How the HPE Data Breach Exposed Sensitive Information: Protecting Critical Systems and Data

Introduction
The world of cyber security is dynamically sophisticated, and many corporate brands have faced highly evolved breaches. The recent news about HPE(Hewlett Packard Enterprise) hacking has alarmed the tech industries worldwide. IntelBroker his tea named CyberNiggers operating on the dark web, took credit for a breach that exposed sensitive data and access credentials tied to HPE. This breach, unfolding over two days, serves as a sober reminder of vulnerabilities in even the most well-resourced organizations.
The implications reach far beyond the confines of HPE, spilling over and affecting customers, partners, and downstream systems. This blog delves deeper into revealing details of the breach incident, how such an incident could occur, and actionable mitigations to guard against similar mishaps in the future.
The Breach Unveiled
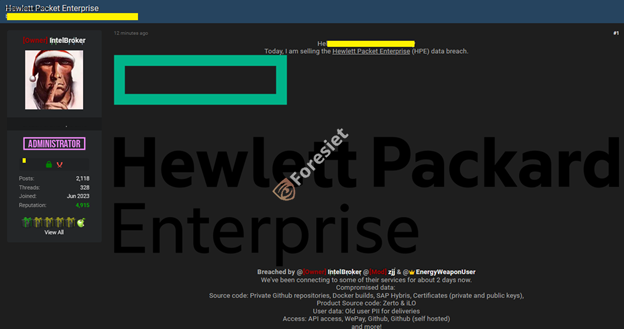
As indicated by IntelBroker, the breach was a treasure trove of sensitive information. Compromised data included private GitHub repositories, Docker builds, SAP Hybris files, and critical certificates—both public and private keys. The breach even extended to proprietary product source code, including Zerto and iLO, along with user data containing old PII related to deliveries.
Alarmingly, the hacker accessed several HPE services, including APIs, WePay accounts, and even hosted and self-hosted GitHub instances. This kind of compromise goes beyond an internal intrusion into HPE's systems. It is now a potential window to exploit HPE customers based on their technologies.
It contained hardcoded credentials for services like Salesforce integrations, Quote ID systems, and internal email notifications that are part of the breach. The risk is enhanced as it makes it easy for attackers to exploit related systems and services. In addition, a screenshot shared by the hacker exposed information about an HPE web service with endpoint details and the WSDL file. This further indicates potential exploitability by bad actors.
The Samples provided by the hackers
IntelBroker shared some samples of the leaked data with proof. Samples reveal the number of breaches that occurred and sensitive information that got leaked as well:
Leaked Configuration File
A configuration file that is included in one of the samples, comprises the following sensitive details:
- Hardcoded credentials for Salesforce integrations, containing usernames and passwords.
- Details regarding Quote IDs, plus email notices showing username/credentials with a highlighted Watson user and the obvious passwords in text, for instance, 1qaz2wsx
- Internally located system URLs of a similar fashion for example http://corona-itg.austin.hp.com/QuoteIds-itg2/hpe/2.3/quoteServices/readquote/jacksonJson
- The addresses used in such error notification internal emails include the ones displayed below:
NGEC_ITG_HPE@groups.int.hpe.com.
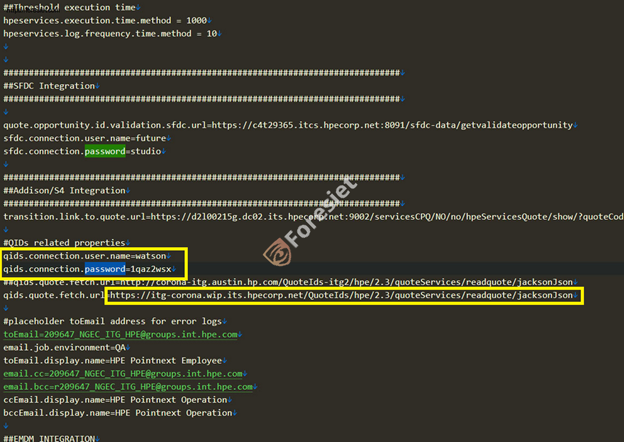
In doing that, those credentials and URLs give direct access to critical systems alongside highlighting poor security practices, for example using plaintext passwords and hard coding of sensitive information.
Web Service Endpoint Details
As another example from IntelBroker, a print screen of the HPE web service endpoint is shown. Points of interest pulled out from the above print screen include;
- The name of the service (SignonService) and its associated port (SignonServicePort).
