Zero-Day in Your ZIP: Inside CVE-2025-33028: How a WinZip Flaw Exposes Users to Silent Malware Execution

Introduction: The Silent Power of ZIP Files
In the vast landscape of cybersecurity, it’s often not the zero-click iPhone exploits or flashy ransomware variants that expose the most users — sometimes it’s the tools we’ve trusted for decades. One such example is CVE-2025-33028, a vulnerability in WinZip, a program that’s been a staple in personal and corporate environments for over 30 years.
This blog post explores CVE-2025-33028 — a vulnerability that allows attackers to silently remove Windows security flags (Mark-of-the-Web or MotW) from files during ZIP extraction. We’ll walk through the technical behavior, demonstrate the exploit using real screenshots, and analyze its implications for targeted attacks, including military and espionage operations.
What is CVE-2025-33028?
CVE-2025-33028 is a flaw that impacts how WinZip processes files stamped with Mark-of-the-Web (MotW) — a Windows security feature that stamps files downloaded from the web. When a MotW-stamped file is opened, Windows (or utilities such as Microsoft Office) notifies the user or opens it in Protected View to avoid automatic code execution.
The vulnerability: Extracting a ZIP file containing MotW using exploitable versions of WinZip (such as v21) will not preserve the MotW flag for files within the archive. This enables attackers to insert evil files such as .docm (macro-containing Word documents) into ZIPs that evade Microsoft Office's Protected View.
Affected Software:
- WinZip 21.0 – 27 (as per public PoC)
- Potentially others (research ongoing)
Technical Breakdown: How the Exploit Works
Let's do a step-by-step walkthrough in a lab testing environment. Our test used the following:
- WinZip 21.0
- Windows 10 (64-bit)
- Sample payload: malicious.docm (macro-enabled Word document)
- Zip file: test_archive.zip
Step 1: MotW Tagging
When a ZIP file is remotely downloaded from the internet (i.e., downloaded through a web browser), MotW is appended automatically by Windows. This is seen in the file's Properties under Security.
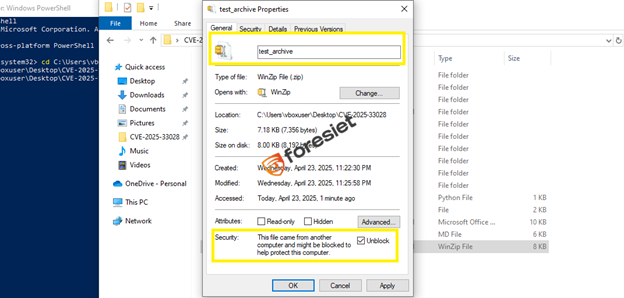
Screenshot 1: test_archive.zip showing “properties showing MotW tag.”
Step 2: Extraction using WinZip
Using vulnerable WinZip version 21.0, we extract the file to a local directory:
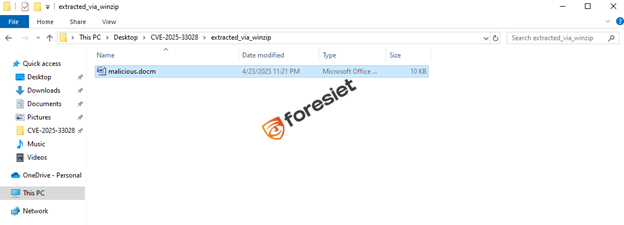
C:\Users\vboxuser\Desktop\CVE-2025-33028\extracted_via_winzip
Step 3: Examining Extracted Payload
We now examine the extracted file malicious.docm → Properties.
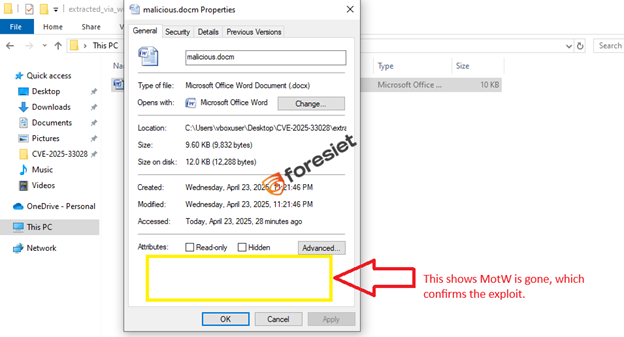
Screenshot 2: malicious.docm — the “Unblock” checkbox is missing
This demonstrates the crux of the vulnerability: WinZip has removed the MotW. In regular behavior, this file ought to have preserved the MotW flag and cautioned the user when opening it.
Contrastingly, programs such as WinRAR and the Windows native extractor properly preserve the MotW flag on extraction, blocking this type of bypass. This vulnerability makes legitimate-looking ZIP attachments zero-click phishing vectors.
What Makes This Dangerous?
This flaw converts legitimate-looking ZIP attachments into zero-click phishing attacks. After extraction, malicious payloads (such as DOCM, HTA, or JS files) can run without warning — allowing macro execution, script injection, or malware installation.
Threat Actor Usage
If packaged in phishing emails:
- A fraudulent invoice or job offer with a DOCM within a ZIP might execute malicious code without Protected View.
- PowerShell scripts or backdoors within HTA or JS files may run directly.
Military or Espionage Use Cases
This CVE has nation-state-level potential, particularly in:
- Targeted spear phishing attacks on defense contractors or journalists
- Supply-chain compromise: Masked as project ZIPs being sent to developers or vendors
- Espionage against critical infrastructure, evading Windows security layers without exploits
Since the user opens the ZIP and clicks the DOCM, security solutions often log it as a legitimate action — making forensic detection harder.
Detection & Mitigation
Detection:
- Seek out discrepancies between ZIP MotW and internal file indicators
- SIEM rules may detect .docm, .hta, .js opened from ZIPs w/o MotW
Mitigation:
- Don't use vulnerable WinZip versions (update to latest version)
- Use Windows' built-in extractor or WinRAR, which save MotW appropriately
- Turn Attack Surface Reduction (ASR) rules on to prevent Office macros from untrusted sources
Conclusion
CVE-2025-33028 isn't a matter of code exploitation — it's a matter of exploiting trust and undernoticed behavior in aged software. When every phishing technique is under observation, this CVE enables attackers to fly under the radar.
By learning and illustrating this weakness, we emphasize the way even old, well-established tools such as WinZip can become avenues for today's attacks — and why technical analysis, as demonstrated above, is vital to blue teams, red teams, and all those in between.
Resources & References
- [CVE-2025-33028 - NVD]
(https://nvd.nist.gov/vuln/detail/CVE-2025-33028)
- [PoC GitHub Repository]
(https://github.com/EnisAksu/Argonis/blob/main/CVEs/CVE-2025-33028%20(WinZip)/CVE-2025-33028.md)
- [Microsoft Docs: Mark-of-the-Web]
(https://learn.microsoft.com/en-us/windows/win32/secauthz/mark-of-the-web)
About us!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


July 1, 2025, 7:17 p.m.

July 1, 2025, 7:07 p.m.