Understanding SharePoint Remote Code Execution Exploits

Introduction
In recent cybersecurity news, several critical vulnerabilities (CVE-2024-38094, CVE-2024-38024, CVE-2024-38023) have been discovered in Microsoft SharePoint. These vulnerabilities allow for remote code execution (RCE), which can be exploited to gain unauthorized access to SharePoint servers. This blog will provide a detailed breakdown of an exploit that leverages these vulnerabilities, showcasing how it works and the potential impact.
Introduction to SharePoint RCE Exploits
SharePoint, a widely used platform for collaboration and document management, has unfortunately been targeted by remote code execution (RCE) exploits. RCE vulnerabilities allow attackers to execute arbitrary commands on the server hosting SharePoint, potentially leading to data breaches, system compromise, and unauthorized access to sensitive information.
Exploit Overview
The exploits identified by CVE-2024-38094, CVE-2024-38024, and CVE-2024-38023 leverage specific weaknesses in SharePoint's handling of user inputs and server-side functionalities. Attackers can exploit these vulnerabilities to inject and execute malicious code remotely, bypassing authentication and gaining unauthorized access to the SharePoint server.
Understanding the Exploit Code
To illustrate the severity and technical intricacies of these exploits, let's break down the exploit scripts found in poc_filtered.py, poc_specific.py, and poc_sub.py.
Technical Breakdown
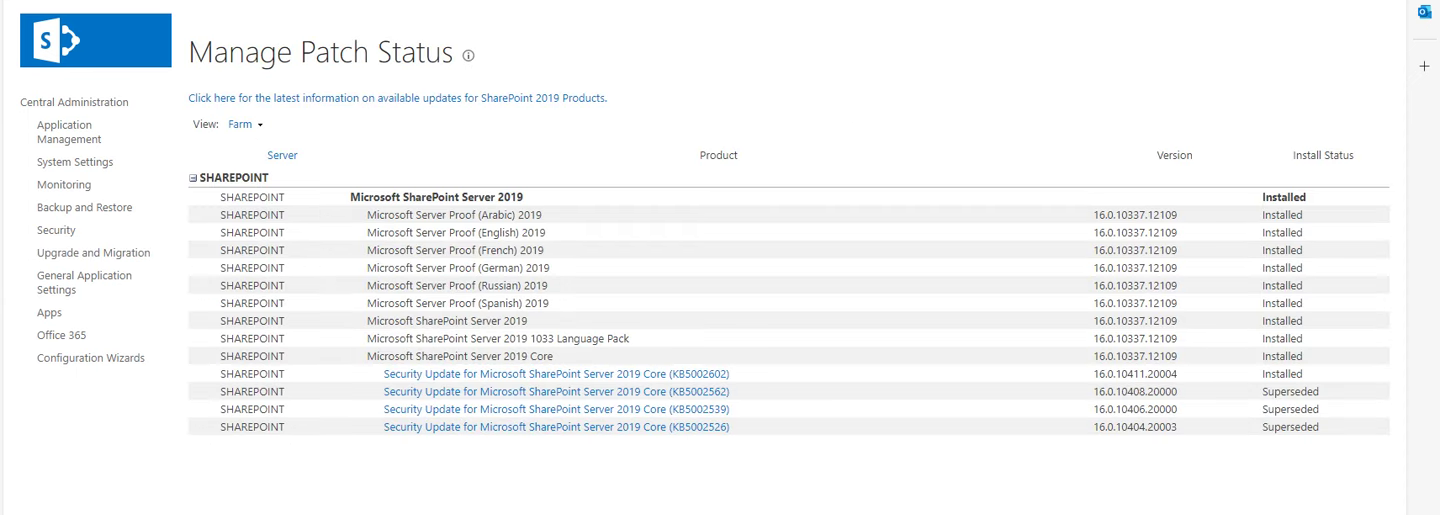
poc_filtered.py
script poc_filtered.py is designed to interact with SharePoint to perform various operations, primarily focusing on creating folders and uploading files.
- Imports and Setup: The script imports necessary modules (requests, requests_ntlm2, InsecureRequestWarning) and sets up a session with requests.session(). SSL warnings are disabled to handle insecure requests.
- Authentication: It retrieves command-line arguments (sys.argv) for the SharePoint site URL, username, and password. It uses NTLM authentication (requests_ntlm2.HttpNtlmAuth) with the provided credentials.
- Initial Authentication Check: It sends a GET request to check if the user is the site owner or if the credentials are correct. If the request returns a 401 status code, indicating unauthorized access, it checks if the credentials are incorrect and exits if so.
- Creating Folders: After successful authentication, it waits for 5 seconds (possibly to allow setup time) and then attempts to create a folder named /BusinessDataMetadataCatalog using POST requests to SharePoint's _api/web/Folders endpoint.
- Error Handling: If the folder creation fails (status code is not 201), it prints an error message indicating that the folder might already exist.
- Uploading Files: Next, the script attempts to upload a BDC metadata file (BDCMetadata.bdcm) to the newly created folder. It constructs a POST request to SharePoint's _api/web/GetFolderByServerRelativeUrl endpoint for file upload.
- Vulnerability Trigger: Finally, the script attempts to trigger a vulnerability using a POST request to SharePoint's _vti_bin/client.svc/ProcessQuery endpoint. This part of the script seems to attempt a specific operation (CreateProduct) that might be part of a vulnerability testing or exploitation process.
- Output: Throughout its execution, the script prints various status codes returned by SharePoint to indicate the success or failure of each operation.
