How Banshee Stealer is Redefining macOS Cyber Threats and Data Theft

Introduction
MacOS, often regarded for its robust security measures, has increasingly become a target for sophisticated cyber threats. Among the latest examples is Banshee Stealer, a malware engineered to compromise macOS systems by extracting sensitive user information. Developed by Russian cybercriminals and offered at a premium subscription fee of $3,000 per month, this malware underscores the growing attention of threat actors toward macOS platforms. With the rise of such threats, cybersecurity risk assessment and dark web monitoring services are crucial for protecting sensitive data and preventing cyber attacks. Leveraging cyber threat intelligence can help businesses stay ahead of emerging threats and safeguard their systems.

Shows the advertisement of banshee Stealer on cyber crime forum
Summary
Banshee Stealer, analyzed by researchers at Foresiet, is a macOS-specific malware targeting both x86_64 and ARM64 architectures. Its primary focus lies in harvesting sensitive information, including passwords, browser data, and cryptocurrency wallets, while employing techniques to evade detection. The following analysis delves into its features, delivery mechanisms, and market positioning, offering insights into its implications for individuals and organizations.
Banshee Stealer has recently gained attention due to its emergence as a significant threat targeting macOS devices. Discovered in August 2024, With the increasing threat of cybersecurity risks and the growing need for digital risk protection, organizations must adopt cyber risk management software and dark web monitoring to safeguard sensitive data and prevent future attacks.
Key Features of Banshee Stealer
Targeted Systems: Designed exclusively for macOS, Banshee Stealer is compatible with both x86_64 and ARM64 architectures.
Data Collection: It harvests sensitive information, including user passwords, files from the Desktop and Documents folders, browser history, cookies, and logins from nine major browsers such as Chrome, Firefox, and Edge. While limited to cookie collection on Safari, it also targets cryptocurrency wallets like Wasabi Wallet, Exodus, and Ledger, alongside data from around 100 browser extensions.
Delivery and Exfiltration: Stolen data is compressed and encrypted into ZIP archives before being transmitted to a remote server.
Anti-Analysis Techniques:Basic evasion methods include detecting debugging environments, virtual machines, and leveraging the CFLocaleCopyPreferredLanguages API to avoid systems where Russian is the primary language.
User Deception: The malware employs fake macOS password prompts to trick users into revealing their system passwords, granting access to keychain data.
Understanding the Banshee Stealer Code
Foresiet researchers analyze the macOS stealer "Banshee," diving into its Objective-C code to understand its components, methods, and overall functionality. This malware targets macOS systems, focusing on data exfiltration and evasion techniques. Let's break it down.
Overview of the Banshee Malware
Banshee is a macOS stealer designed to perform several malicious operations, including:
- Collecting system information.
- Extracting sensitive credentials from the macOS Keychain.
- Executing AppleScript commands for automation.
- Detecting debuggers and virtual machine environments.
- Employing encryption for secure communication or obfuscation.
- Terminating user sessions by force-closing the Terminal application.
Core Functionality of the Main Program
The main.m file acts as the entry point for the application. It handles command-line arguments and executes various tasks based on the arguments provided.
Shows the source code of banshee stealer
Shows the source code of banshee stealer
The program features command-line argument parsing and a unique self-subprocess behavior to manage its functionality. When the argument "run_controller" is passed, the program initializes a Controller object with an encryption key and invokes its manage method to execute specific tasks. In the absence of arguments, the program spawns a new instance of itself as a subprocess using NSTask, passing predefined arguments to control its operations.
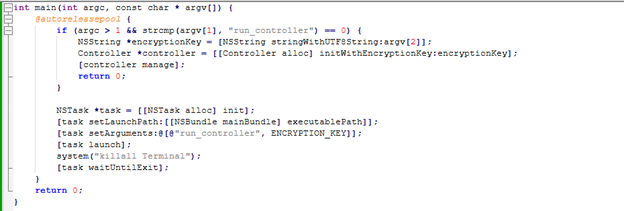
Core Functionality of the Main Program Main Entry Point
Additionally, the self-subprocess behavior includes force-closing all macOS Terminal applications by executing the "killall Terminal" command after launching the subprocess, ensuring a clean operational environment for its tasks.
System Information Collection and File Access
The System class manages system-related information and actions, from gathering OS details to accessing files and credentials.
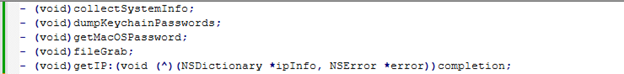
System.h and Related Functionalities
The program employs various functionalities to access and manipulate system resources, potentially with malicious intent. It retrieves IP addresses using a completion handler to gather network information. In terms of credential theft, it leverages functions like dumpKeychainPasswords to extract stored passwords from the macOS Keychain and getMacOSPassword to obtain user credentials, which could be exploited for privilege escalation. Additionally, the program includes a fileGrab feature to extract files from the system, likely targeting sensitive documents or configuration files for further exploitation.
