Navigating the Tides of Cybersecurity: Trends and Insights (May 16th - May 31th, 2024)

Introduction
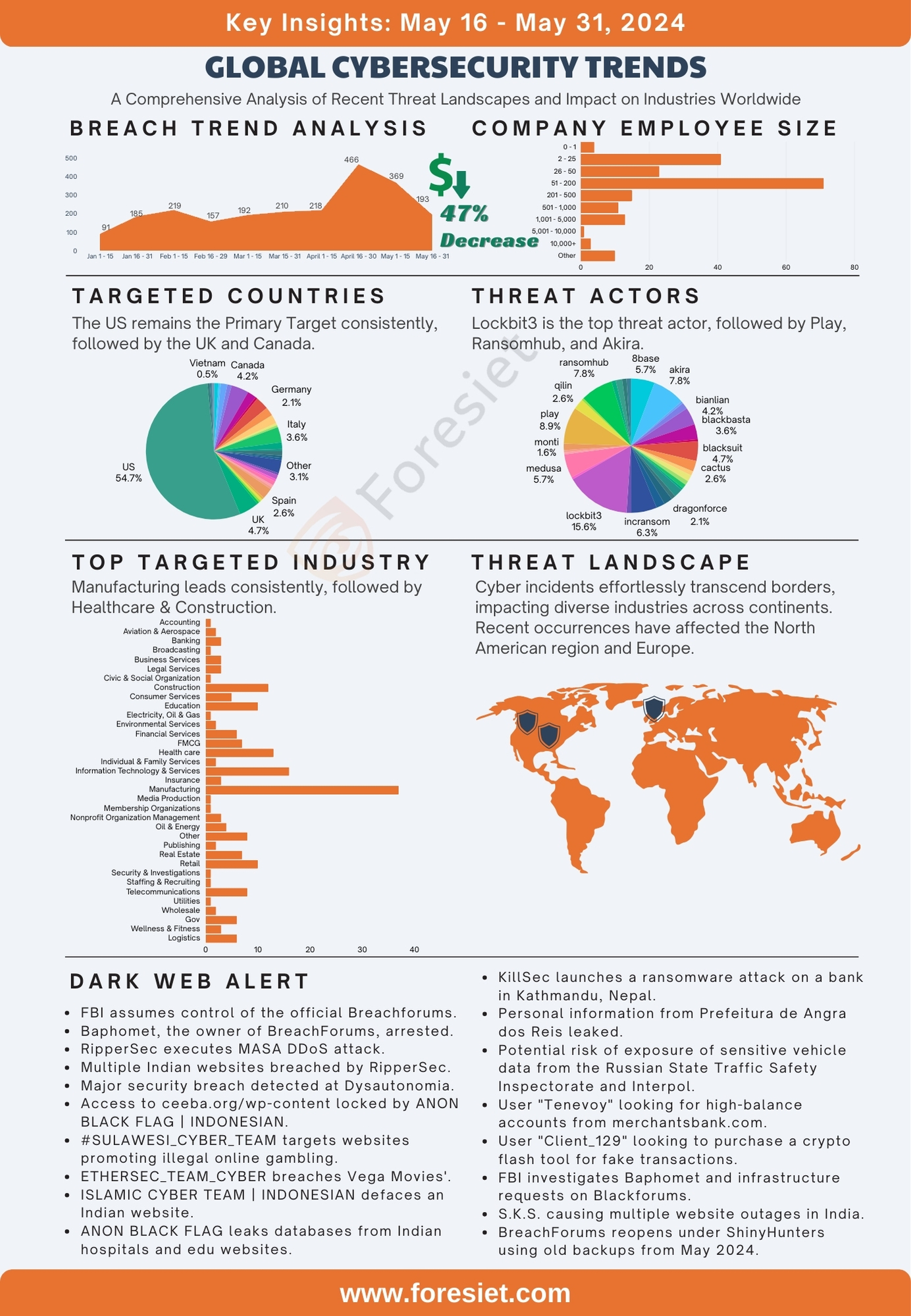
In the latter part of May, there was a noticeable downturn in breach incidents compared to previous months, although 192 breaches were still recorded globally. This underscores the persistent hurdles organizations face in protecting their digital assets. Despite the decrease in breaches, it emphasizes the urgent need for robust cybersecurity measures to mitigate risks and bolster defenses against evolving threats.
