VGod Ransomware Analysis: Golang-Based Threat with ChaCha8 and AES Encryption, Persistence, and Mitigation

Introduction
Ransomware remains one of the most pressing cybersecurity threats, affecting individuals and organizations worldwide. Among the latest ransomware strains making headlines is VGOD ransomware, known for its advanced encryption techniques and aggressive attack methods. In this blog, we will explore the workings of VGOD ransomware, recent incidents, and the critical lessons organizations must learn to protect against such threats.
What is VGOD Ransomware?
VGOD ransomware is a highly sophisticated malware designed to encrypt files on an infected system, rendering them inaccessible until a ransom is paid. This strain utilizes ChaCha8 and AES encryption algorithms to lock files, the ransomware is written in Go (Golang).adding a .locked extension to affected data.
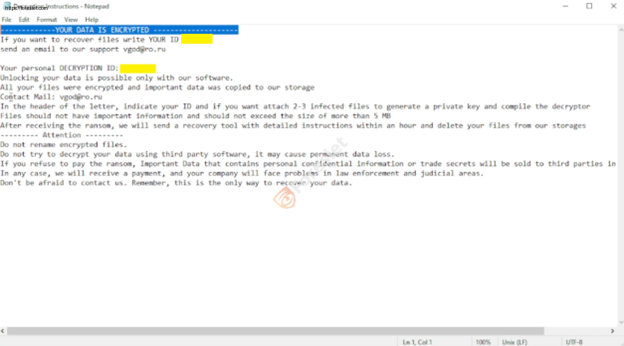
A ransom notes titled Decryption Instructions.txt is then created, containing payment demands and decryption instructions.
Unlike some ransomware variants, VGOD ransomware exhibits persistence mechanisms, ensuring it remains operational even after system restarts. It modifies the Windows registry and employs process manipulation techniques to evade detection and removal.
How Vgod Ransomware infects computers
VGod Ransomware, like many other ransomware variants, utilizes multiple infection vectors to compromise systems. It often infiltrates computers through phishing emails containing malicious attachments or links, designed to trick users by mimicking legitimate communications. Additionally, cybercriminals may exploit vulnerabilities in outdated software to deploy the ransomware silently. Other infection methods include compromised websites, malicious advertisements, and downloads from untrustworthy sources. Once executed, VGod encrypts files and demands a ransom, threatening permanent data loss or exposure if payment is not made.
To mitigate such threats, it is essential to keep software updated, practice cautious browsing habits, and implement strong cybersecurity defenses.
Key Technical Details
1. File Encryption Process
Upon execution, VGOD ransomware scans and encrypts files using ChaCha8 and AES encryption.
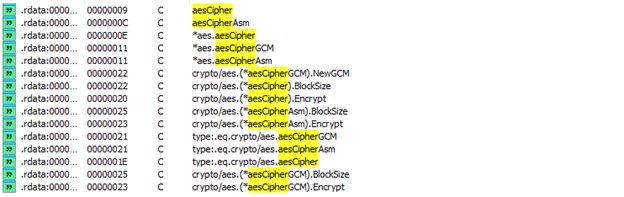
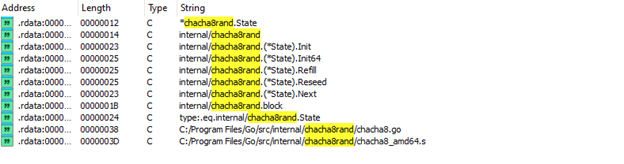
Key API calls involved include:
- CreateFileA/W – Accesses target files before encryption.
- ReadFile – Reads file contents before encryption.
- WriteFile, syscall.WriteFile, os.write – Overwrites original files with encrypted data.
- DeleteFileA – Deletes original files post-encryption, preventing recovery.
2. Ransom Note Creation
Unlike other ransomware that commonly use readme.txt,
VGOD ransomware generates a ransom note titled Decryption Instructions.txt.
