Navigating the Tides of Cybersecurity: Trends and Insights (April 16th - April 30th, 2024)

Introduction
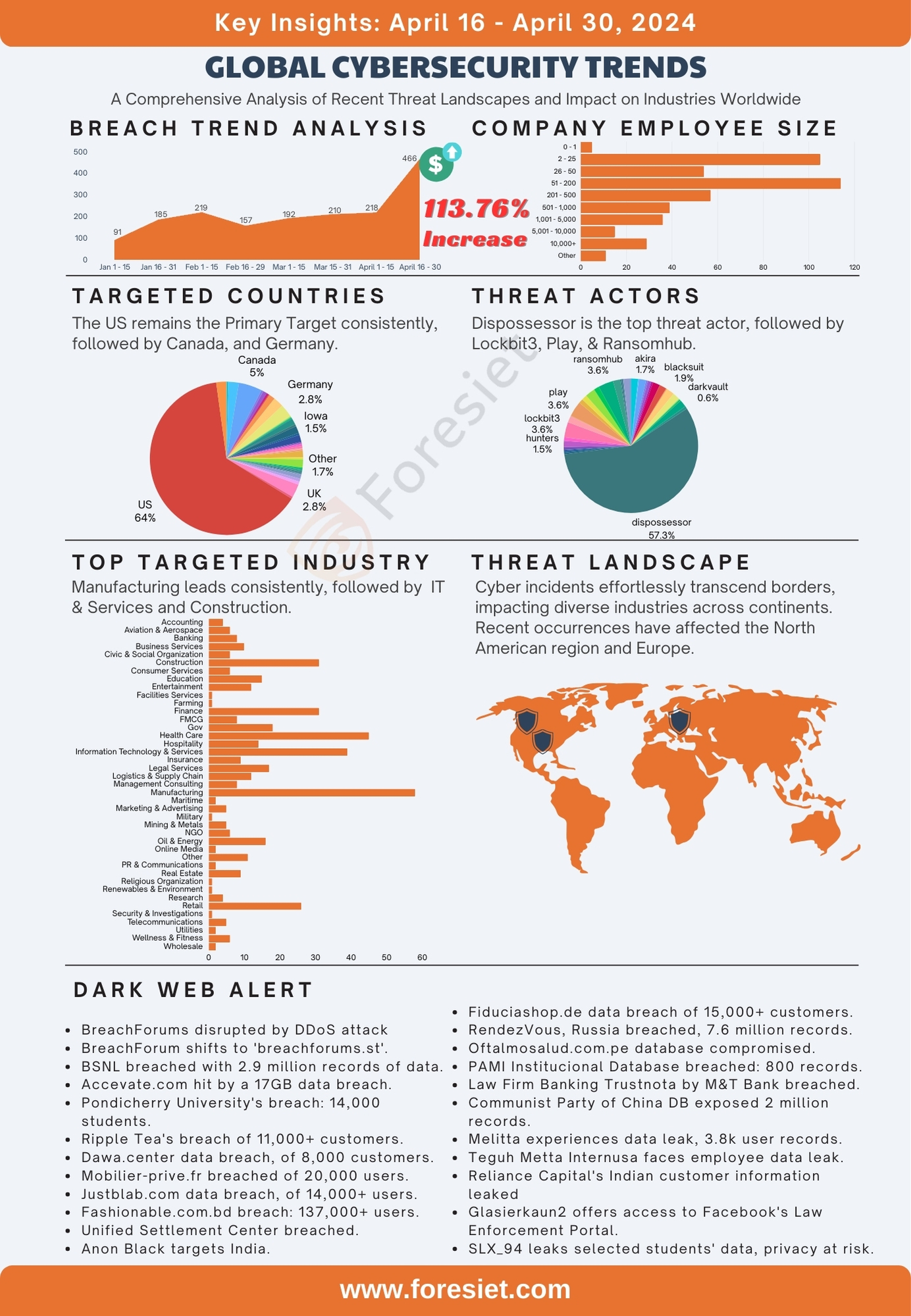
In the dynamic landscape of cybersecurity, the latter half of April 2024 witnessed a striking surge, with breaches escalating by a staggering 113.76% compared to the first half of the month. Threat actors, notably Dispossessor, Lockbit3, Play, & Ransomhub, intensified their activities, targeting key regions such as the United States, Canada, and Germany. Vital sectors like Manufacturing, IT & Services, and Construction found themselves under heightened threat. These cross-border attacks underscore the critical necessity for collaborative efforts on a global scale to bolster cyber defenses and safeguard digital infrastructure. This introduction sets the stage for a comprehensive exploration of breach data, industry dynamics, the correlation between employee size and vulnerabilities, attack surface management, threat actors, and the dark web, offering insights into the multifaceted landscape of cybersecurity. As organizations navigate the complexities of the digital realm, understanding and addressing the threats lurking within the dark web become imperative for maintaining robust security measures and fortifying cyber resilience.