These breaches expose digital assets, leaving organizations grappling with challenges such as securing against external attack surfaces, handling leaked credentials, combating info stealers, and addressing credit card breaches. Moreover, the presence of information on the darknet/dark web raises concerns, along with vulnerabilities from third-party sources and issues in vendor risk posture. Ongoing targeted phishing campaigns and brand impersonation issues further compound the challenges. Additionally, the lack of visibility into digital footprints and the absence of a definitive method to quantify cyber risk in near real-time add to the complexity of the situation.
Global Targets
The dark web analysis of breach data across various countries reveals a significant concentration of incidents in certain regions. The United States leads with 105 breaches, constituting 54.7% of the total 192 breaches. The United Kingdom follows with 9 breaches (4.7%), Canada with 8 breaches (4.2%), Italy with 7 breaches (3.6%), and both France and the "Other" category each with 6 breaches (3.1%). Spain reported 5 breaches (2.6%), while China, Germany, and India each accounted for 4 breaches (2.1%). Additionally, Belgium and Japan each reported 3 breaches (1.6%), and several countries, including Bangladesh, Brazil, Mexico, Poland, and Romania, had 2 breaches each (1.0%). Numerous other countries, such as Czechia, Ireland, Israel, Kuwait, Nepal, Netherlands, Pakistan, Portugal, Senegal, Singapore, Sudan, Sweden, Switzerland, UAE, Vietnam, The Bahamas, and Australia, each reported a single breach (0.5%). This data highlights the disproportionately high number of breaches in the United States, indicating a potential need for enhanced cybersecurity measures in this region.
Industry Dynamics
The dark web analysis of breach data across various industries reveals that the Manufacturing sector experienced the highest number of breaches, with 37 incidents, accounting for 19.3% of the total 192 breaches. This is followed by the Information Technology & Services industry with 16 breaches (8.3%), the Health Care sector with 13 breaches (6.8%), the Construction industry with 12 breaches (6.3%), and the Education sector with 10 breaches (5.2%). Other notable industries include Telecommunications with 8 breaches (4.2%), Financial Services and Government each with 6 breaches (3.1%), and the FMCG and Real Estate sectors each with 7 breaches (3.6%). The remaining breaches are distributed among various other industries such as Aviation & Aerospace, Environmental Services, and Business Services, each reporting between 1 to 4 breaches. This data underscores the need for enhanced cybersecurity measures, particularly in the Manufacturing, IT & Services, Health Care, Construction, and Education industries due to their higher incidence of breaches.
Employee Size
The dark web analysis of breach data across different employee counts reveals significant insights into organizational vulnerability. Organizations with 51 to 200 employees experienced the highest number of breaches, with 71 incidents, accounting for 31.6% of the total breaches. This is followed by organizations with 2 to 25 employees, which had 41 breaches, representing 18.3% of the total. Companies with 26 to 50 employees reported 23 breaches, making up 10.2% of the total. Those with 201 to 500 employees experienced 15 breaches, constituting 6.7% of the total, while organizations with 1,001 to 5,000 employees had 13 breaches, which is 5.8% of the total. Additionally, organizations with 501 to 1,000 employees reported 11 breaches (4.9%), those with 0 to 1 employee had 4 breaches (1.8%), and organizations with over 10,000 employees experienced 3 breaches, making up 1.3% of the total. Furthermore, companies with 5,001 to 10,000 employees and those classified as "Other" reported 1 breach and 10 breaches respectively, together accounting for 4.9% of the total breaches. This data highlights that smaller to mid-sized organizations, particularly those with 51 to 200 employees, are more susceptible to breaches compared to larger organizations.
