Unmasking the Silent Threat: Info Stealer Malware and the Danger of Stealer Logs

Info stealer malware, also known as information stealers, are a growing menace in the cybersecurity landscape. These malicious programs lurk in the shadows, siphoning sensitive data from unsuspecting victims' devices. While data breaches often grab headlines, info stealer attacks can be just as devastating, silently compromising personal information and causing significant financial losses.
This blog post sheds light on the world of info stealer malware and the chilling reality of stealer logs. We'll explore:
- How Info Stealers Work: Demystifying their methods for stealing valuable data.
- The Value of Stealer Logs: Understanding why stolen data is a valuable commodity for cybercriminals.
- Real-World Examples: A glimpse into recent info stealer incidents (without disclosing specific victims).
- Protecting Yourself and Your Organization: Practical steps to mitigate the risk of info stealer attacks.
How Info Stealers Work
Info stealers are versatile and can be deployed through various means, including:
- Phishing emails: Clicking on malicious links or attachments can download info stealers onto your device.
- Drive-by downloads: Visiting compromised websites can unknowingly trigger the download of info stealer malware.
- Malicious software bundles: Free software downloads may come bundled with hidden info stealers.
Once installed, info stealers operate discreetly in the background, often going unnoticed. They can steal a wide range of data, including:
- Login credentials (usernames and passwords)
- Financial information (credit card details, bank account numbers)
- Personal identification details (names, addresses, Social Security numbers)
- Browser cookies and browsing history
- Email content and attachments
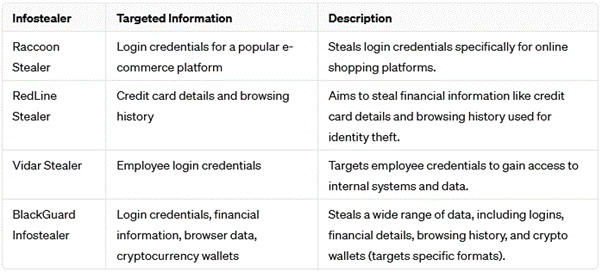
Info Stealer Attacks
few examples of info stealer:
- Raccoon Stealer:
In 2019, Raccoon made its presence known cybercriminal forums, offering subscription packages tailored to different durations and budgets. These included options such as $499 (US) for four months, $200 for one month, and a 'trial' week priced at $75. The affordability of these subscriptions, coupled with Raccoon's established reputation for reliability and effectiveness, proved highly enticing to a wide array of less sophisticated threat actors. This appeal was further accentuated by the potential return on investment (ROI) facilitated by the resale or misuse of pilfered credentials and cryptocurrency wallets.
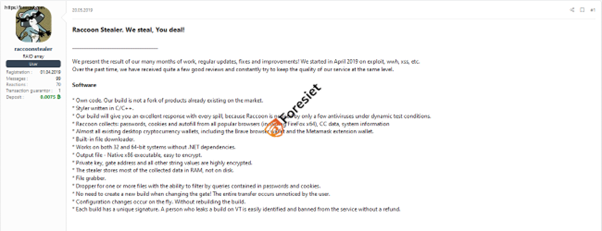
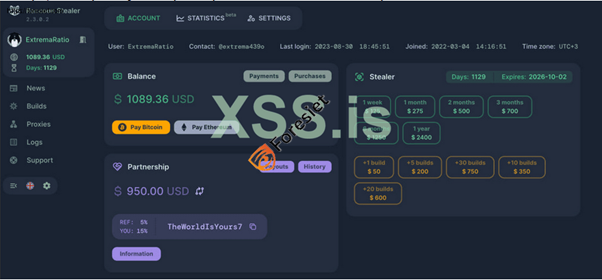
Raccon Stealer Interface 2.3.0.2
On February 4th, 2023, Raccoon Stealer announced the launch of version 2.1, marking the end of beta testing. This update brings enhanced stability, expanded functionality, and an improved user interface.
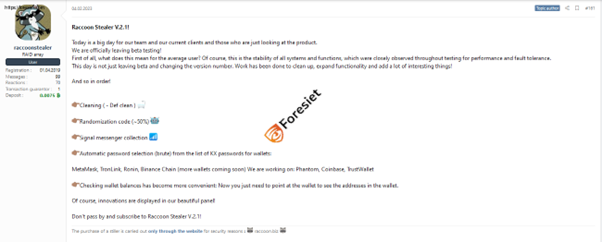
New version of Racoon Stealer V.2.1!
In February 2024, this info stealer targeted the login credentials for a popular e-commerce platform. If successful, this attack could allow criminals to hijack accounts, steal financial information such as credit card details and banking logins, and make fraudulent purchases.
- RedLine Stealer:
On February 19th, 2020, Glade user from the cybercriminal forum known as Glade released REDLINE STEALER. They introduced it as a style specifically crafted for efficient log management, gathering essential information crucial for various operations. This program was meticulously developed, incorporating feedback from seasoned individuals immersed in the realm of carding. Rental options are available at $150 USD per month, while a perpetual Pro version is offered at $900 USD.
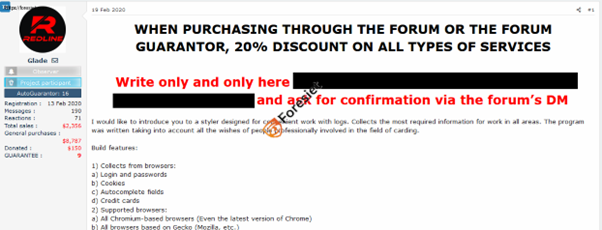
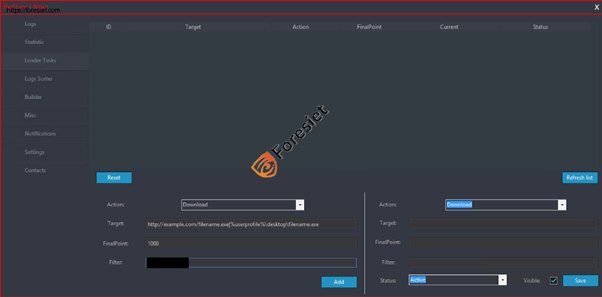
Interface of redline
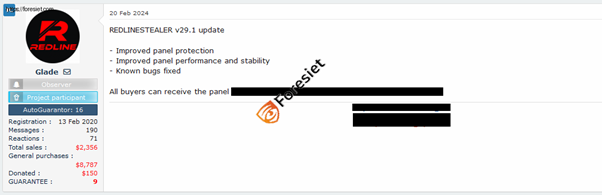
He recently announced the latest update for REDLINE STEALER malware, designated as version 29.1. This update boasts enhancements in panel protection, performance, and stability, along with the resolution of known bugs. Additionally, there has been a reduction in subscription prices for REDLINE: monthly subscriptions are now priced at $100, while the PRO version costs $600. These prices will remain unchanged until the launch of the RedStackRat project, after which they will be subject to revision and potential increases.
In January 2024, RedLine Stealer stole credit card details and browsing history from a travel booking website. This information is a goldmine for criminals. Not only can they use the credit card details to make unauthorized purchases, but the browsing history can also be used to target the victim with further phishing attacks or to identify other accounts they may have.
- Vidar Stealer:
Vidar made its debut in November 2018 and continues to be a prevalent and widely utilized information stealer. Its operators manage a support Telegram channel under the handle @Vidar_supwwh, where they market the software for USD 1500 and provide supplementary installation services. Recent reports from KELA have also identified Vidar being utilized in newly discovered bots on RussianMarket and TwoEasy.