Global Targets
In the realm of cybersecurity, threats know no borders, impacting nations across the globe with varying degrees of severity. Analyzing breach data from the recent period reveals a diverse landscape of cyber incidents, with certain countries emerging as primary targets. Among these, the United States stands out as the most heavily impacted country, accounting for approximately 63.80% of the total breaches documented. Following behind, Canada experienced around 4.96% of breaches, while Germany and the United Kingdom encountered 2.80% of breaches each, representing significant challenges in these regions. Furthermore, countries like Australia, Brazil, and Georgia faced notable cybersecurity incidents, underscoring the widespread nature of cyber threats on a global scale. As organizations and governments strive to enhance their cybersecurity posture, understanding the distribution of breaches across different regions becomes crucial for implementing targeted defense strategies and fostering international collaboration to mitigate risks effectively. The dark web continues to pose additional challenges, serving as a platform for cybercriminal activities and exacerbating the global cybersecurity landscape.
Industry Dynamics
Various industries worldwide face a relentless onslaught of breaches, highlighting the pervasive nature of cyber attacks across sectors. Examining breach data from the recent period reveals significant vulnerabilities across industries, with some sectors bearing the brunt of cyber incidents more than others. Foreseeing these challenges, it's imperative for organizations to fortify their defenses and remain vigilant against emerging threats on the dark web. Leading the tally of breached industries is Healthcare, accounting for approximately 9.66% of the total breaches, reflecting the critical need to safeguard sensitive medical data and patient information. Following closely behind, Manufacturing emerges as another heavily impacted sector, constituting around 12.46% of breaches, underscoring the vulnerability of manufacturing companies to cyber threats. Additionally, Information Technology & Services, Finance, and Education sectors faced notable challenges, representing approximately 8.36%, 6.66%, and 3.22% of breaches, respectively. These figures underscore the imperative for industry-specific cybersecurity strategies tailored to address unique vulnerabilities and risks. As organizations navigate the complex cybersecurity landscape, the dark web remains a looming threat, exacerbating challenges and emphasizing the critical importance of proactive defense measures to mitigate risks effectively.
Employee Size Matters
Breaches continue to impact companies of varying sizes, underscoring the universal vulnerability to cyber attacks across the corporate spectrum. Analyzing breach data from the recent period reveals a diverse array of company sizes affected by cyber incidents. Notably, small to medium-sized enterprises with employee counts ranging from 2 to 500 constitute a significant portion of breached entities, accounting for approximately 63.24% of the total breaches. Within this category, companies with 51 to 200 employees experienced the highest number of breaches, representing around 24.52% of the total, followed closely by those with 2 to 25 employees, constituting approximately 22.58% of breaches. Larger enterprises, comprising organizations with 501 to over 10,000 employees, also faced notable challenges, representing around 36.76% of breaches. Specifically, companies with 1,001 to 5,000 employees accounted for approximately 7.74% of breaches, while those with over 10,000 employees constituted around 6.24% of breaches. These figures underscore the imperative for companies of all sizes to prioritize cybersecurity measures and adopt robust defense strategies to mitigate risks effectively. As organizations navigate the complex cybersecurity landscape, understanding the correlation between company size and vulnerability to breaches is crucial for implementing targeted security protocols and safeguarding digital assets against evolving threats.
