Wayne Memorial Hospital Falls Victim to Monti Ransomware Attack

Wayne Memorial Hospital Targeted in Recent Cyber Attack
Wayne Memorial Hospital, a 114-bed not-for-profit healthcare facility in Honesdale, Pennsylvania, recently fell victim to a severe cyber attack. The notorious Monti gang, known for their sophisticated ransomware operations, claimed responsibility for this breach, once again highlighting the vulnerabilities in critical healthcare infrastructure.
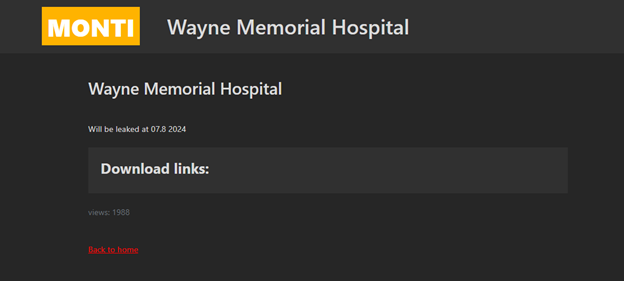
The attack on Wayne Memorial Hospital underscores the growing threat that ransomware poses to essential services. This incident not only disrupts the hospital's operations but also puts patient data and healthcare services at significant risk.
As cyber attacks on healthcare facilities become more frequent and severe, it is imperative to understand the perpetrators and their methods to better defend against such threats.
Monti Ransomware: The New Conti Successor
The Monti group has been active since June 2022, emerging shortly after the notorious Conti ransomware gang ceased its operations. Researchers have noted multiple similarities between the tactics, techniques, and procedures (TTPs) of Monti and Conti, suggesting a possible link or direct inspiration.
In fact, Monti operators have based their encryptor on the Conti’s leaked source code, further cementing the connection between the two groups.
In August 2023, Monti ransomware operators resurfaced with a new Linux version of their encryptor. This variant has been employed in attacks targeting organizations in the government and legal sectors, demonstrating Monti's evolving threat landscape and adaptability.
Understanding Monti Ransomware
Monti ransomware is designed to encrypt data and demand payment for the decryption tools, following the modus operandi of its predecessor, Conti. The public leak of Conti's source code and associated tools in February 2022 provided a blueprint for cyber criminals to replicate and innovate upon.
Consequently, Monti might not be the only group leveraging the Conti leaks, but it is currently one of the most prominent.
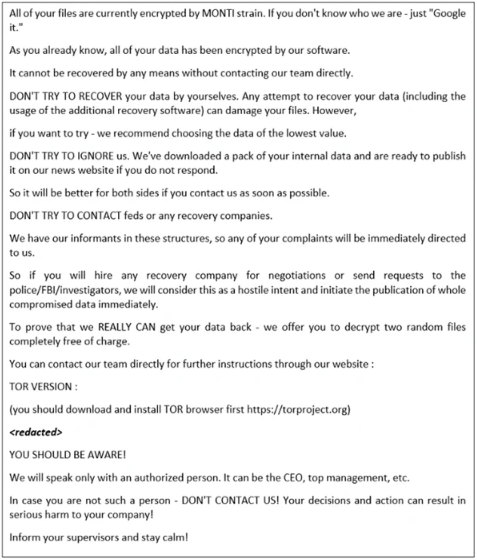
Monti encrypts files by appending a five-character random extension to filenames. For instance, a file named "1.jpg" would appear as "1.jpg.PUUUK" after encryption. Upon completing the encryption process, Monti leaves a ransom note named "readme.txt," demanding payment in exchange for the decryption tools.
The Implications for Healthcare and Beyond
The attack on Wayne Memorial Hospital is a stark reminder of the critical need for robust cybersecurity measures across all sectors, especially in healthcare. The Foresiet Threat Intelligence Team urges all organizations to review their security protocols, implement advanced threat detection systems, and conduct regular cybersecurity training for their staff.
As ransomware groups like Monti continue to evolve and adapt, staying informed and prepared is crucial. By understanding the threats and taking proactive steps, we can better protect our essential services and sensitive data from the ever-growing cyber threat landscape.
How Does Ransomware Infect Computers?
Ransomware can infiltrate computers through various methods, including:
- Phishing Emails: Cybercriminals send deceptive emails that contain malicious attachments or links. Once opened, these attachments or links can download and install ransomware on your computer.
- Drive-by Downloads: Simply visiting a compromised website can trigger an automatic download of ransomware onto your system without your knowledge.
- Social Engineering: Attackers trick users into downloading ransomware through fake software updates or deceptive pop-ups.
- Exploited Vulnerabilities: Cybercriminals exploit unpatched software vulnerabilities to gain access to systems and deploy ransomware.
- Infected USB Drives: Ransomware can spread through infected USB drives when they are plugged into a computer.
- Peer-to-Peer Networks:b> Downloading files from peer-to-peer networks can expose your system to ransomware hidden within the downloaded content.
- Weak or Stolen RDP Credentials: Cybercriminals can use weak or stolen Remote Desktop Protocol (RDP) credentials to access and infect systems remotely.
Protecting Your Computer from Ransomware
To safeguard your computer from ransomware attacks, consider the following precautions:
- Be Cautious with Emails: Avoid opening email attachments or clicking on links from unknown or suspicious sources.
- Keep Software Updated: Regularly update your operating system, applications, and antivirus software to patch known vulnerabilities.
- Use Strong Passwords: Implement strong, unique passwords for all accounts and consider using a password manager.
- Regularly Back Up Data: Maintain regular backups of your data on external drives or cloud services to ensure you can restore your system if needed.
- Install Reputable Security Software: Utilize reliable antivirus and anti-malware programs to detect and prevent ransomware infections.
- Educate Yourself About Cyber Threats: Stay informed about the latest cyber threats and security practices to recognize and avoid potential risks.
Conclusion
The recent ransomware attack on Wayne Memorial Hospital serves as a stark reminder of the persistent threat posed by cybercriminals. Understanding the methods used by ransomware groups like Monti and implementing robust cybersecurity measures are critical steps in protecting our essential services and sensitive data.
The Foresiet Threat Intelligence Team remains committed to providing comprehensive insights and solutions to help organizations defend against cyber threats. By staying informed and proactive, we can collectively strengthen our defenses and mitigate the impact of future cyber attacks.
About Foresiet!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


July 10, 2025, 9 a.m.
