Trojan Warning: Malware Identified in VAHAN PARIVAHAN.apk

Introduction
The Foresiet Threat Intelligence Team has recently conducted an in-depth analysis of an Android malware Trojan masquerading as the "VAHAN PARIVAHAN.apk" application. This trojan poses a significant threat to users by leveraging a backdoor, utilizing the Telegram API bot, and exploiting the services of GoDaddy.com LLC and Mark Monitor Inc. In this blog, we delve into the specifics of this malware, including its technical details, behavior, and potential impact on users.
Scammers are targeting individuals through WhatsApp by sending fake text messages that claim you have been issued a traffic challan. These fraudulent messages are not from any legitimate authority. Be aware of these deceptive tactics and do not respond to or act on such messages.
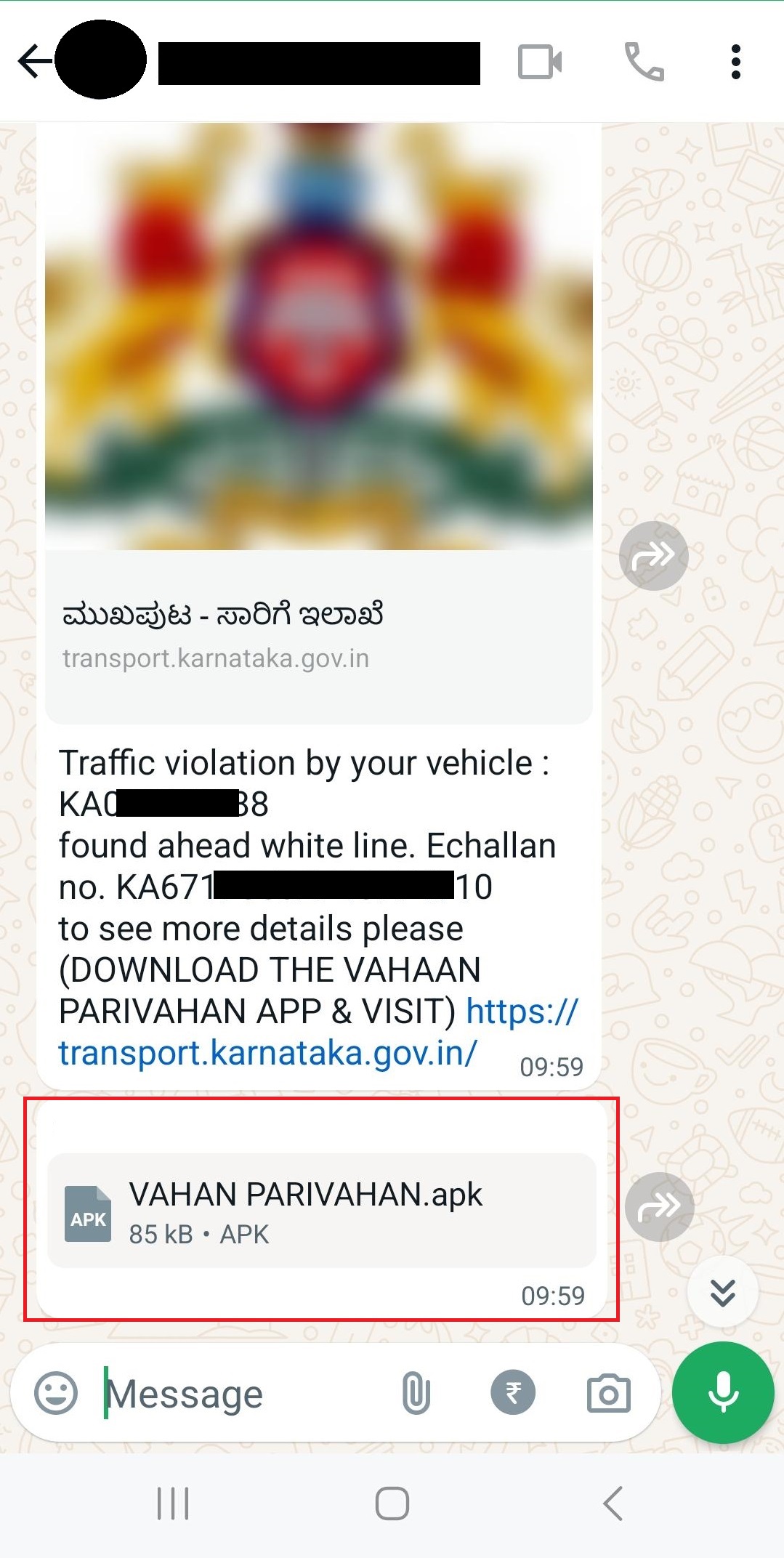
WhatsApp message
What is a Trojan?
