 1, 2025, 7:07 p.m.