Analysis on Attack Surface Management
During the latter half of April 2024, spanning from the 16th to the 30th, our examination of digital environments revealed a total of 1594 vulnerabilities, with 137 classified as critical. Among these critical vulnerabilities, eight have garnered particular attention, with one currently having publicly available exploits. Notably, both of these vulnerabilities have been assigned EPSS scores ranging from 0.04% to 1.60%, signifying a high level of potential exploitation.
The Foresiet research team has diligently pinpointed exploits accessible to opportunistic threat actors, targeting vulnerabilities that present an easy attack surface. Some of the identified exploits include: CVE-2024-33566, CVE-2024-32766, CVE-2024-32651, CVE-2024-32599, CVE-2024-28189, CVE-2024-28185, CVE-2024-4040, CVE-2024-3193, CVE-2024-3191, and others. This revelation underscores the critical importance of proactively addressing these vulnerabilities to mitigate potential threats and fortify our digital defenses against emerging risks.
Threat Actors
In the realm of cybersecurity, the latter half of April 2024 witnessed a notable surge in breach incidents, underscoring the pervasive threat posed by various threat actor groups. Among these, the top five threat actors, namely Dispossessor, Lockbit3, Play, Ransomexx, and Ransomhub, played a significant role in orchestrating cyber breaches during the specified period. Dispossessor emerged as the most prolific threat actor, accounting for a staggering 57.30% of breach incidents. Lockbit3, Play, and Ransomhub followed closely behind, representing 3.65%, 3.65%, and 3.65% of breaches, respectively, while Ransomexx contributed to 2.36% of breach incidents. These threat actor groups engaged in a range of malicious activities, including ransomware attacks, data exfiltration, and system compromise, targeting organizations across various sectors and geographical regions. Understanding the modus operandi of these threat actors is essential for developing proactive defense strategies and mitigating cybersecurity risks effectively.
Top 5 Threat Actors
- Dispossessor: Responsible for approximately 57.30% of breach incidents, Dispossessor emerged as a significant threat actor during the latter half of April 2024. Their activity spiked suddenly, notably on April 19th, when they were exceptionally hyperactive, orchestrating major breaches that had significant repercussions for targeted organizations worldwide.
- Lockbit3: Accounting for around 3.65% of breaches, Lockbit3 operated with a focus on ransomware attacks, encrypting sensitive data and demanding ransom payments from affected organizations.
- Play: Contributing to about 3.65% of breaches, the Play threat actor group leveraged sophisticated attack vectors to infiltrate networks and exfiltrate sensitive information for monetary gain.
- Ransomexx: With approximately 2.36% of breaches attributed to them, the Ransomexx group employed ransomware tactics to encrypt data and extort payments from victimized organizations.
- Ransomhub: Representing 3.65% of breach incidents, Ransomhub engaged in widespread ransomware campaigns, targeting organizations across diverse sectors and geographic locations, aiming to disrupt operations and extract financial gain.
Dark Web Threats
In the cybersecurity landscape from April 16th to April 30th, 2024, various significant incidents in the dark web underscore the persistent threats facing digital environments worldwide. BreachForums experienced a disruptive DDoS attack, emphasizing the critical need for robust cybersecurity measures. Additionally, BSNL, a prominent Indian telecommunications company, suffered a massive breach, compromising millions of sensitive records. The breach highlights the severe risks of unauthorized access, potentially leading to identity theft and financial fraud. Moreover, several other websites worldwide encountered substantial data breaches, affecting users in multiple countries and emphasizing the ongoing challenges in safeguarding digital assets. These incidents serve as stark reminders of the importance of proactive defense strategies and vigilant cybersecurity measures to mitigate risks and protect sensitive data from malicious actors.