Analysis on Attack Surface Management
We have identified 2,271 vulnerabilities, with 81 classified as critical. Among these, 22 currently have publicly available exploits. Notably, of the 81 critical vulnerabilities, 7 have publicly available exploits. It's worth noting that all these vulnerabilities carry an EPSS score ranging from 0.04% to 94.05%, indicating a high level of potential exploitation.
Foresiet research team has identified exploites available for Opportunistic Threat actor, to target easy attack. Listing a few: CVE-2024-32809, CVE-2024-31351, CVE-2024-22476, CVE-2024-5407, CVE-2023-3943, CVE-2023-3941, CVE-2023-3939, Etc.,
Threat Actors
It's evident from the dark web analysis that the threat landscape is diverse, with a total of 192 breaches attributed to various threat actor groups. Notably, Lockbit3 emerges as the most prolific threat actor group, responsible for approximately 15.63% of the total breaches with a count of 30. This highlights the significant impact and operational scale of Lockbit3 in cyberattacks. Following closely behind is the Akira group, comprising 15 breaches, accounting for around 7.81% of the total breaches. Additionally, Play and Ransomhub demonstrate considerable activity, with 17 and 15 breaches respectively, each constituting approximately 8.85% and 7.81% of the total breaches. These top five threat actor groups collectively contribute to around 48.91% of the overall breaches, showcasing their prominence in the cybersecurity landscape.
Among the other threat actor groups listed, Incransom, 8base, and Medusa also exhibit noteworthy activity, with 12, 11, and 11 breaches respectively. These groups each represent approximately 6.25%, 5.73%, and 5.73% of the total breaches, underlining their significance in cyber threat scenarios. Conversely, several groups have fewer instances of breaches, such as Apt73, Blackout, Donutleaks, Meow, and Qiulong, each responsible for only one breach, accounting for 0.52% of the total breaches. Despite their lower frequency, it's crucial to monitor these groups as they may pose emerging threats or indicate evolving tactics in the cybersecurity landscape. Overall, the data underscores the complex and dynamic nature of cyber threats, necessitating robust security measures and proactive defense strategies to mitigate risks effectively.
Top 5 Threat Actors
- Lockbit3 : The top threat actor group, Lockbit3, has executed 30 breaches, representing 15.63% of the total. Their sophisticated ransomware tactics demand fortified defenses from organizations.
- Akira: With 15 breaches (7.81% of total), Akira's versatile cyber weaponry requires vigilant monitoring to thwart their precise attack vectors.
- Play: Consistently a top threat actor group, Play tallies 17 breaches (8.85% of total), demanding a holistic cybersecurity approach to counter their multifaceted tactics.
- Ransomhub: Making a significant impact with 15 breaches (7.81% of total), Ransomhub specializes in ransomware attacks, emphasizing the need for proactive defense measures.
- Incransom: Asserting influence with 12 breaches (6.25% of total), Incransom's combination of ransomware and data exfiltration underscores the persistent threat of ransomware operators, necessitating comprehensive security measures.
Dark web threats
The FBI has taken control of the BreachForums Telegram account amid investigations into cybercriminal activities, leading to the arrest of its owner, Baphomet, and the forum's shutdown. Despite this, numerous cyber threats and breaches continue to emerge, including ransomware attacks, data leaks, and website compromises. Major incidents involve the exposure of sensitive information from entities such as Toyota Makati, Poshmark, and various government and educational institutions. These events underscore the urgent and ongoing need for robust cybersecurity measures to protect personal and organizational data from persistent and evolving threats.
- The FBI has assumed control of the official Breachforums Telegram account.
