Inside the MOVEit Breach: How Cl0p and Nam3L3ss Expose Organizations to Ongoing Cyber Threats
In 2023, a critical vulnerability in MOVEit Transfer software (CVE-2023-34362) was weaponized by the Cl0p ransomware group, leading to a substantial leak of sensitive employee data from major global corporations. The flaw in MOVEit allowed attackers to bypass authentication and access secure files, resulting in a far-reaching data breach that impacted various sectors including finance, healthcare, government, and retail.
Vulnerability Details and Affected Software
- Type of Vulnerability: SQL Injection
- Affected Software: MOVEit Transfer versions prior to 2021.0.6, 2021.1.4, 2022.0.4, 2022.1.5, and 2023.0.1.
- Incident Summary: The Cl0p ransomware group exploited this vulnerability in mid-2023, leading to significant data exfiltration from approximately 130 organizations, underscoring the critical impact of this attack on MOVEit users.
Nam3L3ss: Profiling Cl0p Ransomware Data
Researchers at Foresiet have identified an individual known as Nam3L3ss on cybercrime forums, who has become a prominent figure documenting and posting data from the MOVEit breach. Rather than directly exploiting the MOVEit vulnerability, Nam3L3ss has been downloading databases exposed by the Cl0p ransomware group and other operators. They have been systematically organizing and cleaning the data for wider distribution, citing Cl0p as the primary origin for much of the obtained information.
They are meticulously organizing and cleaning the data for wider release, citing Cl0p as the primary origin for much of the information obtained.
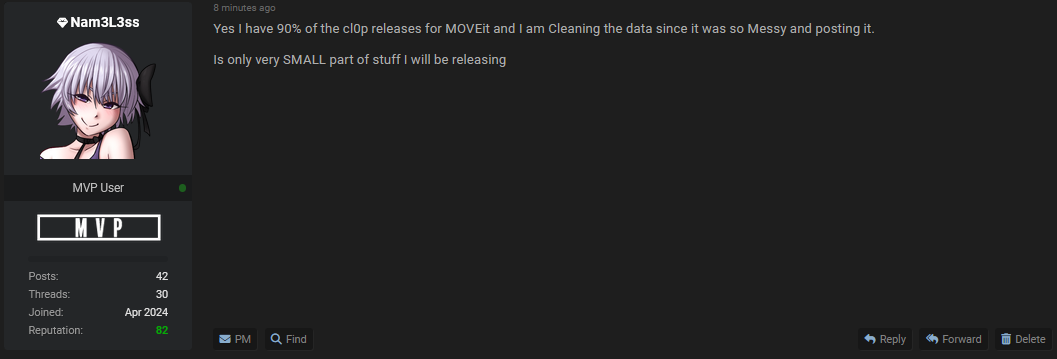
In their own words, the possess “90% of the Cl0p releases for MOVEit” and are undertaking a detailed “cleaning” process.
Motivations and Approach
Nam3L3ss appears to be motivated by the pursuit of credit within cybercrime communities, using the MOVEit data to build a reputation. Each dataset shared includes a label denoting DataSource: MOVEit and DataDate: 2023-05-31, specifying that the information originally stems from Cl0p’s exploitation of the MOVEit vulnerability in 2023.