- An urgent cybersecurity update has been issued regarding BreachForums, a significant clearnet forum, which has experienced a major disruption due to a large-scale DDoS attack launched by threat actors R00TK1T and CyberArmyofRussia. This incident highlights the critical importance of implementing robust cybersecurity measures and proactive defense strategies in response to evolving cyber threats. It's crucial to stay vigilant and secure in light of such developments. #Cybersecurity #DDoS #BreachForums #ThreatIntelligence.
- The administrator of the infamous site BreachForum, facing domain suspension, has initiated a shift to a new domain, 'breachforums.st'. This action underscores the persistent challenges in such environments and emphasizes the critical necessity for robust security measures. Stay vigilant! #DarkWeb #CyberSecurity
- BSNL has suffered a major breach, exposing over 2.9 million lines of data. The compromised databases are accessible for download, prompting users to promptly secure their information. #DataBreach #CyberSecurity
- A massive data breach has impacted Bharat Sanchar Nigam Limited (BSNL), a prominent Indian telecommunications company, compromising over 2.9 million lines of data. The breach, involving unauthorized access and exfiltration of sensitive information including personal details and potentially financial data, poses severe risks such as identity theft and phishing attacks. The impact extends to financial losses, reputational damage, and legal consequences for BSNL. To mitigate risks, immediate security measures, transparent communication with affected users, user awareness campaigns, robust monitoring systems, and regulatory compliance efforts are essential. Affected individuals are advised to secure their information promptly. This incident underscores the ongoing challenges in cybersecurity and the critical need for proactive measures to protect sensitive data. #DataBreach #CyberSecurity
- Accevate.com, a school website in India, has experienced a significant data breach of 17GB, compromising sensitive information including student IDs, names, passwords, contact details, family information, and academic records. Immediate action is recommended to safeguard the privacy and security of students and staff.
- Pondicherry University's website (pondiuni.edu.in) has been breached, compromising data of around 14,000 students, including student IDs, names, contact details, academic records, and more. Urgent measures are required to secure affected students' data and prevent further unauthorized access.
- Ripple Tea's website (rippletea.com) has been compromised, leading to the exposure of information belonging to over 11,000 customers. This includes sensitive details such as names, email addresses, phone numbers, and encrypted passwords. Immediate action is recommended to secure affected accounts and prevent further unauthorized access.
- The website dawa.center has encountered a substantial data breach, affecting over 8,000 customers in the Arabia region. Personal details including names, contact numbers, and email addresses have been compromised. Immediate action is advised to protect affected individuals' privacy and prevent potential misuse of their information.
- The website fiduciashop.de has encountered a substantial data breach, affecting over 15,000 customers in Germany. Personal information such as email addresses, names, and potentially sensitive data may have been compromised. Immediate action is recommended to mitigate potential risks and safeguard affected individuals' privacy.
- The website mobilier-prive.fr has encountered a significant data breach, impacting over 20,000 users in France. Personal information including names, email addresses, and potentially sensitive data may have been compromised. Immediate action is advised to address any potential security risks and safeguard affected individuals' privacy.
- The website justblab.com has suffered a significant data breach, impacting around 14,000 users in the Philippines. Personal information including usernames, passwords, email addresses, phone numbers, and registration dates may have been compromised. Affected users should take immediate action to secure their accounts and monitor for any unauthorized activities.
- fashionable.com.bd has suffered a significant data breach, affecting over 137,000 users in Bangladesh. The leaked data comprises sensitive information like user IDs, names, email addresses, phone numbers, and registration/update timestamps. Affected users should promptly secure their accounts by changing passwords and monitoring for suspicious activities. Additionally, caution is advised against potential phishing attempts or scams related to this breach.
- The "Unified Settlement Center" in Yekaterinburg, Russia, has encountered a substantial data breach, impacting 168,273 lines of sensitive information. This includes user IDs, names, email addresses, phone numbers, and detailed inquiries.
