Inside FunkSec: An Exclusive Interview with a Ransomware Architect

Summary
FunkSec is a new ransomware group that came into the spotlight after attacking many sectors around the world. The group runs a data leak site on Tor. Funksec employees conduct double extortion attacks, which means hackers encrypt and exfiltrate data from the victim to extort them for paying ransom to the attackers.
The mitigation strategies against FunkSec's attacks include strong cybersecurity measures, data backup processes, employee training, and staying up to date on the latest threat intelligence.
Introduction
Ransomware attacks have become more frequent and sophisticated, and now it is threatening organizations worldwide. The latest player in this cybercrime arena is FunkSec, a group that has quickly made its mark with a series of well-planned attacks. This blog explores the background, modus operandi, and impact of FunkSec's operations and gives insights into effective mitigation strategies to defend against such threats.
Who Is FunkSec Ransomware?
Recently identified, FunkSec is a newly identified ransomware cybercrime group. It is first reported in late 2024, using a Tor-based data leak site (DLS) for their extortion operations. To date, on December 3, 2024, FunkSec had compromised 11 organizations cutting across sectors including media, IT, retail, education, automobile, professional services, and NGOs with operations that extended to places such as the United States, Tunisia, India, France, Thailand, Peru, Jordan, and the United Arab Emirates.
Victim listing site of FunkSec on the dark web
Funksec ransomware announcement on darkweb
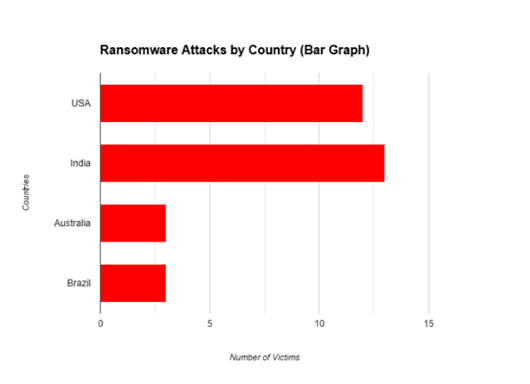
Number of countries targeted by FunkSec in Bar Graph
A Glimpse into Ransomware Operations
We asked a key player in the ransomware business to explain how it works. In a candid interview, we asked them questions about their motivations, techniques, and perspectives on the cybersecurity landscape. Their responses tell us not only what tools they use but also what mindset drives their actions. What follows is an eye-opening look into the world of ransomware from the perspective of someone operating at its core.
Funksec support Private chat box
Motivations and Beginnings
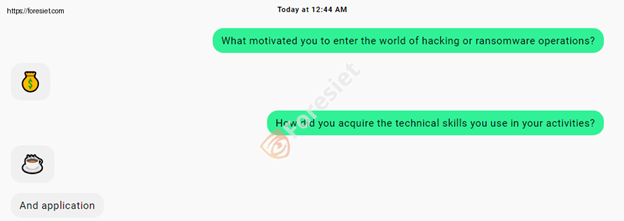
Q: What motivated you to enter the world of hacking or ransomware operations?
A: Money.
A blunt and unsurprising response, but one that underscores a common theme among cybercriminals: the lure of money is stronger than any other consideration.
Q: How did you acquire the technical skills you use in your activities?
A: Coffee and application.
This veiled answer probably relates to the trial-and-error nature typical of hacking communities. Persistence, coupled with the ability to use open-source tools and online resources, is often how hackers hone their craft.
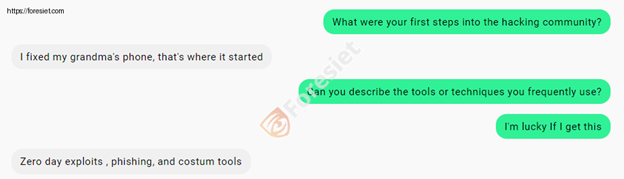
Q: What were your first steps into a hacking community?
A: I fixed my grandma’s phone. That’s where it started.
Even the simplest curiosities will take you down the hacking route. For this man, the smallest problem-solving activity helped him into the world of cybercrime.
Methods and Operations
Q: Can you describe the tools or techniques you frequently use?
A: Zero-day exploits, phishing, and custom tools.
Zero-day exploits and phishing are well-known methods in the cybercrime toolkit, while "custom tools" point to the maturity of modern ransomware operators.
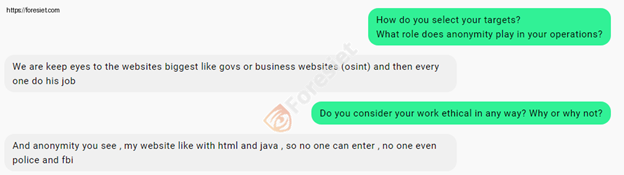
Q: How do you select your targets? What role does anonymity play in your operations?
A: We keep an eye on big websites, like government or business sites. Everyone does this job.
The most common practice is the targeting of high-value organizations with weak defenses. The core aspect is anonymity, and operators use tactics to ensure that their digital footprints are not traced.
Ethics and Boundaries
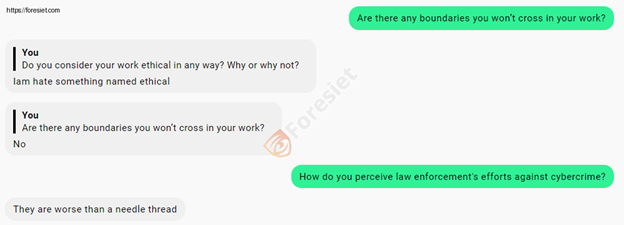
Q: Do you consider your work ethical in any way? Why or why not?
A: I hate something named ethical.