Upcoming post he mentioned clearly data’s are collecting form ransomware groups
Impacted Organizations
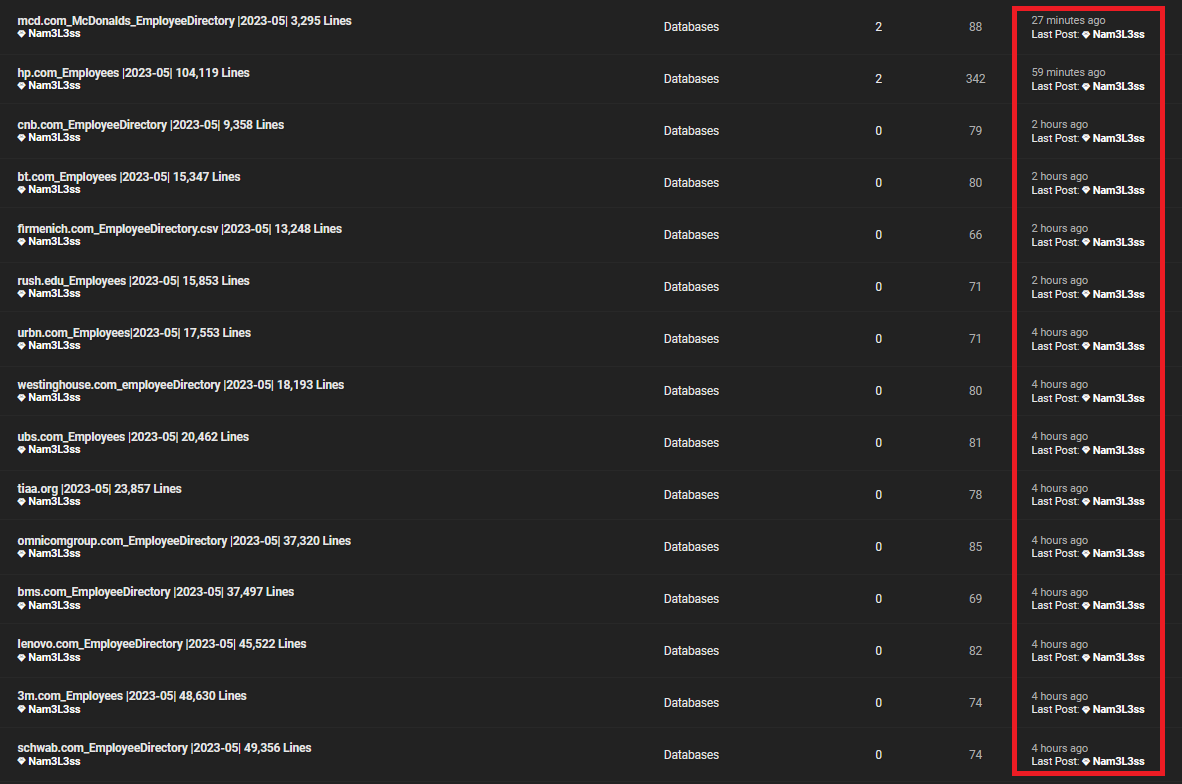
The breach affected numerous organizations, exposing detailed information about employees. Here’s an overview of some impacted companies and their estimated record counts:
- Amazon: 2,861,111 records
- UBS: 20,462 records
- Delta Airlines: 57,317 records
- McDonald’s: 3,295 records
- 3M: 48,630 records
- Lenovo: 45,522 records
- HP: 104,119 records
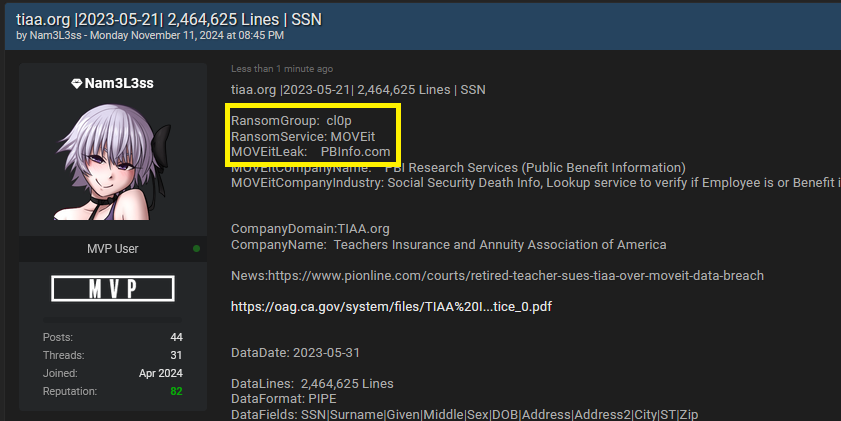
- TIAA: 2,464,625 records, plus an additional 23,857 records
- Applied Materials: 53,170 records
- CalSTRS: 422,311 records
- City National Bank (CNB): 9,358 records
- British Telecom (BT): 15,347 records
- Firmenich: 13,248 records
- Rush University: 15,853 records
- URBN (Urban Outfitters): 17,553 records
- Westinghouse: 18,193 records
- Omnicom Group: 37,320 records
- Bristol-Myers Squibb: 37,497 records
- Charles Schwab: 49,356 records
- Leidos: 52,610 records
- Canada Post: 69,860 records
- Cardinal Health: 407,437 records
- U.S. Bank: 114,076 records
- Fidelity Investments (FMR): 124,464 records
- HSBC: 280,693 records
- MetLife: 585,130 records
- Vertafore: 30,070,951 records (Texas driver records) and 26,541,746 records (Texas lien records)
- Los Angeles Police Department (LAPD): Roster of police officers, including headshots, and potentially compromising details for undercover officers from 2023.
Each dataset contains sensitive information such as employee names, email addresses, positions, and organizational structures, which heightens the risk for phishing and social engineering attacks against these organizations.