- Dark web forums BreachForums and Raidforums are under intense scrutiny as the FBI investigates cybercriminal activities. Victims or informants are encouraged to provide information through the provided questionnaire for assistance. If you have any relevant information, please contact the FBI at breachforums@fbi.gov or via Telegram at t.me/fbi_breachforums. #DarkWebUnderInvestigation #FBIInvestigation #CyberCrimeFocus
- Baphomet, the owner of BreachForums, has been arrested! The FBI, DOJ, and international allies have shut down BreachForums and seized control of associated Telegram chats. #BaphometArrested #BreachForumsDown #FBIControlledTelegram
- USDoD @EquationCorp, a prominent threat actor, declares its intent to revive Breachforums following its takedown by the #USDoJ. Promising a swift return and enhanced privileges for upgraded members, anticipate their resurgence.
- RipperSec executes MASA DDoS attack targeting IPs: 104.21.32.224 and 172.67.136.216, affecting the website. HTTP status: 403 | 301 | 400. Provider: Cloudflare, Inc. #CyberThreat #RipperSec
- Indian Website Vaishnavi Foundation Co. breached by RipperSec. Message reflects #FreePalestine sentiment. Notable hacktivist groups involved: RipperSec, TengkorakCyberCrew, EagleCyberCrew, and others. Stay vigilant! #cybersecurity #infosec
- RipperSec strikes once more, compromising another Indian site, Globus Institute.
- Major security breach detected at Dysautonomia International website! Pendekar1337 x HelangMerahGroup strike again, sending a message to Joe Biden. Cybersecurity alert!
- Access to ceeba.org/wp-content is temporarily locked by ANON BLACK FLAG | INDONESIAN. A warning shot echoing.
- The #SULAWESI_CYBER_TEAM has successfully disrupted the functioning of example.rmitraapp.in and rmitraapp.in. This attack is associated with the #FuckIndia and #OpIndia campaigns. Immediate action is imperative. #CyberAttack #CyberSecurity
- #ETHERSEC_TEAM_CYBER has breached Vega Movies' website, prompting immediate investigation.
- Indian Site Defaced by ISLAMIC CYBER TEAM | INDONESIAN 🇲🇨🇵🇸!
- #ANON_BLACK_FLAG has leaked a 6.7K database from Indian hospital 'Ravi Foundation.'
- #ANON_BLACK_FLAG has leaked 4,233 databases from India's top educational websites.
- #ANON_BLACK_FLAG provides free access to admin dashboard of an Indian website.
- A dark web group named "KillSec" has launched a ransomware attack on laxmicapital.com.np, demanding $10,000 for restoring access to the compromised system. The breach, occurring on May 17, 2024, targeted a bank in Kathmandu, Nepal. The hackers, known by the alias "killsec," have offered the entire database for $10,000, with an additional option to extend access for approximately $500.
- The dark web group "KillSec" has launched a ransomware attack on laxmicapital.com.np, demanding $10,000 for database access. Breach details reveal bank information from Kathmandu, Nepal.
- Personal information of 9,434 individuals from Prefeitura de Angra dos Reis has been leaked online, comprising names, addresses, emails, and more. Stay vigilant and monitor your accounts.
- Threat intelligence highlights a user attempting to acquire sensitive vehicle data from the Russian State Traffic Safety Inspectorate and Interpol. There's a potential risk of exposure of motor vehicle data spanning 2019-2024. Remain vigilant and watch for any suspicious activity.
- New intelligence reveals a user inquiring about SIP telephony services in Russia for "white calls" with SMS capabilities. There's a potential risk of misuse by traffickers. Monitor related activities closely.
- User "Tenevoy" is looking to acquire high-balance accounts from merchantsbank.com, with balances starting at 3000+, available both with and without email access. This raises potential alarms for financial fraud.
- User "Client_129" is looking to purchase a crypto flash tool for fake transactions involving BTC, USDT, BNB, and ETH, offering $1000-$3000. This poses a high risk of crypto fraud.