- A significant data breach has occurred at the Russian online store RendezVous, exposing 7.6 million records, including client information, orders, and 4.5 million emails. The breach occurred on January 23, 2024.
- The database of oftalmosalud.com.pe in Peru has been compromised, exposing sensitive information including names, emails, phone numbers, and messages. If you've used this site, take precautions and monitor your accounts closely.
- The PAMI Institucional Database in Argentina has been compromised, with over 800 user credentials leaked, including usernames, passwords, emails, and personal details. Immediate action and password changes are advised
- The Law Firm Banking Trustnota by M&T Bank has been compromised, exposing sensitive access tokens and files. Over 600+ rows affected. Urgent security measures needed to prevent potential financial losses.
- 2 million members of the Communist Party of China database have been exposed. Includes sensitive information like ID numbers, addresses, and more. Serious implications for security and privacy
- It’s crucial for companies like Melitta to secure their user data. The recent leak of 3.8k user records, including sensitive information like emails and hashed passwords, is a serious concern for privacy and security.
- It appears there has been a leak of employee data from Teguh Metta Internusa (Putra Tidar Perkasa). It's crucial for companies to protect such sensitive information to ensure privacy and security.
- On the dark web, an individual using the alias "r4ng3r" has exposed a data breach involving Reliance Capital's Indian customers. The leaked data includes access to the Super Admin Portal, with capabilities such as email and SMS sending via Reliance servers, editing customer profiles, and altering bank details. Sensitive information like user and customer names, email addresses, phone numbers, Aadhar details, and addresses are compromised. This package is offered for sale at 2500 USD. Breach Date: April 29, 2024. Hacker Alias: r4ng3r. Affected Database: Reliance. Country: India. Attack: April 2024. Samples are available.
- Data breach alert! User 'r4ng3r' has leaked Reliance Capital's Indian customer information. The Super Admin Portal access is compromised, enabling email/SMS sends, EMI changes, and more. Sensitive data is for sale at $2500. Breach Date: April 29, 2024
- Glasierkaun2 offers access to Facebook's Law Enforcement Portal, providing extensive data on targets, incl. IP addresses, phone numbers, emails, messages, and device info via subpoenas. Also offers emergency data requests and post removal/suspension services. Contact @iMaxScraper on Telegram for details.
- Anon Black claims responsibility for recent attacks targeting India, expressing frustration with simplimoney.co.in and w.simplimoney.co.in. Stay vigilant and secure your online presence.
- Hacker SLX_94 (@SLX_94) issues a strong message to India following cyber attacks, highlighting store-247.in/ as a target. Stay alert and prioritize cybersecurity measures.
- Hacker SLX_94 (@SLX_94) exposes sensitive data (2000++) including names, gender, bank details, and parents' names from nskfdc.nic.in/. Immediate action and enhanced security measures are advised.
- Hacker SLX_94 (@SLX_94) has leaked a list of selected students from socialwelfare.ladakh.gov.in/. Urgent measures needed to protect student privacy and prevent misuse.
Conclusion
In conclusion, the latter half of April 2024 witnessed a significant escalation in cybersecurity breaches, highlighting the persistent and evolving nature of cyber threats. From disruptive DDoS attacks to massive data breaches affecting organizations worldwide, the period underscored the critical importance of robust cybersecurity measures and proactive defense strategies. As threat actors continue to target diverse industries and exploit vulnerabilities across different company sizes, it's imperative for organizations to prioritize cybersecurity, leverage threat intelligence, and foster international collaboration to effectively mitigate risks and safeguard digital assets in an increasingly interconnected world. Additionally, the clandestine activities of the dark web further exacerbate these challenges, requiring heightened vigilance and comprehensive strategies to address the ever-growing threat landscape.
About Foresiet!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


June 7, 2024, 7:02 p.m.

May 23, 2024, 8:02 p.m.