Navigating the Tides of Cybersecurity: Trends and Insights (May 1st - May 15th, 2024)

Introduction
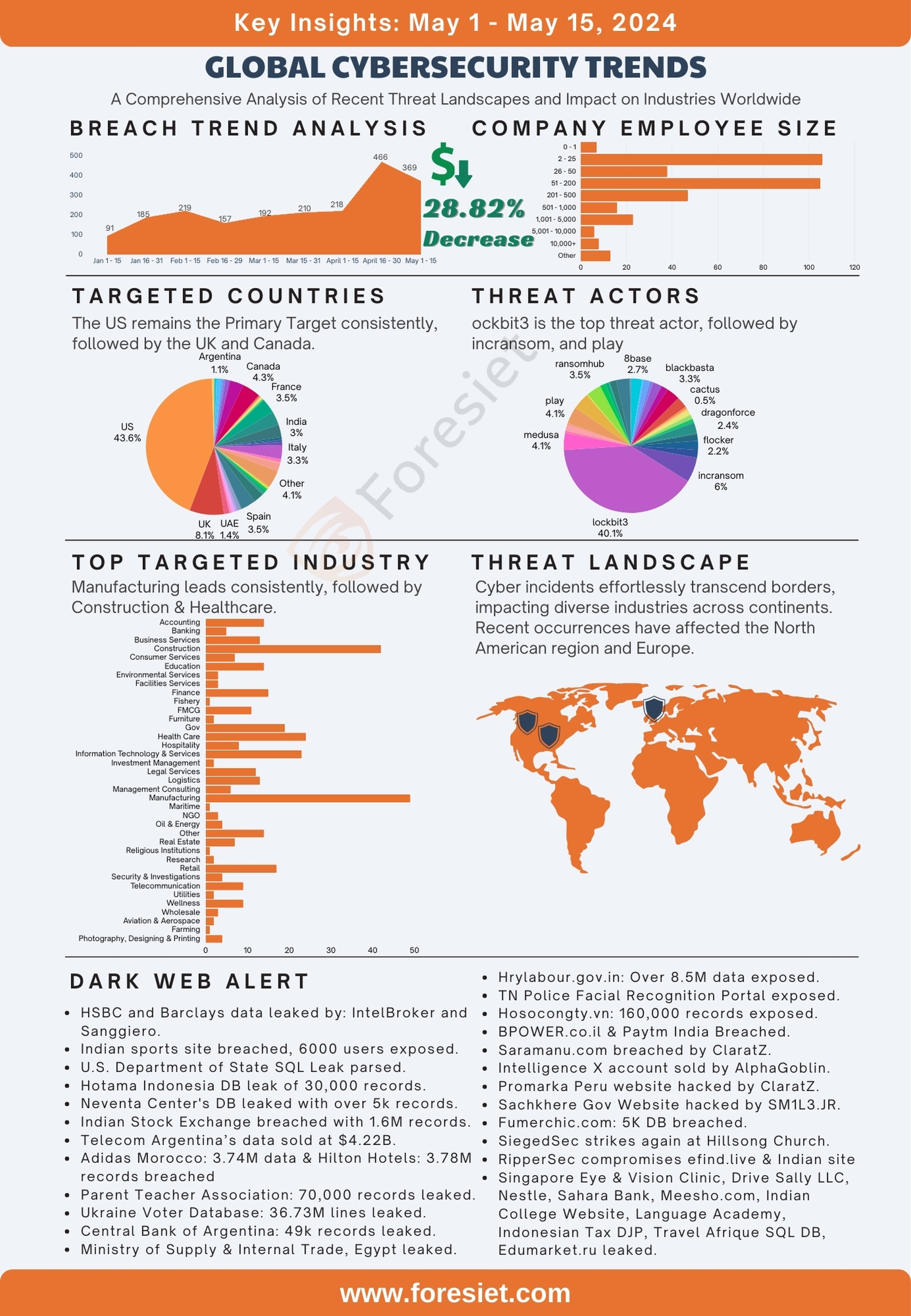
The beginning of May 2024 has seen a significant spike in cybersecurity breaches worldwide, highlighting persistent vulnerabilities across various sectors and regions. This period's data reveals a concerning concentration of breaches in certain countries and industries, emphasizing the critical need for robust cybersecurity measures. Notably, the United States remains the most affected, underscoring the severe cybersecurity challenges faced by organizations within its borders. Similarly, the manufacturing and healthcare sectors show substantial breach incidents, reflecting ongoing threats to vital infrastructure. As we delve into the specifics of these breaches, it's evident that threat actor groups continue to evolve, deploying sophisticated techniques that pose severe risks to global cybersecurity.
