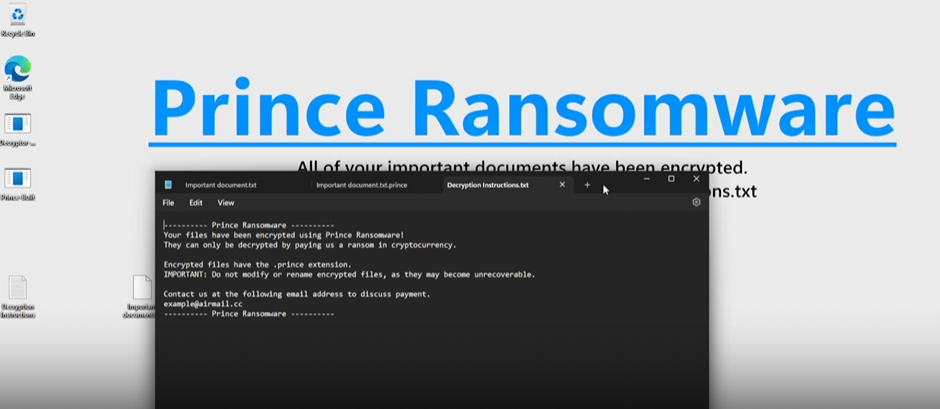
Understanding Prince Ransomware: A Comprehensive Overview