- User "MMOSTEWIE" is offering fresh CVV packs from USA, EU, and Asia with a validity rate of 70%+, starting at $5 per pack. This raises concerns for potential fraudulent activities.
- User "Clownflan" is selling databases containing personal information such as email addresses, names, addresses, and phone numbers. The data includes individuals from various countries, including the Netherlands.
- A potential threat linked to Baphomet has been identified, associated with infrastructure requests on Blackforums. The security of the new BreachForums is under scrutiny due to these concerns.
- Several Indian websites have experienced outages attributed to S.K.S.
- A website has been compromised by S.K.S. Exercise caution and avoid downloads from affected sources.
- A former Blackforums admin suspects Baphomet as an informant, raising concerns about security risks with the new Breachforums under ShinyHunters using old backups. Emphasis is placed on maintaining strong OpSec to avoid legal issues.
- A #ThreatIntel alert reveals FBI agents' covert operations on BreachForums have been exposed. Usernames and emails, including 'Cr4ck4', are revealed, along with suspected data vendor stings. Full document attached in a forum post by Dastardy.
- In a concerning development, a hacker known as "kiberphant0m" has reportedly gained access to an Asian telecom company with an annual revenue exceeding $5 billion. The breach encompasses LAN access to over 150 machines, decryption library for KI (Key Integrity), call logs, databases, SIM card cloning capability (SIM KIM) with decrypted keys, national ID information, source code, HLR (Home Location Register), AUC (Authentication Center) codes, and various other sensitive data. The total data obtained exceeds 250 GB, with more expected as the breach is extensive. This access and data are available for purchase, with prices ranging from $150,000 to $10,000,000 USD. The hacker has established a Telegram group to showcase skills and shared screenshots of the target, explicitly mentioning a major telecom company. Remarkably, access to their entire network was achieved through a single router within their internal infrastructure.
- On the Dread forum, moderators have announced a concerning trend: a consistent increase in unstable connections to the Tor network over the past few days. This instability stems from an ongoing DDoS attack aimed specifically at onion services. Additionally, beyond Dread, many onion links are reported to be non-functional, indicating a broader impact of the attack.
- A #ThreatIntel Alert warns of exposed sensitive employee data from atSistemas, including names, emails, and work schedules. This breach is potentially linked to threat group Chucky. Immediate action is recommended to secure systems and notify affected individuals.
- A new threat has emerged: BlackPlague, a stealer in the market, is capable of exfiltrating data from Discord, Telegram, browsers, wallets, and more. With anti-VM and UAC bypass capabilities, it poses a serious threat to sensitive information.
- A massive breach has been discovered on the USA Criminal database, with 70 million records leaked on 'CrypticNet'. The format is CSV, and the size is 3GB compressed. The breach spans years 2020-2024 and is attributed to threat actor 'SXUL'.
- A leaked Indian university database attributed to 'FidzXploit', impacting 'Swarrnim Startup & Innovation University'. The sensitive data is categorized and available on 'gofile.io'.
- India BN College database leaked by 'Nusantara'! Data exposed on bncollege.co.in.
- A hacker known as 8xexe8 from a hacker forum has reportedly breached Voterportal.eci.gov.in. The breach, announced with the message "pwned by xexe - l33t," included the leakage of some data samples. Details of the leak include the breach date of May 22, 2024, the hacker alias 8xexe8, the affected database India Gov, and compromised data such as usernames and passwords. Samples are available, and the data size is 805.13KB in 7z format. The hacker mentioned that everything is available for free download.
- The "noname" group targets banks in Russia and Ukraine, posing a significant cyber threat.
- The "noname" threat group escalates attacks, targeting German government websites in response to geopolitical issues. Heightened cyber threat in Europe.
- The "noname" threat group intensifies attacks, targeting Moldovan government entities over alleged repression. Heightened cyber risk in Eastern Europe.
- SKS Cyber Team takes down a site.
- "rippersec" conducts MASA DDoS attack on Israeli government network.