In December 2023, Vidar Stealer was used to steal employee login credentials from a small business. Access to these credentials could allow attackers to launch further attacks within the company's network, steal confidential data such as trade secrets or customer information, or disrupt operations by locking employees out of critical systems.
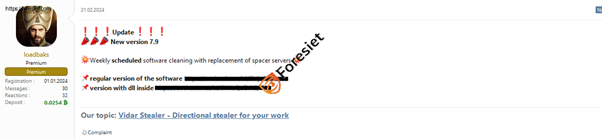
Latest version of Vidar Stealer 7.9 posted on 21.02.2024 undetectable by antivirus https://avcheck.net/id/2Idjn2plsuy2
- BlackGuard Stealer
In the ever-evolving landscape of cybersecurity threats, perpetrators constantly strive to enhance the capabilities of their malicious tools, seeking greater effectiveness and efficiency. A significant example is the emergence of the BlackGuard stealer, which first appeared in early 2021.
Furthermore, individuals participating in discussions related to such topics may face consequences, including being banned from various platforms, as part of enforcement measures implemented by platform operators.


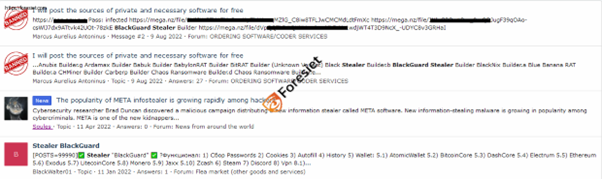
Private Stealers
- Highly Customized: These info stealers are created for specific targets or campaigns. Attackers might modify existing info stealer code or build them from scratch to target unique data or bypass detection mechanisms.
- Limited Distribution: Private stealers are not widely available and are often used in targeted attacks against specific organizations or individuals.
- Evasion Techniques: They may employ advanced techniques to avoid detection by security software. This could involve obfuscating their code, using zero-day exploits (previously unknown vulnerabilities), or constantly updating their functionality.
How to Protect Yourself from Info stealers
There are a number of steps you can take to protect yourself from info stealer attacks:
- Be Wary of Phishing Attacks:
Phishing emails are a common way for info stealers to be delivered. Don't click on suspicious links or attachments, and be cautious of unsolicited emails.
- Practice Strong Password Hygiene:
Use unique and complex passwords for all your online accounts. Consider using a password manager to help you create and manage strong passwords.
- Enable Multi-Factor Authentication (MFA):
MFA adds an extra layer of security by requiring a second verification step beyond your password.
- Keep Software Updated:
Regularly update your operating system, applications, and web browsers to patch security vulnerabilities that info stealers might exploit.
- Use a Reputable Security Solution:
Invest in a robust security solution that includes real-time threat protection and can detect and block info stealers.
By following these tips, you can significantly reduce your risk of falling victim to an info stealer attack.
Building a Secure Future with Foresiet
At Foresiet, we understand the evolving threat landscape and the criticality of protecting your data from info stealers and other cyber threats. Our comprehensive security solutions combine advanced technology with human expertise to identify and neutralize threats before they can cause harm.
Conclusion
In conclusion, stealer malware poses a significant threat due to its covert data-harvesting nature. Unlike ransomware that disrupts operations, stealer malware silently steals valuable information like logins, financial data, and personal details. This stolen information can be used for identity theft, financial fraud, or further attacks.
There are various types of stealer malware, and they can infect systems through phishing emails, malicious websites, software vulnerabilities, and infected downloads. To protect yourself, practice caution with emails, browse safely, update software regularly, use a good antivirus, download wisely, and enable two-factor authentication for your accounts.
By being aware of stealer malware and taking preventive measures, you can significantly improve your online security posture and safeguard your sensitive information.
Contact Foresiet today to discuss how we can help you safeguard your data and build a more secure digital future.
About Foresiet!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