A Trojan is named after the ancient Greek story of the Trojan Horse. Just as the Greeks used a wooden horse to sneak into Troy, cybercriminals use Trojans to gain access to a user's system by disguising the malware as something benign or useful. Unlike viruses and worms, Trojans do not replicate themselves but rely on the user to install them.
Technical Details
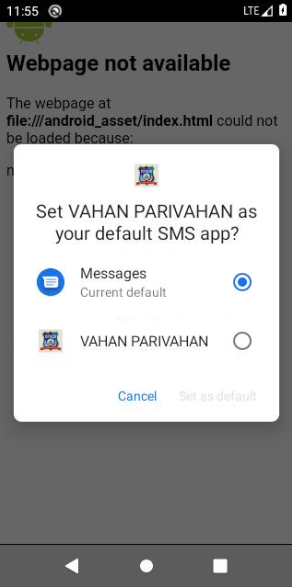
How a Trojan Works in an Android APK
An Android APK is the file format used to distribute and install applications on Android devices. A Trojan embedded in an APK can exploit this format to infiltrate a device. Here’s how it typically works:
Disguising as a Legitimate App
Trojans often disguise themselves as legitimate or desirable apps to trick users into downloading and installing them. These apps can appear to be anything from games to utility applications or even system updates.
Requesting Excessive Permissions
Once installed, the Trojan app will request a variety of permissions that seem unnecessary for its supposed function. These permissions might include access to contacts, SMS, location data, and more. Granting these permissions allows the Trojan to perform its malicious activities. For instance, the VAHAN PARIVAHAN.apk Trojan requests to be set as the default SMS app, enabling it to intercept, send, and receive SMS messages without the user's knowledge.
Performing Malicious Activities
After obtaining the necessary permissions, the Trojan can carry out its intended malicious actions. Common activities include:
- Stealing Information: Collecting data from the device, such as contacts, messages, and personal information.
- Sending SMS Messages: Sending messages to premium-rate numbers, resulting in unexpected charges.
- Monitoring Activity: Recording keystrokes, taking screenshots, and tracking user activity.
- Remote Control: Creating a backdoor to enable remote control by the attacker.
File Details:
- Size : 82KB
- MD5 : 0382a840310d987d2d45cbcba45b57a4
- SHA1 : 981f2629451778120a4f292eb8a7d601b933dff7
- SHA256 : 669ccbf03554a5c1f6e80a8ea9d8a5bae2f09ec0911bcfdf2f04c2793c968d89
- File Magic : application/vnd.android.package-archive
- SHA512 : 3d9942da2a0b01a6c3a27abb16c629f8ac3b207f808ad30874f286beb2bc779a1a5689759c9ba6d2d75202d69c779213b8a7069a2de77924fa241947052a67c1
- SSDEEP : 1536:MwWb4JVDEL3dTw4A8XsLEZarRMgGpDLF1JKhnx7F3ooQgQeosLyqML:Mw+cyxA8XsL7NrGpX7Mhnb3o1edYL
Android Application Information:
- Type : APK
- Package Name : eruyy.yrry
- Internal Version : 1
- Displayed Version : 1.0
- Minimum SDK Version : 21
- Target SDK Version : 29
Malware Behavior:
The VAHAN PARIVAHAN.apk Trojan exhibits several behaviors designed to evade detection, collect sensitive data, and persist on the infected device. These behaviors include:
Evasion and Discovery:
- Checks CPU and memory information to determine if the system is an emulator.
- Queries the mobile country code (MCC).
Data Collection:
- Reads contacts stored on the device.
- Obtains sensitive information copied to the device clipboard.
Persistence:
- Registers a broadcast receiver at runtime, typically for listening to system events.
Permissions Misused:
The trojan requests several dangerous permissions, enabling it to perform malicious activities:
- SEND_SMS : Allows sending SMS messages, potentially causing unexpected charges.
- READ_PHONE_STATE : Grants access to phone state and device IDs.
- READ_CONTACTS : Enables reading of contact data.
- RECEIVE_SMS : Permits receiving and processing SMS messages.
- ACCESS_NETWORK_STATE : Allows viewing network connections.
- INTERNET : Permits network communication, essential for exfiltrating data.