- "ANON BLACK FLAG | INDONESIAN🌐" leaks Indian company database.
- Anonymous group "ANON BLACK FLAG | INDONESIAN🌐" leaks Indian fast food company database.
- "🇲🇾Nusantara🇮🇩" group targets HP Color LaserJet MFP ISRAEL, leading to system file deletion.
- "JUST EVIL" threat group hacks USA medical supplier, compromising 105,000 clients' personal & payment data since 2013.
- "AnonOne" leaks Instagram database on DarkForums, exposing data of 50M users. Major privacy breach detected!
- "GodSpeed69" is selling government-verified Grey Badge X.com accounts on DarkForums. Potential identity fraud risk!
- BreachForums reopens under "ShinyHunters" using old backups from May 2024. Registration is disabled, raising concerns of a possible honeypot.
- "Nusantara" group leaks databases from Israeli websites, compromising TOVADO Real Estate and Orsyx lab data.
- Indonesian Police Academy registrants' data leaked by "kzot," posing a potential cyber risk for individuals exposed.
- "wizard1" leaks intersumi website database, exposing customer details including emails and passwords.
- Massive data breach at Mustafa Singapore by "GhostR," exposing 3,407,880 customer PII records.
- Thailand's Hatari.co.th hit by "Ghostr," resulting in a breach of a 617GB database. Corporate, HR, and customer details exposed. Full data available for sale.
- China iOS email database leaked, exposing 7.6 million rows of personal details from China Telecom, Mobile, and Unicom. Database available for $1000.
- Conti ransomware builder is for sale on the dark web. This malicious tool rapidly encrypts files or locks systems, demanding ransom in cryptocurrency for decryption. Stay vigilant and ensure robust cybersecurity measures.
- The database for an online deals website has been leaked on the dark web. Exposed data includes personally identifiable information such as emails, usernames, and Facebook access tokens of 1,148 users.
- BreachForums has resumed operations, with 863 users active in the last 60 minutes, consisting of 193 members and 662 guests. It's crucial to ensure your operational security (OpSec) is robust to navigate safely. Stay vigilant!
- Private email combinations from Poshmark leaked on the dark web. Over 1.2 million records exposed, posing significant privacy risks.
- BreachForums sellers are offering Twilio API keys for sale. Protect your API keys and ensure strict access control to avoid unauthorized access and potential data breaches.
- Toyota Makati (Philippines) has been compromised, with 1TB of customer data exposed. The leaked information includes full names, addresses, bank documents, valid IDs, and emails. Hackers still have access to phpMyAdmin and POS systems.
- The Bitbose ICO participant database has been leaked! Exposed information includes Bitcointalk usernames, emails, Telegram, Facebook, Twitter usernames, and ERC20 addresses. Sensitive participant details are now circulating on the dark web.
- Cybercriminals on BreachForums are offering compromised databases from trendyol.com and Qatar National Bank. These databases contain personal information, emails, phone numbers, and bank documents. It's crucial to implement robust security measures to safeguard sensitive information.
- A BreachForums user is offering a database containing the data of 1.8 million Mexican citizens, including names, emails, phone numbers, and capture dates spanning from 2023 to 2024. It's imperative to enhance data protection measures and remain vigilant for any suspicious activities.
- A significant 47.9GB database from Singapore's PeopleCentral.co has been leaked on BreachForums, impacting 100,000 users. The breach exposes HR, payroll, and personal details, including NRIC and bank information. It's crucial to remain vigilant and prioritize data security.
- Sensitive company information from dc.gov has been leaked, with the "DBE" table containing 992 rows of data including company names, addresses, contact information, and NAICS codes. Businesses are advised to remain vigilant and prioritize cybersecurity measures.
- The database of womear.com has been compromised, revealing more than 11,600 lines of sensitive customer data such as names, emails, and phone numbers. Immediate security measures are recommended to mitigate risks.