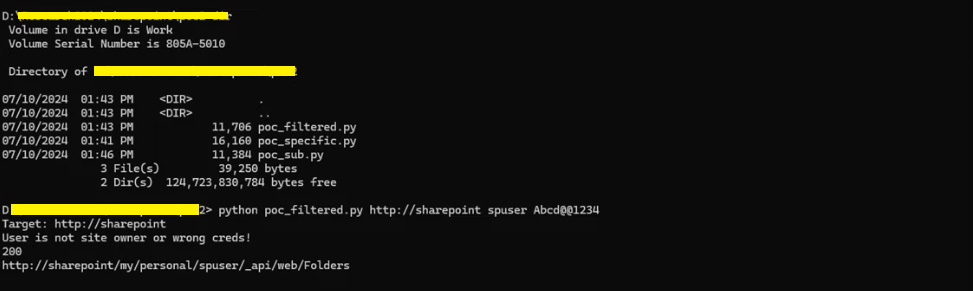
poc_specific.py
Performs operations related to SharePoint, including authentication, folder creation, and file upload.
- Importing Modules: The script starts by importing necessary modules such as requests for making HTTP requests, requests_ntlm2 for NTLM authentication, and InsecureRequestWarning from urllib3.exceptions to handle insecure requests warnings.
- Disabling SSL Warnings: SSL warnings are disabled to allow insecure requests (verify=False).
- Setting Up Session and Authentication: The script initializes a session using requests.session() and sets up NTLM authentication using requests_ntlm2.HttpNtlmAuth.
- Handling Command-Line Arguments: The script takes command-line arguments (sys.argv) for the target URL, username, and password.
- Initial GET Request: It makes an initial GET request to /my/personal/{username} to check if the user is the site owner or if the credentials are correct.
- Error Handling for Authentication: If the initial request returns a 401 status code, it checks if the credentials are wrong and exits if they are incorrect.
- Creating Folders: After verifying credentials, the script creates a folder /my/personal/{username}/BusinessDataMetadataCatalog using POST requests to SharePoint API endpoints.
- Uploading Files: It then uploads a file BDCMetadata.bdcm to the created folder using another POST request to SharePoint API.
- Vulnerability Trigger: Finally, it triggers a vulnerability using a POST request to /vti_bin/client.svc/ProcessQuery endpoint, which could exploit a vulnerability related to SharePoint.
- Output: The script prints various status codes returned by the server during its execution.
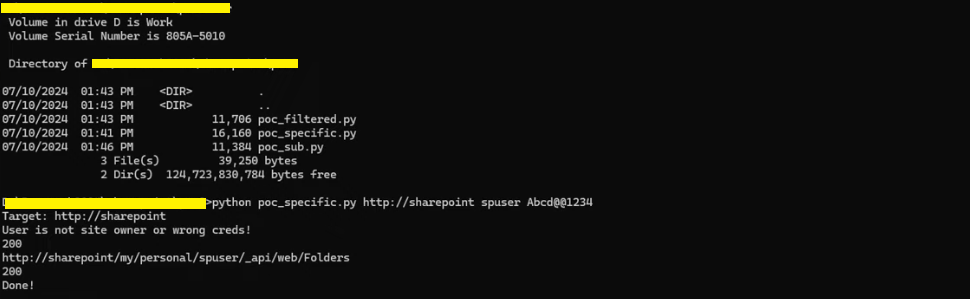
poc_sub.py
The script is designed to interact with SharePoint (SP) using NTLM authentication and perform various actions, including creating folders and triggering specific SharePoint features.
- Setup and Authentication: The script begins by importing necessary libraries (requests, requests_ntlm2) and disabling insecure request warnings. It sets up a session with requests.session() and retrieves command-line arguments (target1, username, pwd). It constructs the SharePoint site URL (target) based on the provided arguments.
- Initial Authentication Check: It attempts to authenticate using the provided credentials (auth = HttpNtlmAuth(username, pwd)). It sends a GET request to the SharePoint _api/web/ endpoint to check if the user has permissions (content = session.get(burp0_url, headers=burp0_headers, auth=auth, verify=False)). If unauthorized (status_code == 401), it retries with adjusted permissions.
- Creating SharePoint Folder: After authentication, it waits (time.sleep(5)) to set up the personal site and then attempts to create a folder (BusinessDataMetadataCatalog) using a POST request (session.post(burp0_url, headers=burp0_headers, json=burp0_json, auth=auth, verify=False)). It checks for errors during folder creation.
- Adding Features and Files: Next, it adds a SharePoint feature (session.post(burp0_url, headers=burp0_headers, json=burp0_json, auth=auth, verify=False)), and creates a BDC metadata file (session.post(burp0_url, headers=burp0_headers, data=burp0_data, auth=auth, verify=False)). It handles responses and prints status codes for debugging.
- Exploiting SharePoint Vulnerability: Finally, the script triggers a vulnerability in SharePoint by executing a method (session.post(burp0_url, headers=burp0_headers, data=burp0_data, proxies=PROXY)). It constructs a specific XML payload (burp0_data) to exploit the vulnerability and sends a POST request to /client.svc/ProcessQuery.
Mitigation Strategies
To protect against these SharePoint RCE exploits, organizations should consider the following measures:
- Patch Management: Regularly update SharePoint installations with the latest security patches and updates from Microsoft.
- Access Controls: Implement strong access control policies to limit user privileges and restrict unauthorized access to critical SharePoint resources.
- Security Monitoring: Deploy intrusion detection systems (IDS), web application firewalls (WAFs), and comprehensive logging to detect and respond to suspicious activities.
Conclusion
In conclusion, the exploitation of CVE-2024-38094, CVE-2024-38024, and CVE-2024-38023 underscores the importance of proactive cybersecurity measures in defending against remote code execution vulnerabilities in SharePoint.
By understanding these exploits and implementing robust security practices, organizations can better safeguard their SharePoint deployments from malicious attacks.
About Foresiet!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


