Latest GitLab Vulnerabilities: A Gateway for FOG Ransomware Attacks?

Introduction
The future cyber threat is not static and appears to exploit vulnerabilities with fresh ransomware gangs and devastate businesses all over the world. One of such infamous gangs, Fog Ransomware, is currently dumping sensitive data of several businesses, recent attacks including GitLab deep. Foresiet security researchers believe that Fogs recently exploited Gitlab Cve perhaps they employed a fresh or unfixed zero-day vulnerability in GitLab.to launch its attacks.
Who is FOG Ransomware?
Fog Ransomware is a new but highly active ransomware group that steals and leaks data unless a ransom is paid. Unlike most ransomware groups, these encrypted the Fog Double extortion tactic -the sensitive information and threatened to leak them before paying the ransom.
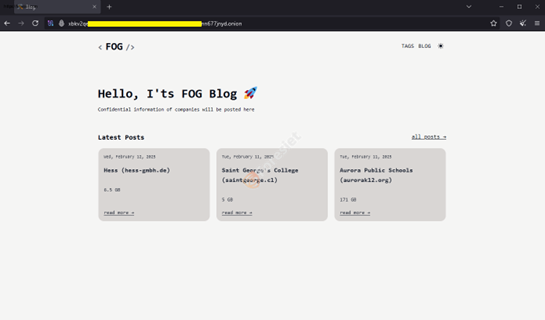
Shows FOG Ransomware tor site
Their latest victims were universities, IT companies and entertainment tech providers, all of whom had Gitlab in their infrastructure.
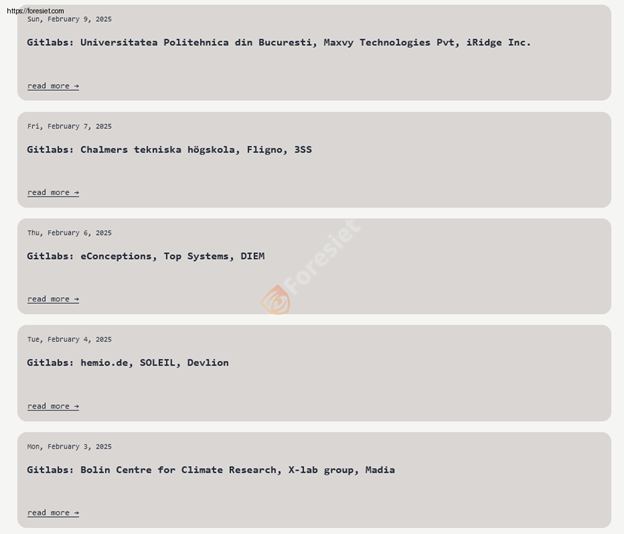
Shows the victim list of the Fog ransomware.
New GitLab CVEs: Can It Be the New Attack Entry Point?
As of February 12, 2025, some Common Vulnerabilities and Exposures (CVEs) in GitLab become attackers' new entry points for FOG ransomware and other attackers. Some of the most critical vulnerabilities are discussed below:
- CVE-2025-0314 (XSS Vulnerability - Published: Jan 24, 2025)
2. CVE-2025-0290 (CI Artifact Metadata Processing Bug - Published: Jan 28, 2025)
3. CVE-2025-0194 (API Token Exposure - Published: Jan 8, 2025)
4. CVE-2025-1072 (Denial of Service via Fogbugz Importer - Published: Feb 7, 2025)
Were These CVEs Used by FOG Ransomware?
Although there is no direct assurance that FOG ransomware used these CVEs, our researchers are certain they might have used one or more of the vulnerabilities in unpatched instances of GitLab. Here's why:
- Massive Data Leaks - The magnitude of data exfiltrated indicates that the attackers possessed deep repository access, which would have been obtained via vulnerabilities such as CVE-2025-0194 (API token leak).
- Cross-Site Scripting as an Entry Point – CVE-2025-0314 (XSS vulnerability) would have been used to steal login credentials or privilege escalation in GitLab, thus enabling attackers to acquire internal repos access.
- Denial of Service as a Distraction – Attackers would have been able to use CVE-2025-1072 to crash GitLab services and erase footprints while exfiltrating data.
What Organizations Should Do to Protect Themselves
Since FOG, like other ransomware groups, is a relatively new and newly emerging threat, GitLab users must act promptly to harden their environments:
- Patch GitLab: Ensure that all systems are updated to the latest secure versions to mitigate known vulnerabilities.
- Monitor Logs for Suspicious Activity: Look out for API logs of unauthorized access of tokens via out-of-band (most probable exploitation of CVE-2025-0194).
- Enforce Multi-Factor Authentication (MFA): Prevent users from using the account maliciously, particularly against high privilege use cases.
- Restrict Public Access to GitLab Instances: Install valid access control settings to thwart attacks from outsiders.
- Regular Backups: Maintain off-the-record backup, secure by nature, as an antidote for ransom attacks that don't necessitate giving away ransom money.
Final Thoughts
Gitlab- The requirement for active cyber security in the Fog Ransomware Group attack on targeted organizations is specifically established. With so many critical vulnerabilities which have just been brought to their notice, organizations must stay ahead of would-be attackers by patching their infrastructure, obtaining proof of access and being on the lookout for malicious activity. If Fogs ransomware utilized Gitlab Cves, then that is an eye-opener for all the companies relying on self-customized depot threats because threats in hospitals are changing and therefore, we have to be cautious.
Conclusion
We are confirming if FOG ransomware utilized these vulnerabilities. Updates and research will be given when more facts come to light. Wait for the update.
About us!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


July 10, 2025, 9 a.m.