C2 Servers and Network Connections:
The trojan communicates with several Command and Control (C2) servers and domains, including:
- api.telegram.org
- clientservices.googleapis.com
- connectivitycheck.gstatic.com
- gstatic.com
- howwelltobe-default-rtdb.firebaseio.com
- markuplang-default-rtdb.firebaseio.com
- play.googleapis.com
- www.googleapis.com
IP Addresses:
- 142.251.143.106
- 142.251.143.132
- 142.251.143.138
- 142.251.143.170
- 142.251.143.202
- 149.154.167.220
Emerging Concern:
It is important to note that while VAHAN PARIVAHAN.apk may appear novel, the techniques and strategies it employs are not new. Similar trojans have been observed using the same evasion methods, data collection practices, and persistence techniques. This underlines the importance of constant vigilance and updated security measures to protect against such threats.
Analysis of the Backdoor:
The most alarming aspect of the VAHAN PARIVAHAN.apk trojan is its backdoor capability, which exploits the Telegram API bot and leverages infrastructure from GoDaddy.com LLC. This backdoor enables the threat actor to gain unauthorized access to the infected device, execute commands remotely, and exfiltrate sensitive data.
Key Characteristics of the Backdoor:
Telegram API Bot: Used for command and control communication, allowing the attacker to send and receive commands to the infected device through Telegram.
GoDaddy.com LLC and MarkMonitor Inc.: Used for domain registration and hosting, making it challenging to trace and takedown the malicious infrastructure. MarkMonitor Inc. is known for providing brand protection services, which the threat actor exploits to mask their activities under legitimate-looking domains.
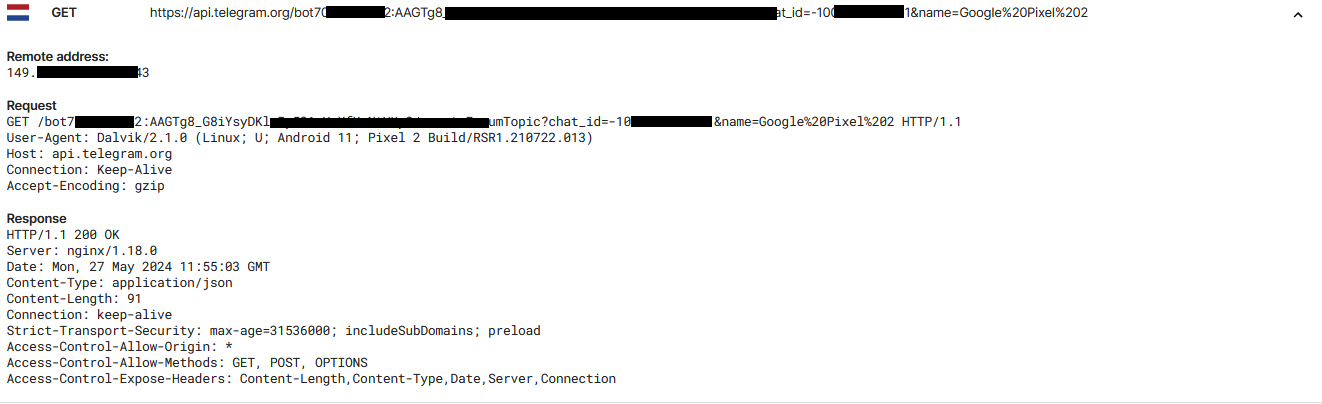
Telegram API responce
The use of legitimate services like the Telegram API bot for C2 communication is a clever tactic by the threat actors to blend malicious traffic with regular network traffic, reducing the chances of detection by conventional security tools. Similarly, using reputable domain registrars and hosting services such as GoDaddy.com LLC and MarkMonitor Inc. helps the threat actors avoid quick blacklisting and takedown efforts, prolonging their malicious campaigns.
Conclusion:
The VAHAN PARIVAHAN.apk Trojan is a sophisticated piece of malware designed to infiltrate Android devices, evade detection, and exfiltrate sensitive data. By understanding its behavior, permissions, and network interactions, users and security professionals can better defend against such threats. The Foresiet Threat Intelligence Team remains committed to uncovering and mitigating the impact of these cyber threats.
This detailed blog post aims to inform users and security professionals about the intricacies of the VAHAN PARIVAHAN.apk Trojan, providing essential insights for improved cyber security practices.
We strongly advise the general public not to respond to such messages received on WhatsApp or any other social media platform. It is crucial to avoid clicking on any direct links provided. Foresiet emphasizes the importance of staying vigilant and securing your personal information against these deceptive tactics.
About Foresiet!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


July 1, 2025, 7:17 p.m.

July 1, 2025, 7:07 p.m.