XDSpy Cyber Espionage Campaign Targets Russian and Moldovan Entities in July 2024

In July 2024, the cyber espionage group XDSpy launched a targeted attack against Russian companies and a potential target in Moldova. The campaign involved sophisticated phishing tactics, where attackers sent emails containing links to download RAR archives. These archives included a legitimate executable file and a malicious dynamic link library (DLL) named msi.dll.
The attackers employed the DLL Side-Loading technique, leveraging the legitimate executable to load and execute the malicious DLL. This DLL, identified as part of the XDSpy.DSDownloader family, acted as a loader for the campaign's payload.
Targeted Entities in Russia and Moldova
The attack targeted a Russian IT company specializing in software for cash registers and possibly an organization in Tiraspol, Transnistria. The use of a decoy document, which was extracted and saved to the user's directory, served to distract the victim while the malicious activities took place in the background.
Key Functionalities of XDSpy.DSDownloader Malware
The XDSpy.DSDownloader malware exhibits several key functionalities, including copying the msi.dll and the legitimate executable to the "C:\Users\Public" directory and creating a registry key entry to ensure persistence. The malware also downloads a payload file from a malicious server, using a specific User-Agent string mimicking legitimate browser traffic.
While the payload file was unavailable at the time of investigation, the campaign's intent and methods highlight the continued threat posed by sophisticated cyber espionage groups like XDSpy.
Potential Payload and RAR Archive Contents
Based on previous attacks by the XDSpy group, it is assumed that the phishing emails in this malicious campaign were intended to deliver a RAR archive containing the XDSpy.DSDownloader malware. However, the RAR archives were unavailable at the time of the study, preventing direct analysis of the contents.
RAR Archive Analysis
The RAR archive typically contains two executable files in the PE32+ format:
- pdf_20240615_00003645.exe (pismo-22-07-2024_0001.exe): This is a legitimate executable file (SHA256: b77a9c7250397242df5956213a17ec0149ba836d64640e7b2a0068a2e6b2cf9e), identified as the IntegratedOffice.exe application version 16.0.17328.20124. It carries a valid digital signature, which helps it bypass security checks.
- msi.dll: This is a malicious dynamic link library loaded when the legitimate executable file specified above is launched. The msi.dll file is designed to facilitate the deployment of the XDSpy.DSDownloader malware by leveraging the legitimate application's processes.
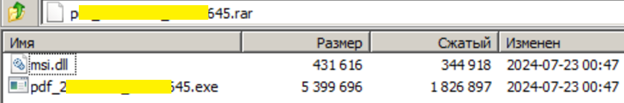
Example of RAR Archive Contents
The combination of these files within the RAR archive demonstrates the group's use of sophisticated techniques, including the DLL Side-Loading method, to mask malicious activities behind legitimate software. This method not only helps evade detection but also exploits trust in well-known applications.
Functional Features of XDSpy.DSDownloader
The XDSpy.DSDownloader malware is characterized by several key functionalities:
- Decoy Document Extraction: The malware extracts a decoy document from the RCDATA resource and saves it in the user directory (%USERPROFILE%). This document is then opened to distract the victim, allowing the malicious actions to proceed unnoticed.
- File Copying to Public Directory: It copies the msi.dll file along with a legitimate executable file to the "C:\Users\Public" directory. This step is crucial for the DLL Side-Loading technique to work, as it ensures the malicious DLL is loaded when the legitimate executable is run.
- Persistence Mechanism via Registry Key: The malware creates a registry key parameter under [HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] with the value pointing to the legitimate executable file in the public directory. This setup ensures that the malware is executed at system startup. For example:
csharp
[HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] pdf_20240615_00003645.exe = "C:\Users\Public\pdf_20240615_00003645.exe" - Payload Downloading: XDSpy.DSDownloader downloads a payload file from a malicious server using a specific User-Agent string to mimic legitimate browser traffic:
scss
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/123[.]0[.]0[.]0 Safari/537.36 The downloaded payload is saved in the "C:\Users\Public[az]{8}.exe" format, with an example being "C:\Users\Public\zwrdntjl.exe". - Executing the Payload: Once downloaded, the payload file is executed. However, the specific payload file was unavailable at the time of investigation, preventing further analysis.