- Sensitive information from Nicaragua's Covid-19 database, including IDs, names, genders, addresses, vaccination data, and more, has been leaked, affecting 5 million citizens. Urgent steps are required to protect privacy.
- Sensitive data of 605,017 individuals in Buenos Aires, Argentina, has been exposed in a breach at partidas.mgob.gba.gob.ar. Urgent measures are needed to safeguard affected citizens' privacy.
- Japan's B2B database of 950K companies has been leaked, exposing sensitive details like addresses and emails. Immediate actions are necessary to prevent misuse.
- A threat actor, dwShark, is selling a JazzCash Pakistan database from May 2024 with 155,000 user records for $1,100. Data includes CNICs, payment modes, account numbers, and more. Proof and samples provided.
- A threat actor, Adm1nFr1end, is selling the Hawk-Eye Surveillance HYD India database on BreachForums. The data includes names, emails, phone numbers, physical addresses, and location coordinates. 130K records available.
- A threat actor, Foxs7, is selling a database of police personnel from West Java (Jawa Barat) on BreachForums. The data includes personal details such as names, emails, phone numbers, and positions. Records show recent activity from April 2024.
- A threat actor, keoperz, is selling the MagicBus website database on BreachForums. Data includes transaction IDs, IP addresses, emails, names, and phone numbers. Contains recent records from January 2023.
- A threat actor, Ghostr, is selling 292 GB of data from India's Direct Sales Company, HHI Marketing Pvt. Ltd. The breach includes corporate info, accounts, and customer data from happyhealthindia.co.in, hhishoppy.com, and rhitrading.in.
- A threat actor, Ghostr, is selling 3,407,880 customer records from Mustafa Singapore, including PII data from various services like travel, retail, and financial services. The breach occurred in April 2024, totaling 180GB.
- A significant data breach involving PeopleCentral.co has occurred, affecting 100,000 users, with 47.9GB of data now for sale by Ghostr. The compromised information includes HR and payroll data, along with personal details such as names, addresses, phone numbers, emails, NRIC, and bank details. This breach took place in April 2024.
- AnonOne has made claims of possessing hacked computer files from a CIA agent, potentially revealing sensitive information.
- Internal documents from Saudi Arabia's military and government have been leaked by AnonOne, revealing confidential data from military officials' email accounts. The implications on the country's governance are under scrutiny.
- Secret documents from a government website have been leaked, exposing sensitive information. This raises potential implications for privacy and security concerns. Stay informed.
- Data from European Parliament meetings in 2024 has been exposed on DarkForums. Sensitive information on 1000 users, including names, companies, and dates, has been compromised, raising serious privacy implications.
- A US Intelligence contractors database has been leaked. Hackers claim it was extracted from a US government-owned cloud server. Serious security concern!
- @DarkForumss member "Yucard" is promoting a CC/VCC Database Shop, offering linkable cards and sniffer bases, potentially facilitating illegal transactions.
- TAnandLab.com, a major Indian healthcare provider, has experienced a significant data breach, resulting in the exposure of 7,677,998 patient records. This breach raises concerns about potential scams or misuse of sensitive personal information.
- TMetro Group of Hospitals in India, including Metrohospitals.com, has encountered a substantial data breach, resulting in the compromise of 2,876,001 patient records. This includes sensitive information such as patient names, contact details, and medical histories.
- T12,000+ confidential documents from Peru's Military have been leaked, revealing sensitive information. The breach encompasses 8 folders of data, amounting to 4.54 GB in PDF format. Caution is advised as there may be duplicates with varying names but identical content.
- TA threat actor is offering unverified major access for sale: RDP via VPN to an undisclosed cryptocurrency platform for $50,000. This includes access to the admin panel, user database (view only), user details, and is secured with VPN, 2FA, and ESET.
- TAn alert has been issued regarding ransomware attacks targeting FPL Food and Walser Automotive Group. It's crucial to remain vigilant against cyber threats during this time.