- The address of the service:
http://ezc-itg.wip.it.hpe.com:80/ngc-maui/SignonService. - A link to the WSDL file:
http://ezc-itg.wip.it.hpe.com:80/ngc-maui/SignonService?wsdl. - The implementation class for the service:
com.hp.ngc.service.SignonService.
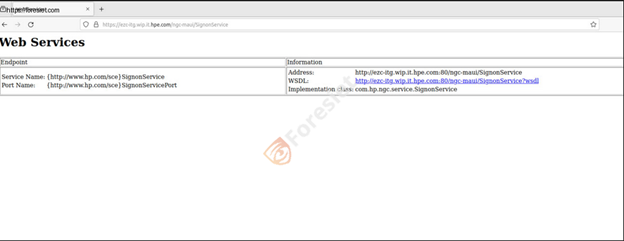
This would indicate an insecure HTTP-based endpoint, perhaps used for unauthorized access or intercepting traffic. The WSDL file is a kind of blueprint for the service, which attackers might use in crafting their targeted requests.
How It Happened
The breach seems to be a result of weak security practices, inadequate monitoring, and exploiting systemic vulnerabilities. Some of the weaknesses highlighted by the leaked files relate to the direct hardcoding of sensitive credentials within configuration files. These included usernames and passwords, and API keys which should have ideally been stored in a secure way using a secrets management system.
Public GitHub repositories, whether hosted or self-hosted, would have provided the hacker with an abundance of information to leverage. Had the repositories not been well-secured and accessed through leaked access credentials, then he could have logged onto IntelBroker. With the information obtained, he would have moved more extensively into the HPE's systems and thus broken the API access and would potentially employ the WSDL file to be aware of how critical web services are designed and work.
It communicated via an unencrypted channel while the other vulnerability was publicly exposed on the Internet, leaving this open to a man-in-the-middle attack since HTTP is used with no encryption at one of the ends. This lack of encryption may have facilitated the interception of sensitive data in transit. It did not monitor the internal systems and the external repositories, which allowed the breach to go unnoticed for two days; it would take a hacker that length of time to extract and analyze sensitive information from the breach.
Mitigation Steps
The first mitigation step for a breach of this magnitude would be to contain the breach.
Immediate Exposure Revocation and Replacement of All Hardcoded Passwords and HPE Credentials through Secure Channels
API key rotation, certificate regeneration, and secure private keys. Such exposure would never occur with the use of a more secure secrets management system, like AWS Secrets Manager or HashiCorp Vault. They can safely and dynamically store sensitive data and prevent it from being hardcoded. Securing GitHub repositories is another critical step. HPE should enforce strict access controls, enable two-factor authentication (2FA) for all contributors, and conduct regular audits to identify exposed credentials or sensitive files. Additionally, repositories should be scanned for vulnerabilities using tools like GitGuardian or Trufflehog, which can identify hardcoded secrets and other security issues.
No compromise measures will be taken by transitioning from HTTP to HTTPS for all web services. The encryption of the data in transit will ensure that no attacker can intercept or modify communications between clients and servers. In addition, the access controls of the SignonService endpoint can be drastically reduced with firewall rules or VPN.
Proactive monitoring and threat intelligence are unavoidable if the breaches are detected. HPE, therefore, will have to resort to using various tools that would monitor dark web activity and check their organization and its data for mention in such breaches so that when a leak arises, they react fast. Their intrusion detection system (IDS) and security information and event management solutions must also detect suspicious activities promptly.
Lastly, there is a review of all systems, configurations, and integrations to look for and remediate vulnerabilities. This includes reviewing the WSDL file of the exposed web service to check if sensitive information might leak out. It is also during this time when the frequency of penetration testing may open other vulnerabilities that hackers can exploit.
Conclusion
This HPE data breach orchestrated by IntelBroker and CyberNiggers must be taken as a wake-up call in terms of the importance of keeping an eye on cybersecurity. Here, in this scenario, leakage of sensitive data such as source code, API access, and user information depicts how strongly malpractice in security can lead to respective repercussions. No system is completely foolproof. However, organizations should focus on putting proactive security measures in place to protect their assets and minimize risks.
This incident brings to the fore a few key takeaways: the importance of secure coding practices, the dangers of hardcoded credentials, and the critical need for encrypted communication channels. Organizations can recover from such incidents by implementing the mitigation strategies outlined above and building a more resilient security posture for the future.
It is a shared responsibility. Every person must recognize the cyber threat; whilst we are learning from these breaches, we need always to focus on making the system and practice safe to protect sensitive data, retain trust, and keep out the bad guys. So, in that sense, it's a wake-up call for HPE - to strengthen their defenses and not repeat what just happened.
About us!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


July 10, 2025, 9 a.m.