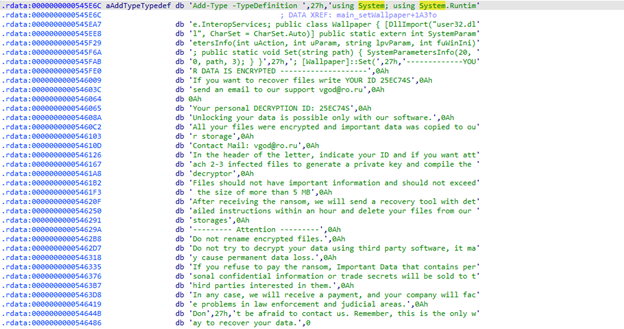
The VGod Ransomware ransom note serves as an encryption notification, informing victims that their files have been encrypted and providing instructions for recovery. It includes a unique personal decryption ID (e.g., "YOUR personal DECRYPTION ###### ") to identify each affected user. Victims are instructed to contact the attackers via email, with specific contact addresses provided for further communication.
The note also outlines several instructions, such as limitations on file size for decryption testing, warnings against renaming encrypted files, and advisories against using third-party recovery tools. Additionally, it employs threatening language, warning victims of permanent data loss if they fail to comply and even referencing potential legal consequences for refusing to follow the instructions.
This file contains:
- Payment instructions
- Contact details of attackers
- Threats regarding data exposure if payment is not made
3. Persistence Mechanisms
he ransomware, inferred to be named "VGod" based on the sample name, utilizes a dual encryption scheme combining ChaCha8 and AES to lock victims' files securely.
Once encryption is complete, affected files are renamed with the .locked extension, rendering them inaccessible without the necessary decryption key.
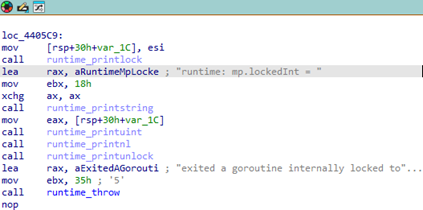
logs a debugging message about mp.lockedInt, then throws a fatal runtime error if a goroutine exits while still being internally locked to an OS thread. This suggests that it's part of Go’s runtime scheduler, handling thread-affinity issues, which can occur when a goroutine that was locked to a system thread exits improperly.
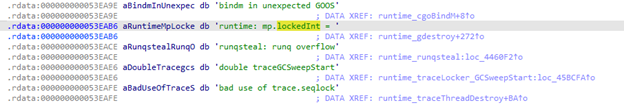
This is likely related to Go’s runtime.LockOSThread(), which prevents a goroutine from migrating between threads, ensuring it stays on the same OS thread. If a go routine that was locked exits unexpectedly, Go triggers a fatal panic (runtime_throw).
Unlike the commonly used "readme.txt" ransom note, this variant drops a file titled "Decryption Instructions.txt," which likely provides details on how victims can recover their files, usually by paying a ransom in exchange for the decryption key.
4. Anti-Forensics and Evasion Techniques
To prevent recovery and detection, VGOD ransomware employs the following:
- Backup Deletion – Executes vssadmin.exe delete shadows /all or wmic shadowcopy delete to remove Volume Shadow Copies.
- Direct System Calls – Uses syscall.WriteFile, os.write instead of standard APIs to evade detection by security tools.
The extracted data consists of character strings (C type), primarily referencing file-related functions. The rightmost column contains variations of the string "WriteFile", including:
- syscall.WriteFile
- syscall.writeFile
- os.WriteFile
- WriteFile
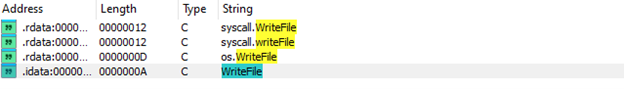
The extracted data consists of character strings (C type), primarily referencing file-related functions such as syscall.WriteFile, syscall.writeFile, os.WriteFile, and WriteFile. The variations in capitalization suggest that these may represent distinct functions within different libraries or modules, with syscall.WriteFile likely interacting with low-level system calls and os.WriteFile serving as a higher-level abstraction. These functions indicate file-handling operations, which could involve writing, modifying, or creating files. In the context of reverse engineering or security analysis, identifying such calls can provide valuable insights into a program’s behavior.