The Attacker’s Methodology: Curating Data from Ransomware Leaks
Foresiet has been closely monitoring Nam3L3ss has disclosed details of their approach to collecting and organizing the compromised data, focusing heavily on ransomware data leaks:
- Tracking Ransom Group Sites: They monitor ransomware sites and utilize tools to automatically locate open cloud storage buckets on platforms like AWS, Azure, and others.
- Database Collection: They download databases from ransomware sites that expose entire datasets from breached organizations, specifically MySQL, PostgreSQL, SQL Server, and Azure databases. These databases are then converted into manageable formats such as CSV.
- Data Curation: Each dataset undergoes a cleaning process to remove duplicates, irrelevant fields, and any data that lacks utility for cybercrime purposes.
- Data Volume: With over 250TB of archived database files from various breaches, Nam3L3ss is releasing only a fraction at a time, maximizing exposure and impact for each dataset.
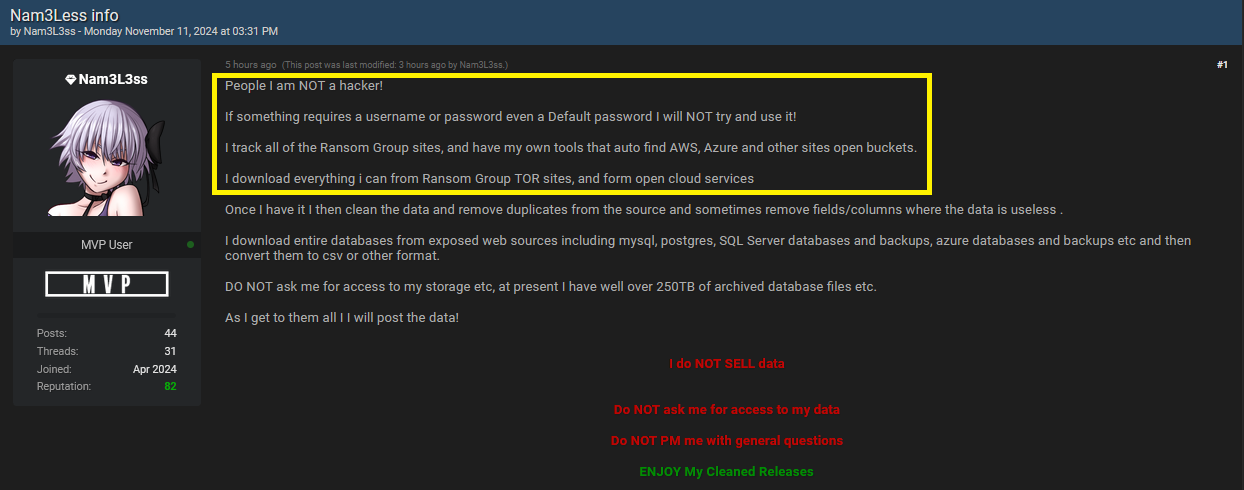
Despite this intense process, they maintain a code of ethics regarding protected access:
“If something requires a username or password—even a default password—I will NOT try and use it!”
A Prolonged Threat: Incremental Data Releases
Nam3L3ss has indicated plans to release this data incrementally, noting that only a “very SMALL part of the stuff I will be releasing” has been disclosed so far. This phased release strategy prolongs the reputational and security impact on affected organizations, keeping the MOVEit breach visible to cybercrime circles while continuously introducing fresh data.
Cybersecurity Implications and Lessons for Organizations
This breach underscores the critical need for robust cybersecurity measures, particularly around third-party software. Key takeaways for organizations include:
- Swift Patch Management: Timely application of updates is essential to protect against exploits, especially in commonly used applications like MOVEit.
- Continuous Threat Monitoring: Organizations must monitor for emerging threats and act quickly when vulnerabilities are discovered.
- Employee Security Training: Ongoing training for employees is crucial to help them recognize potential phishing attempts resulting from exposed personal data.
- Enhanced Cloud Security: Given the use of open cloud storage by cybercriminals, securing cloud environments is a growing priority for data protection.
Conclusion
The MOVEit vulnerability exploited by Cl0p in 2023 continues to have a widespread and ongoing impact. With data meticulously curated and incrementally released by individuals like Nam3L3ss, the breach remains a stark reminder of the need for strong security measures across software platforms and third-party services.
Organizations must remain vigilant, ensuring timely updates and robust data protection strategies. As Cl0p’s data leak is released in stages, the potential for additional disruptions emphasizes the importance of proactive cybersecurity and incident response practices.
About us!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


July 10, 2025, 9 a.m.