Important Strings and Obfuscation Techniques
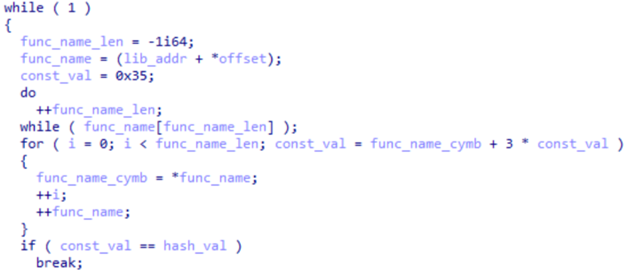
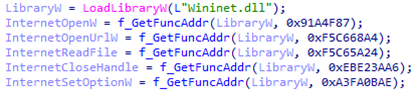
The malware contains several important strings in plaintext, including the names of the decoy document, legitimate executable, malicious DLL, payload file, registry key, public directory path, payload download link, and User-Agent header line. Additionally, the names of called WinAPI functions are hashed using a simple algorithm, adding a layer of obfuscation to hinder analysis and detection.
In this example, the malware first loads the necessary module (e.g., "kernel32.dll") using the LoadLibrary function. After successfully loading the module, it retrieves the address of the required WinAPI function using the GetProcAddress function.
Domains and URLs
- Domains:
- protej[.]org
- nashtab[.]org
- URLs:
- hxxps://protej[.]org/zpwidnydav/?e&n=bVq7NwlXhjYOMT
- hxxps://protej[.]org/zpwidnydav/?n=wHFbIDNW9YutX
- hxxps://nashtab[.]org/biyasqbuk4/?e&n=GuVZoipdI2UIxk
- hxxps://nashtab[.]org/pqwebyug3/?n=PDVXCGFwWnCaNv
IP Addresses
- 89.114.69[.]65
- 89.114.69[.]48
- 82.221.129[.]24
- 185.56.136[.]50
- 159.100.6[.]5
File Paths
The following file paths are associated with the XDSpy.DSDownloader malware:
- Executable Files:
- C:\Users\Public\pdf_20240615_00003645.exe
- C:\Users\Public\pismo-22-07-2024_0001.exe
- C:\Users\Public\zwrdntjl.exe
- C:\Users\Public\spbbpzmq.exe
- C:\Users\Public\yvpxqixd.exe
- Malicious DLL:
- C:\Users\Public\msi.dll
- Decoy Documents:
- %USERPROFILE%\pdf_20240615_00003645.pdf
- %USERPROFILE%\pismo-22-07-2024_0001.pdf
Registry Keys
The following registry keys are used by XDSpy.DSDownloader for persistence:
- [HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
- pdf_20240615_00003645.exe = "C:\Users\Public\pdf_20240615_00003645.exe"
- ppismo-22-07-2024_0001.exe = "C:\Users\Public\pismo-22-07-2024_0001.exe"
Summary
The XDSpy cyber espionage campaign utilizes various indicators of compromise to execute and maintain its malicious presence. By monitoring and analyzing these domains, IP addresses, file paths, and registry keys, organizations can better detect and respond to the XDSpy threat.
Ensuring comprehensive security measures and up-to-date defenses is essential to protect against such sophisticated cyber threats.
Conclusion
The XDSpy cyber espionage campaign of July 2024 underscores the advanced capabilities of modern threat actors. By leveraging sophisticated phishing tactics, DLL Side-Loading, and obfuscation techniques, XDSpy demonstrates the need for robust cybersecurity measures and heightened vigilance against advanced persistent threats (APTs).
Organizations must remain proactive in their defenses to mitigate the risks posed by such sophisticated cyber threats.
About us!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


July 10, 2025, 9 a.m.