Anti-VM and Anti-Debugging Techniques
Banshee employs the AntiVM class to detect virtual machine environments and debugging tools.
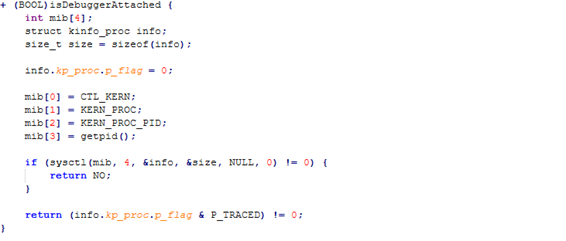
Shows the code path of Debugger Detection
This method checks if a debugger is attached by querying process information via sysctl.
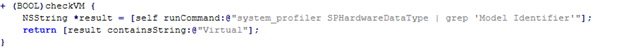
Shows the code path of VM Detection
Uses a shell command to identify virtual machine environments by analyzing hardware details.
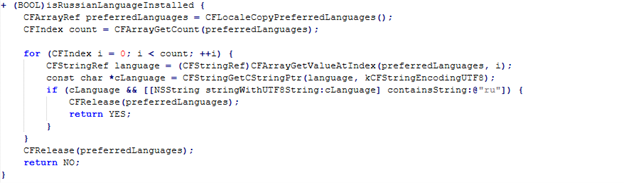
Shows the code path of Russian Language Check
Detects if the Russian language is installed. This may be used to evade certain geographical targets. The malware includes a mechanism that avoids targeting Russian systems by inspecting the user's language settings via the CFLocaleCopyPreferredLanguages API. If the detected language matches Russian, the malware does not execute its malicious payload. However, this can be bypassed, which may allow it to deploy on systems where the language settings have been changed or spoofed.
Encryption and Command Execution
The malware manages encryption by initializing with an *NSString encryptionKey, likely used to encrypt stolen data before exfiltration, ensuring secure transfer to its operators.
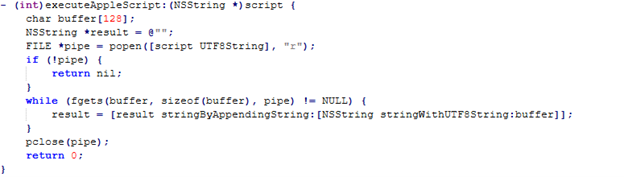
Shows the code path of Encryption Key Management AppleScript Execution
The malware employs a modular structure, with the Controller class serving as the central orchestrator, managing components like AntiVM, System, and other modules to execute its tasks efficiently.
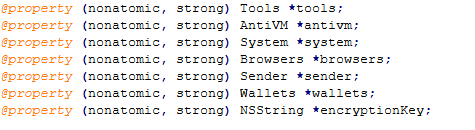
Shows the code path of Controller Properties
Each property represents a module with specific responsibilities:
- Tools: Utility functions for malware operations.
- Browsers: Possibly for stealing browser data (cookies, saved passwords).
- Sender: Exfiltration of data to command-and-control servers.
- Wallets: Cryptocurrency wallet data theft.
Malicious Intent and Impact
Banshee is a malware designed for data theft and user disruption. Its key actions include:
- Credential Theft: Extracting macOS Keychain and system passwords.
- System Manipulation: Abruptly closing Terminal applications and collecting sensitive system files.
- Detection Evasion: Avoids execution in virtual environments or under debugging tools.
- Stealth and Encryption: Employs encryption keys to secure its operations and payloads, ensuring stealth and data confidentiality.
Behavior Detection
Behavior detection for Banshee involves monitoring actions like credential extraction, abnormal file access, system manipulation (e.g., closing Terminal), and checks for virtual machines or debugging tools. Network traffic analysis can also help spot encrypted exfiltration attempts.
Mitigations
- Enable Multi-Factor Authentication (MFA) to secure sensitive accounts.
- Keep software updated, including macOS and browsers, to patch vulnerabilities.
- Use anti-malware software that targets macOS threats.
- Limit browser extensions and remove untrusted ones.
- Encrypt sensitive data, including cryptocurrency wallet keys.
- Educate users about phishing and deceptive login prompts.
- Backup important data regularly to secure storage.
- Implement network segmentation to limit malware spread.
These steps can help mitigate the risks posed by Banshee Stealer and similar threats.
Conclusion
Banshee Stealer marks a significant development in macOS-targeted malware, reflecting a growing focus on this platform by cybercriminals. Its ability to extract sensitive data, including passwords, browser information, and cryptocurrency wallets, combined with evasion techniques and deceptive tactics, underscores its potential impact.
As highlighted by Foresiet researchers, this malware's high price and targeted capabilities signal a rising threat level, making it essential for users and organizations to prioritize macOS security measures and remain vigilant against emerging threats.
About us!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