- TA threat actor is offering shell access to multiple undisclosed universities for sale. The price ranges from $1,000 to $4,000, with payments accepted only in Monero or BTC. This poses a significant cybersecurity risk and warrants heightened vigilance.
- TA data breach in Dell has affected 49 million users. Spud is selling US customer data post-hack, including email and phone numbers. This alarming breach underscores the urgent need for heightened cybersecurity measures.
- TA previously surfaced data breach, the USA_Customers_04.2021 database containing over 153 million user records, initially posted by JohnRipper on the XSS forum, is reemerging. This database includes contact information in international format, raising significant concerns for user privacy and cybersecurity.
- The public university in Mataram, Indonesia (pmbmandiri.unram.ac.id) has been compromised. An SQL database containing usernames, passwords, and personal details of users has been accessed. Alarmingly, this data is publicly accessible, posing significant risks to user privacy and cybersecurity
- French site extranet.lde.fr compromised. SQL database leak includes user IDs, hashed passwords, and emails. Data is freely accessible.
- FrotCom's database has been compromised following a refusal to pay ransom demands. The first part of the dump has been released, containing sensitive customer information such as phone numbers, emails, plate numbers, usernames, and IMEI GPS numbers. This breach affects customers across more than 20 countries, with the possibility of further releases. Urgent action is advised to mitigate the potential risks posed by this breach.
- FrotCom's database compromised after ransom refusal. Initial dump includes customer phone numbers, emails, plate numbers, usernames, and IMEI GPS numbers across 20+ countries.
- memori.co.kr database compromised, exposing sensitive user information. Data includes user IDs, passwords, names, emails, phone numbers, addresses, and more.
- Hacker "Pills" is selling VPN access to the Ministry of Rural Development and Food in an EU country, providing serious internal system connectivity. Price: $5,000 USD. Middleman service required for transactions.
- Super Cash Back India website compromised, exposing personal and financial details of users, including names, contact info, bank details, and transaction history.
- Major health center in Panama compromised, exposing sensitive info of 2-3 million citizens, including ID numbers, names, addresses, and medical conditions. Breach year: 2024.
- "zazeado" has leaked a database containing personal information of nearly 6 million Argentine citizens from the Social Welfare Institute. The breach includes full names, ID numbers, and email addresses
- "rootSc3p" shares Ermac Botnet, Hook Botnet, and Craxs Rat 7.4 on Telegram.
- The FBI's domain seizure backfires as ShinyHunters relocate, highlighting law enforcement's tech missteps.
- A technical glitch in iMobile Pay has exposed credit card data of 17,000 ICICI Bank customers, underscoring the urgent need for heightened cybersecurity in financial institutions.
- The breach at OSDig exposes data of over 3,000 automotive business clients in Brazil, emphasizing significant privacy risks. Threat actors, such as SupahHackah, exploit such leaks for potential cyberattacks.
- The breach in the Puerto Rico Police Database has exposed sensitive data of over 16,000 officers, including emails, phone numbers, positions, and department details. This breach raises serious privacy and security concerns.
- A data breach has been detected in the Association PRO Guardia Civil's database from aprogc.es, exposing sensitive information. This underscores the persistent cyber threat landscape in law enforcement sectors.
- Recent cyber threats have emerged with the SySNet group claiming to leak sensitive documents from agencies like DoD, NSA, NATO, and more. This highlights the persistent risk of data breaches and underscores the need for robust cybersecurity measures.
Conclusion
As the cybersecurity landscape continues to evolve, vigilance and proactive defense strategies are paramount. The prevalence of breaches across various industries, regions, and organizational sizes underscores the importance of prioritizing cybersecurity measures. By staying abreast of emerging threats and implementing robust defense mechanisms, organizations can mitigate risks and safeguard against potential cyber threats, ensuring the integrity and security of their data and systems.
About Foresiet!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


June 7, 2024, 7:02 p.m.

May 23, 2024, 8:02 p.m.