Global Targets
The United States stands out significantly, with a staggering 297 breaches, constituting approximately 64% of the total breaches. This dominance underscores the prevalent cybersecurity challenges faced by organizations within the US. Following closely behind is Canada, with 23 breaches, making up around 5% of the total breaches. This suggests a notable cybersecurity landscape in Canada as well. Other countries with relatively higher numbers of breaches include Germany, reporting 13 breaches, accounting for approximately 3% of the total breaches, and the UK, also with 13 breaches, comprising around 3% of the total breaches. Australia follows closely with 10 breaches, representing approximately 2% of the total breaches. Collectively, these top five countries account for nearly three-quarters of the total breaches. Conversely, several countries have reported only one or two breaches, indicating a lower incidence of cybersecurity incidents. These findings highlight the varying levels of cybersecurity preparedness globally and the need for robust security measures across different regions.
Industry Dynamics
The landscape of breaches across industries reveals noteworthy patterns. The manufacturing sector emerges as the most impacted, with 58 reported incidents, constituting approximately 12% of the total breaches. This sector's vulnerability underscores the pressing need for enhanced cybersecurity measures within manufacturing environments. Following closely behind is health care, with 45 breaches, representing around 10% of the total breaches. Such breaches in health care raise significant concerns regarding data privacy and security. Information Technology & Services reported 39 breaches, accounting for approximately 8% of the total, highlighting the challenges faced by companies entrusted with protecting digital assets. Additionally, the finance sector, with 31 incidents, and the construction industry, also with 31 breaches, reflect persistent vulnerabilities, each comprising around 7% of the total breaches. These top five industries collectively account for over 40% of the breaches. Conversely, several sectors reported minimal breaches, suggesting disparities in cybersecurity readiness. These findings underscore the imperative for robust cybersecurity strategies across industries to effectively combat cyber threats.
Employee Size Matters
In analyzing the breaches by the number of employees affected, several trends emerge. Most breaches impact smaller organizations, with 105 incidents reported among companies with 2 to 25 employees, constituting approximately 23% of the total breaches. This suggests that smaller entities may be more vulnerable to cyber threats due to potentially limited resources for cybersecurity measures. Conversely, larger organizations with 10,000 or more employees reported 29 breaches, making up around 6% of the total breaches. This indicates that while larger companies may have more robust security infrastructure, they are still susceptible to cyberattacks. Additionally, companies with 51 to 200 employees reported the highest number of breaches, with 114 incidents, comprising approximately 25% of the total breaches. This suggests that mid-sized companies face significant cybersecurity challenges. The ranges of 201 to 500 employees and 501 to 1,000 employees reported 57 and 39 breaches, respectively, representing around 12% and 8% of the total breaches. Collectively, these top five categories account for over three-quarters of the total breaches. Conversely, companies with 0 to 1 employee reported only 5 breaches, indicating a lower incidence rate. These findings underscore the importance of cybersecurity measures across organizations of all sizes, with emphasis on smaller and mid-sized entities to enhance their resilience against cyber threats.
Analysis on Attack Surface Management
During the first half of May 2024, spanning from the 1st to the 15th, our examination of digital environments revealed 2797 vulnerabilities, with 114 classified as critical. Among these critical vulnerabilities, 9 have garnered attention, with 3 currently having publicly available exploits. Notably, both vulnerabilities have been assigned EPSS scores ranging from 0.04% to 1.97%, signifying a high level of potential exploitation.
The Foresiet research team has diligently pinpointed exploits accessible to opportunistic threat actors, targeting vulnerabilities that present an easy attack surface. Some of the identified exploits include CVE-2024-32962, CVE-2024-32888, CVE-2024-32741, CVE-2024-32700, CVE-2024-31377, CVE-2024-30207, CVE-2024-29895, Ect., and others. This revelation underscores the critical importance of proactively addressing these vulnerabilities to mitigate potential threats and fortify our digital defenses against emerging risks.
