Unveiling the Nestle Data Breach: A Deep Dive into R00TK1T's Threat

In the ever-evolving landscape of cybersecurity threats, the recent breach by the notorious hacker group R00TK1T serves as a stark reminder of the vulnerabilities faced by even the most established organizations. As the Foresight Threat Team delves into the details of this alarming incident, it becomes imperative to shed light on the implications and lessons to be learned from this breach.
The Breach: Targeting Nestle
R00TK1T, a threat actor group known for its sophisticated cyber operations, has once again made headlines with its brazen attack on Nestle, one of the world's largest food and beverage companies. Claiming to have infiltrated Nestle's security infrastructure, R00TK1T alleges the exposure of sensitive internal information, striking at the heart of the multinational corporation. The group's assertion of leaking confidential data from Nestle on a private data channel under its control sends shockwaves through the cybersecurity community. With the potential compromise of proprietary information, customer data, and internal communications, the ramifications of this breach extend far beyond the confines of Nestle's network.
The Response: Foresiet Threat Team Investigation
As news of the breach spreads, the Foresiet Threat Team swiftly mobilizes to investigate the extent of the intrusion and assess the impact on Nestle's security posture. Combining cutting-edge cybersecurity tools with expert analysis, our team endeavors to uncover the root cause of the breach and provide actionable insights to mitigate future risks.
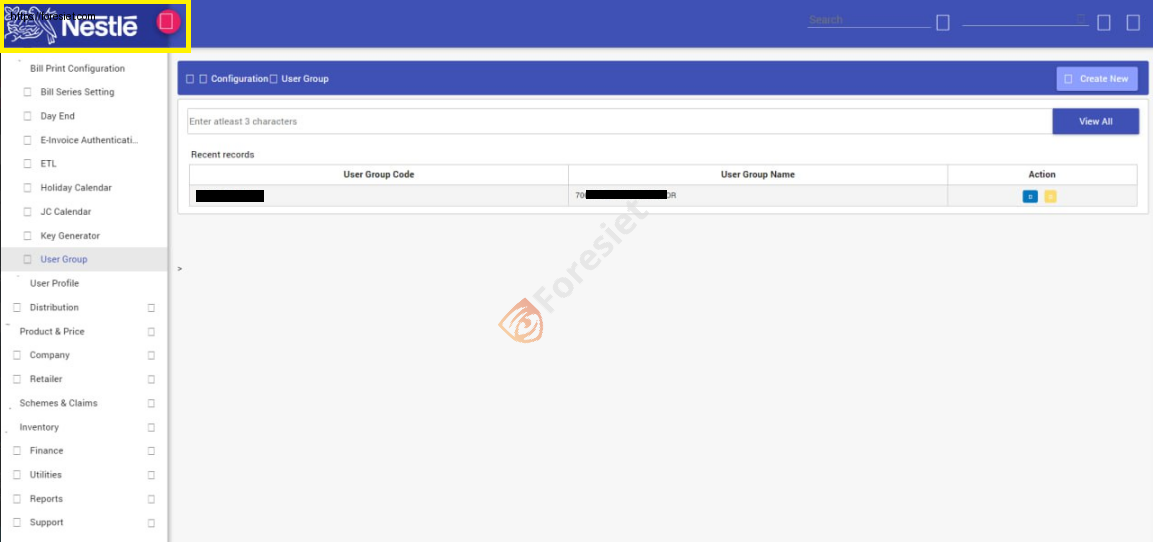
Through meticulous forensic analysis and threat intelligence gathering, the Foresiet Threat Team uncovers the sophisticated tactics employed by R00TK1T to bypass Nestle's defenses. From exploiting vulnerabilities in third-party software to employing social engineering tactics, the attackers demonstrate a high level of sophistication and persistence in their pursuit of sensitive information.
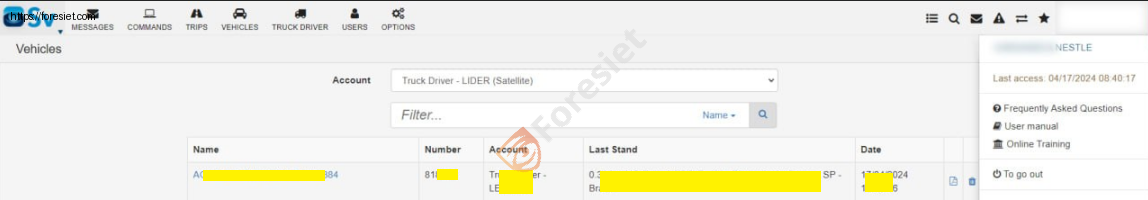
the company's vehicles Tracking system
R00TK1T Cyber-Attacks of the Past
R00TK1T has a track record of exploiting vulnerabilities across various sectors, leveraging both technical weaknesses and insider knowledge. Their targets span diverse industries, including education, healthcare, and transportation. Previous cyber-attacks attributed to R00TK1T include:
Qatar Airways Cyber-Attack
The group allegedly accessed sensitive documents and aviation software, highlighting vulnerabilities in the airline's digital infrastructure.
Lebanese Government Cyber-Attack
R00TK1T breached government websites, exposing classified data and sparking concerns over national security.
Sodexo Cyber-Attack
In a display of audacious threats, R00TK1T aimed to disrupt operations at Sodexo's South African branch, raising alarms about the group's capability to cause chaos.
Nestle Breach
The recent breach at Nestle underscores the persistent threat posed by R00TK1T. Claiming to have accessed confidential information, the group's actions raise questions about the adequacy of Nestle's cybersecurity measures and the broader implications for consumer trust and data security.
R00TK1T Hacking Group Threatens Malaysia
On January 26th, targeting Malaysian infrastructure. This ominous message was further disseminated on the dark web, issuing a stark warning of impending chaos and urging the populace of Malaysia to brace themselves for potential infrastructure disruptions. The hackers' proclamation asserted a chilling reality.
Key lessons emerge from this incident
- Strengthening Cyber Defenses: Organizations must adopt a proactive approach to cybersecurity, prioritizing robust defense mechanisms, regular vulnerability assessments, and employee training programs to mitigate the risk of breaches.
- Third-Party Risk Management: As demonstrated in the Nestle breach, third-party vendors and partners can serve as potential entry points for attackers. Implementing rigorous third-party risk management protocols is essential to safeguarding sensitive data.
- Incident Response Preparedness: In the face of a cyberattack, swift and effective incident response is paramount. Establishing incident response plans, conducting regular drills, and collaborating with external cybersecurity experts can help organizations minimize the impact of breaches.
- Heightened Vigilance: Cyber threats are dynamic and ever-evolving, requiring constant vigilance and adaptation. Organizations must remain vigilant against emerging threats, continually reassessing their security posture and implementing proactive measures to stay ahead of adversaries.
Moving Forward: A Call to Action
As the cybersecurity landscape continues to evolve, the Nestle data breach serves as a clarion call for organizations to prioritize cybersecurity and adopt a proactive approach to risk management. By leveraging advanced threat intelligence, robust defense mechanisms, and a culture of cybersecurity awareness, organizations can strengthen their resilience against emerging threats and safeguard their most valuable assets.
Conclusion
As the digital landscape becomes increasingly perilous, proactive measures are essential to safeguard against cyber threats. The Foresiet Threat Team remains vigilant in detecting and mitigating risks, offering comprehensive solutions to fortify defenses and mitigate the impact of potential breaches. By staying informed and proactive, organizations can navigate the complex cybersecurity landscape with confidence and resilience.
About Foresiet!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


July 10, 2025, 9 a.m.