This blunt answer reflects the fact that most cybercriminals completely disregard ethics. Profit is what matters, not morality.
Q: Are there any boundaries you won’t cross in your work?
A: No.
Such an answer reflects the moral void in the ransomware ecosystem. This absence of boundaries is a sobering reality for cybersecurity professionals.
Perceptions of Law Enforcement and Security Weaknesses
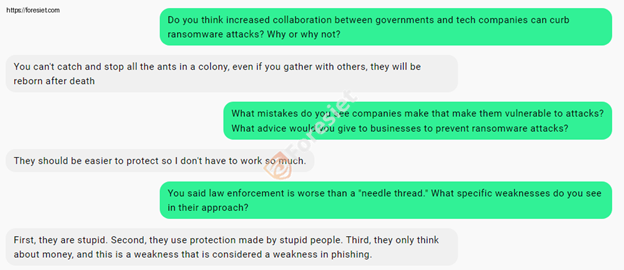
Q: How do you perceive law enforcement efforts against cybercrime?
A: They are worse than a needle thread.
This response expresses loathing for law enforcement, implying that cybercriminals believe the present efforts are inadequate or misguided.
Q: What weaknesses do you see in their approach?
A: First, they are stupid. Second, they use protection made by stupid people. Third, they only think about money.
This is harsh. However, the comments point to perceived inadequacies in the tools and strategies used by law enforcement and bureaucracy that might delay effective action.
Q: Do you think increased collaboration between governments and tech companies can curb ransomware attacks? Why or why not?
A: You can’t catch and stop all the ants in a colony. They will be reborn after death.
This metaphor signifies the resurging ransomware operations and demands constant innovative measures to check those threats.
Exploited Vulnerabilities and Prevention Advice
Q: What mistakes do you see companies make that make them vulnerable to attacks? What advice would you give to businesses to prevent ransomware attacks?
A: They should be easier to protect, so I don’t have to work so much.
This sarcastic response sheds light on the preventable nature of many attacks. Weak security measures, such as outdated systems or untrained staff, make organizations easy targets.
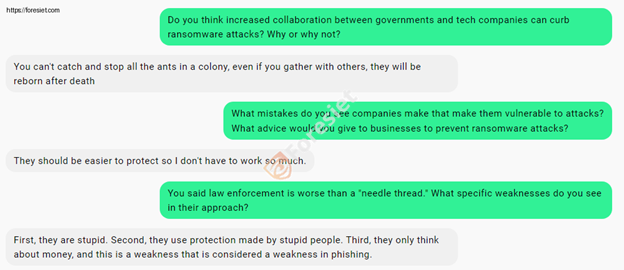
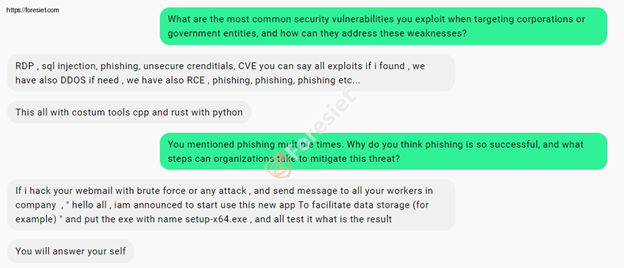
Q: What are the most common security vulnerabilities you exploit when targeting corporations or governments? How can they address these weaknesses?
A: RDP, SQL injection, phishing, unsecured credentials, CVEs, DDoS, RCE, phishing, phishing, phishing.
The multiple uses of the word "phishing" point to its high efficacy. Businesses have to train employees, enforce better password policies, and protect their endpoint solutions to counter such problems.
Q: You mentioned phishing multiple times. Why do you think phishing is so successful, and what steps can organizations take to mitigate this threat?
A: If I hack your webmail and send a fake message to employees asking them to install a malicious app, most will do it. The result is obvious.
This chilling example illustrates the power of social engineering. Organizations must focus on phishing awareness campaigns and simulate attacks to build resilience.
Reflections and Closing Thoughts
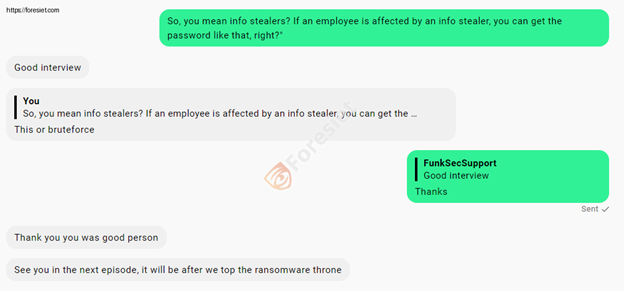
As the interview concluded, the ransomware operator left us with a chilling remark:
"See you in the next episode, after we top the ransomware throne."
This statement captures the confidence and ambition of ransomware groups today. It is a wake-up call for organizations to bolster their defenses and collaborate to outpace these ever-evolving threats.
Mitigation Strategies: Protecting Against Ransomware
A proactive cybersecurity approach needs to be applied to combat ransomware demands. Organizations need to be certain that all their employees are phishing-trained, all systems and software are updated, and they hold regular backups of secure data. Enhancing the security level by using a multilayer approach may reduce some of the weaknesses of networks. Strongly emphasizing prevention and preparation in organizations reduces risks involved in ransomware and results in quick recovery time if it has affected any of the business activities.
Conclusion
It will give an idea of ransomware operations: what motivates people, the methods they use, and vulnerabilities exploited. Sobering as that sounds, it indeed zeroes in on a need for greater cybersecurity to be undertaken by businesses, governments, and individuals.
It's far from the end in fighting ransomware. And with more awareness and proactive steps, we could well make major headway against the impact.
About us!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