Threat Actors
Analyzing breaches by threat actor groups reveals notable insights into cybersecurity trends. The most significant threat actor group is Dispossessor, with a staggering 267 breaches, comprising approximately 57% of the total breaches. This dominance underscores the pervasive threat posed by this group in orchestrating cyberattacks. Following closely behind are Lockbit3, Play, and Ransomhub, each with 17 breaches, representing around 4% of the total breaches. These groups demonstrate significant activity and effectiveness in executing ransomware attacks. Additionally, Blacksuit reported 9 breaches, making up approximately 2% of the total breaches. This suggests a notable presence in the cyber threat landscape. Collectively, these top five threat actor groups account for over 70% of the total breaches. Conversely, several threat actor groups reported only one or a few breaches, indicating a lower incidence rate. These findings highlight the persistent and evolving nature of cyber threats and emphasize the importance of robust cybersecurity measures to mitigate risks effectively across various threat landscapes.
Top 5 Threat Actors
- Lockbit3 A prolific ransomware group known for sophisticated encryption techniques and large-scale attacks worldwide. Consistently top 3 in threat actor groups with the highest number of breaches.
- Incransom Known for its ransomware-as-a-service model, providing tools to affiliates for ransomware attacks.
- Medusa Active ransomware group deploying payloads through various attack vectors.
- Play Relatively new but aggressive ransomware group, consistently top 5 in threat actor groups with highest number of breaches.
- Ransomhub Offers ransomware tools to affiliates, targeting organizations and consistently in top 5 threat actor groups, including the second half of April.
Dark web threats
In May 2024, the Central Bank of Argentina experienced a significant data breach that exposed the personal information of over 49,000 customers. This incident was disclosed on the dark web forum "303," where the data was offered for under 8 credit coins. A hacker known as 888 also offered to sell a leaked Nestle database, attributed to hacker 303, for 3 credit points. RipperSec compromised Language Academy, leaking 12,000 user records. Additionally, data from HSBC and Barclays was leaked by @IntelBroker and @Sanggiero, including database files and source code. An Indian sports site had data from over 6,000 users leaked, while the U.S. Department of State's SQL data from 2012-2017 was parsed, revealing extensive details. The Tamil Nadu Police Facial Recognition Portal database was leaked, exposing over 1.2 million users' data. In Indonesia, over 100,000 patient records were leaked, and Hotama Indonesia had 30,000 user records exposed. Neventa Center's student database leak revealed over 5,000 records. Meanwhile, Zero Tolerance claimed responsibility for breaching Banco Central of Argentina, and yeshiyi96 offered 1.6 million records from the Indian Stock Exchange for $15,000. Europol's data was also leaked by @IntelBroker, and Telecom Argentina's shell access was sold by 303. Significant breaches occurred in Punjab, India; Adidas Morocco; Hilton Hotels; the Parent Teacher Association; the Ukraine Voter Database; Singapore Eye & Vision Clinic; Americanbuildersoutlet.com; Paytm India; edma-tools.us; Travel Afrique; the Indonesian Tax DJP Database; Fumerchic.com; Sahara Bank; Drive Sally LLC; hrylabour.gov.in; edumarket.ru; hosocongty.vn; BPOWER.co.il; Meesho.com; Intelligence X; and various other sites and databases, highlighting a widespread issue of data security breaches affecting millions globally.
- Central Bank of Argentina Over 49,000 customers' personal info exposed, including names, IDs, addresses; data offered on dark web forum "303" for under 8 credit coins.
- Nestle database Leaked by hacker 303, sample data available, 888 offers full database for 3 credit points.
- Language Academy 12,000 user records leaked by RipperSec, includes names, phone numbers, emails, and courses.
- HSBC and Barclays Data leaked by @IntelBroker and @Sanggiero, includes database files, source code, SQL files.
- Indian sports site Data from over 6,000 users leaked.
- U.S. Department of State 2012-2017 SQL Leak parsed, revealing program details, budgets, activity statuses, congressional notifications, more.
- Tamil Nadu Police Facial Recognition Portal Database leaked, exposes 1.2 million users' data including police records.
- Indonesian patient records Over 100,000 leaked, includes names, IDs, contact details, medical info.
- Hotama Indonesia Database leaked, 30,000 user records exposed including emails, phone numbers, names.
- Neventa Center Student database leaked, over 5,000 records exposed including student IDs, names, contact info.
- Zero Tolerance ransom group Claims Banco Central of Argentina breach, sensitive data compromised.
- Indian Stock Exchange Breached by yeshiyi96, 1.6 million user records offered for $15,000.