If present in a suspicious binary, they might suggest malicious file operations, such as data exfiltration, ransomware encryption, or persistence mechanisms, making them a crucial element in malware analysis.
Mitigation Strategies
Mitigating the impact of VGod ransomware requires a combination of preventative measures, detection strategies, and recovery techniques. Organizations should implement regular data backups to ensure the availability of critical files in case of an attack. These backups should be stored offline or on a secure, cloud-based solution with restricted access to prevent tampering. Network segmentation is essential to prevent lateral movement in case of infection, ensuring that compromised systems do not affect the entire infrastructure.
Deploying endpoint detection and response (EDR) solutions can help identify malicious activity related to file encryption, registry modifications, and unauthorized process executions. Monitoring suspicious API calls such as WriteFile, CreateFileA/W, and RegSetValueExA can provide early warnings of ransomware activity. Additionally, behavioral-based detection methods should be employed to detect anomalies such as rapid file modifications and bulk renaming of files.
To prevent initial infection, user education and phishing awareness training must be conducted regularly. Many ransomware infections begin with social engineering tactics, such as phishing emails containing malicious attachments or links. Enforcing email security policies, including spam filtering and attachment scanning, can reduce the risk of malware execution. Application whitelisting can prevent unauthorized binaries, such as ransomware executables, from running on critical systems.
System hardening techniques, such as disabling unnecessary services and enforcing least privilege principles, can reduce the attack surface. Regular patch management and vulnerability assessments should be performed to mitigate known exploits that ransomware operators may leverage. Restricting script execution policies, such as disabling macros in Office documents and blocking PowerShell execution for non-administrative users, can further limit the execution of malicious scripts used in ransomware attacks.
Finally, organizations should have a well-defined incident response plan in place. If an attack occurs, infected systems must be immediately isolated from the network to prevent further spread. Security teams should analyze the attack using forensic tools and attempt recovery using secure backups rather than paying the ransom.
Engaging law enforcement and cybersecurity experts can provide additional support in dealing with ransomware incidents and identifying possible decryption solutions.
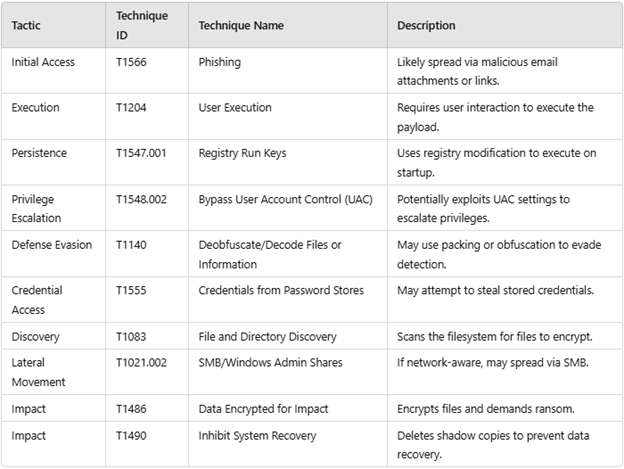
MITRE ATT&CK Techniques
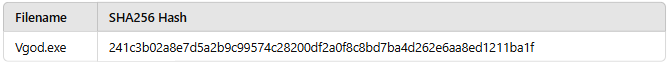
Sample Hash Information
Conclusion
VGod ransomware is a highly destructive malware that encrypts files using ChaCha8 and AES algorithms, appends a .locked extension, and demands ransom through Decryption Instructions.txt. It employs registry modifications for persistence and attempts to delete backups to increase the chances of victims paying the ransom.
Cybersecurity professionals should monitor API calls related to file access (WriteFile, CreateFileA/W) and registry modifications (RegSetValueExA). Additionally, disabling vssadmin.exe execution for unauthorized processes can help mitigate damage.
Regular backups, robust endpoint protection, and proactive network monitoring remain the best defenses against such ransomware attacks.
About us!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


July 1, 2025, 7:17 p.m.

July 1, 2025, 7:07 p.m.