LockBit Ransomware Panel Breached: Database Dump Reveals Deep Insights into RaaS Infrastructure

LockBit Ransomware Group Suffers Major Breach
The LockBit ransomware group's dark web infrastructure has suffered a major blow following a significant breach on May 7, 2025. This cyberattack targeted LockBit's onion-based infrastructure—including their affiliate and admin panels—and resulted in the complete defacement of the sites. The attackers left behind a taunting message: "Don't do crime, CRIME IS BAD xoxo from Prague," along with a link to a leaked MySQL database dump.
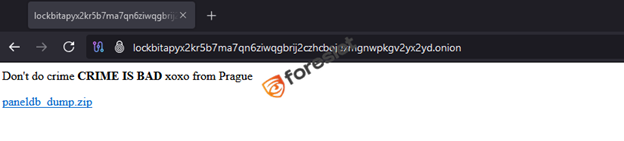
This is not the first instance of such a defacement. Previously, the Everest ransomware group's onion site was similarly compromised, bearing the same exact message: "Don't do crime, CRIME IS BAD xoxo from Prague." This pattern suggests a recurring actor or group intent on delivering a moralizing message to the ransomware community, while simultaneously exposing sensitive data.
This breach exposed a wealth of sensitive internal data, providing a rare look into the inner workings of one of the most infamous Ransomware-as-a-Service (RaaS) groups. The leaked SQL dump, generated using phpMyAdmin version 5.1.1, was designed to recreate a MySQL database named paneldb_dump. It contains a comprehensive backend snapshot of a ransomware control panel, possibly operated by LockBit or a similar RaaS collect.

Inside the Dump: Database Structure and Tables
The paneldb_dump.sql file includes SQL commands to set up the environment, create the database, and define 20 different tables. These tables indicate the system was used for managing payloads, tracking infections, and interacting with both victims and affiliates.
Here are the first 10 tables found in the dump:
- api_history
- btc_addresses
- builds
- builds_configurations
- chats
- clients
- events
- events_seen
- faq
- files
The following tables are particularly data-rich and suggest key operational functionality:
- pkeys – 316 entries (potentially encryption keys or affiliate/public key infrastructure)
- btc_addresses – 76 entries (likely cryptocurrency wallets used for ransom payments)
- builds_configurations – 59 entries (malware build configurations)
- builds – 26 entries (actual payloads or ransomware samples)
- system_invalid_requests, chats, socket_messages – Possibly command-and-control communication logs, negotiation chats, or error handling
These structures reinforce the notion that this was a comprehensive malware control panel, likely used to manage payload deployment, communication with infected machines, and the administration of affiliates.
Negotiation Logs and Threat Actor Behavior
This data appears to be a raw dump of communications—most likely from a ransomware negotiation portal—between victims and attackers. It contains dialogue fragments with timestamps, user IDs, message IDs, and message content, with notable examples of:
- Ransom negotiations: Discussions around ransom amounts (e.g., "$50k", "40k", "10000$") and attempts by the victim to negotiate a lower amount.
- Proof-of-life or decryption tests: The attacker provides instructions on how victims can submit files for test decryption, which is standard in ransomware extortion to demonstrate decryption capability.
- Threat actor tone: Occasionally casual or even humorous (e.g., "Can I call you robin hood?", "I want to be rich."), which is typical of ransomware groups who attempt to manipulate victims psychologically.
- Mentions of payment methods: Bitcoin is the currency used, and .onion addresses for file sharing are included—indicating Tor-based infrastructure, which is common for ransomware gangs.
- Indicators of multiple victims: The repeated change in negotiation tone and references to different companies imply the attackers are handling several cases concurrently.
Threat Actor Behavior Insights:
- Willingness to negotiate – evident in lines like “discount possible” or “we can make a deal if agree on the price”.
- Attempt at emotional manipulation – using empathy (“we don’t want a lose-lose situation”) or humor.
- Multi-language support – suggests targeting of global victims (mentions of "Tw", "cn", NTD = New Taiwan Dollar).
- Automated infrastructure – structured messages, possibly templated responses, and use of multiple Tor portals hint at operational maturity.
Attribution and Speculation: Who Did It?
While the identities of the perpetrators remain unknown, the tone of the defacement message—"Don't do crime, CRIME IS BAD xoxo from Prague"—hints at either hacktivists or rival cybercriminals aiming to undermine LockBit. The playful yet moralistic messaging style does not fit typical law enforcement operations, which are usually more discreet and procedural.
This is not the first time a ransomware group's infrastructure has been hacked. Previously, the Everest ransomware group's onion site was defaced with a similar message from the same apparent actors: "Don't do crime, it's bad xoxo from Prague."
Indicators That This Belongs to LockBit
Several aspects of the database dump strongly suggest its origin is indeed LockBit or a very similar RaaS group:
- Bitcoin Wallets
• Found in the btc_addresses table (76 entries)
• Likely used for receiving ransom payments - Encryption or Decryption Keys
• Contained in the pkeys table (316 entries)
• Could include victim-specific keys or malware communication keys (RSA, ECC) - Custom Malware Builds
• builds and builds_configurations tables (26 and 59 entries respectively)
• Indicates a system designed to generate payloads for affiliates—a LockBit hallmark - Victim Negotiations and Internal Comms
• chats table (20+ entries)
• May include interactions between victims, affiliates, and administrators - Affiliate and Victim Tracking
• invites, clients, events, events_seen
• Could log infections, beaconing, C2 activity, and affiliate registration
Fallout: A Blow to LockBit's Credibility
This incident follows sustained pressure on LockBit from global law enforcement agencies. Notably, in February 2024, "Operation Cronos"—a coordinated takedown by the FBI, UK's National Crime Agency (NCA), and Europol—resulted in the seizure of LockBit’s servers, arrests across multiple countries, and the unmasking of Dmitry Khoroshev, a Russian national alleged to be the group’s leader.
Despite these disruptions, LockBit attempted to reestablish its operations, launching new dark web domains and continuing ransomware campaigns. However, this latest breach significantly damages their credibility and may deter future affiliate partnerships—an essential part of any RaaS model.
Conclusion
The breach of LockBit’s backend database marks a pivotal moment in the ongoing battle against ransomware. It offers rare insight into the backend of a RaaS operation, undermines LockBit’s operational integrity, and provides a treasure trove of intelligence for defenders. Whether carried out by hacktivists, rivals, or whistleblowers, this operation reinforces the reality that the cybercriminal ecosystem is not immune to disruption—and that the walls are closing in, even on the most elusive threat actors.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