- Europol data leak Offered by @IntelBroker, includes CCSE, Cryptocurrencies - EC3, Space - EC3, additional datasets.
- Telecom Argentina Shell access offered by 303, estimated revenue $4.22 billion, method RCE, 121GB data available.
- Punjab, India: Over 1 million records compromised, includes names, genders, mobile numbers, current locations.
- Adidas Morocco 3.74 million lines of data compromised, including emails, passwords.
- Hilton Hotels 3.78 million records breached, includes guest names, check-in/out dates, reservation details.
- Parent Teacher Association 70,000 rows of data leaked, COIAdditionalInsured.csv compromised.
- Ukraine Voter Database 36.73 million lines leaked, includes names, birth details, addresses.
- Singapore Eye & Vision Clinic 813,000 records exposed, includes gender, clinic details, contact info.
- Americanbuildersoutlet.com 123,000 user records compromised, includes emails, hashed passwords, addresses.
- Paytm India Customer data compromised, includes names, mobile numbers, emails, income declarations.
- Edma-tools.us Customer data breached, includes customer IDs, names, emails, encrypted passwords.
- Travel Afrique SQL database leaked, 314,961 lines compromised, includes nicknames, names, admin settings.
- Indonesian Tax DJP Database Breached, sensitive info exposed, includes names, tax numbers.
- Fumerchic.com DB France 5K breached, personal info exposed, includes names, addresses, contact details.
- Sahara Bank Debit card info, customer data compromised, threatened to leak by Black_Dolphin.
- Drive Sally LLC Customer and staff data leaked, payment card info exposed, sold by CrystalPWN for $300.
- Hrylabour.gov.in Over 8.5 million individuals' data exposed, sold by Dark_Daddy, putting lives at risk.
- Edumarket.ru Russian Database breach, user data exposed, sold by Dark_Daddy.
- Hosocongty.vn 160,000 job search platform records exposed, sold by Makishimaaaa for $320.
- BPOWER.co.il Breached, order records exposed, sold by Pwns3c for $20.
- Meesho.com Indian shopping platform breached, personal info exposed, sold by qpwomsx.
- Intelligence X account Sold by AlphaGoblin for $2000, includes Identity Portal access.
- OTP mail access bot Offered by MrrRobot for Yahoo, AOL, Microsoft, with Ledger Live module.
- Indian College Teacher Training Website Hacked by SM1L3.JR, reflects tensions, support for Israel, involvement of multiple groups.
- Promarka Peru Website hacked by ClaratZ, impacting security.
- Saramanu.com Breached by ClaratZ, mirror on zone-bbx.com.
- Sachkhere Government Website Hacked by SM1L3.JR, denounces support for Israel, multiple groups involved.
- Ministry of Supply and Internal Trade, Egypt Breached by R00TK1T, deep infiltration into systems.
- CorporateStack Breached by R00TK1T, backend access compromised.
- NoName group Targeting Italian transportation, Moldovan websites, critical Ukrainian sites.
- SiegedSec Targets Hillsong Church with website hack.
- ANON BLACK FLAG | INDONESIAN Targets websites in protest.
- Efind.live Compromised by RipperSec, message in support of Palestine.
- RipperSec Breaches Indian site, leaks sensitive data.
- Outlook Remote Code Execution (RCE) 0day Sold by "Cvsp" for $1,700,000, claimed 100% success rate.
- DuckyMummy (FrotCom) Significant breach involving vehicle GPS, sleep management, offers live GPS feeds, company logins.
- Nationalist Claims sensitive data from wcd.nic.in, over 110 rows, available for purchase.
Conclusion
The early days of May 2024 have underscored the relentless nature of cyber threats, with many breaches reported across various industries and regions. The dominance of specific threat actor groups, particularly Dispossessor, highlights the sophisticated and pervasive nature of these cyberattacks. The analysis reveals that both large and small organizations are vulnerable, with a notable concentration of breaches impacting smaller entities. This trend emphasizes the need for comprehensive cybersecurity strategies tailored to organizations of all sizes. The dark web's activity further illustrates the widespread implications of data breaches, affecting millions globally. As cyber threats continue to evolve, it becomes increasingly crucial for organizations to implement proactive and resilient cybersecurity measures to safeguard against these persistent risks.
About Foresiet!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


June 7, 2024, 7:02 p.m.

May 23, 2024, 8:02 p.m.