Introduction
In the ever-evolving landscape of cybersecurity threats, ransomware remains a formidable adversary. Among the recent additions to this domain is Prince Ransomware, a sophisticated piece of malware written from scratch in Go. This blog will provide an in-depth look at Prince Ransomware, its unique encryption mechanisms, the process of building and deploying it, and the ethical considerations surrounding its release as an open-source project.
What is Prince Ransomware?
Prince Ransomware is a newly developed ransomware that employs a unique combination of cryptographic techniques to encrypt files securely. Unlike many ransomware variants that repurpose existing code, Prince is written entirely from scratch in the Go programming language. Its primary aim is to render files unrecoverable by traditional recovery tools, ensuring that only the designated decryptor can restore the affected files.
Encryption Mechanisms
Prince Ransomware uses a combination of ChaCha20 and ECIES (Elliptic Curve Integrated Encryption Scheme) cryptography to achieve secure file encryption. Here’s how it works:
- ChaCha20: This stream cipher encrypts data on a byte-by-byte basis. Prince utilizes a pattern where one byte is encrypted, followed by two bytes left unencrypted. This approach is facilitated by ChaCha20's stream-based nature, making it an efficient and effective encryption method.
- ECIES: This scheme is chosen for its robust security, comparable to RSA, but with shorter key lengths. It encrypts the ChaCha20 key and nonce (a number used once), which are then prepended to the encrypted file, ensuring that decryption is only possible with the correct ECIES private key.
Building the Ransomware
Creating the encryptor and decryptor for Prince Ransomware involves a specific process:
- Running the Builder: The Builder.exe program is the core tool for generating the ransomware’s executables. It must reside in the same directory as the Encryptor and Decryptor directories.
- Generating Keys: The builder creates a unique ECIES key pair and outputs the compiled encryptor and decryptor executables to the current directory.
- Handling the Executables: The resulting Prince-Built.exe is the encryptor, which must be handled with extreme caution due to its destructive potential. The Decryptor-Built.exe is the corresponding decryptor, capable of restoring files encrypted by the Prince-Built.exe.
Main Function
main: The entry point of the program.
- Clear the console: Executes the cls command to clear the Windows console.
- Prints the startup banner.
- Generates ECIES key pair: Calls generateECIESKeyPair to create a public-private key pair.
- Prints the keys in hexadecimal format.
- Compiles the encryptor: Calls compileEncryptor with the public key.
- Compiles the decryptor: Calls compileDecryptor with the private key.
- Prints a success message.
Generate ECIES Key Pair Function
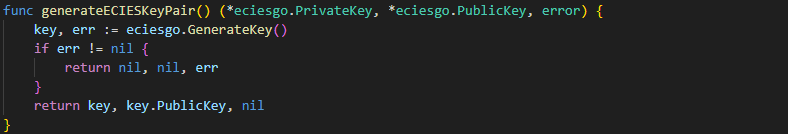
generateECIESKeyPair: Generates an ECIES key pair using eciesgo.GenerateKey().
- Returns: The private key, public key, and any error encountered.
Compile Encryptor Function
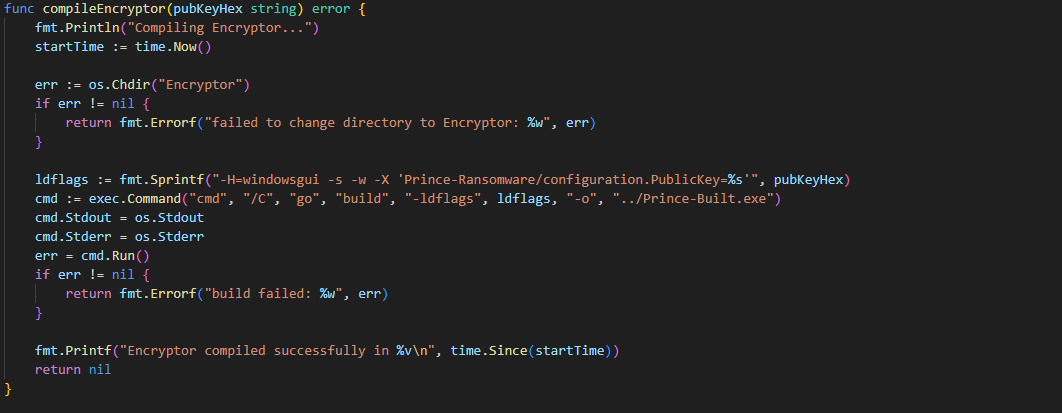
compileEncryptor: Compiles the encryptor program.
- Changes directory to "Encryptor".
- Sets build flags (ldflags) to include the public key in the binary.
- Runs go build with the specified flags to produce the executable.
- Returns: Any error encountered.
Compile Decryptor Function
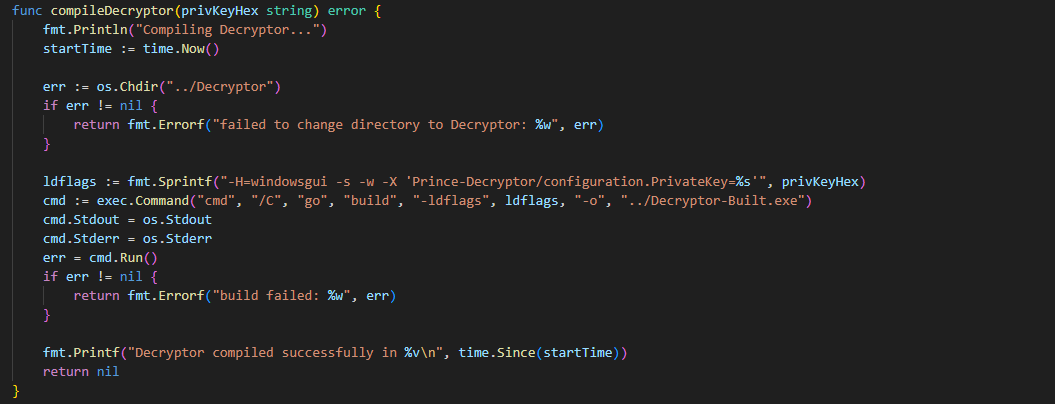
compileDecryptor: Compiles the decryptor program.
- Changes directory to "Decryptor".
- Sets build flags (ldflags) to include the private key in the binary.
- Runs go build with the specified flags to produce the executable.
- Returns: Any error encountered.
getDrives Function
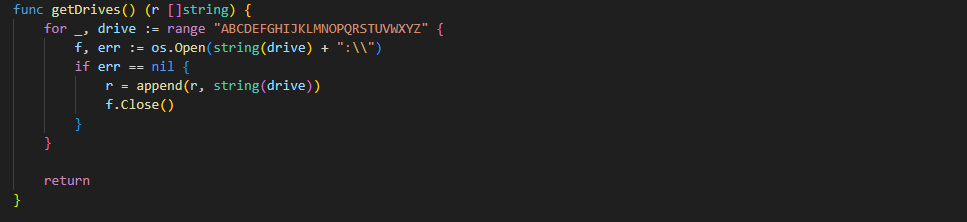
getDrives: A function to get a list of available drives.
- Loop through "ABCDEFGHIJKLMNOPQRSTUVWXYZ": Iterates through each letter to check if the corresponding drive exists.
- os.Open(string(drive) + ":\"): Tries to open the root directory of each drive.
- If successful: Appends the drive letter to the result list r.
- Closes the file: Ensures the file handle is closed.
- Returns: The list of available drives.
Encryption Process
Once deployed, Prince Ransomware follows a systematic process to encrypt files on the target system:
- Enumeration: The encryptor scans all drives on the system and iterates through each directory recursively.
- File Selection: It ignores blacklisted files, directories, and extensions, focusing only on target files.
- Encryption: For each file, a unique ChaCha20 key and nonce are generated. The file is then encrypted in the 1 byte encrypted, 2 bytes unencrypted pattern. The ChaCha20 key and nonce are encrypted using the ECIES public key and prepended to the file, ensuring secure encryption.
Benefits of ChaCha20 and ECIES
The choice of ChaCha20 and ECIES for Prince Ransomware provides several advantages:
- Efficiency: ChaCha20's stream-based encryption allows for efficient, byte-level encryption, fitting the 1:2 encryption pattern perfectly.
- Security: ECIES offers strong security similar to RSA but with shorter key lengths, making it a more efficient choice for key management and encryption.
Ethical Considerations
Releasing Prince Ransomware as an open-source project on platforms like GitHub raises significant ethical questions. However, it also presents notable benefits, particularly for the cybersecurity community:
- Research and Countermeasures: Open-source ransomware provides invaluable insights into the techniques employed by threat actors. This knowledge is crucial for developing effective countermeasures and enhancing overall cybersecurity practices.
- Simulation and Training: Security professionals can use tools like Prince to simulate real-world ransomware attacks in a controlled and ethical manner. This helps in identifying vulnerabilities and fortifying defenses.
- Community Collaboration: Open-source projects foster collaboration among researchers, enabling them to share findings and work collectively towards developing more robust defenses against ransomware attacks.
Conclusion
Prince Ransomware represents a significant development in the realm of cybersecurity threats. Its unique combination of ChaCha20 and ECIES cryptography, combined with its open-source availability, offers both challenges and opportunities for the cybersecurity community.
While the ethical implications of releasing such tools must be carefully considered, the potential benefits for research, training, and collaboration cannot be overlooked.
As we continue to confront the evolving threat landscape, tools like Prince Ransomware will play a crucial role in our ongoing efforts to understand and combat ransomware attacks.
About Foresiet!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


July 1, 2025, 7:17 p.m.

July 1, 2025, 7:07 p.m.